Abstract
This Chapter presents a review of the quantum mechanical properties of spatially structured light fields, specifically those fields carrying orbital angular momentum (OAM). This review is concerned both with the conceptual understanding of the quantum features of these light fields and with the use of these features for applications. We describe how to produce spatially entangled light fields by means of the nonlinear optical process of parametric downconversion. We ask and provide a tentative answer to the question of how much information can be encoded into a single photon. As an example, we review a recent experiment that demonstrated the ability to discriminate among four target objects using only one photon for illumination. We also present a description of the concept of the OAM of light, and we describe means to generate and detect OAM. We then present a brief survey of some recent studies of the fundamental quantum properties of structured light beams. Much of this work is aimed at studying the nature of entanglement for the complementary variables of angular position and OAM. Finally, as a realworld application, we describe a secure communication system based on quantum key distribution (QKD). This key distribution system makes use of encoding information in the OAM modes of light and hence is able to transmit more than one bit of information per photon.
You have full access to this open access chapter, Download chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
1 Introduction
There is a growing appreciation of the importance of quantum mechanics and in particular of quantum information science both for understanding the nature of the world in which we live and in the development of new technologies for communication and imaging. It is in this spirit that this chapter is written. The chapter deals with structured light fields, especially fields that carry orbital angular momentum (OAM), and their application to communication systems.
The topic of structured light fields in the quantum domain is intimately related to the topic of quantum imaging [1]. Quantum imaging is a discipline that studies quantum aspects of image formation and that uses quantum properties of light to produce images. Imaging techniques inherently require the ability to encode massive amounts of information in a light field. The quantum aspects of optical images can therefore be a key resource for quantum information and communication systems.
In this chapter we will review several examples of the quantum properties of structured light field. In broad concept, there are two sorts of quantum states that appear in our examples. One sort is a “single-photon” state, a state in which it is known that there is one and only one photon present in the field of interest. Such a state shows strong quantum properties because, for example, if you send such a beam onto a beamsplitter, the photon will emerge in one of the two output ports but not half and half in both. The other sort of quantum state of interest in this chapter is an entangled state of two photons. In fact, the concept of entanglement is one of the great mysteries of quantum mechanics. The term entanglement and the first explicit description of this phenomenon were introduced by Schrödinger in 1935 [2]. Here is quote from his paper:
“When two systems, of which we know the states by their respective representatives, enter into temporary physical interaction due to known forces between them, and when after a time of mutual influence the systems separate again, then they can no longer be described in the same way as before, viz. by endowing each of them with a representative of its own. I would not call that one but rather the characteristic trait of quantum mechanics, the one that enforces its entire departure from classical lines of thought.”
This concept of entanglement leads to what today is often called “quantum weirdness,” a term that arises from the seemingly paradoxical effects that can occur in an entangled system. Entanglement has, for instance, played a key role in compelling laboratory demonstrations [3, 4] of the nonlocality of quantum phenomena. However, this weirdness has in fact turned into an asset. This entanglement weirdness leads to effects such as quantum teleportation and certain forms of quantum communication with guaranteed security. One of the easiest ways to produce quantum entanglement uses nonlinear optical methods, and it is these methods that therefore give the field of photonics a special and elevated position in the arena of quantum technologies.
The concept of entanglement generation as applied to light fields can be visualized using the drawing shown in Fig. 17.1. Here a laser beam at frequency ω p excites a second-order nonlinear optical crystal, whose nonlinear response can be characterized in terms of its second-order susceptibility χ (2). Occasionally, a pump photon can be absorbed and generates two lower-frequency photons of frequencies ω s and ω i , a process known as spontaneous parametric downconversion (SPDC) [5–7]. It can be shown that the rate at which photon pairs are created is proportional to the product [χ (2)]2 L 2 I p , where L is the length of the nonlinear crystal and I p is the intensity of the pump laser.
By conservation of energy, the condition \( {\omega}_p={\omega}_s+{\omega}_i \) must be satisfied, as illustrated in part (b) of the figure, furthermore these two new photons are generated at the same position (i.e., position correlated). However, photon momentum must also be conserved in this generation process, as illustrated in part (c) of the figure, and hence the two new photons are generated with opposite transverse momentum components (i.e., momentum anti correlated). It is these simultaneous conditions on position and momentum that lead to the paradox of Einstein et al. [8] and the concept of quantum entanglement [2].
The photons created by SPDC form entangled pairs, and in fact these photons can be entangled simultaneously in more than one pair of degrees of freedom. The possible types of entanglement that are often studied are
-
position and transverse momentum
-
angular position and orbital angular momentum
-
time and energy
-
polarization in different measurement bases.
Examples of the first two types of entanglement will be presented later in this chapter. Here we present a brief discussion of the other two types of entanglement.
