Abstract
Alon et al. (CRYPTO 2021) introduced a multiparty quantum computation protocol that is secure with identifiable abort (MPQC-SWIA). However, their protocol allows only inside MPQC parties to know the identity of malicious players. This becomes problematic when two groups of people disagree and need a third party, like a jury, to verify who the malicious party is. This issue takes on heightened significance in the quantum setting, given that quantum states may exist in only a single copy. Thus, we emphasize the necessity of a protocol with publicly verifiable identifiable abort (PVIA), enabling outside observers with only classical computational power to agree on the identity of the malicious party in case of an abort. However, achieving MPQC with PVIA poses significant challenges due to the no-cloning theorem, and previous works proposed by Mahadev (STOC 2018) and Chung et al. (Eurocrypt 2022) for classical verification of quantum computation fall short.
In this paper, we obtain the first MPQC-PVIA protocol assuming post-quantum oblivious transfer and a classical broadcast channel. The core component of our construction is a new authentication primitive called auditable quantum authentication (AQA) that identifies the malicious sender with overwhelming probability. Additionally, we provide the first MPQC protocol with best-of-both-worlds (BoBW) security, which guarantees output delivery with an honest majority and remains secure with abort even if the majority is dishonest. Our best-of-both-worlds MPQC protocol also satisfies PVIA upon abort.
You have full access to this open access chapter, Download conference paper PDF
1 Introduction
Secure multiparty computation (MPC) allows two or more parties to compute a function on their joint private inputs securely [28]. Most of the MPC literature studies classical functionality over classical inputs with different notions of security, such as full security, security with abort, and security with identifiable abort [22, 25, 26].
Recently, secure multiparty quantum computation (MPQC) has raised research interest. Most of the works consider the fully quantum setting i.e., the functionality, including inputs and outputs, is quantum. Like in the classical setting, it is known that an honest majority is both sufficient [9, 16], and necessary [4] to achieve full security, which guarantees output delivery for everyone. In light of this, the study of MPQC protocols in the dishonest majority setting has focused on the weaker notion of security with abort [6, 17, 18], which allows all honest parties to abort when they detect an attack. However, such a notion is vulnerable to a denial-of-service attack because an attacker can repeatedly induce aborts. For this reason, a more recent work [3] has proposed an MPQC protocol with identifiable abort (MPQC-SWIA) that allows all honest parties to agree on the identity of a corrupted party in case of an abort. Regrettably, the identification mechanism of [3] only allows the participants of the protocol to identify a malicious party. This is unsatisfactory in many practical scenarios because during a dispute, external observers are aware that two groups of people are in disagreement, but it is unclear which side is acting maliciously. Consider an instance where a client accuses a tech company of failing to provide a service and, therefore, refuses payment. Conversely, the company asserts that they have indeed provided the service. In such cases, it becomes vital to employ a publicly verifiable protocol to assess their integrity. This is especially important in the quantum setting, where each party may possess only one copy of their quantum input. Once the quantum inputs are ruined, it results in the irreversible loss of inputs for honest parties. Therefore, we consider a notion of security called publicly verifiable identifiable abort (PVIA) that allows everyone, including outside observers, to identify the malicious party. We ask:
Is it possible to construct MPQC with publicly verifiable identifiable abort (PVIA)?
In the classical setting, one can turn MPC-SWIA into MPC-PVIA almost for free. A publicly verifiable protocol can be obtained by requiring each party to broadcast their messages and proofs to outside observers. Unfortunately, this simple solution does not work in the quantum setting due to the no-cloning theorem. One may be tempted to turn to classical verification of quantum computation (CVQC) [14, 24] in order to achieve public verifiability. However, this approach is restricted to computation that is performed by a single quantum party with classical outputs, and it is unclear how it can be adapted to fit into the setting of MPQC. Furthermore, all existing MPQC protocols face an inherent difficulty in achieving PVIA because their sender-receiver mechanism cannot differentiate a malicious sender from a malicious receiver. To address this issue, we propose a new primitive called Auditable Quantum Authentication (AQA), which subverts the traditional sender-receiver mechanism and holds the sender accountable for his behavior.
While PVIA security can act as insurance for honest parties when a dishonest majority is present, it is desirable to have a stronger security notion, such as full security, if it turns out that the honest parties outnumber the malicious ones. An intriguing scenario involves reducing the maximal number of malicious parties allowed for security with abort while conditionally offering full security. Such a notion is called best-of-both-worlds (BoBW) securityFootnote 1. In the classical setting, [21] constructs, for every threshold \(t< \frac{n}{2}\), an MPC protocol that achieves security with abort against \(n-1-t\) malicious parties and achieves full security tolerating \(t\) malicious parties. [23] proved that these corruption thresholds are optimal. In the quantum setting, none of the existing MPQC protocols satisfy BoBW security. Therefore, we ask:
Is it possible to construct a single MPQC that achieves full security under an honest majority and is secure with abort under a dishonest majority?
1.1 Our Results
We answer both questions affirmatively. First, we design protocols in the preprocessing model, which features an offline setup that prepares input-independent auxiliary quantum states. After the setup, we require that the parties exchange only classical bits. With this approach, the parties can create classical proofs that are accessible to everyone, which in turn facilitates PVIA. Moreover, combined with quantum error correction code (QECC), the setup can create quantum states that enable distributed computation and ultimately achieve best-of-both-worlds security. Finally, we show that our offline setup can be instantiated without requiring any trusted third party.
Our first result is an MPQC protocol secure with publicly verifiable identifiable abort (PVIA) under a trusted setup. Similar to existing MPQC works [3, 6, 17, 18], we assume that parties have access to an ideal functionality \({\textsf{cMPC}}\) for classical MPC (this model is known as the MPC-hybrid model; see Sect. 4.2). Here, the classical MPC is assumed to be PVIA-secure. Such an MPC can be based on post-quantum oblivious transfer (OT) and classical broadcast channel.
Theorem 1
(MPQC-PVIA with trusted setup, informal). There exists a multiparty quantum computation protocol secure with publicly verifiable identifiable abort supporting poly-size quantum circuits in the preprocessing MPC-hybrid model.
To achieve Theorem 1, we propose and construct a new primitive called auditable quantum authentication (AQA) that allows a classical auditor to decide the integrity of a quantum message sender. Then, in our MPQC-PVIA protocol, the actions of the trusted auditor will be taken by classical MPC.
Our second result is a best-of-both-worlds (BoBW) MPQC protocol that achieves full security against \(t\) corruptions and satisfies security with abort against \(n-1-t\) corruptions under a trusted setup. We call \(t\) as the BoBW threshold. Here, we assume our underlying classical MPC to be BoBW-secure with threshold \(t\) as well, which can be based on post-quantum OT for \(t< \frac{n}{3}\) and additionally requires a classical broadcast channel for \(\frac{n}{3} \le t < \frac{n}{2}\).
Theorem 2
(BoBW-MPQC with trusted setup, informal). There exists a best-of-both-worlds multiparty quantum computation protocol of threshold \(t\) supporting poly-size quantum circuits for any \(t< \frac{n}{2}\) in the preprocessing MPC-hybrid model.
The key to arriving at best-of-both-worlds security is our protocol’s compatibility with decentralized quantum computation using QECC. In particular, no single party in our protocol holds all the quantum information of a piece of data during the computation step, as opposed to prior security-with-abort protocols [3, 6, 17].
Combining these two results, we obtain a BoBW-MPQC-PVIA protocol that achieves full security against \(t\) corruptions and satisfies PVIA security against \(n-1-t\) corruptions under a trusted setup. The underlying classical MPC should be BoBW-PVIA-secure, which can be based on a post-quantum OT and a classical broadcast channel.
Theorem 3
(BoBW-MPQC-PVIA with trusted setup, informal). There exists a best-of-both-worlds multiparty quantum computation protocol secure with publicly verifiable identifiable abort of threshold \(t\) supporting poly-size quantum circuits for every \(t< \frac{n}{2}\) in the preprocessing MPC-hybrid model.
Furthermore, we can instantiate the setups, thus obtaining the above three results without needing a trusted setup.
Theorem 4
(BoBW-MPQC-PVIA without trusted setup, informal). Theorems 1,2,3 hold in the (standard) MPC-hybrid model.
Our main technique for instantiating the setup is to leverage MPQC secure with identifiable abort (SWIA) protocols. Interestingly, the properties of both BoBW and PVIA can be preserved under our instantiation. Note that our instantiation is based on an MPQC-SWIA protocol which, contrasting with the previous result [3], only assumes classical MPC.
2 Technical Overview
In this section, we first explain why PVIA does not follow directly from existing works. Then, we put forth a novel primitive called Auditable Quantum Authentication (AQA), which ensures the secure transmission of quantum outputs and the public identification of malicious identities within a protocol. Following a high-level understanding of AQA, we then incorporate the input encoding and computation steps together to realize MPQC-PVIA. Finally, we discuss the difficulty of achieving best-of-both-worlds security and elucidate our approach to attaining a BoBW-MPQC protocol.
2.1 Why is MPQC-PVIA Hard to Achieve?
A first observation is that classical techniques for public verifiability cannot apply to their quantum counterparts. Existing methods for classical MPC-PVIA protocols are to commit to classical messages, provide zero-knowledge arguments over the commitments, and let outside observers check whether any party deviates from the protocol. There are several issues when adapting to MPQC in the fully quantum setting. If one considers classical commitments to quantum messages [24], one cannot fulfill MPQC with purely quantum outputs because such classical commitment schemes always end with measurements. Instead, one may have to consider quantum commitments [20]. However, quantum commitments are unlikely to be duplicated and broadcast to each party for verification because of the no-cloning theorem. In addition, zero-knowledge arguments for quantum computation (e.g., [11]) only apply to problems with a classical description. Those arguments cannot prove relations involving quantum commitments.
Another difficulty arises because we require the outside observers of MPQC to have only classical computational power. Although there is research on classical verification of quantum computation (CVQC), a seemingly similar task, CVQC needs to be more relaxed because it can only resolve computations with classical outputs conducted by a single quantum prover. The techniques of CVQC fail in the fully quantum setting. Moreover, CVQC already produces an inverse polynomial soundness error when extended from decisional problems [24] to sampling problems [14]. Thus, there is little hope that CVQC can aid the construction of MPQC-PVIA.
One may try to upgrade MPQC-SWIA to MPQC-PVIA directly, but there is still a gap between them. The MPQC-SWIA protocol by [3] is based on a Sequential Authentication primitive that outputs two suspects whenever message tampering is detected. However, it gives no information about the exact party that deviates from the protocol. The resulting MPQC-SWIA allows honest parties to agree on the same malicious party when protocol aborts, but an outside observer only sees two groups of people accusing each other. This outcome arises from the conventional utilization of quantum authentication codesFootnote 2, where the sender sends an authenticated state to the receiver, and the receiver is in charge of measuring the authentication checksum to validate the state. However, this kind of validation mechanism relies on the synergy of both sender and receiver over a single-copy state, which makes it challenging to achieve public verifiability. To address this, we subvert the old idea and creatively combine quantum authentication codes with quantum teleportation in a white-box manner.
2.2 Our Solution: Auditable Quantum Authentication (AQA)
The primary goal of AQA is to establish a mechanism where the sender of an authenticated state is held responsible for his own sending action through a test performed by someone trustworthy. In a normal quantum authentication scheme, the receiver of an authenticated state runs the decoding algorithm to obtain either the original message or an authentication failure symbol. To learn the true authentication outcome, an outside observer has to trust the party who executes the decoding algorithm. This would require trust in the receiver, who might be malicious. To resolve this issue, we propose an auditable quantum authentication scheme that separates the authenticity check from the message decoding process. Importantly, the AQA scheme is equipped with a classical auditing algorithm that decides message authenticity and outputs a decoding key for the receiver to recover the message. With AQA, an outside observer can learn the authentication outcome by trusting a classical auditor who executes the auditing algorithm. Later on, we can replace the classical auditor with a publicly verifiable classical MPC (cMPC) to completely remove the need of trust.
AQA is designed to be cooperated by three parties: a sender, a receiver, and a classical auditor. We define AQA as consisting of five algorithms: \(\textsf{Setup}, \textsf{Enc}, \textsf{Send},\) \(\textsf{Audit}, \textsf{Recv}\). In the beginning, \(\textsf{Setup}\) prepares initial states for all the parties, and \(\textsf{Enc}\) produces an authenticated state \(\sigma \) for the sender. The sender runs \(\textsf{Send}(\sigma )\) to generate a classical proof \(\textsf{pf}\) showing that the quantum message has been delivered. Next, the auditor runs \(\textsf{Audit}(\textsf{pf})\) to verify the proof and produce a decoding key \(\textsf{dk}\). Afterward, the receiver can run \(\textsf{Recv}(\textsf{dk})\) to obtain the quantum message. The security of AQA entails that \(\textsf{Recv}(\textsf{dk})\) produces the correct quantum message (up to a negligible error) whenever \(\textsf{Audit}(\textsf{pf})\) outputs a positive verification outcome.
Constructing a (Simplified) AQA. We will start with a normal quantum authentication scheme (\(\textsf{Gen}\),\(\textsf{Enc}\),\(\textsf{Dec}\)), the Clifford code [2] in particular. We aim to keep the encoding procedure \(\textsf{Enc}\) and split its decoding procedure into several parts. The decoding procedure of Clifford code applies a secret Clifford gate
 to an authenticated state
to an authenticated state
 and measures
and measures
 register in the computational basis. An authentication failure occurs if the measurement result is not all zeros. Otherwise, the content of the
register in the computational basis. An authentication failure occurs if the measurement result is not all zeros. Otherwise, the content of the
