Abstract
As security protocols are used to authenticate more transactions, they end up being relied on in legal proceedings. Designers often fail to anticipate this. Here we show how the EMV protocol – the dominant card payment system worldwide – does not produce adequate evidence for resolving disputes. We propose five principles for designing systems to produce robust evidence. We apply these principles to other systems such as Bitcoin, electronic banking and phone payment apps. We finally propose specific modifications to EMV that could allow disputes to be resolved more efficiently and fairly.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
References
Aldrick, P.: Former Lloyds head of fraud and security Jessica Harper charged over
 2.5m fraud. The Telegraph (May 2012), http://www.telegraph.co.uk/finance/financial-crime/9289673/Former-Lloyds-head-of-fraud-and-security-Jessica-Harper-charged-over-2.5m-fraud.html
2.5m fraud. The Telegraph (May 2012), http://www.telegraph.co.uk/finance/financial-crime/9289673/Former-Lloyds-head-of-fraud-and-security-Jessica-Harper-charged-over-2.5m-fraud.html
Anderson, R.: On the security of digital tachographs. In: Quisquater, J.-J., Deswarte, Y., Meadows, C., Gollmann, D. (eds.) ESORICS 1998. LNCS, vol. 1485, pp. 111–125. Springer, Heidelberg (1998)
Anderson, R.: Offender tagging. Light Blue Touchpaper, September 2013. http://www.lightbluetouchpaper.org/2013/09/02/offender-tagging/
Anderson, R., Bond, M., Murdoch, S.J.: Chip and spin. Comput. Secur. J. 22(2) (2006). http://www.chipandspin.co.uk/spin.pdf
ARM: Building a secure system using TrustZone technology, April 2009. http://infocenter.arm.com/help/topic/com.arm.doc.prd29-genc-009492c/PRD29-GENC-009492C_trustzone_security_whitepaper.pdf
Bellare, M., Yee, B.: Forward-security in private-key cryptography. In: Joye, M. (ed.) CT-RSA 2003. LNCS, vol. 2612, pp. 1–18. Springer, Heidelberg (2003)
Bond, M., Choudary, O., Murdoch, S.J., Skorobogatov, S., Anderson, R.: Chip and skim: cloning EMV cards with the pre-play attack. In: IEEE Symposium on Security and Privacy, San Jose, USA, May 2014
Clayton, R., Bond, M.: Experience using a low-cost FPGA design to crack DES keys. In: Kaliski Jr., B.S., Koç, Ç.K., Paar, C. (eds.) CHES 2002. LNCS, vol. 2523, pp. 579–592. Springer, Heidelberg (2003). http://www.cl.cam.ac.uk/rnc1/ descrack/DEScracker.pdf
Drimer, S., Murdoch, S.J.: Keep your enemies close: Distance bounding against smartcard relay attacks. In: USENIX Security Symposium, August 2007
EMVCo: About EMV. http://www.emvco.com/about_emv.aspx
EMVCo: EMV Specifications. http://www.emvco.com/specifications.aspx
Evans, T.: Barclays blamed me when
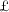 1,150 was stolen from my account - but its excuse was actually the bank’s own blunder. Daily Mail, June 2012. http://www.dailymail.co.uk/money/saving/article-2162199/Barclays-blamed-1-150-stolen-account.html
1,150 was stolen from my account - but its excuse was actually the bank’s own blunder. Daily Mail, June 2012. http://www.dailymail.co.uk/money/saving/article-2162199/Barclays-blamed-1-150-stolen-account.html
Kelman, A.: Job v Halifax PLC (not reported) case number 7BQ00307. In: Mason, S. (ed.) Digital Evidence and Electronic Signature Law Review, vol. 6 (2009)
Ma, D., Tsudik, G.: A new approach to secure logging. ACM Trans. Storage 5(1), 2:1–2:21 (2009)
MasterCard Worldwide: Progress against roadmap, http://www.mastercard.us/_assets/docs/MasterCard_EMV_Timeline.pdf
Meiklejohn, S., Pomarole, M., Jordan, G., Levchenko, K., McCoy, D., Voelker, G.M., Savage, S.: A fistful of bitcoins: characterizing payments among men with no names. In: Internet Measurement Conference, pp. 127–140. ACM (2013)
Mitchell, A.: Indian call center fraud case highlights need for change. E-Commerce Times, April 2005. http://www.ecommercetimes.com/story/42112.html
Möser, M., Böhme, R., Breuker, D.: An inquiry into money laundering tools in the Bitcoin ecosystem. In: Proceedings of the APWG eCrime Researchers Summit (ECRIME 2013), San Francisco, USA (2013)
Murdoch, S.J., Drimer, S., Anderson, R., Bond, M.: Chip and PIN is broken. In: IEEE Symposium on Security and Privacy, pp. 433–446, May 2010
Sellami, S.: L’imparable escroquerie à la carte bancaire. Le Parisien, January 2012. http://www.leparisien.fr/faits-divers/l-imparable-escroquerie-a-la-carte-bancaire-24-01-2012-1826971.php
Visa: Presentation at ATM Security, London, UK, October 2008
Xu, R., Saïdi, H., Anderson, R.: Aurasium: Practical policy enforcement for Android applications. In: USENIX Security Symposium, Bellevue, WA, USA, August 2012
Acknowledgements
Steven Murdoch is funded through a Royal Society University Research Fellowship.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 International Financial Cryptography Association
About this paper
Cite this paper
Murdoch, S.J., Anderson, R. (2014). Security Protocols and Evidence: Where Many Payment Systems Fail. In: Christin, N., Safavi-Naini, R. (eds) Financial Cryptography and Data Security. FC 2014. Lecture Notes in Computer Science(), vol 8437. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-45472-5_2
Download citation
DOI: https://doi.org/10.1007/978-3-662-45472-5_2
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-45471-8
Online ISBN: 978-3-662-45472-5
eBook Packages: Computer ScienceComputer Science (R0)


 2.5m fraud. The Telegraph (May 2012),
2.5m fraud. The Telegraph (May 2012), 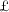 1,150 was stolen from my account - but its excuse was actually the bank’s own blunder. Daily Mail, June 2012.
1,150 was stolen from my account - but its excuse was actually the bank’s own blunder. Daily Mail, June 2012.