By time-energy entanglement, one means that if one measures, for example, the energy of the signal photon, one is able to predict with certainty that the energy of the idler photon will be given by \( \hslash {\omega}_i=\hslash {\omega}_p-\hslash {\omega}_s. \) However, if one instead chooses to measure the moment of time at which the signal photon is emitted, one will always find that the idler photon is emitted at exactly the same moment. It seems that the product of uncertainty in tightness in the correlation of energies multiplied the uncertainty in the correlation of times can be arbitrarily small and certainly smaller than the value \( \frac{1}{2}\hslash \) that one might have envisaged from the naive application of uncertainty relations [9, 10]. The situation is the essence of entanglement: the resolution of this seeming paradox is that a measurement that one performs on the signal photon results in a restriction of our ability to predict the properties of the idler photon, even if that idler photon is arbitrarily distant from the signal photon measurement location. This nonlocality which applies to entangled systems leads to the phrase “spooky action at a distance.”
Polarization entanglement can be similarly described. Under certain circumstances [6], each of the photons emitted by SPDC will be unpolarized, that is a complete statistical mixture of two orthogonal polarization states. However, for any one particular measurement the polarization of the signal photon will be found to have a defined value; one says that the measurement process projects the polarization state unto one of the polarization eigenstates. Furthermore, one finds that the idler photon will always be projected onto a polarization state that is orthogonal to that of the first photon (due to the conservation of angular momentum in the down conversion process). This type of entanglement is conveniently described in terms of the Bell states, which have played a key role in the understanding of many of the conceptual foundations of quantum mechanics. Details can be found in the excellent textbook of Gerry and Knight [11].
(a) Schematic illustration of the process of spontaneous parametric downconversion (SPDC). A laser beam excites a second-order (χ (2)) nonlinear optical crystal, leading to the generation of pairs of photons conventionally known as signal and idler photons. This process must obey the conservation of both energy (b) and momentum (c). These conditions lead to quantum correlations known as entanglement between the signal and idler photons, as discussed further in the text
2 How Much Information Can One Photon Carry?
In classical optical telecommunication systems, many photons are required to transmit one bit of information. But it can be interesting to turn this question around and ask it differently: How much information can be carried by a single photon? Perhaps surprising to some is that research conducted over the last decade shows that there is no fundamental limit to the amount of information that can be carried by a single photon.
We start this section by giving a specific example of the ability to transfer many bits of information for each photon; this example will be developed in greater depth in the following sections. Laboratory procedures now exist for switching between single-photon states in any one of the Laguerre–Gaussian modes (Eq. (17.3)) of light using, for example, liquid crystal-based spatial light modulators [12] or a digital micromirror devices (DMD) [13]. It is crucial to recall that the Laguerre–Gaussian modes constitute an infinite set of basis functions. Thus, to the extent that one can perform OAM encoding and decoding with high efficiency, there is no limit to the amount of information that can be carried by a single photon.
Configuration of the “single-photon imaging” experiment of Broadbent et al. [14] described in the text. Part (a) shows the procedure for writing a multiplexed hologram, and part (b) shows the read-out stage, which operates at the single-photon level. The TCPSC is a time-correlated single-photon counter
The ability to encode more than one bit per photon is, of course, not restricted to the Laguerre–Gaussian light beams. More generally, the transverse degree of freedom of the light field offers a means to carry and manipulate quantum information. An example of multi-bit information transfer relating to imaging is provided in an experiment performed by Broadbent et al. [14]. A schematic of this experiment is shown in Fig. 17.2. Part (a) of the figure shows a multiplexed hologram of objects A and B. By saying that the hologram is multiplexed, we mean that different write-beam directions are used to form the interference fringes for each object. Part (b) of the figure shows the read-out stage. It makes use of entangled photons created by parametric downconversion in a BiBO crystal. One of these photons falls onto the trigger detector, which heralds the presence of the photon in the other arm. This photon falls onto an object in its arm, which could be either object A or B. This photon is diffracted from the hologram into the path of either detector A or B, depending on which object is placed in this arm. In this manner, one can determine with high reliability which object is located in this arm, even though only one photon is used to make this determination. Quantitative results are presented in the paper. It is shown that the likelihood of a misidentification (that is, for example, that the photon is detected by detector B when in fact object A is present) is less than 1 %.
Configuration of an experiment to demonstrate the discrimination among four different objects at the single-photon level, as described by Malik et al. [15]
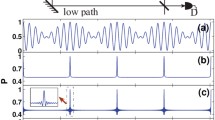
The experiment just described shows that one can discriminate between two objects using single-photon illumination. A subsequent experiment [15] demonstrated the ability to discriminate among four objects, again using only single-photon illumination. For this experiment a “quantum ghost-imaging” protocol [16] is used. The setup is shown schematically in Fig. 17.3. Spatially entangled photons are again created by the process of parametric downconversion. One of these photons illuminates one of the four test objects (only two are displayed in the diagram to avoid clutter) and the other falls onto a multiplexed hologram, where it is diffracted into one of four output ports. Coincidence events between the reference detector R and one of the detectors A, B, etc. are recorded. In this figure, DM denotes a dichroic mirror for blocking the pump laser and IF is an interference filter with a 10 nm bandwidth, centered at 727.6 nm.