 register will be the message state. To make this authentication scheme classically auditable, we consider the following alternative decoding procedure that involves 4 algorithms. We take
register will be the message state. To make this authentication scheme classically auditable, we consider the following alternative decoding procedure that involves 4 algorithms. We take
 and
and
 as an example Fig. 1.
as an example Fig. 1.
AQA Setup: Each edge represents an EPR pair. The nodes on the left contain halves of EPR pairs \(\{e^i_0\}_{i \in [\lambda +1]}\), and the nodes on the right contain the other halves of EPR pairs \(\{e^i_1\}_{i \in [\lambda +1]}\). The encircled vertices (the sending register S and checking register C) are given to the sender. The lonely vertex (receiving register R) is given to the receiver.
\(\underline{\textsf{Setup}}\):
-
Generate EPR pairs \(\{(e_0^i,e_1^i)\}_{i \in [\lambda +1]}\) of length \(\lambda +1\). Put \(\{e^i_0\}_{i \in [\lambda +1]}\), \(\{e_1^i\}_{i \in \{2,\cdots ,\lambda +1\}}\), \(e_1^1\) into the sending, checking, receiving registers
 respectively.
respectively. -
Apply the secret Clifford gate \(F^\dag \leftarrow \mathscr {C}_{\lambda +1}\) to
 .
.
\(\underline{\textsf{Send}}\):
-
Sending: Teleport the authenticated state \(\sigma \) through the sending register
 .
. -
Proving: Measure the checking register
 in the computational basis.
in the computational basis. -
Set classical proof as the teleportation Pauli P and measurement result c.
\(\underline{\textsf{Audit}}\):
-
Compute the Pauli \(F^\dag P F\) and express it as a tensor product of two Pauli gates \(\hat{P}_R, \hat{P}_C\) that act on \(1, \lambda \) qupits respectively.
-
Report an authentication failure if \(c \ne x(\hat{P}_C)\). Set the decoding key as \(\hat{P}_R\).
\(\underline{\textsf{Recv}}\):
-
Apply
 and output the state on the receiving register
and output the state on the receiving register
 .
.
Running these 4 algorithms in a row is equivalent to running the decoding procedure of Clifford code. This follows almost directly from quantum teleportation: If we denote
 and if teleporting \(\sigma \) through
and if teleporting \(\sigma \) through
 during \(\textsf{Send}\) yields teleportation result P, then the state in
during \(\textsf{Send}\) yields teleportation result P, then the state in
 would collapse from \(F^\dag (\{e_1^i\}_{i\in [\lambda +1]})\) to
would collapse from \(F^\dag (\{e_1^i\}_{i\in [\lambda +1]})\) to
This shows that the measurement result of the checking register
 equals \(x(\hat{P}_C)\) if and only if the measurement result of \(\tau \) equals all zeros. The current decoding procedure includes a classical algorithm \(\textsf{Audit}\) that determines the authentication outcome, so we can set our simplified AQA as these 4 algorithms plus the encoding algorithm of Clifford code.
equals \(x(\hat{P}_C)\) if and only if the measurement result of \(\tau \) equals all zeros. The current decoding procedure includes a classical algorithm \(\textsf{Audit}\) that determines the authentication outcome, so we can set our simplified AQA as these 4 algorithms plus the encoding algorithm of Clifford code.
Proving Security of AQA. For the security of AQA, it’s crucial for \(\textsf{Recv}\) to recover the original message whenever \(\textsf{Audit}\) doesn’t indicate an authentication failure upon receiving proof from an adversarial sender. Take, for instance, a malicious sender who alters the authenticated message \(\sigma \) prior to the execution of \(\textsf{Send}\). In such a specific scenario, the security of the simplified AQA is derived from the established equivalence between the processes \((\textsf{Send},\textsf{Audit},\textsf{Recv})\) and \(\textsf{Dec}\) mentioned in the preceding paragraph and grounded on the efficacy of \((\textsf{Enc},\textsf{Dec})\) as a quantum authentication scheme. However, the simplified AQA is presented mainly as an explanation of how we achieve the audit functionality, and is not yet secure against arbitrary malicious senders. To further protect against adversaries employing arbitrary attacks, our formal AQA in Sect. 5 additionally integrates quantum one-time pads. To offer a high-level intuition, the use of quantum one-time pads can split the attack of the malicious sender into a combination of Pauli attacks. Since the malicious sender knows nothing about the random Clifford key F, the Clifford twirl will transform Pauli attacks into random Pauli operators distributed across the states, breaking the consistency of P and c.
2.3 From AQA to MPQC-PVIA
From the previous section, we see that transmission of quantum information can be audited by a classical party. We now build an MPQC-PVIA protocol with AQA where the auditing is performed by a publicly verifiable classical MPC.
MPQC-PVIA with Setup. The MPQC-PVIA consists of two phases: an offline setup and an online phase. The offline setup generates EPR pairs that would allow each party to send their input to the server (who is a designated party, say \(\textsf{P}_1\)), and runs the setup of AQA. During the online phase, every party teleports their input to \(\textsf{P}_1\) and \(\textsf{P}_1\) only obtains a ciphertext of the joint inputs. Next, \(\textsf{P}_1\) performs quantum computation on the ciphertext as instructed by classical MPC. Finally, \(\textsf{P}_1\) sends the output ciphertexts to other parties using AQA, which is audited by classical MPC. These three steps in the online phase are called input encoding, computation, and output delivery, respectively.
We now move on to examine security. In our protocol, the parties’ inputs are gathered towards \(\textsf{P}_1\), and the quantum computation is solely performed by \(\textsf{P}_1\). Thus, only \(\textsf{P}_1\) can launch an effective attack. The attack would ruin \(\textsf{P}_1\)’s ciphertext, and \(\textsf{P}_1\) would ultimately face an authentication error when transmitting the ciphertext with AQA. In this case, the classical MPC that runs the audit algorithm can publicly output \(\textsf{P}_1\) as malicious. As a result, our protocol achieves MPQC while maintaining PVIA security.
Instantiable Setup. Next, we show how to instantiate our setup with an MPQC protocol secure with identifiable abort (SWIA). Note that we refine a slightly different version of MPQC-SWIA, thereby circumventing the need for the post-quantum Fully Homomorphic Encryption (FHE) assumption needed in [3].
MPQC-SWIA guarantees that whenever an abort happens, \({\textsf{cMPC}}\) will output a partition of parties with all honest parties staying in the same group. Our approach for instantiating the setup is to run MPQC-SWIA hierarchically to prepare the states that the setup would generate. The hierarchical MPQC-SWIA maintains a grouping between parties, where all parties are initially in the same group. Each group will try to run MPQC-SWIA by themselves, and a group breaks into two whenever MPQC-SWIA fails. At some point, all parties must have succeeded in running MPQC-SWIA within their group (or they will continue running MPQC-SWIA within descent subgroups), so they can proceed to execute the online MPQC-PVIA protocol. By employing the security of MPQC-PVIA with preprocessing, it is guaranteed that either the honest parties obtain their outputs, or some malicious party in the group that contains all honest parties will be publicly identified Fig. 2.
Hierarchical MPQC-SWIA parties try to run the offline setup using MPQC-SWIA. Initially, G contains all the parties. When the first MPQC-SWIA run by G terminates with a failure, parties in G separate into two groups \(G_0\) and \(G_1\), who run another MPQC-SWIA within their own group. In this figure, \(G_{1}\) executes MPQC-SWIA successfully and obtains the setup output. They can proceed to execute the online MPQC-PVIA protocol.
2.4 Best-of-Both-Worlds Security
One advantage of our protocol design is its flexibility to provide best-of-both-worlds security. That is, we construct an MPQC protocol that simultaneously achieves full security when there are at most \(t< \frac{n}{2}\) corruptions and satisfies security with publicly verifiable identifiable abort against at most \(n-1-t\) corrupted parties.
Prior to this work, the honest-majority and the dishonest-majority worlds were once separated because of a tension between sharing and extracting quantum information. We elaborate on it as follows. MPQC protocols that obtain full security in an honest majority setting [9] are based on verifiable quantum secret sharing (VQSS). In these protocols, each party individually creates VQSS of their input and distributes the shares across parties. The problem is that the secret shares sent between malicious parties are private information. Once the number of corrupted parties reaches one-half, the simulator cannot extract the adversary’s input from the available secret shares. This is also why current MPQC protocols designed for a dishonest majority need every quantum message to be transmitted through all parties: the simulator can extract inputs when the quantum message passes through an honest party. As a result, protocols against a dishonest majority cannot divide a piece of quantum information across multiple parties, and a single malicious party is sufficient to destroy the information subjected to the computation.
Our solution to this tension is to utilize the offline-online structure of our protocol and incorporate quantum error correction codes (QECC). First, our offline setupFootnote 3 prepares QECC codewords on EPR pairs and distributes the codewords evenly across parties. Afterward, the parties can perform distributed computation over QECC codewords in the online protocol. In this protocol, the honestly-generated QECC codewords facilitate the sharing of quantum information. Moreover, to extract quantum information even in the presence of a malicious majority, the setup can entangle a trapdoor with the states prepared for the parties and use the trapdoor to extract online inputs. We see that the offline setup acts as a vital piece of machinery that allows information extraction while preparing for the online distributed computation.
Our BoBW-MPQC protocol is reminiscent of the classical BoBW-cMPC protocols [8, 21, 23]. A key difference is that the classical protocols need to broadcast secret sharings and invoke the ideal functionality on the inputs multiple times, both of which are infeasible in MPQC due to no-cloning. Our protocol does not follow the same pattern, and we achieve the same goal in the merit of quantum teleportation.
3 Preliminary
Let \([n] = \{1, \cdots , n\}\). We denote by \(A_{[n]}\) the tuple \((A_1,\cdots ,A_n)\). Uniform sampling from a set S is denoted by \(s\leftarrow S\). A function \(f :\mathbb {N}\rightarrow [0,1]\) is called negligible if for every polynomial \(\textrm{poly}(\cdot )\) and all sufficiently large n, we have \(f(n)<|{1}/{\textrm{poly}(n)}|\). We use \({\text {negl}}(\cdot )\) to denote an unspecified negligible function.
Quantum states are written in lowercase Greek alphabets, e.g., \(\rho ,\sigma \). Quantum operations are written in uppercase Latin alphabets, e.g., U, V. We write
 and
and
 to specify that \(\rho \) is stored in register
to specify that \(\rho \) is stored in register
 and U operates on register
and U operates on register
 . The notation \((\rho , \sigma )\) denotes a state on two registers that may be entangled. The letters qpt stands for quantum polynomial time.
. The notation \((\rho , \sigma )\) denotes a state on two registers that may be entangled. The letters qpt stands for quantum polynomial time.
Fix a prime p. A qupit in pure state \(|\phi \rangle \) is a unit vector in the p-dimensional Hilbert space \(\mathbb {C}^{p}\) and can be identified with the density operator \(\textsf{Mixed}\left[ |\phi \rangle \right] := |\phi \rangle \!\langle \phi |\). The set of n-qupit mixed states, denoted \(\mathcal {D}^{n}\), consists of positive semi-definite operators on \(\mathbb {C}^{p^n}\) with trace 1. We sometimes identify a mixed state \(\rho \) with its purification, which is a pure state \(|\phi \rangle \) such that \(\textsf{Mixed}\left[ |\phi \rangle \right] \) has partial trace \(\rho \). We also consider sub-normalized mixed states, which are positive semi-definite operators with trace at most 1. We identify a distribution \(\{\rho _j\}\) of sub-normalized states with the state \(\mathbb {E}_j \rho _j\). Two sequences of sub-normalized states \(\rho (n), \sigma (n) \in \mathcal {D}^{\textrm{poly}(n)}\) are said to be statistically indistinguishable, denoted \(\rho \approx \sigma \), if they have trace distance \(\textrm{tr}|\rho (n)-\sigma (n)| = {\text {negl}}(n) \textrm{tr}(\rho (n))\).
3.1 Quantum Computation
A quantum operation is a completely positive, trace preserving (CPTP) map acting on mixed states. Any such map can be represented as \(\{A_j\}\) which maps a mixed state \(\rho \) to the mixed state \(\sum _j A_j \rho A_j^\dag \). Each \(A_j\) defines a completely positive (CP) map \(\rho \mapsto A_j \rho A_j^\dag \). For example, measurement in the computation basis \(\{|j\rangle \}_{j \in \mathbb {Z}_p}\) is a CPTP map, whereas each projector \(|j\rangle \!\langle j|\) is only a CP map.
Consider the phase \(\omega = e^{2\pi i/p}\), the shift operator \(\textsf{X}: |j\rangle \mapsto |j+1\rangle \) and the clock operator \(\textsf{Z}: |j\rangle \mapsto \omega ^j |j\rangle \). Write \(\textsf{X}^{(x_1,\cdots ,x_n)} \textsf{Z}^{(z_1,\cdots ,z_n)} = \bigotimes _{j\in [n]}\textsf{X}^{x_j}\textsf{Z}^{z_j}\) where each \(x_j, z_j \in \mathbb {Z}_p\). We define the Pauli basis \(\mathscr {P}^*_n = \{\textsf{X}^x \textsf{Z}^z ~|~ x,z \in \mathbb {Z}_p^n\}\), which is a basis for the space of linear operators on \(\mathbb {C}^{p^n}\). Decomposing a linear operator according to this basis is called the Pauli decomposition. We identify the Pauli \(P_a = \textsf{X}^{x_a} \textsf{Z}^{z_a} \in \mathscr {P}^*_n\) with the string \((z_a, x_a) = (z(P_a), x(P_a)) \in \mathbb {Z}_p^{2n}\). Define the Pauli group \(\mathscr {P}_n\) as \(\{\omega ^k \textsf{X}^x \textsf{Z}^z ~|~ k \in \mathbb {Z}_p, ~x,z \in \mathbb {Z}_p^n\}\) and the Clifford group \(\mathscr {C}_n\) as the normalizer of \(\mathscr {P}_n\) in the unitary group quotient by global phases. That is, a unitary \(C \in \mathscr {C}_n\) if and only if for all \(A \in \mathscr {P}_n\), \(CAC^\dag \in \mathscr {P}_n\).
The Clifford group is generated by the Fourier transform gate \(\textsf{H}: |j\rangle \mapsto \frac{1}{\sqrt{p}}\varSigma _k~ \omega ^{jk} |k\rangle \), the phase gate \(\textsf{S}: |j\rangle \mapsto \omega ^{j(j-1)/2} |j\rangle \) and the sum gate \(\textsf{CX}: |j,k\rangle \mapsto |j,k+j\rangle \) [15]. When \(p=2\), the phase gate is defined as \(\textsf{S}: |j\rangle \mapsto i^{j}|j\rangle \) instead. One can sample uniformly random Clifford gates in polynomial time [19, 27]. We denote
 as the abbreviation of
as the abbreviation of
 .
.
Universal quantum computation can be carried out with Clifford gates and \(\textsf{T}\) gates, where \(\textsf{T}: |j\rangle \mapsto e^{\frac{2\pi i \eta _j}{p^2}}|j\rangle \) with \(\eta _j= p\left( {\begin{array}{c}j\\ 3\end{array}}\right) -j\left( {\begin{array}{c}p\\ 3\end{array}}\right) +\left( {\begin{array}{c}p+1\\ 4\end{array}}\right) \) [12]. When \(p=2\), the \(\textsf{T}\) gate is defined as \(\textsf{T}: |j\rangle \mapsto e^{\frac{\pi i j}{4}}|j\rangle \) instead. Although \(\textsf{T}\) gate is not in the Clifford group, it can be applied using classically controlled (i.e., adaptive) Clifford operations with the help of the \(\textsf{T}\) state \(|\textsf{T}\rangle =\textsf{T}|+\rangle \), where \(|+\rangle =\frac{1}{\sqrt{p}}\sum _{j=0}^{p-1} |j\rangle \). \(\textsf{T}\) states can be purified from noisy ones using classically controlled Clifford gates [10, 12].
3.2 Quantum One-Time Pad
Definition 1
A quantum one-time pad (QOTP) with key \(P \in \mathscr {P}_n\) is a symmetric-key encryption scheme that consists of the following two algorithms.
-
Encryption: \(\mathsf {QOPT.Enc}_P(\rho ):= P \rho P^\dag \).
-
Decryption: \(\mathsf {QOPT.Dec}_P(\rho ):= P^\dag \rho P\).
It is well known that the ciphertext under QOTP is maximally mixed:
Lemma 1
(Pauli Twirl). For every
 , it holds that
, it holds that

