Abstract
When readers study on campus, work in a company, or shop at the mall, they may notice that these places are all covered by networks. Through these networks, one can access internal school resources, use internal devices of the company such as printers, or access the Internet to browse news and information. These networks are classified as campus networks and are usually built by the companies or organizations themselves. Campus networks not only enhance the operational efficiency of enterprises, but also provide network access services to the outside world.
You have full access to this open access chapter, Download chapter PDF
When readers study on campus, work in a company, or shop at the mall, they may notice that these places are all covered by networks. Through these networks, one can access internal school resources, use internal devices of the company such as printers, or access the Internet to browse news and information. These networks are classified as campus networks and are usually built by the companies or organizations themselves. Campus networks not only enhance the operational efficiency of enterprises, but also provide network access services to the outside world.
This chapter will introduce the definition of campus network, explain the typical networking architecture of campus network, analyze the planning and design methods of small campus network, deployment and implementation methods, as well as the basic work required for operation, maintenance and optimization. At the end of this chapter, a network engineering project will be created based on enterprise requirements.
15.1 Basic Concepts of Campus Networks
15.1.1 What Is a Campus Network?
A campus network is a local area network that connects people and things in a limited area, and usually has only one management body. If there are multiple management bodies, it will be considered as multiple campus networks.
A campus network can be large or small in size, ranging from smaller ones such as a small home office (SOHO) and wireless coverage in a coffee shop, to larger ones like networks for a campus, corporate campus, park and shopping center. The scale of the campus is limited, and the general size of large campuses, such as college campuses and industrial parks, is generally within a few square kilometers. Within this range, we can use LAN technology to build a network. A “campus” larger than this is usually regarded as a “metropolitan area” and needs to use WAN technology, and the corresponding network will be regarded as a MAN.
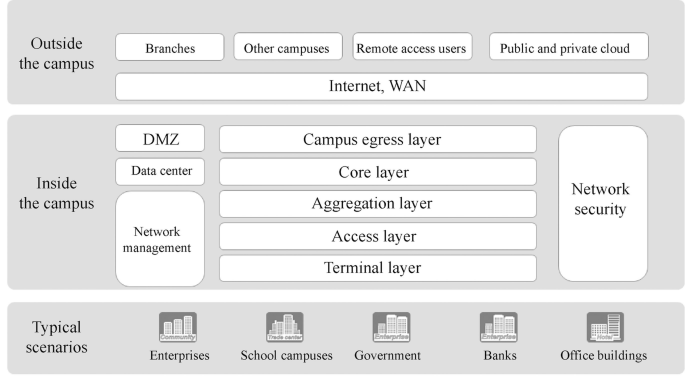
As shown in Fig. 15.1, campus networks can be used in enterprises, school campuses, government, banks and office buildings. Inside the campus network is usually a hierarchical and regional design, which is the modular design we usually refer to. Hierarchical design by the location of devices in the network can divide the network devices into terminal layer (wireless devices such as computers and cell phones are in the terminal layer), access layer, aggregation layer and core layer. According to the functions achieved, network is divided into network management, network security, Demilitarized Zone (DMZ) and data center zone. The area connecting the outside of the campus is the campus egress layer, which connects other branches, other campuses, remote access users and private and public clouds via Internet and WAN (Wide Area Network).
Typical LAN technologies used in the campus network include Ethernet technology (wired) following the IEEE 802.3 standard and Wi-Fi technology (wireless) following the IEEE 802.11 standard.
15.1.2 Typical Architecture of Campus Network
Campus networks generally follow the principles of hierarchical, regional and modular design. According to the number of end users or network elements (including routers, switches, wireless ACs, APs and other devices), campus networks can be divided into small campus networks, medium campus networks, and large campus networks. Figure 15.2 shows the typical architecture of a campus network.
-
1.
The core layer is the backbone of the campus network and the core of data exchange in the campus。It connects various components of the campus network, such as the aggregation layer, data center, egress area and network management area.
-
2.
The aggregation layer is in the middle level of the campus network, performing the function of data aggregation or exchange, and providing some key basic network functions, such as routing, QoS (Quality of Service) and security.
-
3.
The access layer provides end users with campus network access services and is the border of the campus network.
-
4.
The egress area is the border separating the internal campus network from the external network, and is used to realize internal users’ access to the public network as well as the external users’ access to the internal network. Generally, a large number of network security devices are deployed in this area to defend against attacks from external networks, such as IPS (Intrusion Prevention System), Anti-DDOS (traffic cleaning) devices and Firewall.
-
5.
The data center area is the area where servers and application systems are deployed to provide data and application services for internal and external users.
-
6.
Network management area is the area where network management system is deployed, including SDN controller, wireless controller, eLOG (log server), etc. It manages and monitors the whole campus network.
-
1.
Small campus network architecture
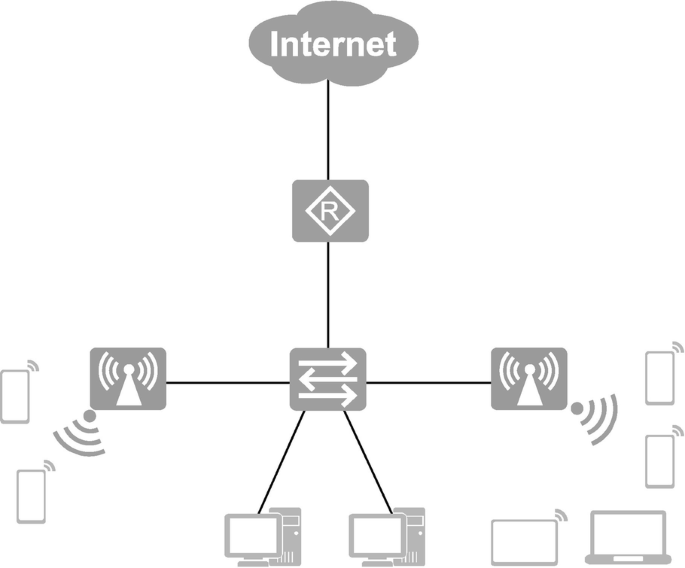
Small campus networks are mostly used in scenarios where there are a small number of access users, generally supporting a few to dozens of users. The network is built to enable the access to internal resources. It only covers a single location, and is not hierarchical, with simple networking requirements. The architecture of small campus network is shown in Fig. 15.3.
