Abstract
In this paper, we cope with malicious nodes dropping packets to disrupt the well-functioning of mobiles ad hoc networks tasks. We propose a new hybrid acknowledgment punishment scheme based on Dempster Shafer theory, called HAPS. The proposed scheme incorporates three interactive modules. The monitor module monitors the behaviour of one-hop nodes in the data forwarding process. The reputation module assesses the direct and the indirect reputation of nodes using Dempster Shafer theory, which is a mathematical method, that can aggregate multiple recommendations shared by independent sources, while some of these recommendations might be unreliable. Since recommendations exchange between nodes consumes resources, a novel recommendation algorithm has been incorporated to deal with false dissemination attack and to minimize the recommendation traffic. The exclusion module punishes nodes regarded as malicious. The simulation results show that HAPS improves the throughput and reduces the malicious dropping ratio in comparison to existing acknowledgment scheme.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Mobile ad hoc network (MANET) is a collection of wireless mobile nodes that are able to perform the network tasks without requiring a fixed infrastructure or centralized administration. The communication between nodes follows a multi-hop approach. This approach depends on the assumption that all mobile nodes cooperate. Nevertheless, this assumption cannot be ensured due to the MANET features including the distributed nature, resource constraint of nodes [1]. These features make MANET vulnerable to selfish and malicious nodes. Selfish nodes may refuse to relay packets for other nodes to preserve their resources. On the other hand, malicious nodes may drop all packets passing through them in order to disrupt the functioning of the network’s activities. Therefore, to improve the network performance, it is critical to cope against the selfish and malicious behavior.
In the literature, one can categorize two types of related works dealing with selfish and malicious nodes dropping packets: credit-based schemes [3,4,5,6,7] and reputation-based schemes [2, 5, 8,9,10, 12, 13, 18,19,20,21, 24]. The goal of incentive-based schemes consists of encouraging nodes to relay packets for the benefits of other nodes by using credit. Node earns credits by relaying packets for other nodes and loses credits to send their packets. In the reputation-based schemes, each node monitors its one-hop nodes and computes their reputation values according to their behaviour. Almost of the reputation-based schemes use the watchdog technique [2] for the monitoring. However, this technique presents several feebleness as reported in [2, 11]. To deal with this feebleness, the acknowledgment technique is proposed in [12]. This technique permits to expand the range of neighbours monitoring to the two-hop by introducing a new kind of packet called TWOACK packet.
One of the recent scheme employing the acknowledgment technique is EAACK scheme [13]. EAACK can detect and punish malicious links. EAACK can effectively resolve some feebleness of the watchdog technique. However, EAACK is still vulnerable to other threats. (1) When nodes move faster, their neighbourhoods change often and therefore, malicious nodes have a several chances to drop more packets. Because, each new neighbour for malicious node forms a potential malicious link. This threat is inherited from TWOACK scheme [12], since TWOACK scheme can detect only malicious links and EAACK is based on TWOACK. (2) All requests initiated by malicious nodes are still relayed because the purpose is to relive malicious nodes from relaying data packets instead of punishing them.
To address the above threats, we propose a hybrid acknowledgment punishment scheme based on Dempster Shafer theory [14, 15, 23], called HAPS. HAPS scheme aims to enhance the performance of EAACK [13] by punishing malicious nodes more severely. HAPS is structured around three interactive modules: monitor, reputation, exclusion. The monitor module monitors the behavior of one-hop nodes in the data forwarding process. The reputation module computes the direct and indirect reputation values of neighbour nodes based on the information provided by the monitor module and the recommendations shared between nodes. We propose a new combination algorithm based on Demspter Shafer theory [14, 15] to compute the direct reputation value of the node. Thus, HAPS enables nodes to share their recommendations about other nodes, but only when it is necessary, and the combination of different recommendations is done based on Dempster Shafer Theory. The exclusion module punishes all nodes having reputation values smaller than the reputation threshold.
The remainder of this paper is organized as follows. In the Sect. 2, We present some preliminaries on Dempster Shafer Theory. Section 3 is devoted to the adversarial model. In Sect. 4, we present our proposed scheme (HAPS). In Sect. 5, we examine the performance of HAPS via simulation and finally conclude the paper.