The results of this experiment are shown in Fig. 17.4. Note that input object a produces counts predominantly in detector A, and similarly for the other three object-detector combinations. The data are displayed using two different normalization conventions. In part (a), data for each object-detector combination are normalized by the maximum coincidence count for the corresponding object. In part (b), the T/A ratio is calculated by dividing the total coincidences by the accidental coincidences for each object-detector combination. Part (c) of the figure shows the four test objects. These results show that one can reliably discriminate among four objects even when they are illuminated with weak light at a single photon level. However, in this experiment the detection efficiency was low, and thus more than one photon needed to illuminate the object in order to make an unambiguous determination. In fact, for the sort of simple, multiplexed hologram used in this experiment the maximum detection efficiency (that is, assuming lossless optical elements and unit quantum efficiency detectors) is equal to 1∕N (where N is the number of objects). However, there seems to be no reason in principle [17] why a hologram could not be designed to give a maximum detection efficiency of unity.
We note that this sort of ghost imaging relies upon correlations between photon pairs. If detector R registers a photon, we know with certainly that this photon possessed the transverse mode structure given by the transmission function of the object in its path. Since this detected photon is entangled with the photon in the other arm, this detected photon must therefore acquire the same conjugate mode structure, and thus be diffracted by the hologram into a specific output port.
3 Light Beams that Carry Orbital Angular Momentum
We turn now to another example of a structured light field, namely one carrying orbital angular momentum, which displays interesting quantum properties that can lead to important applications. First, we consider a light field of the form
Here u(x, y) is some function of the transverse coordinates x and y, ℓ is a positive or negative integer, \( k=\omega / c \) is the propagation constant, z is the longitudinal coordinate, and ω is the angular frequency. We assume propagation through vacuum. It is well known that such a field carries angular momentum of amount \( \ell \hslash \) per photon [18]. For this reason, ℓ is often referred to as the OAM quantum number or OAM mode index. This contribution to the angular momentum is referred to as orbital angular momentum (OAM), distinguishing it from spin angular momentum, which is associated with circular polarization of a light field. These two contributions are additive, and in the paraxial limit considered here independent of each other.
We can understand why the field given by Eq. (17.1) carries angular momentum with the help of the sketch in part (a) of Fig. 17.5. We see that such a field possesses a wavefront structure in the form of a helix, and that the phase at each point advances in the azimuthal direction at a rate proportional to the value of l. One might well imagine that a small particle placed in such a beam would experience a radiation pressure in the direction of phasefront normal and hence a force with an azimuthal component that induces the object to begin to rotate around the beam axis, and in fact this is just what has been observed experimentally [19, 20].
Two methods of producing a light beam that carries orbital angular momentum. (a ) The conceptually simplest way to form a beam carrying OAM is to pass a plane wave beam through a spiral phase plate, an optical element whose thickness increases linearly with the azimuthal angle. After transmission through such an element, a incident plane wave is transformed into a light beam with helical phasefronts. The height of the phase step controls the azimuthal index ℓ of the transmitted beam. (b ) Alternatively, one can replace the phase plate with its holographic equivalent with a phase or amplitude structure in the form of a pitchfork as shown. The first-order diffracted beam will have helical phasefronts with an azimuthal index given by the number of dislocations in the pitchfork. These holograms are conveniently created by using a spatial light modulator. (c ) Examples of some OAM beams produced by these approaches
Equation (17.1) shows that the a light field will carry OAM for any transverse mode function u(x, y). However, some specific mode functions are especially important in the utilization of structured light fields. One such example is that of the Laguerre–Gaussian modes, and we will now briefly explore their properties. The paraxial approximation to the wave equation \( \left({\nabla}^2-{\partial}^2 / \partial {t}^2\right)E\left(x,y,z\right)=0 \) gives us the paraxial wave equation, which is written in the cartesian coordinate system as
The paraxial wave equation is satisfied by the Laguerre–Gaussian modes, a family of orthogonal modes that have a well-defined orbital angular momentum. The field amplitude, in cylindrical coordinates, LG p l(ρ, ϕ, z) of a normalized Laguerre–Gaussian mode is given by
where k is the wave-vector magnitude of the field, z R the Rayleigh range, w(z) the radius of the beam at z, ℓ is the azimuthal quantum number, and p is the radial quantum number. L p l is the associated Laguerre polynomial.
Some methods for the production of beams that carry OAM are sketched in Fig. 17.5. The use of a spiral phase plate is shown in part (a) [19]. Another important method for generating OAM light beams (part b) is to impress a specially designed computer-generated hologram (CGH) taking the form of a forked diffraction grating [12, 20–23] or a digital micromirror device (DMD) [13]. If a beam with nearly plane wave fronts, such as a Gaussian laser beam, is made to fall onto such a CGH, the diffracted light will acquire the desired form of a beam carrying OAM. Another means to form beams carrying OAM is through the use of a device known as a q-plate [24, 25]. This device is a birefringent phase plate in which the orientation of the birefringent axes varies uniformly as a function of azimuthal position around the axis of the plate. Such a device acts as a spin angular momentum to OAM converter, that is, the OAM carried by the output beam depends on the polarization state of the input beam. A q-plate can thus serve as a quantum interface between polarization-encoded quantum light states and OAM-encoded quantum light states.
4 Fundamental Quantum Studies of Structured Light Beams
In Sect. 17.1 of this chapter we noted that the process of spontaneous parametric downconversion can lead to entanglement in several different degrees of freedom, including position-momentum [26], time-energy [9, 10], polarization [3, 4], and superpositions of OAM modes [27] or explicitly angle-OAM [28]. In this section we provide a brief account of work aimed at studying these various types of entanglement.