-
2.
Medium campus network architecture
The number of end users of medium campus network is generally between 200 and 2000, and the number of network devices is generally between 25 and 100, which can support several hundreds to thousands of users to access. For medium networks, the concept of dividing areas by function is introduced, which is the modular design, but there are relatively few functional modules. Areas are generally flexibly divided according to business needs.
The medium campus network is used in the most scenarios, and its functional modules are shown in Fig. 15.4. It generally adopts a Layer 3 network structure – core layer, aggregation layer, and access layer, and it is divided into two functional areas– the data center and egress layer. The data center is usually deployed with enterprise servers, such as Web sites of the intranet, office systems and database servers. The egress layer is connected to the Internet and the core layer, and usually deploys firewalls to control the traffic from the intranet to the Internet. In the meantime, it prevents attackers on the Internet from invading the intranet. In addition, the network address is also translated at the egress layer.
-
3.
Large campus network architecture
A large campus network may be a network covering multiple buildings, or a network connecting multiple campuses within a city via WAN. It generally provides access services, such as allowing traveling users to access the company’s internal network through technologies such as VPN.
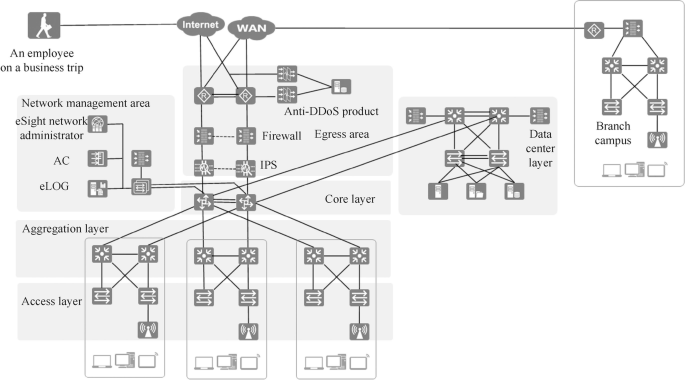
A large network has the following features: wide coverage, large number of users, complex network requirements, full functional modules and rich network hierarchy. The architecture of large campus network is shown in Fig. 15.5. The functional modules of the headquarters campus are access layer, aggregation layer, core layer, egress layer, data center and network management area. At the egress layer, cloud data centers and branch campuses can be connected via Internet or WAN, and users on business trips and users working from home can access the network of the headquarters campus via Internet.
15.1.3 Protocols and Technologies Commonly Used in Campus Networks
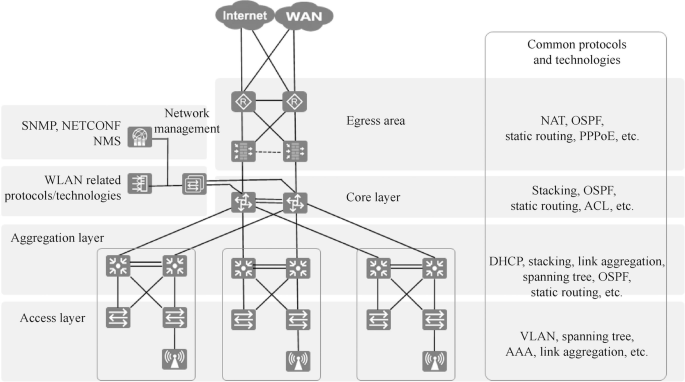
Protocols or technologies that will be used in each layer and module of the campus network are shown in Fig. 15.6.
The technologies used in the core layer of the campus network are stacking, OSPF, static routing and ACL. The technologies used at the aggregation layer include DHCP, stacking, link aggregation, spanning tree, OSPF and static routing. The technologies used at the access layer are VLAN, spanning tree, AAA and link aggregation. The technologies used in the egress area are NAT, OSPF, static routing and PPPoE. And the technologies used in the network management area include SNMP.
To be specific, core layer switches, aggregation layer switches, egress area firewalls and routers all need to be configured with static routing or dynamic routing to enable network connections between the intranets and to access the Internet. Among them, the router in the egress area connected to the Internet is configured with NAT or NAPT to enable the intranet to access the Internet, and NAT Server can also be configured so that computers in the Internet can access the servers on the intranet. The link in the egress area connecting the ISP is usually a WAN link and may also use PPPoE or PPP protocol. The aggregation layer switches and access layer switches use Spanning Tree Protocol to prevent loops. Inter-VLAN routing is usually implemented on aggregation layer switches, and aggregation layer switches use DHCP to assign IP addresses to computers in the VLANs. The FIT APs of the campus network are configured on the AC through WLAN-related protocols. And devices in the network is managed and monitored on the network management server via SNMP protocol or NETCONF protocol.
15.2 Lifecycle of a Campus Network
Generally speaking, the life cycle of a campus network includes at least the whole process of planning and programming, deployment and implementation, operation and maintenance, and network optimization of the network system. The life cycle of a campus network is a cyclic iterative process, and each cyclic iteration is driven by changes in network application requirements. Each cycle of change is centered on four phases: planning and programming, deployment and implementation, operation and maintenance, and network optimization.
-
1.
Planning and design.
Network planning and design is the starting point of a project. Perfect and detailed planning will lay a solid foundation for the specific subsequent work of the project. The work in this phase includes determining the physical topology of the network, the logical topology, technologies and protocols to be used, etc.
-
2.
Deployment and implementation.
Project implementation is where engineers deliver the specific operation of the project. Systematic management and efficient processes are the fundamental elements to ensure the successful implementation of the project. The work in this phase includes equipment installation, stand-alone commissioning, interconnection testing, cutover and grid connection, etc.
-
3.
Operation and maintenance.
To ensure the normal operation of network functions and thus support the successful provision of user services, daily maintenance and troubleshooting of the network are required. The work in this phase includes daily maintenance, software and configuration backup, centralized network management monitoring, software upgrade, etc.
-
4.
Network optimization.
The user’s business is constantly evolving, so the user’s demand for network functions will change accordingly. When the existing network fails to meet the business needs, or when the network reveals certain hidden problems during the operation, network optimization is required to address the problems. The work in this phase includes improving the security of the network and enhancing the experience of network users.
