Abstract
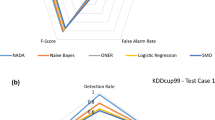
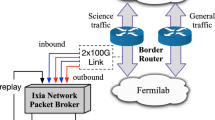
In network intrusion detection research, two characteristics are generally considered vital to build efficient intrusion detection systems (IDSs) namely, optimal feature selection technique and robust classification schemes. However, an emergence of sophisticated network attacks and the advent of big data concepts in anomaly detection domain require the need to address two more significant aspects. They are concerned with employing appropriate big data computing framework and utilizing contemporary dataset to deal with ongoing advancements. Based on this need, we present a comprehensive approach to build an efficient IDS with the aim to strengthen academic anomaly detection research in real-world operational environments. The proposed system is a representative of the following four characteristics: It (i) performs optimal feature selection using branch-and-bound algorithm; (ii) employs logistic regression for classification; (iii) introduces bulk synchronous parallel processing to handle computational requirements of large-scale networks; and (iv) utilizes real-time contemporary dataset named ISCX-UNB to validate its efficacy.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Buczak, A.L., Guven, E.: A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutorials 18(2), 1153–1176 (2016)
Suthaharan, S.: Big data classification: Problems and challenges in network intrusion prediction with machine learning. ACM SIGMETRICS Perform. Eval. Rev. 41(4), 70–73 (2014)
Grahn, K., Westerlund, M., Pulkkis, G.: Analytics for network security: a survey and taxonomy. In: Information Fusion for Cyber-Security Analytics, pp. 175–193. Springer (2017)
Manzoor, M.A., Morgan, Y.: Network intrusion detection system using apache storm. Adv. Sci. Technol. Eng. Syst. J. 2(3), 812–818 (2017)
Rathore, M.M., Ahmad, A., Paul, A.: Real time intrusion detection system for ultra-high-speed big data environments. J. Supercomputing 72(9), 3489–3510 (2016)
Anderson, J.P.: Computer security threat monitoring and surveillance. vol. 17. Technical report, James P. Anderson Company, Fort Washington, Pennsylvania (1980)
Shiravi, A., et al.: Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur. 31(3), 357–374 (2012)
Liu, H.: Instance Selection and Construction for Data Mining (2010)
Hosmer Jr., D.W., Lemeshow, S., Sturdivant, R.X.: Applied Logistic Regression, vol. 398. Wiley, New York (2013)
Sokolova, M., Lapalme, G.: A systematic analysis of performance measures for classification tasks. Inf. Process. Manag. 45(4), 427–437 (2009)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Siddique, K., Akhtar, Z., Kim, Y. (2018). Intrusion Detection in High-Speed Big Data Networks: A Comprehensive Approach. In: Park, J., Loia, V., Yi, G., Sung, Y. (eds) Advances in Computer Science and Ubiquitous Computing. CUTE CSA 2017 2017. Lecture Notes in Electrical Engineering, vol 474. Springer, Singapore. https://doi.org/10.1007/978-981-10-7605-3_217
Download citation
DOI: https://doi.org/10.1007/978-981-10-7605-3_217
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-7604-6
Online ISBN: 978-981-10-7605-3
eBook Packages: EngineeringEngineering (R0)