2 Preliminaries on Dempster-Shafer Theory
Dempster Shafer theory of evidence [14, 15] is a mathematical method, handling the uncertainty and the subjective judgment. This method is especially efficient in situation when there is a need to aggregate multiple evidences shared by independent sources while some shared evidences might be unreliable, imprecise or incomplete/ambiguous. Let \(\varphi = \{A_{1},..,A_{n}\}\) be a finite set of mutually exclusive and exhaustive hypotheses denoted as the frame of discernment, where \(A_i\) are the individual hypotheses [22]. \(2_{}^{\varphi }\) denotes the possible subsets (or power set) of \(\varphi \). In this section, we outline some basic concepts of Dempster Shafer theory.
Definition 1
[15]: A basic probability assignment function (BPA) or a mass function m is a function that assigns to each subset of \(\phi \) a quantity of belief which is a number between 0 and 1. m is defined from \(2_{}^{\varphi } \rightarrow [0,1]\) and satisfying the following two constraints:
Definition 2
[15]: Let \(m:2^{\varphi }\rightarrow [0,1]\) be a mass function. The belief function \(bel:2^{\varphi }\rightarrow [0,1]\) related to the mass function m over \(\varphi \) is defined as follows
bel(A) corresponds to the total of belief given to the hypotheses A.
Definition 3
[15]: Dempster’s rule of combination permits to combine independent evidences issued from independent sources by applying the orthogonal sum \(\bigoplus \). Given two mass functions \(m_1\) and \(m_2\) over the same frame of discernment \(\varphi \). According to the Dempster’s rule of combination, \(m_1\) and \(m_2\) can be combined into a new mass function \(m:2^{\varphi }\rightarrow [0,1]\) as follows:
Where \(K_{12}=\sum _{A_i\cap B_j=\emptyset }{m_1\left( A_i\right) m_2(B_j)}\). \(m\left( c\right) \) represents the mass function of the combined evidence and \(K_{12}\) reflects the amount of conflicts between \(m_1\) and \(m_2\).
According to the Dempster’s rule of combination, we can combine n evidences as follows:
Where \(K=\sum _{C_1\cap \dots \cap C_n=\emptyset }{m_1\left( C_1\right) m_2\left( C_2\right) \dots m_n(C_n)}<1\).
3 Adversarial Model
According to their purposes, nodes may behave maliciously in order to degrade the network performance. In our paper, we suppose that malicious nodes may launch: (1) Black hole attack by dropping all data packets passing through them. (2) False dissemination attack by sharing fake recommendation to falsely improve or degrade the reputation value of the malicious or honest node, respectively.
4 The Proposed HAPS Scheme
HAPS scheme is structured around three interactive modules: monitor, reputation, exclusion.
4.1 Monitor Module
This module monitors the behaviour of one-hop nodes in the data forwarding process. HAPS employ the monitoring technique proposed in the EAACK scheme [13]. EAACK scheme is the result of the combination of three modes: ACK, S-ACK and MRA. In this paper, we implement only ACK and S-ACK modes. In the ACK mode, the destination node should send back an ACK packet to the source node for every data packet received. The S-ACK mode is similar to the TWOACK scheme. In the S-ACK mode, a new kind of packet called S-ACK is used. Each node forwarding data packets should send an S-ACK packet to the two-hop node in the opposite direction of the forwarding path.
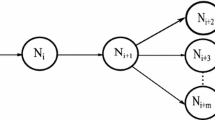
To illustrate the functioning of this technique, let \(p=\{N_{s},...,N_{i},N_{j},\) \(N_{k},...,N_{d}\}\) the selected forwarding path, \({<}N_{i},N_{j},N_{k}{>} \in p\) a triplet of nodes taken as an example (see Fig. 1). \(List_{ID}\) denotes the list of ID of data packets sent or forwarded waiting to be acknowledged. The source \(N_{s}\) sends data packets to the destination \(N_{d}\) through the path p. In the startup, the ACK mode is employed. In this mode, \(N_{s}\) adds the ID of each data packet sent D to \(List_{ID}\). Each ID is maintained for \(\theta \) second. Upon reception of D at \(N_{d}\), it should send back an ACK packet to \(N_{s}\). For each ACK packet relayed by all nodes \(N_{i}\in p\), the monitor module of \(N_{i}\) registers a good action through the link \((N_{j},N_{k})\). If \(N_{s}\) receives an ACK packet before \(\theta \) expires, which means that there are no malicious actions along the path p, it removes the ID of D from \(List_{ID}\). Otherwise, \(N_{s}\) switches to the S-ACK mode. \(N_{i}\) adds the ID of each data packet forwarded D to \(List_{ID}\). Each ID is maintained for \(\vartheta \) second. \(N_{j}\) Will forward D to \(N_{k}\) if it behaves cooperatively. Once the packet D reaches \(N_{k}\) , it should send back an S-ACK packet \(N_{i}\) if it does not behave maliciously. If \(N_{i}\) receives S-ACK packet before \(\vartheta \) expire, it deletes the ID of D from \(List_{ID}\) and registers a good action against the link \((N_{j},N_{k})\). Otherwise, if \(N_{i}\) does not receive S-ACK packet after \(\vartheta \) expires, \(N_{i}\) removes the ID of D from \(List_{ID}\) and registers a bad action against the link \((N_{j},N_{k})\). The same process is repeated for each triplet of nodes along p. This process is repeated until \(N_{s}\) receives a switch packet from \(N_{d}\), which means that p is a safer path. Therefore, \(N_{s}\) switches to the ACK mode.