15.3 Hands-On Practice of Campus Network Projects
15.3.1 Network Requirements
A company (with about 200 employees) plans to create a new campus network due to business development needs, and the network requirements are as follows.
-
1.
It can meet the current business needs of the company.
-
2.
The network has a simple topology and is easy to maintain.
-
3.
It provides wired access for employees to use in their offices and Wi-Fi service for visitors.
-
4.
Simple network traffic management.
-
5.
A certain level of security is ensured.
15.3.2 Planning and Design of Small Campus Networks
The planning and design of small and medium campus networks in this case need to take into consideration the following elements.
-
1.
The design of networking plan, including equipment selection, physical topology and equipment naming.
-
2.
Basic service design, including VLAN design and planning, IP address design and planning, IP address assignment method, and routing design.
-
3.
WLAN design, including WLAN networking design, WLAN data forwarding mode design.
-
4.
Network reliability design.
-
5.
Layer 2 loop avoidance design.
-
6.
Egress NAT design.
-
7.
Security design, including traffic control, DHCP security and network management security.
-
8.
Operation, maintenance management design, including the management using traditional equipment, and management based on the iMaster NCE platform.
-
1.
The design of networking plan
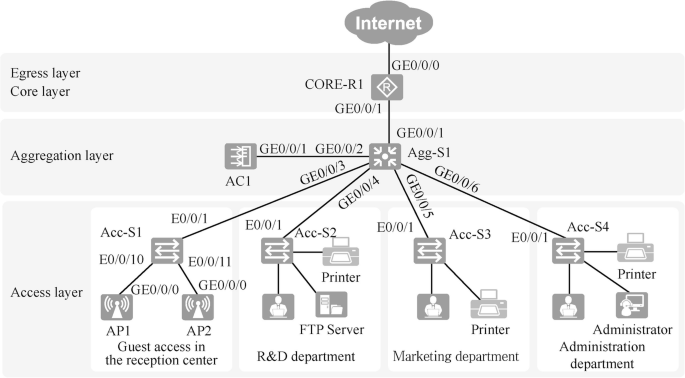
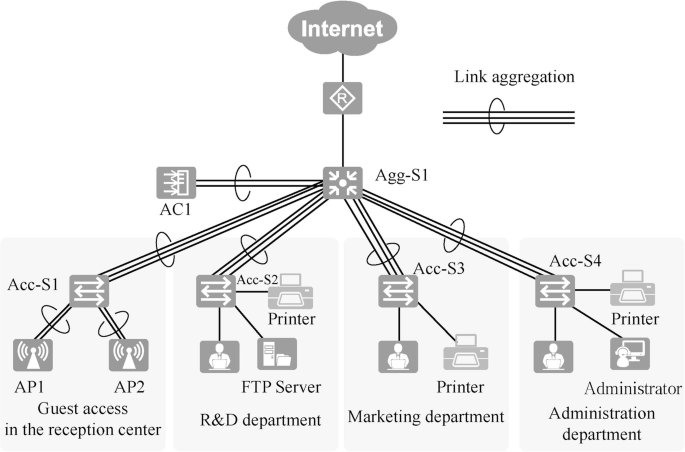
After taking into consideration the budget, business requirements and other factors, the physical layer topology in this case is designed as shown in Fig. 15.7. The devices can be named according to a uniform method that is easy to remember and scalable. For example, the access layer switches are named Acc-S1, Acc-S2, Acc-S3, etc., and the aggregation layer switches are named Agg-S1, Agg-S2, etc. The selection of interfaces for interconnecting devices should meet the bandwidth requirements.
Note: Acc is the abbreviation of Access, which represents the access layer device; and Agg is the abbreviation of Aggregation, which represents the aggregation layer device.
The entire network adopts a Layer 3 architecture. The access layer switch is S3700, which provides 100-gigabit network access for employees’ PCs, printers and other terminals. The aggregation layer switch is an S5700, which serves as the gateway to the Layer 2 network. The core and egress layers are combined into one, and the router is AR2240, which functions as the egress of the whole campus network.
-
2.
Basic service design
-
(a)
Design and planning of VLAN.
The design of VLANs is recommended as follows.
-
VLAN numbers are recommended to be assigned consecutively to ensure the reasonable use of VLAN resources.
-
VLAN division needs to distinguish between service VLAN, management VLAN and interconnection VLAN.
-
VLANs can be divided based on interfaces.
-
Service VLAN design can divide VLANs by geographical area, by logical area, by personnel structure and by service type.
-
Management VLANs are mostly used for remote management of network devices, and it is necessary to configure IP addresses, subnet masks and default routes for the devices to be managed. It is recommended that all switches belonging to the same Layer 2 network use the same management VLAN, with the managed address in the same network segment. Usually, Layer 2 switches use the VLANIF interface address as the managed address.
The VLAN planning for this case is as follows (see Table 15.1).
-
Management VLANs for Layer 2 devices are reserved.
-
Based on the personnel structure, the VLANs are divided into guest VLAN, R&D VLAN, marketing VLAN and administration VLAN.
-
Considering that Layer 3 switches need to be connected to routing through VLANIF, it is necessary to reserve interconnection VLANs.
-
The VLANs required to establish CAPWAP tunnel between AP and AC are reserved.
-
-
-
(b)
Design and planning of IP addresses.
The service IP address is the address allocated to servers, hosts, wireless devices, etc. The design and planning principles of the service IP address are as follows.
-
Gateway IP address is recommended to uniformly use the last or the first available address of this network segment, for example, for network segment 192.168.80.0/24, the address of the gateway is 192.168.80.254 or 192.168.80.1, so as to avoid conflict with the computer addresses of the network segment as far as possible.
-
The IP address range planning of each service VLAN should ensure that the IP address of each type of service terminal is continuous and aggregatable, which is convenient for routing aggregation.
-
It is recommended to use an IP address segment with a 24-bit mask.
-
Switches use VLANIF interfaces to configure the managed addresses, and it is recommended that all switches use the same network segment for their managed addresses.
-
It is recommended that network device interconnection IP addresses use IP addresses with 30-bit masks and core devices use IP addresses with smaller addresses.
When planning network segments and gateway addresses for each type of services, the number of access clients should be taken into account and sufficient IP addresses should be reserved. Table 15.2 lists the addresses, subnets and gateways of each network segment in this case.