The same result holds when P is randomly sampled from the Clifford group \(\mathscr {C}_n\). Moreover, it is well known that QOTP can split a quantum attack into a probabilistic combination of Pauli attacks. This work considers a specific scenario where an untrusted party measures a state which is protected under QOTP. We formulate the following lemma, which shows that any attack would be equivalent to a probabilistic combination of Pauli attacks that cause different shifts. We prove the lemma in the full version of this paper.
Lemma 2
(Pauli Twirl with Measurement). Let
 be a state and \(v \in \mathbb {Z}_p^n\) be the target measurement result. For any attack
be a state and \(v \in \mathbb {Z}_p^n\) be the target measurement result. For any attack
 applied on the QOTP-protected state, we have
applied on the QOTP-protected state, we have

3.3 Quantum Authentication Code
Quantum authentication code detects whether unauthorized alterations have been made to the data. When alternation is detected, the algorithm will output a rejection symbol \(\bot \).
Definition 2
(Quantum Authentication Code, [5]). A quantum authentication code consists of three algorithms. The key generation algorithm \(\textsf{Gen}\) takes in the security parameter \(1^\lambda \) and the message size \(1^\ell \) and outputs a random secret key \(\textsf{sk}\). The encoding algorithm \(\textsf{Enc}\) maps a secret key \(\textsf{sk}\) and a quantum message on
 to a quantum ciphertext on
to a quantum ciphertext on
 . The decoding algorithm \(\textsf{Dec}\) maps a secret key \(\textsf{sk}\) and a quantum ciphertext on
. The decoding algorithm \(\textsf{Dec}\) maps a secret key \(\textsf{sk}\) and a quantum ciphertext on
 to a quantum message
to a quantum message
 . These algorithms should satisfy the following properties.
. These algorithms should satisfy the following properties.
-
Completeness: For every secret key \(\textsf{sk}\), it holds that \(\textsf{Dec}_\textsf{sk}\circ \textsf{Enc}_\textsf{sk}= \mathbbm {1}\).
-
Security: For any quantum map \({{\mathcal {A}}}\), there exists two CP maps \({{\mathcal {A}}}_{{\textsf{Acc}}}\) and \({{\mathcal {A}}}_{{\textsf{Rej}}}\) such that \({{\mathcal {A}}}_{{\textsf{Acc}}} + {{\mathcal {A}}}_{{\textsf{Rej}}}\) is trace preserving and that for any (possibly entangled) states \({\rho }, {\rho _{{\textsf{aux}}}}\),