4.2 Reputation Module
This module assesses and manages the reputation values of one-hop nodes. The reputation is classified into three types: direct, indirect and final. This module maintains four parameters ranging from 0 and 1: the reputation value of each monitored link \(\left( N_j,N_k\right) \in {}{FL}_i^j\) denoted by \(R_i\left( j,k\right) \) where \({FL}_i^j\) denotes the set of forwarding links in which \(N_j\) is involved, The direct, indirect and final reputation values denoted by \(DR_{i}^{j}(t)\), \(IR_{i}^{j}(t)\) and \(FR_{i}^{j}(t)\), respectively, where denotes the time of the computation of the reputation value.
Direct Reputation
A reputation is considered type direct, if it is computed based only on the recommendation of the monitor module. The reputation module of \(N_i\) evaluates the trustworthiness of \(N_j\) in all forwarding links \(\left( N_j,N_k\right) \in {FL}^j_i\) in which is involved (see Fig. 1). If the monitor module detects a good action, \(R_i\left( j,k\right) \) is increased. Otherwise, \(R_i\left( j,k\right) \) is decreased. To compute the direct reputation value \({DR}^j_i(t)\) of \(N_j\) at time slot t, we propose a combination algorithm based on Demspter Shafer theory [14, 15, 23]. This algorithm combines and aggregates the reputation values of all links \(R_i\left( j,k\right) ,\left( N_j,N_k\right) \in {FL}^j_i\) to come up to a single reputation value of \({N}_j\). The proposed algorithm functions as follows. In the startup, \(R_i\left( j,k\right) \) of each link \(\left( N_j,N_k\right) \in {FL}^j_i\) is initialized to \(neutral_v\) and it is updated according to the action detected by the monitor module. We consider two exclusive and exhaustive hypothesis that construct the frame of discernment \(\varphi =\{C,\overline{C}\}\) where C means that the node \(N_j\) is cooperative and \(\overline{C}\) means that the node \(N_j\) is uncooperative. The power set \(2^{\varphi }\) consists of four elements: \(\emptyset \), \(C=cooperative\), \(\overline{C}=uncooperative\) and hypothesis \(U= \varphi \) (\(N_j\) is either cooperative or uncooperative which represents the uncertainty). In this scenario, the reputation module of \(N_i\) perceives the reputation of each link \(\left( N_j,N_k\right) \in {FL}^j_i\) as recommendation provided by \(N_k\). The reputation module determines the state of the node \(N_{j}\) in the link (j, k) according to \({R}_i\left( j,k\right) \). If reputation module states that \(N_j\) is cooperative through the link (j, k), which means that \(R_i\left( j,k\right) \ge neutral_v\), The BPA of \(N_k\) is:
If reputation module states that \(N_j\) is uncooperative through the link (j, l), which means that \(R_i\left( j,k\right) <neutral_v\), the BPA of \(N_l\) is
The direct reputation value \({DR}^j_i(t)\) is computed by combining all recommendations collected from all links \(\left( N_j,N_k\right) \in {FL}^j_i\) by applying the Dempster rule of combination. \(neutral_v-R_i\left( j,l\right) \) value reflects the degree of maliciousness of the link (j, l). The rational of this algorithm is that: a malicious node should compromise multiple forwarding links (multiple forwarding paths) to achieve its purpose that consists on disrupting the data forwarding process. Therefore, it is involved in multiple bad actions that cause the degradation of its direct reputation value. On the other hand, an honest node is involved in more good actions than bad actions; therefore, it can improve its direct reputation value.