-
-
(c)
IP address assignment method.
Dynamic IP address assignment or static IP address assignment can be adopted to assign IP addresses. In small and medium campus networks, the specific assignment principles of IP addresses are as follows.
IP addresses of WAN interfaces are assigned by the carriers, such as through static IP addressing and dynamic IP addressing (DHCP or PPPoE method). For IP addresses of WAN interfaces, communication with the carrier is required in advance in order to obtain them.
For servers and special terminal devices (such as punch-card machines, printers, IP video monitoring devices, etc.), it is recommended to use static IP address binding to assign them.
For user terminal devices (such as PCs in user’s offices, IP phones, etc.), their IP addresses are recommended to be dynamically assigned through DHCP by deploying a DHCP server on the gateway device in a unified manner.
The IP address assignment method in this case is shown in Table 15.3. The WAN interface connected to the Internet can use PPPoE to obtain IP address. All terminals (office computers and devices that wirelessly access the network) can obtain IP addresses by DHCP. Servers and printers will be assigned fixed IP addresses. IP addresses of all network devices can be configured by a static method (except APs).
-
(d)
Route design.
The route design of small and medium campus network includes the internal route design and the campus egress route design.
The internal route design must meet communication requirements of devices and terminals on the campus network and enable communication with the external network. As the network of small and medium campus is relatively small and the network structure is comparatively simple, the internal route design is not complicated. By default, AP devices generate a default route after IP addresses are assigned by DHCP. Switches and gateway devices can meet the demand through static routes without deploying complex routing protocols.
The route design of the campus egress is mainly required to meet the demand of the internal users of the campus to access the Internet and WAN, and it is recommended to configure static default routes on the egress devices.
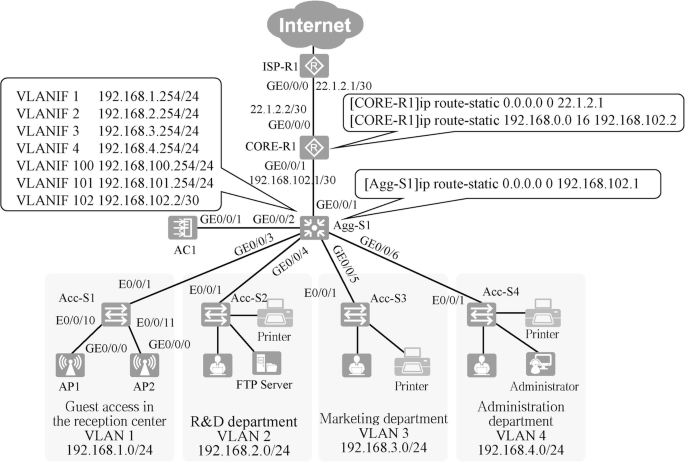
In this case, the routes on devices Agg-S1 and CORE-R1 are shown in Fig. 15.8. Add a default route in device Agg-S1 to address 192.168.102.1 of interface GE0/0/1 of router CORE-R1. Add a default route in router CORE-R1 to IP address 22.1.2.1 of interface GE0/0/0 of router ISP-R1., and another static route to the intranet, which summarizes the intranet into a network segment 192.168.0.0/16, with the next hop pointing to IP address 192.168.102.2 of interface VLANIF 102 of device Agg-S1.
-
(a)
-
3.
WLAN Design
-
(a)
WLAN networking design.
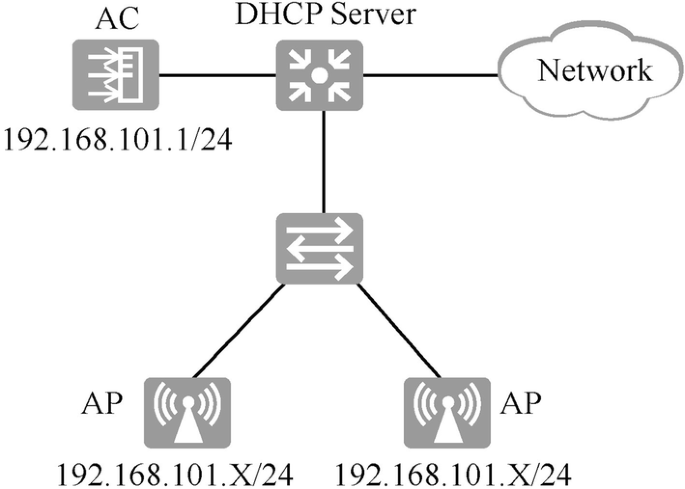
According to the IP addresses of AC and AP, and whether the data traffic passes through AC, the network can be divided into directly connected Layer 2 network, Layer 2 network in bypass mode, directly connected Layer 3 network, and Layer 3 network in bypass mode. As shown in Fig. 15.9, this case adopts the Layer 2 networking in bypass mode.
-
(b)
WLAN data forwarding mode design.
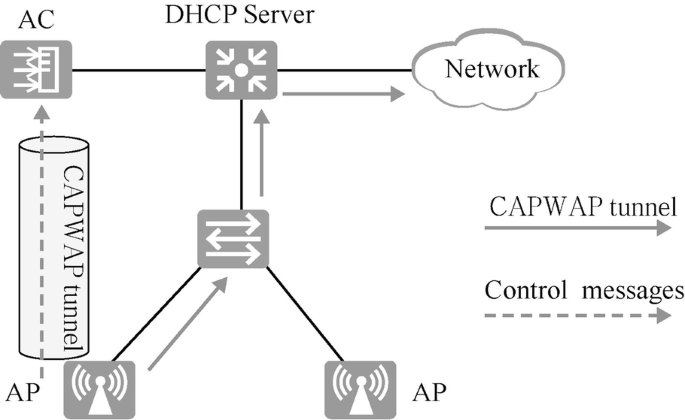
The data in WLAN includes control messages and data messages. Control messages are forwarded through CAPWAP tunnel, while data messages are forwarded by tunnel forwarding and direct forwarding. This case uses the direct forwarding, as shown in Fig. 15.10.
-
(c)
Other designs.
In addition to planning the networking and data forwarding methods, the following designs are also necessary.
Network coverage design: the area covered by wireless network shall be designed and planned to ensure that the signal strength within the covered area can meet the requirements of users and solve the problem of co-channel interference between neighboring APs.