Here, we recall the Clifford authentication code from [2]. The key generation algorithm outputs a uniformly random Clifford gate
 . The encoding procedure augments the message state
. The encoding procedure augments the message state
 with traps
with traps
 and applies
and applies
 . The decoding procedure applies \(E^\dag \) followed by measuring the register
. The decoding procedure applies \(E^\dag \) followed by measuring the register
 in the computational basis. If the measurement results are not all zero, the content of
in the computational basis. If the measurement results are not all zero, the content of
 is replaced with \(|\bot \rangle \). The Clifford authentication code satisfies Definition 2. The following lemma is crucial to its proof, and we will use the lemma directly later on.
is replaced with \(|\bot \rangle \). The Clifford authentication code satisfies Definition 2. The following lemma is crucial to its proof, and we will use the lemma directly later on.
Lemma 3
(Pauli Partitioning by Clifford, [2, 13]). For every Pauli operators \(Q, Q' \in \mathscr {P}_n\) that do not lie in \(\{ \omega ^k I ~|~ k \in \mathbb {Z}_p \}\), it holds that
The Clifford code also supports homomorphic computation for any Clifford operator. Consider a Clifford-code ciphertext
 with secret key \(\textsf{sk}= {E}\). To perform a Clifford gate G on \(\rho \), it suffices to update the secret key as \(\textsf{sk}' = {E} {G^{\dag }}\). This works because we have \(\textsf{Enc}_\textsf{sk}(\rho ) = E({\rho }, {|0\rangle ^{\otimes \lambda }}) = {E} {G^{\dag }} ({G\rho }, {|0\rangle ^{\otimes \lambda }}) = \textsf{Enc}_{\textsf{sk}'}(G(\rho ))\).
with secret key \(\textsf{sk}= {E}\). To perform a Clifford gate G on \(\rho \), it suffices to update the secret key as \(\textsf{sk}' = {E} {G^{\dag }}\). This works because we have \(\textsf{Enc}_\textsf{sk}(\rho ) = E({\rho }, {|0\rangle ^{\otimes \lambda }}) = {E} {G^{\dag }} ({G\rho }, {|0\rangle ^{\otimes \lambda }}) = \textsf{Enc}_{\textsf{sk}'}(G(\rho ))\).
3.4 Quantum Error-Correction Code
Quantum error correction code protects quantum states from errors as long as the number of errors is limited. In this work, it suffices to consider erasure errors.
Definition 3
(Quantum Error Correction Code). A \([[n,k]]_p\) quantum error correction code consists of two algorithms. The encoding algorithm \({\mathsf {QECC.Enc}}: \mathcal {D}^{k}\rightarrow \mathcal {D}^{n}\) encodes a k-qupit message into a \(n\)-qupit codeword. The decoding algorithm \(\mathsf {QECC.Dec}:\mathcal {D}^{n}\times \{0,1\}^n\rightarrow \mathcal {D}^{k}\) takes a modified codeword and its location of errors and outputs a k-qupit message. A quantum error correction code is said to correct \(t\) erasure errors, if for any \(\rho \in \mathcal {D}^{k}\) and any quantum channel
 acting on
acting on
 qupits, it holds that
qupits, it holds that