In Einstein, Podolski, and Rosen’s (EPR’s) classic paper [8], they argued against the completeness of quantum mechanics. Their argument was based on the situation of two particles that were strongly correlated both in position and momentum. Later, David Bohm [29] restated this argument in terms of two particles entangled in their spin (or polarization), and it was this spin-version of the EPR paradox that was treated by John Bell in devising his celebrated Bell inequalities. In the ensuing decades, most subsequent work [3, 4] has concentrated on the polarization of the EPR paradox. In 1990 Rarity and Tapster [30] extended the Bell violation to one based on measurement of phase and momentum. Howell et al. [26] later performed an experimental investigation in which they studied the original (i.e., Einstein et al. [8]) position-momentum version of the EPR paradox. Some of their results are summarized in Fig. 17.6. Their experimental procedure is as follows. Photons entangled in position and momentum were created by type-II parametric downconversion in a BBO nonlinear crystal, and the two photons were separated by a polarizing beamsplitter (PBS) and traveled over separate paths. Either the birthplace (i.e., position) of each photon or its transverse momentum could be determined by placing a slit followed by an area detector either in a focal plane of the crystal or in its far field, respectively. Coincidence counts between the two detectors were measured, and the conditional count rates associated with position and momentum are shown in the graphs on the right-hand side of the figure. The measured conditional uncertainty product is found to be \( {\left(\varDelta {x}_2\right)}_{x_1}{\left(\varDelta {p}_2\right)}_{p_1}=0.1\hslash \), which is ≈ five times smaller than which might be expected for the uncertainty principle as applied to independent particles.
Laboratory setups (left) and measured conditional count rates (right) for a laboratory demonstration of the EPR effect for position and transverse momentum variables. The notation P(x 2 | x 1) means that probability of measuring one photon at position x 1 conditioned on the other photon being detected at position x 1, and analogously for P( p 2 | p 1). The measured conditional uncertainty product is \( 0.1\hslash \), which violates the Heisenberg uncertainty relation for independent particles [26]
There has also been considerable interest in studies of time-energy entanglement. For example, Ali-Khan et al. [10] have developed a protocol for quantum key distribution (QKD) that can encode as much as ten bits of information onto a single photon. In a separate study, Jha et al. [10] have studied time-energy entanglement controlled by a geometrical (Berry) phase on the Poincare sphere instead of by using a dynamical phase. The ability to manipulate entanglement by means of a geometrical phase could have important consequences for quantum information technology, because polarization controllers can be much more stable than translation stages needed to actively control optical path lengths.
We next turn to a description of angle-OAM entanglement. We first note that angle and OAM form a Fourier transform pair [22, 31]:
where A ℓ is the amplitude a OAM state ℓ and where ψ(ϕ) represents the azimuthal dependence of the complex beam amplitude. One might well expect this result based on classical reasoning. However, Jha et al. [32] showed theoretically that a similar Fourier relation holds between the photons of an entangled photon pair produced by a down-conversion source. They also experimentally demonstrated the characteristic OAM sideband structure that this Fourier relationship implies (Fig. 17.7).
Laboratory setup (top) and conditional probability of detection (bottom) for a laboratory demonstration of the EPR effect for angular position and orbital angular momentum variables. The conditional uncertainty product is 0.024, which violates the Heisenberg uncertainty relation for independent particles [28]
(left) Laboratory setup to study angular two-photon interference and angular two-qubit states. In this experiment, an entangled two-photon state is created by parametric downconversion, and each photon falls onto a different aperture having the form of a double angular slit. The OAM content of each photon is then measured, and correlations between the two outputs are calculated. (right) Some of the results of this experiment. Here the coincident count rate is plotted as a function of the OAM of the signal photon for two different values of the OAM of the idler photon. The high visibility of the interference fringes is an indication of the high level of entanglement between the two photons [33]
In a related experiment, Jha et al. [33] studied the correlations between the OAM values of two entangled photons after each had passed through separated double-slit apertures. Strong, non-classical, correlations were observed in the resulting interference pattern. These authors also showed that under their experimental conditions the visibility of this interference pattern was numerically equal to the concurrence of the two-photon state, a measure of the degree of entanglement between the two photons. A measured visibility of between 85 and 92 % quantifies the nonclassical entanglement of the photons produced by their two-photon source.
In still another related experiment, Leach et al. [28] performed an experiment that is the direct analog of the Einstein–Podolsky–Rosen (EPR) gedankenexperiment, but in the angle-OAM degrees of freedom. Part of the motivation for this study is that, unlike the continuous and unbounded variables in position-momentum entanglement considered by EPR, angular position is a periodic variable leading to a discrete OAM spectrum. As such, the analysis of EPR for angles involves subtleties similar to the issue of the existence of photon-number photon-phase uncertainty relation [34]. The details of this experiment are presented in Fig. 17.8.