Indirect Reputation
A reputation is considered indirect, if it is computed based only on the recommendations shared between neighbours. In HAPS, this reputation is calculated and used only when there is need. The exchange method is done only when it is necessary, especially when a particular neighbour needs to send its packets. The goal is to improve the accuracy of the computation of nodes reputation and to minimize the recommendations traffics. When a node termed requestor needs to relay its packets through neighbours, all neighbours exchange their computed direct reputation values about this requestor. After that, they compute its indirect reputation value by aggregating all received recommendations using Dempster Shafer theory. Note that recommendations from nodes regarded as malicious are ignored.
When \(N_i\) receives a RREQ packet, it checks whether the requestor \(N_j\) is a neighbour \((N_j\in NG_i)\). If the requestor \(N_j\) is not neighbour, \(N_i\) simply forwards the RREQ packet. Else, \(N_i\) shares its recommendation about \(N_j\) in the neighbourhood and set the timer \({T}_r\). To prevent malicious nodes from colluding with other nodes or from manipulating the reputation values of some nodes, node \(N_i\) accepts only recommendation received before \(T_r\) expire. In order to compute the indirect reputation value of \({N}_j\), \(N_i\) aggregates all received recommendations using Dempster Shafer Theory. The recommendation of \(N_i\) about \(N_j\) is one among the set \(\{\)cooperative-uncooperative\(\}\). Therefore, the frame of discernment is \(\varphi =\{cooperative,uncooperative\}\). For instance, the reputation value of \(N_k\) at \(N_i\) is \({DR}^k_i(t)\). If \(N_k\) states that \(N_j\) is cooperative, the BPA of \(N_k\) is [16]:
If \(N_k\) claims that \(N_j\) is uncooperative, the BPA of \(N_k\) is:
The indirect reputation value of \(N_j\) is obtained after combining all recommendations using the Dempster’s rule of combination. According to Dempster Shafer Theory features, the relevance of a recommendation depends on the reputation value of the recommender, which permit to get a reliable reputation value. This feature make our approach resilient to false recommendation dissemination. Thus, our approach can cope with collusion attack that occurs when a group of malicious nodes provides fake recommendations about an honest node. Because, the time \(T_rec\) between the diffusion and the combination of recommendations is very low. Then, these nodes have not sufficient times to collude.
Illustration Example:
Let assume three nodes \(N_k, N_l~and~N_f\) with reputation values 0.4, 0.45 and 0.9 at \({N}_i\), respectively. They share their recommendations about \(N_j\). \(N_k\) claims that \(N_j\) is cooperative, \(N_{l}~and~N_f\) claims that \(N_j\) is uncooperative. Hence, the mass function are:
The reputation module of \(N_i\) combines \(m_k~and~m_l\) as follows:
The obtained \(m_{kl}\) is combined with \(m_f\) as:
From this result, the indirect reputation value \({IR}^j_i(t)\) of node \(N_j\) is 0.81.
Final reputation
After obtaining \({DR}^j_i\left( t\right) \) and \({IR}^j_i\left( t\right) \), the final reputation value \({FR}^j_i\left( t\right) \) is computed by combining \({DR}^j_i\left( t\right) \) and \({IR}^j_i\left( t\right) \) with the following equation:
Where \(\delta (0<\delta <1)\) determines the relevance of direct reputation compared to the indirect reputation.
4.3 Exclusion Module
The exclusion module is responsible for punishing malicious nodes. It considers a node having final reputation value smaller than the threshold as malicious. This module puts the detected node in its black list \(Black_{list}\), and it sends a misbehaving report to the source node of data packets to proceed to its punishment. All nodes forwarding, receiving or overhearing the misbehaving report put the detected node in their \(Black_{list}\) and proceed to its punishment. The punishment consists on: (1) invalidating all forwarding paths involving this node and evicting to route their data packets through this node. (2) Refusing to forward packets initiated from this node by discarding all its RREQ packets generated.
5 Performance Evaluation
In this section, we conduct a series of simulation experiments to examine the performance efficiency of the HAPS scheme using the network simulator NS-2.34. We evaluate the effectiveness of the HAPS scheme on the exclusion of malicious nodes dropping data packets in comparison to EAACK [13]. We simulate 40 mobile nodes deployed within an area of \(700*700\) m. The number of malicious nodes varies from 2 to 12. The rest of simulation parameters are shown in Table 1. The following two metrics are used to examine the efficiency of HAPS:
-
Average throughput (Kbps) represents the total size of data packets that successfully reached their destination over the simulation times.