where \(\mathbbm {1}_R\) specifies the locations of
 among the \(n\) qupits.
among the \(n\) qupits.
To arrive at best-of-both-worlds security for any threshold \(t< \frac{n}{2}\), we can use the quantum polynomial code of [1], which satisfies other desirable properties.
Lemma 4
(Polynomial Code, [1]). For every \(t< \frac{n}{2}\) and prime \(p > n\), there exists a \([[n,1]]_p\) quantum error correction code that corrects \(t\) erasure errors with the following additional properties:
-
Syntax: \({\mathsf {QECC.Enc}}\) applies a Clifford gate to input \(\rho \) and ancilla \(|0\rangle ^{\otimes (n-1)}\).
-
Fault-Tolerant Computation: \(\textsf{X}, \textsf{Z}, \textsf{CX}, \textsf{H}\) gates and measurement in the computational basis can be applied to the message \(\rho \) by locally applying some of these operators to the individual components of the codeword using ancillas.
A state injection technique shows that the \(\textsf{S}\) gate can be performed through \(\textsf{X}, \textsf{Z}, \textsf{CX}^{-1}\) gates and measurements in the computational basis using ancillas. Hence, the entire Clifford group \(\mathscr {C}_n = \langle \textsf{S}, \textsf{H}, \textsf{CX}\rangle \) can be applied fault-tolerantly using ancillas under the polynomial code.
3.5 Quantum Teleportation
Quantum teleportation allows parties to transmit quantum messages using only classical communication and pre-shared quantum states. Below, an EPR pair
 of length n stands for the state
of length n stands for the state
 where \(|\varPhi ^+\rangle = \frac{1}{\sqrt{p}} \varSigma _{j=0}^{p-1} |j, j\rangle \).
where \(|\varPhi ^+\rangle = \frac{1}{\sqrt{p}} \varSigma _{j=0}^{p-1} |j, j\rangle \).
Definition 4
(Quantum Teleportation Without Measurement). Let \((e_S, e_R)\) be an EPR pair of length n independent to a state \(\psi \in \mathcal {D}^{n}\). Quantum teleportation consists of two algorithms. We will also abbreviate \(\mathsf {TP.Send}\) as \(\textsf{TP}\).
-
 applies
applies
 to
to
 and outputs
and outputs
 .
. -
 applies \(({\textsf{X}}^x {\textsf{Z}}^z)^\dag \) to
applies \(({\textsf{X}}^x {\textsf{Z}}^z)^\dag \) to
 and outputs
and outputs
 .
.
When we speak of teleporting a state
 via register
via register
 , we mean to apply
, we mean to apply
 , measure
, measure
 in the computational basis and interpret the measurement result (z, x) as the Pauli \(\textsf{X}^x \textsf{Z}^z\). The following lemma states that the teleportation result \(\textsf{X}^x \textsf{Z}^z\) can help recover the original quantum message \(\psi \).
in the computational basis and interpret the measurement result (z, x) as the Pauli \(\textsf{X}^x \textsf{Z}^z\). The following lemma states that the teleportation result \(\textsf{X}^x \textsf{Z}^z\) can help recover the original quantum message \(\psi \).
Lemma 5
Let \((\psi , \tau )\) be a purified state independent of \((e_S,e_R)\). Then