There has also been great recent interest in harnessing the radial modes of Laguerre–Gaussian (LG) beams in addition to the azimuthal modes that we have primarily discussed up to now. One reason for this interest is to increase the information capacity of a light beam of a given restricted diameter. We note that the LG modes of Eq. (17.3) depend on two indices, the azimuthal index ℓ and the radial index p. But there are also further subtleties involved in exploiting the radial distribution, related to the fact that the radial coordinate ρ ranges from 0 to \( \infty \), unlike the azimuthal coordinate ϕ, which ranges from 0 to 2π. Recently, Karimi et al. [35] presented a theoretical analysis of the operator nature of the radial degree of freedom. Moreover, Karimi et al. [36] have studied the dependence of Hong–Ou–Mandel interference on the transverse structure of the interfering photons.
5 Secure Quantum Communication with More than One Bit Per Photon
We now turn to an application for the OAM of light in the field of cryptography and secure communication. To put this application topic in context, we first review the use of a one-time pad in cryptography (Shannon [37]). We consider the situation in which one party, A (or Alice), wants to communicate securely to another party, B (or Bob). We assume that by pre-arrangement the two parties share the same string of random binary digits known as the key, that no one else has access to this key, and that this string of digits is at least as long as the message that Alice wants to send. Alice encodes her message by first placing it into a binary format and then performing a binary add of the i-th digit in her message with the i-th digit in the one-time pad. This encoded message is then sent over a public channel. It is provably true that this message contains no useful information except to someone who has possession of the secret key. Bob then decodes the message by performing a binary add with his copy of the key, thus obtaining the original message that Alice sent.
A difficulty with implementing the one-time pad method is the distribution of the secret key between Alice and Bob. This is especially difficult if the two parties are not and cannot be in the same place, where the key can simply be handed from one to the other. When not in the same place, a procedure proposed by Bennet and Brassard in 1984 (know as the BB-84 protocol) can be used to distribute the key in an entirely secure manner. In brief (some of the details are provided below), Alice sends the key one element at a time, and each digit is encoded in the quantum state of a single photon. If an eavesdropper (Eve) intercepts and measures this photon and then tried to send an exact replacement photon of it, she will certainly fail, because the laws of quantum mechanics prohibit her from determining full knowledge of the quantum state of a photon in a single measurement. The impossibility of doing so results from the celebrated “no-cloning” theorem of quantum mechanics [38]. Secure communication through use of the BB-84 protocol of quantum key distribution (QKD) is now a commercial reality (see, for example the website http://www.idquantique.com).
Work in which the present authors have participated involves extending the BB-84 protocol so that more than one bit of information can be carried by each photon. Such a procedure may be used to increase the secure bit rate of a quantum communication system. To achieve the goal of transmitting more than one bit per photon, we encode information in the transverse degree of freedom of the light field. For the transverse degree of freedom one can choose any complete set of orthonormal modes. In keeping with the context of this chapter we consider encoding in OAM modes such as Laguerre–Gaussian (LG) modes. In the original QKD proposal of Bennett and Brassard, information is encoded in the polarization degree of freedom of an individual photon. As a result, only one bit of information could be impressed onto each photon. In contrast, when using OAM, there is no limit to how many bits of information can be impressed onto a single photon, as the LG modes span an infinite-dimensional state space. As mentioned above, one motivation for doing this is that rate of data transmission is thereby increased. Another more subtle motivation is that the security of the protocol can be increased by encoding information within a higher-dimensional state space.
System schematic of the baseline QKD protocol of Mirhosseini et al. [41]. A sender (A or Alice) impresses information onto an individual photon through use of a spatial light modulator (SLM). This photon is then sent to the receiver (B or Bob) through a free-space link, where it may experience degradation by means of atmospheric turbulence. The receiver then determines the quantum state of this photon
The system that we envisage is illustrated in broad scope in Fig. 17.9. It consists of a sender, Alice, and a receiver, Bob. Alice impresses information onto the transverse degree of freedom of individual photons through the use of a spatial light modulator (SLM). Bob then randomly guesses which basis (OAM or angle) Alice might be using and makes a measurement of the quantum state of the received photon in this basis. The procedure for ensuring the security of the transmission is a generalization of that of the BB84 protocol and is described in the review of Gisin and Thew [39]. In the remainder of the present section we describe in more detail our laboratory procedure and present some laboratory data.
The LG basis (top) and a linear combination of the LG states (bottom) that constitutes the angular basis (AB). The information is encoded by launching individual photons that have been prepared in one of these modes [40]
The BB84 QKD protocol entails Alice sending each photon in a randomly chosen basis. At least two mutually unbiased bases (MUBs) must be used. Certain advantages accrue from using more than two MUBs. It is known that the maximum number B max of MUBs is related to the dimension D of the state space by \( {B}_{max}=D+1 \). In our laboratory investigations we use the minimum number of MUBs, B = 2. We choose this value for convenience and to maximize our data transmission rate. Our two basis sets are illustrated in Fig. 17.10. One basis is comprised of the LG states themselves. The other basis is composed of a linear combination of the LG states of the form
From this expression we obtain the states shown in the lower row of the figure, which is referred to as the angular basis (AB).
