Abstract
While most lightweight authentication protocols have been well analyzed with respect to their security, often only little (or even nothing) is known with respect to their suitability for low-cost RFIDs in the range of $0.05 to $0.10. Probably this is mainly due to the fact that open literature rarely provides information on what conditions need to be met by a scheme in practice, hindering a sound development and analysis of schemes.
We provide a comprehensive collection of several conditions that should be met by lightweight authentication schemes if deployed in low-cost RFID systems. Afterwards, we show that none of the existing authentication protocols that are based on the hardness of the Learning Parity with Noise (LPN) problem complies to these conditions, leaving the design of an LPN-based protocol for low-cost RFIDs as an open question.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
In [6], it is stated that “in accordance with C1G2, a maximum tag to reader data transmission rate of 640 kbps and a reader to tag data transmission rate of 126 kbps based on equi-probable binary ones and zeros in the transmission can be calculated” and that “performance criteria of an RFID system demand a minimum label reading speed in excess of 200 labels per second”.
- 2.
- 3.
For the sake of simplicity, in this subsection, the term key will always be used to refer to the shared secret’s unique representation as a binary vector in the corresponding scheme, irrespective of potential blow-up measures like, e.g., the use of Toeplitz matrices. In particular, the key size lower bounds the size of the individual key storage required on each tag.
- 4.
At the current state, Lapin was omitted from the table in Appendix B as, according to its authors, it is actually “targeting lightweight tags that are equipped with (small) CPUs” as compared to “ultra constrained tokens (such as RFIDs in the price range of few cents targeting the EPC market)” [17]. (See also [11] for a very recent suggestion of an FPGA implementation for Lapin, which, however, is still not feasible when transferred to low-cost ASICs. Again, the details of this will be discussed in the full version of the paper.)
References
Abyaneh, M.R.S.: On the security of non-linear HB (NLHB) protocol against passive attack. In: 2010 IEEE/IFIP 8th International Conference on Embedded and Ubiquitous Computing (EUC), pp. 523–528. IEEE (2010)
Balachandran, G.K., Barnett, R.E.: A 440-nA true random number generator for passive RFID tags. IEEE Trans. Circ. Syst. I: Regular Pap. 55(11), 3723–3732 (2008)
Bosley, C., Haralambiev, K., Nicolosi, A.: HB\(^{N}\): An HB-like protocol secure against man-in-the-middle attacks. IACR Cryptology ePrint Archive 2011, p. 350 (2011)
Bringer, J., Chabanne, H.:. Trusted-HB: A low-cost version of HB\(^{+}\) secure against man-in-the-middle attacks. arXiv preprint (2008). arXiv:0802.0603
Bringer, J., Chabanne, H., Dottax, E.: HB\(^{++}\): A lightweight authentication protocol secure against some attacks. In: Second International Workshop on Security, Privacy and Trust in Pervasive and Ubiquitous Computing, 2006, SecPerU 2006, pp. 28–33. IEEE (2006)
Cole, P.H., Ranasinghe, D.C.: Networked RFID Systems and Lightweight Cryptography: Raising Barriers to Product Counterfeiting, 1st edn. Springer, Berlin Heidelberg (2008)
Duc, D.N., Kim, K.: Securing HB\(^{+}\) against GRS man-in-the-middle attack. In: Institute of Electronics, Information and Communication Engineers, Symposium on Cryptography and Information Security (2007)
Feldhofer, M., Wolkerstorfer, J., Rijmen, V.: AES implementation on a grain of sand. IEE Proc.: Inf. Secur. 152(1), 13–20 (2005)
Feldhofer, M., Dominikus, S., Wolkerstorfer, J.: Strong authentication for RFID systems using the AES algorithm. In: Joye, M., Quisquater, J.-J. (eds.) CHES 2004. LNCS, vol. 3156, pp. 357–370. Springer, Heidelberg (2004)