Network capacity design: the number of APs for the network shall be designed and deployed according to data such as the bandwidth requirements of wireless terminals, the number of terminals, concurrent volume and single AP performance to ensure that the wireless network performance can meet the Internet service needs of all terminals.
AP layout design: based on the network coverage design, the actual layout location of the AP, layout method and power supply alignment principle will be revised and confirmed according to the actual situation.
In addition, WLAN security design and roaming design are also vital, which are not listed in this chapter.
There are many items and contents to be configured when configuring WLAN. Before configuring WLAN, it is necessary to clarify the configuration options and contents. Table 15.4 shows the WLAN configuration items and configuration contents in this case. In the process of configuration, the configuration items should be configured with reference to the configuration content to avoid errors.
-
(a)
-
4.
Network reliability design
The access layer and aggregation layer in this case both use a switch for networking. The reliability of switch networking is divided into port-level reliability and device-level reliability.
-
(a)
Port-level reliability. Using Ethernet link aggregation technology can enhance the reliability between the access switch and the aggregation switch, and also increase the link bandwidth. As shown in Fig. 15.11, link aggregation is implemented between AC1 and Agg-S1, between AP1 and Acc-S1, and between the access layer switch and the aggregation layer switch.
-
(b)
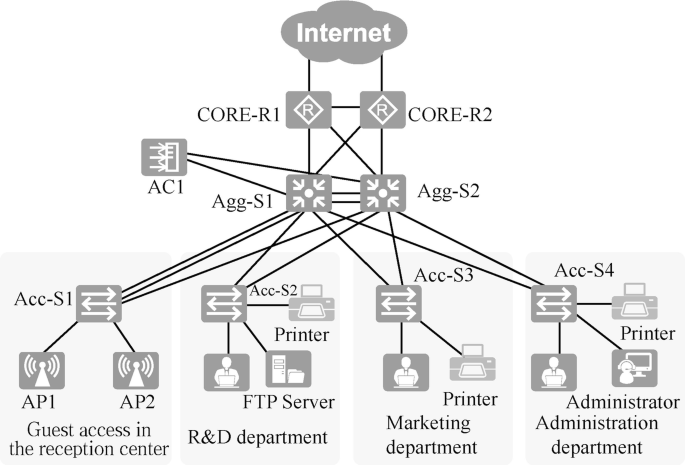
Device-level reliability. This can be achieved by using dual aggregation layers and dual layers, as shown in Fig. 15.12. You can also use iStack or CSS technology, which is not introduced in this case.
In this case, port-level reliability is chosen. Compared with device-level reliability, this scheme uses fewer devices and can save network cost.
-
(a)
-
5.
Layer 2 loop avoidance design
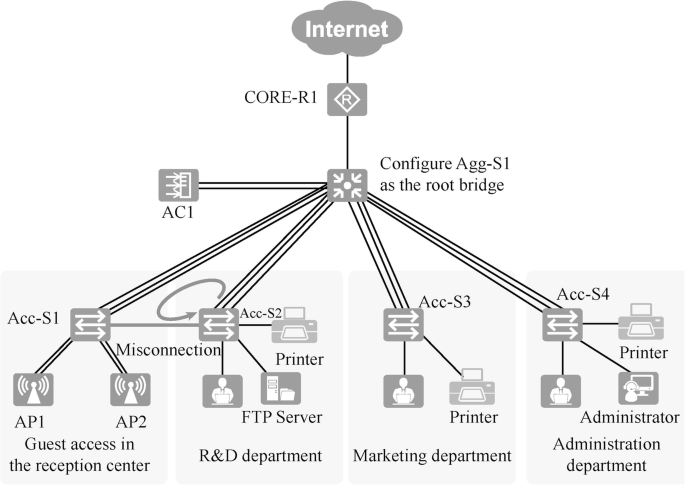
According to the reliability design, this case chooses the port-level reliability design scheme. Redundant links are not introduced to the current network segment, and there is no loop, as shown in Fig. 15.13. However, it is possible for office workers to connect two switches by mistake and form a loop. To prevent the loops caused by the maloperation of office workers, the switches can be configured to use spanning tree technology. The Rapid Spanning Tree Protocol (RSTP) is adopted, and in the meantime, it is recommended to manually configure Agg-S1 as the root bridge.
-
6.
Egress NAT design
The intranet of the campus network usually uses private addresses, and network address translation (NAT) is needed for the intranet computers to access the Internet. The router connected to the Internet usually has a public address and is configured with NAT. NAT includes static NAT, dynamic NAT, NAPT, easy IP and NAT server, and the appropriate type of NAT can be selected according to the actual situation.
Static NAT is suitable for the scenario where there are a lot of static public IP addresses and the intranet computers need to use a fixed public address to access the Internet. In this scenario, computers on the Internet can also use the public address to directly access the corresponding private address.
An address pool is a concept for dynamic NAT, and the available addresses in the public address pool are chosen to enable the intranet computers to access the Internet. In this scenario, the intranet can initiate an access to the Internet, while the Internet is unable to initiate an access to the intranet through the public address. A public address can only translate the address for one computer on the intranet.
NAPT is suitable for scenarios where there are a limited number of IP addresses in the public address pool. If there are more computers on the intranet than the addresses in the public address pool, NAPT should be configured to save public network IP addresses and improve the utilization of public network IP addresses.
Easy IP is appropriate for scenarios where the address of the interface connected to the Internet is dynamically obtained. When using the public address of the interface as NAPT, there is no need to configure a public address pool.
NAT server is suitable for scenarios where computers on the intranet need to provide services to computers on the Internet. With NAT server configured, computers on the Internet can access specific services on the intranet, such as Web services on the intranet, through the public address of the router.
In this case, it is recommended to choose easy IP for egress NAT, and the NAT server does not need to be configured.
-
7.
Security design
The security design in this case involves traffic control, DHCP security and network management security, which can be enabled by using routers and switches.
-
(a)
Traffic control.