An example of the implementation of this protocol is shown in Fig. 17.11. In this example, Alice is attempting to send the string of numbers 13, 3, 2, 3, 15, 14, 16, 8, 24, 26 to Bob. For each transmitted photon, Alice chooses randomly between the LG basis and the AB basis. Also, for each transmitted photon Bob chooses randomly between the OAM and AB bases. After the transmission of the entire data train is complete, Alice and Bob publicly disclose the basis they used for each measurement. If they used different bases (which occurs on average half of the time), they discard the results of that measurement. The remaining data string is known as the sifted data, and this data should contain no errors. Any error in this data string could be the result of measurement errors or to the presence of an eavesdropper. For reasons of extreme caution, one must ascribe all errors to the presence of an eavesdropper. To test for errors, Alice and Bob sacrifice some fraction of their data for public comparison. If errors are detected, they conclude that an eavesdropper is present and take appropriate corrective measures.
Example of a proposed implementation of a generalized BB84 protocol in a high-dimensional (27-dimensions as illustrated) state space [40]
We have implemented this BB84-type protocol in our laboratory. Figure 17.11 shows how Alice forms each of the basis states. Basically, she programs a spatial light modulator (SLM) to convert an individual photon in a plane-wave state into one of the desired LG or AB modes [41]. The upper row shows the LG basis and the lower row shows the angular AB basis. The panel on the left shows representative examples of the pattern displayed on the SLM. The panels on the right show examples of the field distribution written onto the light field. These frames show actual laboratory results, although read out with intense classical light, not with single photons (Fig. 17.12).
Illustration of the procedure for producing light fields in one of the Laguerre–Gaussian or angular basis states, shown for the case of a five-state bases (D = 5). The dotted circles in the panels on the right denote the aperture of the transmitting optics [Unpublished laboratory results of M.N. O’Sullivan]
Special considerations apply to the configuration of the receiver, or Bob. He is presented with a single photon and needs to determine its quantum state. Thus, he is allowed to perform only one measurement to determine in which of a large number of quantum states the received photon resides. This sorting task has eluded the scientific community until very recently, when Berkhout et al. [40] demonstrated a means for performing this task. Their approach is illustrated in Fig. 17.13. The key element of this approach is the ability to map the azimuthal phase distribution of an incident mode onto a linear phase distribution at the output of the device. Of course, a linear phase ramp in one cartesian dimension is simply a wavefront tilt, and leads to a shift in the position of the beam in the far field. It turns out that one can determine analytically the form of the phase function that needs to be applied to a light field to perform this mapping. In their original implementation of this sorting procedure, Berkhout et al. [42] applied this phase mapping through the use of an SLM. In a more recent work they have fabricated refractive elements that perform this same function but with much higher conversion efficiency than those based on diffraction from an SLM.
The angular-to-linear reformatter (Glasgow mode-sorter). (top) Physical layout of the reformatter. (bottom) Some results showing the performance of the reformatter used as a sorter. Note that the vertical position of the light beam at the output of the sorter depends on the OAM value ℓ of the beam (Unpublished data from the Boyd laboratory)
Some laboratory results validating the performance of this sorter are shown in Fig. 17.14. These results demonstrate our ability to discriminate among various quantum states in either the LG or angular basis. In each basis we include only four basis states. This limitation is due to the number of photodetectors (APDs) available to us. We see no fundamental limit to our ability to distinguish among all of the states in our protocol, 27 in this particular situation. We see that there is a small amount of crosstalk among the various channels.
Using the procedures described here, we recently performed a realistic demonstration of quantum key distribution based on OAM encoding [43]. Our experimental setup is shown in Fig. 17.15 and is composed of the various components described above. Alice prepares state to be sent by first carving out pulses from a highly attenuated He-Ne laser through the use of an AOM. Then spatial mode information is impressed on these pulses with a digital micromirror device (DMD). Bob’s mode sorter and fan-out elements map the OAM modes and the ANG modes onto separated spots that are collected by an array of fibers and sent to individual APD detectors.
Experimental setup of Mirhosseini et al. [43]. This system uses the OAM and angle bases to implement a QKD system. Alice encodes information in either the OAM or angle basis (chosen randomly), and Bob performs a measurement after making a further random choice of basis. Data obtained when they use different bases is later discarded, in a process known as sifting. If there is no eavesdropper, there should in concept be no errors in this data. Alice and Bob can test for the presence of an eavesdropper by the following procedure. They openly disclose a subset of this data, and check to see if any errors are present. The presence of errors suggests the presence of an eavesdropper
Some of the results of this demonstration are shown in Fig. 17.16. The top row (left) shows the string of numbers sent by Alice and the top row right shows the string of numbers received by Bob. Note that the strings are not identical; due to various transmission and detection errors, some of the symbols are not detected as transmitted. In the figure errors are marked in red and are underlined. As a test of their system, Alice and Bob could publicly disclose these results to determine the fractional error rate. However, in an operating system, Alice and Bob would want to sacrifice only a small fraction of their data to test system security. Alice and Bob therefore employ an error correction algorithm and a method known as privacy amplification (which shortens the length of their shared string) to decrease the number of errors in the shared strings. They end up with a shared key that contains essentially no errors. (For this reason we show the string constituting the shared key only once.) As a graphic demonstration of the use of this procedure, we also show how it could be used for the secure transmission of an image. The image is separated into pixels which are then digitized and transmitted using the secret key shared by Alice and Bob. An eavesdropper who intercepted the signal would see only the noisy pattern that is also displayed.