4 Model and Definition
We focus on interactive protocols between n parties \(\textsf{P}_1,\cdots ,\textsf{P}_n\) with quantum computational power. They can communicate using pairwise authenticated quantum channels and a broadcast channel for classical messages. We work in the synchronous communication model where the protocol proceeds in rounds, and each message will certainly arrive at the end of each round. In addition, we consider the presence of a protocol observer \(\textsf{O}\) who passively receives and records classical information from the broadcast channel all the time.Footnote 4 The adversary \({\mathcal {A}}\) can statically corrupt a set \(I \subset \{\textsf{P}_1, \cdots , \textsf{P}_n\}\) of up to \(n-1\) parties.
The quantum computation to be performed is modeled as a quantum circuit C, which takes n parts of quantum inputs and produces n parts of quantum outputs. Without loss of generality, we assume that the corresponding inputs and outputs have equal size. We always apply [10, 12] to convert \({C}\) into the following format, incurring only a polynomial growth in description size. The ancilla \(\phi _{{\textsf{anc}}}\) consists of \(|0\rangle \) and \(|\textsf{T}\rangle \) states, and the circuit operates on a total of \(\ell _{{\text {total}}} = \sum _{i} \ell _i + d\) qupits.

4.1 The Ideal World of BoBW-MPQC-PVIA
A multi-party quantum computation protocol is defined using the real vs. ideal paradigm. In the ideal world, the parties delegate the computation C to a trusted party \(\textsf{T}\). The only way for the corrupted parties to interrupt the delegation is to ask \(\textsf{T}\) to abort, in which case \(\textsf{T}\) publicly announces their identities. The ideal world of best-of-both-worlds multi-party quantum computation secure with publicly verifiable identifiable abort is formally defined as follows. We denote its joint output distribution as \({\textsf{Ideal}}^{{\textsf{MPQC}}}_{{\mathcal {A}}_I(\rho _{{\textsf{aux}}})}(1^{\lambda }, t, C, \rho _1, \cdots , \rho _n)\).

For a protocol \(\varPi \), we denote by \({\textsf{Real}}^{\varPi }_{{\mathcal {A}}_I(\rho _{{\textsf{aux}}})}(1^{\lambda }, \rho _1, \cdots , \rho _n)\) the joint output distribution of the honest parties, the observer, and the adversary at the end of protocol \(\varPi \) when executed by \(\textsf{P}_i(\rho _i)\) in the presence of an adversary \({\mathcal {A}}_I(\rho _{{\textsf{aux}}})\) corrupting parties in I. For a protocol \(\varPi \) with a trusted setup \(\varSigma \), we define \({\textsf{Real}}^{\varPi \circ \varSigma }_{{\mathcal {A}}_I(\rho _{{\textsf{aux}}})} (1^{\lambda }, {\rho _1, \cdots , \rho _n})\) similarly with \(\varSigma \) being executed by a trusted party prior to \(\varPi \).
Definition 5
We say that a protocol \(\varPi \) is a best-of-both-worlds multi-party quantum computation secure with publicly verifiable identifiable abort (BoBW-MPQC-PVIA) of threshold \(t\) over a circuit \({C}\), if for every \(|I| \le n-1-t\) and every non-uniform (qpt) adversary \({\mathcal {A}}_I\) corrupting parties in I, there is a non-uniform (qpt) simulator \(\textsf{Sim}_I\) corrupting parties in I, such that for any quantum inputs \(\rho _i \in \mathcal {D}^{\ell _i}\), \(i\in [n]\),
If the protocol \(\varPi \) has a trusted setup \(\varSigma \), the indistinguishability requirement is replaced with
Definition 6
We say that \(\varPi \) is a multi-party quantum computation secure with publicly verifiable identifiable abort (MPQC-PVIA) over a circuit \({C}\) if Definition 5 holds for \(t= 0\).
4.2 (Preprocessing) MPC-Hybrid Model
Following [3, 6, 17, 18], we assume an ideal functionality \({\textsf{cMPC}}\) for reactiveFootnote 5 classical multiparty computation within our MPQC protocol. The ideal world of classical MPC is similar to that of MPQC defined in section Sect. 4.1, but allows only classical messages and classical computation. In additional to producing n private outputs, the classical computation is allowed to generate an additional output which the ideal functionality publicly outputs if there is no abort. In our presentation, we will simply view \({\textsf{cMPC}}\) as a trusted classical party. We refer this setting as the MPC-hybrid model. The preprocessing MPC-hybrid model extends the MPC-hybrid model by allowing an input-independent trusted setup to be executed prior to the actual protocol.
One can instantiate the MPC ideal functionality using a post-quantum best-of-both-worlds MPC protocol with publicly verifiable identifiable abort and publicly verifiable output. In the literature [3, 6, 17], post-quantum MPCs are typically derived from classical MPC protocols featuring black-box, straight-line simulations and reductions in the CRS model to circumvent the challenging issue of quantum rewinding in proving post-quantum security. In our case, we begin with the MPC-PVIA protocol of [7] Theorem 1.3 that has black-box, straight-line simulations and reductions and then apply the [21] compiler to obtain BoBW security. To facilitate straight-line simulation, we replace the commitment scheme in [21] with a UC-secure commitment scheme akin to the one in [7]. The resulting BoBW-MPC-PVIA protocol achieves post-quantum security in the CRS model, assuming post-quantum OT and a classical broadcast channel.Footnote 6
5 Auditable Quantum Authentication (AQA)
This section presents a new primitive called Auditable Quantum Authentication (AQA) that lets a sender send quantum messages to a receiver and be accountable for his sending action. AQA is designed to identify the malicious sender only, while the receiving behavior is automatically guaranteed by successfully passing the test. In contrast to traditional quantum authentication codes like the Clifford or Trap codes, which necessitate the receiver to verify the checking bits, AQA adopts a different approach. It obliges the sender to generate the proof that should be verified by the auditor.
Definition 7 (Auditable Quantum Authentication)
[Auditable Quantum Authentication] An auditable quantum authentication scheme consists of the following five algorithms:
-
\(\textsf{Setup}(1^\lambda , 1^\ell ) \rightarrow (\textsf{sk}, \phi _S, \phi _R)\) takes as input the security parameter \(\lambda \) and the message length \(\ell \) and outputs a classical secret key \(\textsf{sk}\), a quantum sending state \(\phi _S\) and a quantum receiving state \(\phi _R\).
-
\(\textsf{Enc}(\textsf{sk}, \rho ) \rightarrow \sigma \) takes as input a classical secret key \(\textsf{sk}\), a quantum message state \(\rho \in \mathcal {D}^{\ell }\) and outputs a quantum authenticated state \(\sigma \).
-
\(\textsf{Send}(\sigma , \phi _S) \rightarrow \textsf{pf}\) takes as input a quantum authenticated state \(\sigma \), a quantum sending state \(\phi _S\) and outputs a classical proof \(\textsf{pf}\).
-
\(\textsf{Audit}(\textsf{sk}, \textsf{pf}) \rightarrow \textsf{dk}\) is a classical algorithm that takes as input a secret key \(\textsf{sk}\), a proof \(\textsf{pf}\) and outputs a decryption key \(\textsf{dk}\). When the proof is invalid, \(\textsf{dk}\) will be set as \(\bot \).
-
\(\textsf{Recv}(\textsf{dk}, \phi _R) \rightarrow \rho '\) takes as input a classical decryption key \(\textsf{dk}\), a quantum receiving state \(\phi _R\) and outputs a quantum message state \(\rho '\). When \(\textsf{dk}= \bot \), \(\rho '\) will be set as \(\bot \).
These algorithms should satisfy the following properties:
-
Sender completeness: For every quantum message state \(\rho \in \mathcal {D}^{\ell }\), it holds that