Frumkin, D., Shamir, A.: Untrusted-HB: Security vulnerabilities of Trusted-HB. Cryptology ePrint Archive, Report 2009/044 (2009)
Gaspar, L., Leurent, G., Standaert, F.-X.: Hardware implementation and side-channel analysis of lapin. In: Benaloh, J. (ed.) CT-RSA 2014. LNCS, vol. 8366, pp. 206–226. Springer, Heidelberg (2014)
Gilbert, H., Robshaw, M., Sibert, H.: Active attack against \(\text{ HB }^+\): A provably secure lightweight authentication protocol. Electron. Lett. 41(21), 1169–1170 (2005)
Gilbert, H., Robshaw, M., Seurin, Y.: Good variants of HB\(^ \text{+ } \) are hard to find. In: Tsudik, G. (ed.) FC 2008. LNCS, vol. 5143, pp. 156–170. Springer, Heidelberg (2008)
Gilbert, H., Robshaw, M., Seurin, Y.:
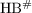 : Increasing the security and efficiency of HB\(^{+}\). In: Smart, N.P. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 361–378. Springer, Heidelberg (2008)
: Increasing the security and efficiency of HB\(^{+}\). In: Smart, N.P. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 361–378. Springer, Heidelberg (2008) Gold, R.: Maximal recursive sequences with 3-valued recursive cross-correlation functions (corresp.). IEEE Trans. Inf. Theory 14(1), 154–156 (1968)
Hammouri, G., Sunar, B.: PUF-HB: A tamper-resilient HB based authentication protocol. In: Bellovin, S.M., Gennaro, R., Keromytis, A.D., Yung, M. (eds.) ACNS 2008. LNCS, vol. 5037, pp. 346–365. Springer, Heidelberg (2008)
Heyse, S., Kiltz, E., Lyubashevsky, V., Paar, C., Pietrzak, K.: Lapin: An efficient authentication protocol based on Ring-LPN. In: Canteaut, A. (ed.) FSE 2012. LNCS, vol. 7549, pp. 346–365. Springer, Heidelberg (2012)
Hopper, N.J., Blum, M.: Secure human identification protocols. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 52–66. Springer, Heidelberg (2001)
Juels, A.: RFID security and privacy: A research survey. IEEE J. Sel. A. Commun. 24(2), 381–394 (2006)
Juels, A., Weis, S.A.: Authenticating pervasive devices with human protocols. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 293–308. Springer, Heidelberg (2005)
Katz, J., Shin, J.S.: Parallel and concurrent security of the HB and HB\(^{+}\) protocols. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 73–87. Springer, Heidelberg (2006)
Katz, J., Shin, J.S., Smith, A.: Parallel and concurrent security of the HB and HB\(^{+}\) protocols. J. Cryptol. 23(3), 402–421 (2010)
Kiltz, E., Pietrzak, K., Cash, D., Jain, A., Venturi, D.: Efficient authentication from hard learning problems. In: Paterson, K.G. (ed.) EUROCRYPT 2011. LNCS, vol. 6632, pp. 7–26. Springer, Heidelberg (2011)
Krawczyk, H.: LFSR-based hashing and authentication. In: Desmedt, Y.G. (ed.) CRYPTO 1994. LNCS, vol. 839, pp. 129–139. Springer, Heidelberg (1994)
Leng, X., Mayes, K., Markantonakis, K.: HB-MP\(^{+}\) protocol: An improvement on the HB-MP protocol. In: 2008 IEEE International Conference on RFID, pp. 118–124. IEEE (2008)
Levieil, É., Fouque, P.-A.: An improved LPN algorithm. In: De Prisco, R., Yung, M. (eds.) SCN 2006. LNCS, vol. 4116, pp. 348–359. Springer, Heidelberg (2006)
Madhavan, M., Thangaraj, A., Sankarasubramanian, Y., Viswanathan, K.: NLHB: A non-linear Hopper-Blum protocol. In: 2010 IEEE International Symposium on Information Theory Proceedings (ISIT), pp. 2498–2502. IEEE (2010)
Martin, H., Millán, E.S., Entrena, L., Castro, J.C.H., Peris-Lopez, P.: AKARI-X: A pseudorandom number generator for secure lightweight systems. In: IOLTS, pp. 228–233 (2011)
Melià-Seguí, J., Garcia-Alfaro, J., Herrera-Joancomartí, J.: J3Gen: A PRNG for low-cost passive RFID. Sensors 13(3), 3816–3830 (2013)
Munilla, J., Peinado, A.: HB-MP: A further step in the HB-family of lightweight authentication protocols. Comput. Netw. 51(9), 2262–2267 (2007)
Ouafi, K., Overbeck, R., Vaudenay, S.: On the security of