Experimental results from the study of Mirhosseini et al. [43] (a ) Example of a random sifted key from the experiment. The spatial modes are mapped to numbers between 0 and 6, and errors are marked in red and are underlined. Each symbol is converted into a three digit binary number first and the binary key is randomized before the error-correction. Privacy amplification minimizes Eve’s information by shortening the key length. (b ) Alice encrypts the secret message (in this case an image of an ancient Persian tablet) using the shared secure key and Bob subsequently decrypts it
6 Summary and Conclusions
In this chapter we have presented a review of the quantum mechanical properties of spatially structured light fields, paying special attention to light fields that carry orbital angular momentum (OAM). We have considered both the conceptual understanding of the quantum features of these light fields and the use of these quantum features for applications. We describe how to produce spatially entangled light fields by means of the nonlinear optical process of spontaneous parametric downconversion. We address the question of how much information can be encoded onto a single photon. As an example, we review a recent experiment that demonstrated the ability to discriminate among four target objects using only one photon for illumination. We also present a description of the concept of the OAM of light, and we describe means to generate and detect OAM. We then present a brief survey of some recent studies of the fundamental quantum properties of structured light beams. Much of this work is aimed at studying the nature of entanglement for the complementary variables of angular position and OAM. Finally, as a real-world application, we describe a secure communication system based on quantum key distribution (QKD). This key distribution system makes use of encoding information in the OAM modes of light and hence is able to transmit more than one bit of information per photon.
References
Kolobov MI (ed) (2006) Quantum imaging. Springer, New York
Schrödinger E (1935) Discussion of probability between separated systems. Proc Camb Phys Soc 31:555
Freedman SJ, Clauser JF (1972) Experimental test of local hidden-variable theories. Phys Rev Lett 28(938):938–941
Aspect A, Grangier P, Roger G (1981) Experimental tests of realistic local theories via Bell’s theorem. Phys Rev Lett 47(7):460–463
Burnham DC, Weinberg DL (1970) Observation of simultaneity in parametric production of optical photon pairs. Phys Rev Lett 25:84
Kwiat PG, Mattle K, Weinfurter H, Zeilinger A, Sergienko AV, Shih Y (1995) New high-intensity source of polarization-entangled photon Pairs. Phys Rev Lett 75:4337
Ling A, Lamas-Linares A, Kurtsiefer C (2008) Absolute emission rates of spontaneous parametric down-conversion into single transverse Gaussian modes. Phys Rev A 77:043834
Einstein A, Podolsky B, Rosen N (1935) Can quantum-mechanical description of physical reality be considered complete? Phys Rev 47:777
Ali-Khan I, Broadbent CJ, Howell JC (2007) Large-alphabet quantum key distribution using energy-time entangled bipartite States. Phys Rev Lett 98:060503
Jha AK, Malik M, Boyd RW (2008) Exploring energy-time entanglement using geometric phases. Phys Rev Lett 101:180405
Gerry C, Knight PL (2005) Introductory quantum optics. Cambridge University Press, Cambridge
Curtis JE, Koss BA, Grier DG (2002) Dynamic holographic optical tweezers. Opt Commun 207:169–175
Mirhosseini M, Magaña-Loaiza OS, Chen C, Rodenburg B, Malik M, Boyd RW (2013) Rapid generation of light beams carrying orbital angular momentum. Opt Exp 21:30204
Broadbent CJ, Zerom P, Shin H, Howell JC, Boyd RW (2009) Discriminating orthogonal single-photon images. Phys Rev A 79:033802
Malik M, Shin H, O’Sullivan M, Zerom P, Boyd RW (2010) Quantum ghost image discrimination with correlated photon Pairs. Phys Rev Lett 104:163602
Strekalov DV, Sergienko AV, Klyshko DN, Shih YH (1995) Observation of two-photon “Ghost” interference and diffraction. Phys Rev Lett 74:3600
Miller DAB (2013) Self-configuring universal linear optical component. Photon Res 1(1):1. http://doi.org/10.1364/PRJ.1.000001
Allen L, Beijersbergen MW, Spreeuw RJC, Woerdman JP (1992) Orbital angular-momentum of light and the transformation of Laguerre-Gaussian laser modes. Phys Rev A, 45(11):8185–8189
He H, Friese M, Heckenberg N, Rubinsztein-Dunlop H (1995) Direct observation of transfer of angular momentum to absorptive particles from a laser beam with a phase singularity. Phys Rev Lett 75:826–829
O’Neil AT, MacVicar I, Allen L, Padgett MJ (2002) Intrinsic and extrinsic nature of the orbital angular momentum of a light beam. Phys Rev Lett 88(5):053601
Leach J, Dennis MR, Courtial J, Padgett MJ (2005) Vortex knots in light. New J Phys 7:55. http://doi.org/10.1088/1367-2630/7/1/055
Yao E, Franke-Arnold ES, Courtial J, Barnett SM, Padgett MJ (2006) Fourier relationship between angular position and optical orbital angular momentum. Opt Exp14:9071
