Abstract
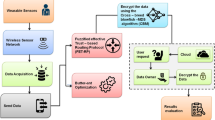
With rapid and successful advancement in communication technology and semiconductor devices Internet of Things based smart healthcare is not a concept, but reality. Patients’ vital information sensed by sensing devices is transmitted through heterogeneous communication links to fog/cloud layer for processing, storage, and decision-making or knowledge extraction. Sensitive health data is vulnerable to various security attacks and threats of different levels and impact while getting sensed, are saved or getting transmitted. Off-the-shelf security techniques such as encryption, trust can be applied for privacy and security of data but application-specific demands such as latency/end to end delay in data transmission, additional overhead in terms of computation time, etc., must be taken care of, especially in time-critical healthcare application. This work implements encryption-decryption algorithms and hashing techniques on ECG signals of varying size for secure transmission through communication layer to cloud layer for performance evaluation based on computation time (as in healthcare maximum permissible end to end delay is 250 ms) to ensure Confidentiality, Integrity, and Authentication.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Zanella, A., Bui, N., Castellani, A., Vangelista, L., Zorzi, M.: Internet of things for smart cities. IEEE Internet Things J. 1(1), 22–32 (2014)
Zhang, K., Ni, J., Yang, K., Liang, X., Ren, J., Shen, X.S.: Security and privacy in smart city applications: challenges and solutions. IEEE Commun. Mag. 55(1), 122–129 (2017)
Singh, M.M., Singh, A., Mandal, J.K.: Preventing node replication attack in static wireless sensor netwroks. In: Proceedings of 3rd International Conference on Reliability, Infocom Technologies and Optimization, Noida, pp. 1–5 (2014)
Saif, S., Gupta, R., Biswas, S.: Implementation of cloud-assisted secure data transmission in WBAN for healthcare monitoring. In: Bhattacharyya, S., Chaki, N., Konar, D., Chakraborty, U., Singh, C. (eds.) Advanced Computational and Communication Paradigms. Advances in Intelligent Systems and Computing, vol. 706. Springer, Singapore (2018)
Patil, P., Narayankar, P., Narayan, D., Meena, S.: A comprehensive evaluation of cryptographic algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Comput. Sci. 78, 617–624 (2016)
He, D., Ye, R., Chan, S., Guizani, M., Xu, Y.: Privacy in the internet of things for smart healthcare. IEEE Commun. Mag. (2018)
Ben Ida, I., Jemai, A., Loukil, A.: A survey on security of IoT in the context of eHealth and clouds. In: IEEE 2016 11th International Design and Test Symposium (IDT) (2016)
Baker, S.B., Xiang, W., Atkins, I.: Internet of things for smart healthcare: technologies, challenges, and opportunities. IEEE Access 5, 26521–26544 (2017). Electronic ISSN: 2169-3536
Elhoseny, M., Ramírez-González, G., Abu-Elnasr, O.M., Shawkat, S.A., Arunkumar, N., Farouk, A.: Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 6, 20596–20608 (2018)
Yin, L., Zhang, A., Ye, X., Wang, L.: Security-aware attribute-based access control for fog-based eldercare system. In: 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, pp. 2680–2684 (2017)
Al Hamid, H.A., Rahman, S.M.M., Hossain, M.S., Almogren, A., Alamri, A.: A security model for preserving the privacy of medical big data in a healthcare cloud using a fog computing facility with pairing-based cryptography. IEEE Access 5, 22313–22328 (2017)
Alrawais, A., Alhothaily, A., Hu, C., Xing, X., Cheng, X.: An attribute-based encryption scheme to secure fog communications. IEEE Access 5, 9131–9138 (2017)
Diro, A.A., Chilamkurti, N., Nam, Y.: Analysis of lightweight encryption scheme for fog-to-things communication. IEEE Access 6, 26820–26830 (2018)
Zheng, Q., Wang, X., Khurram Khan, M., Zhang, W., Gupta, B.B., Guo, W.: A lightweight authenticated encryption scheme based on chaotic SCML for railway cloud service. IEEE Access 6, 711–722 (2018)
Abdallah, E.G., Zulkernine, M., Gu, Y.X., Liem, C.: TRUST-CAP: a trust model for cloud-based applications. In: 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Turin, pp. 584–589 (2017)
Chen, R., Mu, Y., Yang, G., Gao, F., Huang, X., Wang, X., Wang, Y.: Server-aided public key encryption with keyword search. IEEE Trans. Inf. Forensics Secur. 11(12), 2833–2842 (2016)
Kao, Y.W., Huang, K.Y., Gu, H.Z., Yuan, S.M.: uCloud: a user-centric key management scheme for cloud data protection. IET Inf. Secur. 7(2), 144–154 (2013)
Shen, J., Liu, D., He, D., Huang, X., Xiang, Y.: Algebraic signatures-based data integrity auditing for efficient data dynamics in cloud computing. IEEE Trans. Sustain. Comput. (2017)
Kim, H., Lee, E.A.: Authentication and authorization for the internet of things. IT Professional 19(5), 27–33 (2017)
Movassaghi, S., Abolhasan, M., Lipman, J., Smith, D., Jamalipour, A.: Wireless body area networks: a survey. IEEE Commun. Surv. Tutor. 16(3), 1658–1686 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Saif, S., Biswas, S. (2020). On the Implementation and Performance Evaluation of Security Algorithms for Healthcare. In: Kundu, S., Acharya, U.S., De, C.K., Mukherjee, S. (eds) Proceedings of the 2nd International Conference on Communication, Devices and Computing. ICCDC 2019. Lecture Notes in Electrical Engineering, vol 602. Springer, Singapore. https://doi.org/10.1007/978-981-15-0829-5_59
Download citation
DOI: https://doi.org/10.1007/978-981-15-0829-5_59
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-0828-8
Online ISBN: 978-981-15-0829-5
eBook Packages: Physics and AstronomyPhysics and Astronomy (R0)