 against a man-in-the-middle attack. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 108–124. Springer, Heidelberg (2008)
against a man-in-the-middle attack. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 108–124. Springer, Heidelberg (2008)Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Ribagorda, A.: LAMED - A PRNG for EPC Class-1 generation-2 RFID specification. Comput. Stand. Interfaces 31(1), 88–97 (2009)
Pietrzak, K.: Subspace LWE, Manuscript. http://homepages.cwi.nl/~pietrzak/publications/SLWE.pdf
Piramuthu, S., TU, Y.-J.: Modified HB authentication protocol. In: WEWoRC, pp. 41–44 (2007)
Poschmann, A.: Lightweight cryptography: Cryptographic engineering for a pervasive world (2009)
Poschmann, A., Moradi, A., Khoo, K., Lim, C., Wang, H., Ling, S.: Side-channel resistant crypto for less than 2,300 GE. J. Cryptol. 24(2), 322–345 (2011)
Ranasinghe, D.C., Engels, D.W., Cole, P.H.: Low-cost RFID systems: Confronting security and privacy. In: Auto-ID Labs Research Workshop, Portal (2005)
Repec, C.A.: Regulatory status for using RFID in the EPC Gen 2 band (860 to 960 MHz) of the UHF spectrum (2013). http://www.gs1.org/docs/epcglobal/UHF_Regulations.pdf
Rizomiliotis, P., Gritzalis, S.:
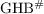 : A provably secure HB-like lightweight authentication protocol. In: Bao, F., Samarati, P., Zhou, J. (eds.) ACNS 2012. LNCS, vol. 7341, pp. 489–506. Springer, Heidelberg (2012)
: A provably secure HB-like lightweight authentication protocol. In: Bao, F., Samarati, P., Zhou, J. (eds.) ACNS 2012. LNCS, vol. 7341, pp. 489–506. Springer, Heidelberg (2012)Rizomiliotis, P.: HB \(-\) MAC: Improving the Random \(-\)
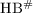 authentication protocol. In: Fischer-Hübner, S., Lambrinoudakis, C., Pernul, G. (eds.) TrustBus 2009. LNCS, vol. 5695, pp. 159–168. Springer, Heidelberg (2009)
authentication protocol. In: Fischer-Hübner, S., Lambrinoudakis, C., Pernul, G. (eds.) TrustBus 2009. LNCS, vol. 5695, pp. 159–168. Springer, Heidelberg (2009) Rolfes, C., Poschmann, A., Leander, G., Paar, C.: Ultra-lightweight implementations for smart devices – Security for 1000 gate equivalents. In: Grimaud, G., Standaert, F.-X. (eds.) CARDIS 2008. LNCS, vol. 5189, pp. 89–103. Springer, Heidelberg (2008)
Saarinen, M.-J.O., Engels, D.W.: A do-it-all-cipher for RFID: Design requirements (extended abstract). IACR Cryptology ePrint Archive, 2012, p. 317 (2012) (informal publication)
Song, X., Kobara, K., Imafuku, K., Imai, H.: HB\(^{b}\) protocol for lightweight authentication; Its information theoretic indistinguishability against MITM attack watching reader’s response. In: 2012 International Symposium on Information Theory and its Applications (ISITA), pp. 536–540. IEEE (2012)
Susini, J., Chabanne, H., Urien, P.: RFID and the Internet of Things, p. 304. ISTE - Wiley, London (2011)
Tokunaga, C., Blaauw, D., Mudge, T.: True random number generator with a metastability-based quality control. In: Solid-State Circuits Conference, 2007, ISSCC 2007. Digest of Technical Papers. IEEE International, pp. 404–611, Feb 2007
Wu, W., Zhang, L.: LBlock: A lightweight block cipher. In: Lopez, J., Tsudik, G. (eds.) ACNS 2011. LNCS, vol. 6715, pp. 327–344. Springer, Heidelberg (2011)
Acknowledgment
We would like to thank the anonymous reviewers of RFIDSec 2014 and Gildas Avoine for their helpful comments. Finally, we would also like to express our special thanks to Peter Fischer and Michael Ritzert, who supplied us with the necessary technical means and additional valuable information for actually implementing the discussed protocols.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Overview of the Considered Protocols