Bolduc E, Bent N, Santamato E, Karimi E, Boyd RW (2013) Exact solution to simultaneous intensity and phase masking with a single phase-only hologram. Opt Lett 38:3546
Marrucci L, Manzo C, Paparo D (2006) Optical spin-to-orbital angular momentum conversion in inhomogeneous anisotropic media. Phys Rev Lett 96:1605
Karimi E, Piccirillo B, Nagali E, Marrucci L, Santamato E (2009) Efficient generation and sorting of orbital angular momentum eigenmodes of light by thermally tuned q-plates. Appl Phys Lett 94:1124
Howell JC, Bennink RS, Bentley SJ, Boyd RW (2004) Realization of the Einstein-Podolsky-Rosen paradox using momentum and position-entangled photons from spontaneous parametric down conversion. Phys Rev Lett 92:210403
Mair A, Vaziri A, Weihs G, Zeilinger A (2001) Entanglement of the orbital angular momentum states of photons. Nature 412(6844):313–316
Leach J, Jack B, Romero J, Jha AK, Yao AM, Franke-Arnold S, Ireland DG, Boyd RW, Barnett SM, Padgett MJ (2010) Quantum correlations in optical angle-orbital angular momentum variables. Science 329:662
Bohm D (1951). Quantum theory. Prentice-Hall, Englewood Cliffs, p 29, and Chapter 5 Section 3, and Chapter 22 Section 19
Rarity JG, Tapster PR (1990) Experimental violation of Bell?s inequality based on phase and momentum. Phys Rev Lett 64(21):2495–2498
Pors JB, Aiello A, Oemrawsingh SSR, van Exter MP, Eliel ER, Woerdman JP (2008) Angular phase-plate analyzers for measuring the dimensionality of multimode fields. Phys Rev A 77:033845
Jha AK, Jack B, Yao E, Leach J, Boyd RW, Buller GS, Barnett SM, Franke-Arnold S, Padgett MJ (2008) Fourier relationship between the angle and angular momentum of entangled photons. Phys Rev A 78:043810
Jha AK, Leach J, Jack B, Franke-Arnold S, Barnett SM, Boyd RW, Padgett MJ (2010) Angular two-photon interference and angular two-qubit states. Phys Rev Lett 104:010501
Pegg DT, Barnett SM (1997) Tutorial review - quantum optical phase. J Mod Opt 44:225–264
Karimi E, Boyd RW, de la Hoz P, de Guise H, Rehacek J, Hradil Z, Aiello A, Leuchs G, Sánchez-Soto LL (2014) Radial quantum number of Laguerre-Gaussian modes. Phys Rev A89:063813
Karimi E, Giovannini D, Bolduc E, Bent N, Miatto FM, Padgett MJ, Boyd RW (2014) Exploring the quantum nature of the radial degree of freedom of a photon via Hong-Ou Mandel interference. Phys Rev A 89:013829
Shannon C (1949) Communication theory of secrecy systems. Bell Syst Tech J 28(4):656–715. As is often the case, the idea of the one-time pad appears to have been invented independently several times in the past. Shannon presents a good review of communication security based on the one-time pad
Wootters WK, Zurek WH (1982) A single quantum cannot be cloned. Nature 299:802–803
Gisin N, Thew R (2007) Quantum communications. Nat Photon 1:165
Boyd RW, Jha A, Malik M, O’Sullivan C, Rodenburg B, Gauthier DJ (2011) Quantum key distribution in a high-dimensional state space: exploiting the transverse degree of freedom of the photon. In: Proceedings of the SPIE 7948, 79480L
Gruneisen MT, Miller WA, Dymale RC, Sweiti AM (2008) Holographic generation of complex fields with spatial light modulators: application to quantum key distribution. Appl Opt 47:A32
Berkhout GCG, Lavery MPJ, Courtial J, Beijersbergen MW, Padgett MJ (2010) Efficient sorting of orbital angular momentum states of light. Phys Rev Lett 105:153601
Mirhosseini M, Magaña-Loaiza OS, O’Sullivan MN, Rodenburg B, Malik M, Lavery MPJ, Padgett MJ, Gauthier DJ, Boyd RW (2015) High-dimensional quantum cryptography with twisted light. New J Phys 17:033033
Acknowledgements
One of us (RWB) acknowledges support from the Canada Excellence Research Chair program, from the US Office of Naval Research, DARPA, and the Air Force Office of Scientific Research. Moreover, MJP acknowledges support from the Engineering and Physical Sciences Research Council of the UK and from the European Research Council.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Open Access This chapter is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, duplication, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, a link is provided to the Creative Commons license and any changes made are indicated.
The images or other third party material in this chapter are included in the work’s Creative Commons license, unless indicated otherwise in the credit line; if such material is not included in the work’s Creative Commons license and the respective action is not permitted by statutory regulation, users will need to obtain permission from the license holder to duplicate, adapt or reproduce the material.
Copyright information
© 2016 The Author(s)
About this chapter
Cite this chapter
Boyd, R.W., Padgett, M.J. (2016). Quantum Mechanical Properties of Light Fields Carrying Orbital Angular Momentum. In: Al-Amri, M., El-Gomati, M., Zubairy, M. (eds) Optics in Our Time. Springer, Cham. https://doi.org/10.1007/978-3-319-31903-2_17
Download citation
DOI: https://doi.org/10.1007/978-3-319-31903-2_17
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-31902-5
Online ISBN: 978-3-319-31903-2
eBook Packages: Physics and AstronomyPhysics and Astronomy (R0)