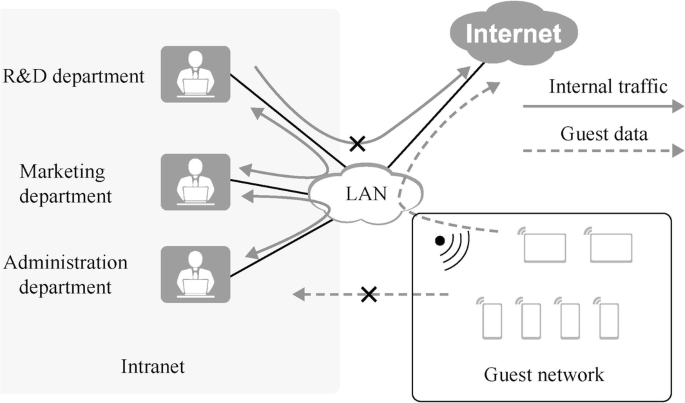
As shown in Fig. 15.14, the computers in R&D department, marketing department and administration department are allowed to access each other, but not the Internet. Computers in the guest network can access the Internet, but not the internal campus network. We can use traffic-policy, traffic-filter and other technologies to control the traffic and allow the guest network to access the Internet by configuring NAPT. Configuring NAPT requires creating ACLs and defining the network segments that are allowed to access the Internet. In this case, only two rules need to be added to the ACL, one is to allow the guest traffic to pass and the other is to deny other traffic to pass. Then configure Easy IP at the router egress.
-
(a)
[CORE-R1]acl 2000 [CORE-R1-acl-basic-2000]rule 5 permit source 192.168.1.0 0.0.0.255 [CORE-R1-acl-basic-2000]rule 10 deny [CORE-R1-GigabitEthernet0/0/0]nat outbound 2000
-
(b)
DHCP security.
In campus networks, it is a common situation that employees connect to DHCP wireless router without permission, so that the intranet addresses become a mess, which results in address conflict and inability to access the Internet. At this time, DHCP Snooping can be adopted in the access layer switch to prevent this situation and ensure DHCP security.
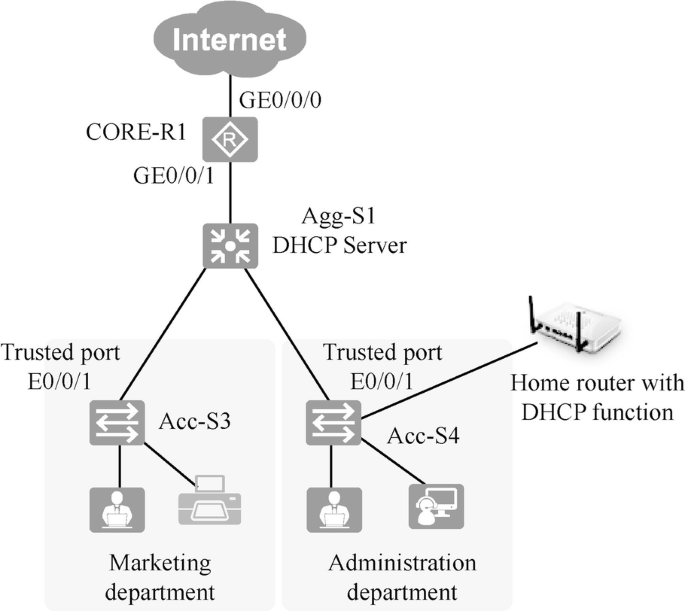
As shown in Fig. 15.15, to prevent the computers in the administration department from obtaining IP addresses from the home router, DHCP Snooping is enabled on the Acc-S4 switch and E0/0/1 is set as the Trusted port. so that DHCP requests sent by computers will only be sent to interface E0/0/1.
[Acc-S4]dhcp enable [Acc-S4]dhcp snooping enable [Acc-S4]vlan 4 [Acc-S4-vlan4]dhcp snooping enable [Acc-S4-vlan4]quit [Acc-S4]interface Ethernet 0/0/1 [Acc-S4-Ethernet0/0/1]dhcp snooping trusted
-
(c)
Network management security.
When using Telnet, Web or other methods for network management of the device, only fixed users (computers with fixed IP addresses) can be allowed to login for network management through ACL technology. For centralized network management [the administrator can get the working status of all the managed devices in time through the operation port of a management terminal program, and can configure all the managed devices through this port. Simple Network Management Protocol (SNMP) defines the standard for the management communication between the management terminal and the network devices]. SNMPv3 adds authentication and encryption processing, which can significantly improve the security of network management.
-
8.
Operation, maintenance and management design
The operation, maintenance and management of small and medium campus network can be managed by traditional devices or on the iMaster NCE platform. Traditional device management is chosen in this case.
-
(a)
Management by traditional devices.
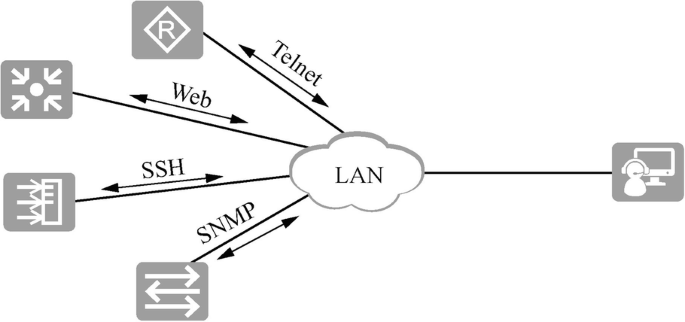
If the network administrator and the device IP are reachable, the device can be managed through Telnet, Web and SSH, as shown in Fig. 15.16. When there are many network devices, SNMP protocol-based unified network management software can be deployed for network operation, maintenance and management.
-
(b)
Management based on iMaster NCE platform.
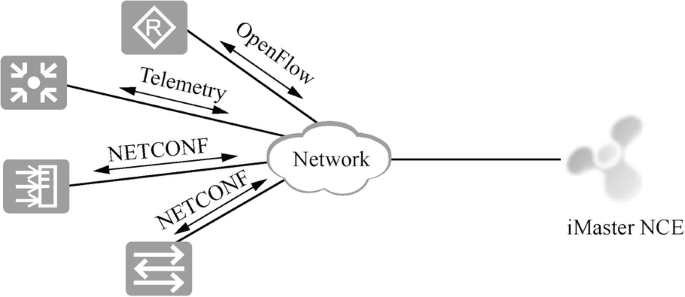
In addition to management by traditional devices based on SNMP, Huawei iMaster NCE platform can also be adopted for network operation, maintenance and management so as to achieve “autopilot” of the network. As shown in Fig. 15.17, on iMaster NCE platform, network devices can be managed through OpenFlow, NETCONF and Telemetry protocols.