-
Receiver security: There exists algorithms \(\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, \widetilde{\textsf{Audit}}\) such that \(\textsf{Recv}\circ \widetilde{\textsf{Enc}} = \mathbbm {1}\) and that for every completely positive map \({\mathcal {A}}\) and every possibly entangled quantum states \(\rho , \rho _{{\textsf{aux}}}\), it holds that
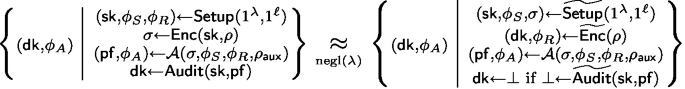
Sender completeness guarantees that the honest sender always passes the audit. Receiver security is defined through the indistinguishability of two kinds of executions, implying that whatever property is satisfied by the right-hand side will also hold up to a negligible error for the left-hand side.
In particular, receiver security captures the following properties. First, it guarantees that the sender’s inputs \((\sigma , \phi _S)\) are as if they can be generated independently of \(\rho \), and hence contain no information about the message \(\rho \). Similarly, the receiver’s input \(\phi _R\) is as if it already encodes \(\rho \). Second, \(\textsf{dk}\) is the only information required for the receiver to recover \(\rho \) from \(\phi _R\), and the honest receiver always obtains the true message given that the audit accepts. Third, all the adversarial sender can do, even if the sender and the receiver collude, is to completely destroy \(\textsf{dk}\) at the cost of making the audit output \(\bot \) at the same time Fig. 3.
5.1 Construction

5.2 Security
Theorem 5
Construction 1 is an Auditable Quantum Authentication scheme.
Proof
We take the following steps. First, we analyze the state \((\textsf{dk}, \phi _A)\) that results from executing \((\textsf{Setup}, \textsf{Enc}, {\mathcal {A}}, \textsf{Audit})\) in a row. Second, we prove sender completeness by plugging in \({\mathcal {A}}= \textsf{Send}\). Third, we show that the distribution of \((\textsf{dk}, \phi _A)\) generated above is indistinguishable from a simpler state. Last, we construct \(\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, \widetilde{\textsf{Audit}}\) that satisfy the requirements of receiver security.
Step 1. Without loss of generality, we assume that \({\mathcal {A}}\) has the same output length in \(\phi _A\) as the input length. We can also assume that
 produces the classical proof \(\textsf{pf}\) by measuring the registers
produces the classical proof \(\textsf{pf}\) by measuring the registers
 in the computational basis. Moreover, we can assume that the CP map \({\mathcal {A}}\) takes the form \(\tau \mapsto A \tau A^\dag \) because every CP map can be decomposed into a sum of such operators and indistinguishability of subnormalized states extends under addition. We denote the Pauli decomposition of
in the computational basis. Moreover, we can assume that the CP map \({\mathcal {A}}\) takes the form \(\tau \mapsto A \tau A^\dag \) because every CP map can be decomposed into a sum of such operators and indistinguishability of subnormalized states extends under addition. We denote the Pauli decomposition of
 as
as
 .
.
By definition, the execution of \(\textsf{Setup}\) and \(\textsf{Enc}\) yields a random classical key \(\textsf{sk}= (F, P_M, P_S, P_C, P_R)\) and quantum state

After the execution of \({\mathcal {A}}\), the joint state is

The first and second equalities follows from the definitions of \(A'\) and \(P_{M,S}\), and the last equality is by quantum teleportation. Let us define the linear functions
for every Clifford operator F. The joint state can be simplified as

The next step is to apply \(\textsf{Audit}\), which checks whether the value stored in
 is equal to \(L_F(\hat{P}) \oplus x(P_{M,S} \otimes P_C)\) for some \(\hat{P} \in \mathscr {P}_{\ell +\lambda }\). If there is such a \(\hat{P}\), then \(\textsf{Audit}\) outputs \(\textsf{dk}= P_R K_{F}(\hat{P})\); otherwise, it outputs \(\textsf{dk}= \bot \). To analyze the resulting state post-selected on finding \(\hat{P}\), we can apply Pauli twirl with target measurement result \( L_{F}(\hat{P})\) (lemma 2) using the Pauli decomposition of \(A'\). We obtain
is equal to \(L_F(\hat{P}) \oplus x(P_{M,S} \otimes P_C)\) for some \(\hat{P} \in \mathscr {P}_{\ell +\lambda }\). If there is such a \(\hat{P}\), then \(\textsf{Audit}\) outputs \(\textsf{dk}= P_R K_{F}(\hat{P})\); otherwise, it outputs \(\textsf{dk}= \bot \). To analyze the resulting state post-selected on finding \(\hat{P}\), we can apply Pauli twirl with target measurement result \( L_{F}(\hat{P})\) (lemma 2) using the Pauli decomposition of \(A'\). We obtain
where we change variables \(P_R \leftarrow P_{R} K_{F}(P)\) in the second line and \(P \leftarrow \hat{P}/P\) in the third line. Summing the post-selected states corresponding to every Pauli \(\hat{P} \in \mathscr {P}_{\ell +\lambda }\), we obtain the state conditioned that \(\textsf{Audit}\) accepts as

Similarly, the state conditioned that \(\textsf{Audit}\) rejects is

Step 2. To see sender completeness, we take \({\mathcal {A}}= \textsf{Send}\), which applies
 followed by measuring
followed by measuring
 in the computational basis. The induced \(A' = A \; {\textsf{TP}^\dag }\) is a measurement in the computational basis, and the Pauli decomposition of \(A'\) involves only terms with \(x(Q) = 0 \in \textsc {Range}(L_F)\). For such \(A'\), expression (2) shows that \(\textsf{Audit}\) never outputs \(\bot \).
in the computational basis. The induced \(A' = A \; {\textsf{TP}^\dag }\) is a measurement in the computational basis, and the Pauli decomposition of \(A'\) involves only terms with \(x(Q) = 0 \in \textsc {Range}(L_F)\). For such \(A'\), expression (2) shows that \(\textsf{Audit}\) never outputs \(\bot \).
Step 3. We claim that (1)+(2) is statistically indistinguishable to (3)+(4).