In 2000, the HB [18] protocol was proposed, which is proven to be secure against passive attacks [22]. In order to resist active attacks, \(\text {HB}^{+}\) [20] was introduced that is provably secure in the detection-based model (where the adversary is able to communicate only with the tag before attempting to authenticate itself to the reader). However, if the attacker is given the ability to modify messages which go from the reader to the tag (GRS model), the \(\text {HB}^{+}\) protocol is not secure anymore as it was shown in [12]. As a result, many new HB-type protocols were proposed in order to overcome this and other types of Man-in-the-middle (MITM) attacks. In 2006, the \(\text {HB}^{++}\) protocol was introduced [5], which can be seen as running \(\text {HB}^{+}\) twice with correlated challenges and independent secrets. Later, [30] proposed the \(\text{ HB-MP }\) protocol, which was designed to be more efficient than \(\text {HB}^{+}\) but turned out to be vulnerable w.r.t. certain MITM attacks [13], which is why \(\text{ HB-MP }^+\) [25] has been suggested. Another attempt to improve the performance of \(\text {HB}^{+}\) and to make it resistant against GRS-type MITM attacks was the \(\text {HB}^{*}\) protocol [7]. In 2008, the \(\text {HB}^{\#}\) and RANDOM-\(\text {HB}^{\#}\) protocols were proposed, where the keys were extended from vectors to matrices [14]. Another proposal called Trusted-HB [4] is based on the idea of using a hardware efficient hash function for verifying the integrity of the data in order to resist MITM attacks. PUF-HB [16] is a construction which relies on Physically Unclonable Functions (PUFs) as a hardware primitive. In the protocols NLHB [27] and GHB# [39], the linear functions are replaced by non-linear functions, while \(\text {HB}^{N}\) [3] can be seen as a bilinear variant of \(\text {HB}^{}\). In 2011, AUTH [23] was proposed, where the security is based on a modified LPN problem, called the subspace LPN problem [33]. One year later, a more efficient proposal building on the ideas from [23] called Lapin [17] was introduced, whose security relies on assumed hardness of the Ring LPN-problem.
B Evaluation Results for the Considered Protocols
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Armknecht, F., Hamann, M., Mikhalev, V. (2014). Lightweight Authentication Protocols on Ultra-Constrained RFIDs - Myths and Facts. In: Saxena, N., Sadeghi, AR. (eds) Radio Frequency Identification: Security and Privacy Issues. RFIDSec 2015. Lecture Notes in Computer Science(), vol 8651. Springer, Cham. https://doi.org/10.1007/978-3-319-13066-8_1
Download citation
DOI: https://doi.org/10.1007/978-3-319-13066-8_1
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-13065-1
Online ISBN: 978-3-319-13066-8
eBook Packages: Computer ScienceComputer Science (R0)


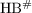 : Increasing the security and efficiency of HB
: Increasing the security and efficiency of HB against a man-in-the-middle attack. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 108–124. Springer, Heidelberg (2008)
against a man-in-the-middle attack. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 108–124. Springer, Heidelberg (2008)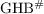 : A provably secure HB-like lightweight authentication protocol. In: Bao, F., Samarati, P., Zhou, J. (eds.) ACNS 2012. LNCS, vol. 7341, pp. 489–506. Springer, Heidelberg (2012)
: A provably secure HB-like lightweight authentication protocol. In: Bao, F., Samarati, P., Zhou, J. (eds.) ACNS 2012. LNCS, vol. 7341, pp. 489–506. Springer, Heidelberg (2012)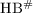 authentication protocol. In: Fischer-Hübner, S., Lambrinoudakis, C., Pernul, G. (eds.) TrustBus 2009. LNCS, vol. 5695, pp. 159–168. Springer, Heidelberg (2009)
authentication protocol. In: Fischer-Hübner, S., Lambrinoudakis, C., Pernul, G. (eds.) TrustBus 2009. LNCS, vol. 5695, pp. 159–168. Springer, Heidelberg (2009)