-
Malicious dropping ratio refers to the ratio between the total numbers of data packets dropped by malicious nodes to the total numbers of data packets sent.
All plotted results are obtained after averaging the result of 20 simulation runs.
5.1 Average Throughput (Kbps)
Figure 2 shows the average throughput of HAPS and EAACK under varying the number of malicious nodes. We can observe that as the number of malicious nodes increases, the average throughput of two schemes decreases. However, the obtained results indicate that HAPS improves the average throughput much more than EAACK. This improvement is due to the fact that HAPS can identify and isolate malicious nodes instead of malicious links. Therefore, using HAPS scheme, the established paths between each pair of nodes is more reliable.
5.2 Malicious Dropping Ratio
Figure 3 depicts the malicious dropping ratio of HAPS and EAACK as a function of the number malicious nodes. The results show that the malicious dropping ratio increases as the number of malicious nodes increases. But, the malicious dropping ratio with HAPS increases more gently than with EAACK. This is because AASC penalizes malicious nodes more effectively and severely compared EAACK that is able to isolate only malicious links.
Figure 4 plots the malicious dropping ratio across varying the node speed. In this scenario, the network contains 4 malicious nodes. From this figure, we can observe that HAPS has a lower malicious dropping ratio in all cases compared to EAACK. This gap is more apparent when the nodes move faster. Because, when the nodes move faster, their neighbourhoods change frequently. As EAACK isolates only malicious links, each new neighbour for malicious nodes forms a new opportunity (malicious link) to drop more packets. Therefore, HAPS is more resilient to topology changes.
6 Conclusion and Future Work
In this paper, we have proposed HAPS, which is a novel acknowledgment Punishment Scheme aiming to detect and punish malicious nodes dropping data packets. In HAPS scheme, the reputation values of all links in which node is involved, are perceived as recommendations. Using Dempster Shafer Theory, these recommendations are combined to compute the reputation value of the node. HAPS incorporates a novel manner to exchange recommendations between nodes following the nature of on-demand routing protocol. The recommendations exchange is performed only when it is necessary and the aggregation is done based on Dempster Shafer Theory. HAPS punishes malicious nodes, whose the reputation values are smaller than the threshold by refusing to forward their packets, and isolating them from all network activities. The simulation results demonstrate that HAPS improves the throughput and reduces the malicious dropping ratio. As future work, We plan to evaluate mathematically the complexity of HAPS approach, and by simulation the effect of other network parameters in the effectiveness of HAPS approach (such Node density). We also plan to extend the HAPS scheme with an incentive mechanism aiming to cope against the selective packet dropping attack, while to motivate the cooperation of selfish nodes.
References
Peng, S.C., Wang, G.J., Hu, Z.W., Chen, J.P.: Survivability modeling and analysis on 3D mobile ad-hoc networks. J. Cent. South Univ. Technol. 18(4), 1144–1152 (2011)
Marti, S., Giuli, T.J., Lai, K., Baker, M.: Mitigating routing misbehavior in mobile ad hoc networks. In: Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, pp. 255–265 (2000)
Buttyan, L., Hubaux, J.P.: Stimulating cooperation in self-organizing mobile ad hoc networks. Mob. Netw. Appl. 8(5), 579–592 (2003)
Zong, C., Yang, S.: Sprite: a simple, cheat-proof, credit-based system for mobile ad-hoc networks. In: Twenty-Second Annual Joint Conference of the IEEE Computer and Communications (INFOCOM), pp. 1987–1997 (2003)
Bansal, S., Baker, M.: Observation-based cooperation enforcement in ad hoc networks. arXiv preprint cs/0307012 (2003)