-
(a)
15.3.3 Deployment and Implementation of Small Campus Networks
In the deployment and implementation phase, a list of configuration contents is required before configuring the network devices, and then the devices are configured with reference to the list. After the configuration is completed, testing is performed to ensure that the configuration can achieve the designed functionality.
-
1.
Network configuration
-
(a)
Configure the port.
After physical lines between the network devices are connected, you need to configure the link aggregation between the access layer switches and aggregation layer switches and add the port description. To avoid configuration errors, first, information including the link aggregation interface (Eth-Trunk) number, link aggregation mode, port members of the link aggregation port and link aggregation port description required for each switch shall be organized in the table. The Eth-Trunk ports that need to be created on the switch in this case and what needs to be configured are shown in Tables 15.5 and 15.6.
-
(b)
Configure VLANs.
In this case, VLANs are created based on the personnel structure. Four service VLANs, two management VLANs and one interconnection VLAN need to be created for three departments and guests (see Table 15.1). After creating the port-based VLANs on the switch, you also need to configure the port type and the VLAN to which the access port belongs, and configure the PVID of the trunk port and the VLANs allowed to pass through.
In order to avoid errors in the configuration process, the information that needs to be configured can be listed in advance in tables. Tables 15.7 and 15.8 show the types of each port and the content that needs to be configured. As it can be seen from the table, we have configured the Eth-Trunk port type as Trunk, the same PVID is specified, and only the necessary VLANs are allowed to pass through the trunk.
-
(c)
Configure static addresses.
The addresses of the management ports of access layer switch and aggregation layer switch, and the ports of aggregation layer switch Agg-S1 and core layer router CORE-R1 are also statically configured. To avoid errors in the configuration, the address of each port needs to be planned in advance. The details of the IP address configuration of routers and switches in this case are shown in Table 15.9. As it can be seen from the table, inter-VLAN routing is enabled by the aggregation layer switch Agg-S1, and the address configured for port VLANIF corresponds to the last address of the VLAN.
-
(d)
Configure DHCP.
Terminals and APs use DHCP to obtain addresses. In this case, Agg-S1, the aggregation layer switch, is configured as a DHCP server to assign addresses to computers in the VLANS of R&D department, marketing department, and administration department as well as for guests, and also to assign addresses to APs in the management VLAN of the WLAN. Therefore, four address pools need to be created on Agg-S1. Gateways and DNS have to be assigned to each address pool, and the lease duration needs to be specified based on the time the terminal stays after accessing the network. If a fixed address needs to be assigned to a specific device, the IP address and MAC address need to be bound. If there are addresses in the address pool that have already been taken, they will be excluded. In this case, the IP address taken by the AC needs to be excluded from the management VLAN of the WLAN.
The IP address pools created on Agg-S1, the gateway and DNS of each address pool, the excluded addresses and the bound addresses in this case also need to be planned and sorted in advance. The details can be found in Table 15.10.
-
(e)
Configure routing.
This case uses static routing. In order to allow administrators to access the access layer switch and AC1 across network segments, it is necessary to configure default routes on the access layer switch and AC1. On the aggregation layer switch, you only need to add a default route to the core layer router CORE-R1, and on CORE-R1, you need to add a route to the intranet and then add a default route to the Internet. The configuration details can be found in Table 15.11.
-
(f)
Network management configuration.
Telnet remote management is applied in this case, and the authentication mode is AAA. On the managed device, you need to create users, set passwords and configure to allow users for Telnet login. In addition, user privilege levels are set. The configuration details can be found in Table 15.12.
-
(g)
Configure the network egress.
In this case, the port of the core layer router CORE-R1 connecting to the Internet uses PPPoE dial-up to obtain the public address. The public address obtained by each dial-up is not fixed, so easy IP should be selected for NAT. See Table 15.13 for configuration details.
-
(h)
Configure the WLAN.
You only need follow the WLAN design and planning content to configure.
-
(i)
Configure network security.
Network security in this case involves three aspects: traffic control, network management security and DHCP security. We can use different security measures in different devices. Traffic control can be enabled by creating basic ACLs and advanced ACLs on the core layer router CORE-R1. Network security management requires creating ACLs on each managed device to allow only specified IP addresses to remotely manage, and creating different users and setting strict privilege levels for different operators. DHCP security needs to be configured on the access layer switch, and the configured uplink port is the Trusted port. See Table 15.14 for the configuration details.
-
(a)
-
2.
Network testing
After the network is configured, connectivity test, high reliability capability test and service performance test should be conducted.
-
(a)
The connectivity test includes basic link interconnection test, Layer 2 interconnection test, and Layer 3 interconnection test.
-
(b)
High reliability test includes loop avoidance function test and path switching test.
-
(c)
Service performance testing includes service traffic testing and access control testing.
-
(a)
15.3.4 Operation and Maintenance of Small Campus Networks
After the project goes online and runs, it enters the operation and maintenance phase of the network.
Network device operation and maintenance is a daily preventive work. It refers to the regular inspection and maintenance of the equipment in the normal operation of the equipment in order to timely detect and eliminate defects or hidden dangers to maintain the health of the equipment, so that the system can operate safely, stably and reliably for a long time.
-
1.
Environmental requirements of the server room
Under normal circumstances, the temperature of the long-term working environment of the server room should be kept between 0 °C and 45 °C, and the temperature of the short-term working environment should be between −5 °C and 55 °C. If the temperature of the server room fails to meet the requirements in the long term, the maintenance personnel should consider overhauling or replacing the air-conditioning system of the server room, checking the cooling situation of air conditioners, the switch situation, etc. The air-conditioning refrigeration should function normally and the switch should be in good contact.
Under normal circumstances, the relative humidity (RH) of the long-term working environment of the server room should be kept between 10% RH and 95% RH, and the relative humidity of short-term working environment should be between 5% RH and 95% RH. If the relative humidity of the server room becomes excessive, the maintenance personnel should consider installing dehumidification equipment for the server room; if the server room is too dry, the maintenance personnel should consider installing humidification equipment for the server room.