Zhu, H., Lin, X., Lu, R., Fan, Y., Shen, X.: Smart: a secure multilayer credit-based incentive scheme for delay-tolerant networks. J. IEEE Trans. Veh. Technol. 58(8), 4628–4639 (2009)
Mahmoud, M.E., Shen, X.: FESCIM: fair, efficient, and secure cooperation incentive mechanism for multihop cellular networks. J. IEEE Trans. Mob. Comput. 11(5), 753–766 (2012)
Buchegger, S., Le Boudec, J.Y.: Performance analysis of the CONFIDANT protocol. In: Proceedings of the 3rd ACM International Symposium on Mobile Ad Hoc Networking and Computing, pp. 226–236 (2002)
Michiardi, P., Molva, R.: Core: a collaborative reputation mechanism to enforce node cooperation in mobile ad hoc networks. In: Jerman-Blažič, B., Klobučar, T. (eds.) Advanced Communications and Multimedia Security. IFIP AICT, vol. 100, pp. 107–121. Springer, Boston (2002). https://doi.org/10.1007/978-0-387-35612-9_9
He, Q., Wu, D., Khosla, P.: SORI: a secure and objective reputation-based incentive scheme for ad-hoc networks. In: Wireless Communications and Networking Conference (WCNC), pp. 825–830 (2004)
Yau, P.W., Mitchell, C.J.: Reputation methods for routing security for mobile ad hoc networks. In: Proceedings of the Mobile Future and Symposium on Trends in Communications, pp. 130–137 (2003)
Balakrishnan, K., Deng, J., Varshney, P.K.: TWOACK: preventing selfishness in mobile ad hoc networks. In: Wireless Communications and Networking, pp. 2137–2142 (2005)
Shakshuki, E.M., Kang, N., Sheltami, T.R.: EAACK—a secure intrusion-detection system for MANETs. IEEE Trans. Industr. Electron. 60(3), 1089–1098 (2013)
Shafer, G.A.: Mathematical Theory of Evidence. Princeton University Press, Princeton (1976)
Sudkamp, T.: The consistency of Dempster-Shafer updating. Int. J. Approx. Reason. 7(1), 19–44 (1992)
Chen, T.M., Venkataramanan, V.: Dempster-Shafer theory for intrusion detection in ad hoc networks. IEEE Internet Comput. 9(6), 35–41 (2005)
Johnson, D.B., Maltz, D.A.: Dynamic source routing in ad hoc wireless networks. In: Imielinski, T., Korth, H.F. (eds.) Mobile Computing. The Kluwer International Series in Engineering and Computer Science, vol. 353, pp. 153–181. Springer, Boston (1996). https://doi.org/10.1007/978-0-585-29603-6_5
Liu, K., Deng, J., Varshney, P.K., Balakrishnan, K.: An acknowledgment-based approach for the detection of routing misbehavior in MANETs. IEEE Trans. Mob. Comput. 6(5), 536–550 (2007)
Sheltami, T., Al-Roubaiey, A., Shakshuki, E., Mahmoud, A.: Video transmission enhancement in presence of misbehaving nodes in MANETs. Multimedia Syst. 15(5), 273–282 (2009)
Sun, H.M., Chen, C.H., Ku, Y.F.: A novel acknowledgment-based approach against collude attacks in MANET. Expert Syst. Appl. 39(9), 7968–7975 (2012)
Djahel, S., NaïtAbdesselam, F., Zhang, Z., Khokhar, A.: Defending against packet dropping attack in vehicular ad hoc networks. Secur. Commun. Netw. 1(3), 245–258 (2008)
Campos, F., Cavalcante, S.: An extended approach for Dempster-Shafer theory. In: Information Reuse and Integration, pp. 338–344 (2003)
Bloch, I.: Some aspects of Dempster-Shafer evidence theory for classification of multi-modality medical images considering partial volume effect. Pattern Recogn. Lett. 17(8), 905–919 (1996)
Bounouni, M., Bouallouche-Medjkoune, L.: A hybrid stimulation approach for coping against the malevolence and selfishness in mobile ad hoc network. Wirel. Pers. Commun. 88(2), 255–281 (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 IFIP International Federation for Information Processing
About this paper
Cite this paper
Bounouni, M., Bouallouche-Medjkoune, L. (2018). Hybrid Acknowledgment Punishment Scheme Based on Dempster-Shafer Theory for MANET. In: Amine, A., Mouhoub, M., Ait Mohamed, O., Djebbar, B. (eds) Computational Intelligence and Its Applications. CIIA 2018. IFIP Advances in Information and Communication Technology, vol 522. Springer, Cham. https://doi.org/10.1007/978-3-319-89743-1_38
Download citation
DOI: https://doi.org/10.1007/978-3-319-89743-1_38
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-89742-4
Online ISBN: 978-3-319-89743-1
eBook Packages: Computer ScienceComputer Science (R0)