-
2.
Network equipment hardware maintenance requirements
-
(a)
The cleaning condition.
All equipment should be clean and tidy, with no obvious dust attached. Equipment shells, the inside of the equipment, and the inside of the rack have to be equipped with a dust net. Pay attention to the cleaning condition of the dust net of the cabinet, which should be timely cleaned or replaced, so as not to affect ventilation and heat dissipation of cabinet door and fan frame.
-
(b)
Heat dissipation condition.
When the equipment is working normally, it is required to keep the fan running (except during the cleaning of the fan). Turning off the fan without permission will cause the temperature of the equipment to rise and may damage the single board. It is not allowed to place sundris on the equipment shelves at the vents, and the fan’s dust net should be cleaned on a regular basis.
-
(c)
Cable laying.
Power cables and service cables are required to be laid separately. Power cables and service cables should be placed in a neat and orderly manner.
-
(d)
Cable labeling.
Pay attention to the cable labels inside the cabinet, which are required to be clear and accurate, and in line with the specifications.
-
(e)
Equipment appearance.
Observe whether the equipment is complete, and whether the free slot is protected by a dummy panel.
-
(a)
-
3.
Network equipment alarms and data configuration maintenance requirements
-
(a)
Alarm information.
Under normal circumstances, there should be no alarm information. If there is an alarm, it needs to be records, and serious alarms need to be immediately analyzed and dealt with.
-
(b)
Log information.
Under normal circumstances, there should not be excessive duplicate information in the logs. If there is, it must be immediately analyzed and dealt with.
-
(c)
CPU occupancy status.
Under normal circumstances, the CPU occupancy should be less than 80%. If the CPU occupancy rate is too high for a long time, the device should be checked and the cause analyzed.
-
(d)
Memory occupancy.
Under normal circumstances, the occupancy rate of memory should be lower than 80%. If the occupancy rate is too high for a long time, the equipment should be checked and the cause determined.
-
(e)
Interface traffic.
Compare the current traffic with the interface bandwidth. If the utilization rate exceeds 80% of the port bandwidth, it needs to be recorded and confirmed. Check whether there are error statistics in the inbound and outbound directions of the interface, focusing on the growth of error statistics.
-
(f)
Interface and link status.
The status of interfaces and links in use is UP, and that of unused interfaces is SHUTDOWN.
-
(g)
Debug switch.
Check whether the switch of the current debugging information “debugging” is off. Under normal operating conditions, all switches of all debugging information are off.
-
(h)
Configuration file.
Check whether the current configuration information and the saved configuration information are consistent. The configuration being run needs to be the same as the configuration saved.
-
(i)
Remaining capacity of Flash.
All the files in Flash must be useful, otherwise the delete/unreserved command should be executed to delete them.
-
(j)
Administration level user control.
The system must set a password for the administration level user, and the password is required to be set in the cipher text format and longer than six digits.
-
(k)
Telnet login control.
Telnet users must be authenticated. The password must be in cipher text format and cannot be too simple.
-
(l)
Telnet and serial login.
Telnet and serial login are tested to ensure that users can login by both of the two methods.
-
(m)
Change the user password.
For system security, the user password of the device must be changed on a regular basis. Moreover, the password must be set in the cipher text format and longer than six digits. The password is recommended to be updated every quarter.
-
(n)
Interface configuration.
Check the status and the configuration of the interface. The interface whose status is DOWN (except SHUTDOWN) is not allowed to have configuration, and the interface whose status is UP must have configuration.
-
(o)
Interface description.
All activated interfaces are described using the specification. If there is no corresponding specification, it is recommended that the interface description specification be: Local device name_Local port number - >Peer device name_Peer port number_Port rate.
-
(p)
Interface mode.
Execute the display interface command to check the configuration of the interface. The local interface mode (including rate and duplex mode) must be consistent with the peer interface mode. The actual operating mode (Trunk or Access) of the local interface must be the same as that of the peer interface.
-
(q)
System time.
Execute the display clock command to query the system date and time. The time should be consistent with the actual local time (the time difference is no more than 5 min).
-
(a)
15.3.5 Network Optimization of Small Campus Networks
If there are changes in network requirements, a suitable optimization plan needs to be formulated with the actual situation taken into consideration. For example, in this case, the control and security requirements for guests accessing the Internet in the reception center have increased, and bandwidth restrictions are imposed on each guest accessing the Internet, so it is necessary to deploy firewall devices at the egress layer to set security policies and bandwidth restriction policies. Another example is that the number of guests in the reception center has increased, and the performance of the core layer device CORE-R1 is not satisfied, so it is necessary to upgrade the device.
Through network optimization, the overall security and reliability of the network can be improved to better support the development of enterprise services. Common optimization solutions include, but are not limited to, the following.
-
Device performance optimization, for example, upgrading hardware devices, replacing existing devices with higher performance devices, and updating the software versions of the devices.
-
Network infrastructure optimization, for example, network architecture optimization and routing protocol adjustment. Other examples of network architecture optimization include the shift from single-link to dual-link Internet access, and the adjustment of WLAN data forwarding method from direct forwarding to tunnel forwarding. Moreover, changing the static routes to dynamic routes on the intranet is a routing protocol adjustment.
-
Service quality optimization, for example, reserving higher bandwidth for specific guests to the Internet, or prioritizing traffic forwarding for voice and video services.
15.4 Exercises
-
1.
What is the complete life cycle of a campus network?
-
2.
What is the role of managed addresses?
Author information
Authors and Affiliations
Consortia
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License (http://creativecommons.org/licenses/by-nc-nd/4.0/), which permits any noncommercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if you modified the licensed material. You do not have permission under this license to share adapted material derived from this chapter or parts of it.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Copyright information
© 2023 The Author(s)
About this chapter
Cite this chapter
Huawei Technologies Co., Ltd.. (2023). Typical Networking Architectures for Campus Networks and Case Practice. In: Data Communications and Network Technologies. Springer, Singapore. https://doi.org/10.1007/978-981-19-3029-4_15
Download citation
DOI: https://doi.org/10.1007/978-981-19-3029-4_15
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-3028-7
Online ISBN: 978-981-19-3029-4
eBook Packages: Computer ScienceComputer Science (R0)