The trace distance between (1) and (3) is
which follows from the triangle inequality, the positivity of \(\textsf{Mixed}\left[ \cdot \right] \), and the observation that each x has at most one P such that \(L_F(P)=x\). Similarly, the trace distance between (2) and (4) is
which is equal to (5). By the triangle inequality, the trace distance between (1)+(2) and (3)+(4) is upper bounded by
The first inequality follows from the Pauli partitioning by Clifford (lemma 3). This establishes the statistical indistinguishability between (1)+(2) and (3)+(4).
Step 4. Finally, we construct \(\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, \widetilde{\textsf{Audit}}\) and prove receiver security.

It is direct to see that \(\textsf{Recv}\circ \widetilde{\textsf{Enc}} = \mathbbm {1}\). We now analyze the state \((\textsf{dk}, \phi _A)\) that results from executing \((\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, {\mathcal {A}})\) in a row and replacing \(\textsf{dk}\leftarrow \bot \) if \(\bot \leftarrow \widetilde{\textsf{Audit}}\). The execution of \(\widetilde{\textsf{Setup}}\) and \(\widetilde{\textsf{Enc}}\) yields random classical keys \(\textsf{sk}=r,\; \textsf{dk}=P\) and quantum state

After the execution of \({\mathcal {A}}\), the joint state is

The next step is to apply \(\widetilde{\textsf{Audit}}\), which corresponds to the projection
 . The state conditioned that \(\widetilde{\textsf{Audit}}\) accepts can be analyzed through Pauli twirl with target measurement result 0 (lemma 2), which yields exactly (3). Similarly, the state conditioned that \(\widetilde{\textsf{Audit}}\) rejects is exactly (4). Hence, \((\textsf{dk},\phi _A)\) generated from \((\textsf{Setup}, \textsf{Enc}, {\mathcal {A}}, \textsf{Audit})\) and from \((\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, {\mathcal {A}}, \widetilde{\textsf{Audit}})\) are indistinguishable, which establishes receiver security.
. The state conditioned that \(\widetilde{\textsf{Audit}}\) accepts can be analyzed through Pauli twirl with target measurement result 0 (lemma 2), which yields exactly (3). Similarly, the state conditioned that \(\widetilde{\textsf{Audit}}\) rejects is exactly (4). Hence, \((\textsf{dk},\phi _A)\) generated from \((\textsf{Setup}, \textsf{Enc}, {\mathcal {A}}, \textsf{Audit})\) and from \((\widetilde{\textsf{Setup}}, \widetilde{\textsf{Enc}}, {\mathcal {A}}, \widetilde{\textsf{Audit}})\) are indistinguishable, which establishes receiver security.
6 MPQC-PVIA with Trusted Setup
Here, we present our MPQC protocol with a trusted setup. We make use of the Clifford-form \(\textsf{AQA}\) developed in the previous section together with \({\textsf{cMPC}}\) to achieve PVIA security. For simplicity, we work with qubits i.e., \(p=2\) here. The protocol is divided into two parts:
-
1.
An offline phase using a trusted setup: a trusted setup \(\varSigma ^\textsf{PVIA}\) prepares EPR pairs \((\mathcal {S}_i,\mathcal {R}_i)\) of length \(\ell _i\) and distributes the sending side \(\mathcal {S}_i\) to party \(\textsf{P}_i\). Next, the trusted setup encodes all of the receiving sides \(\mathcal {R}_1,\cdots ,\mathcal {R}_n\) and the ancilla \(\phi _{{\textsf{anc}}}\) into a single ciphertext \(\sigma \), which is sent to the server. This server can be any participant in the MPQC game; for simplicity, we can assume it’s the first party. The above quantum states will later be utilized in the input encoding stage. The trusted setup then executes \(\textsf{AQA}.\textsf{Setup}\) to obtain portals for the output delivery stage. Finally, the trusted setup transmits information related to the secret keys to \({\textsf{cMPC}}\).
-
2.
An online phase: every party acts as a client who teleports their input to the server. Directed by \({\textsf{cMPC}}\), the server evaluates the circuit on the ciphertext \(\sigma \). Finally, the server returns the outputs to all clients using AQA.


6.1 Security
Theorem 6
\((\varSigma ^{\textsf{PVIA}}, \varPi ^{\textsf{PVIA}})\) is a multi-party quantum computation secure with publicly verifiable identifiable abort in the preprocessing MPC-hybrid model as defined in Definition 6. i.e., For every non-uniform (qpt) adversary \({\mathcal {A}}\) corrupting party set I with \(|I| \le n-1\), there is a non-uniform (qpt) adversary \(\textsf{Sim}_{\mathcal {A}}\) corrupting I, such that for any (possibly entangled) states \(\rho _1,\cdots \rho _n, \rho _{{\textsf{aux}}}\),
Below is the simulator we use for Theorem 6. We refer the readers to our full version for the proof.

7 BoBW-MPQC-PVIA with Trusted Setup
In this section, we describe our construction of best-of-both-worlds multi-party quantum computation protocol secure with publicly verifiable identifiable abort (BoBW-MPQC-PVIA). The protocol is similar to the MPQC-PVIA protocol but with n servers instead. \(\textsf{P}_j\) will be assigned as server j. The protocol is divided into two parts:
-
1.
An offline setup: a setup \(\varSigma ^{\textsf{BoBW}}\) prepares EPR pairs \((\mathcal {S}_i,\mathcal {R}_i)\) of length \(\ell _i\) and distributes the sending side \(\mathcal {S}_i\) to party \(\textsf{P}_i\). Next, the setup uses a QECC scheme to encode every \(\mathcal {R}_i\) into \(\{\mathcal {R}_i^{(j)}\}_{j\in [n]}\) and the ancilla \(\phi _{{\textsf{anc}}}\) into \(\{\phi _{{\textsf{anc}}}^{(j)}\}_{j \in [n]}\). Afterwards, the setup encrypts the j-th part of the QECC codewords into a Clifford ciphertext and send it to server j. The setup then executes \(\textsf{AQA}.\textsf{Setup}\) to prepare for the output delivery stage. Finally, the setup sends the secret keys to \({\textsf{cMPC}}\).
-
2.
An online phase: every party acts as a client who teleports their input to the servers. Directed by \({\textsf{cMPC}}\), the servers evaluate the circuit in a fault-tolerant manner. Each server j operates only on the ciphertext that encrypts the j-th part of the QECC codewords. Finally, the servers returns the outputs to the clients using AQA.
Theorem 7
For every \(t< \frac{n}{2}\), there is a best-of-both-worlds multi-party quantum computation secure with publicly verifiable identifiable abort of threshold \(t\) in the preprocessing MPC-hybrid model as in Definition 5.
We refer the readers to our full version for the formal protocol and proof. They bear resemblance to those of Theorem 6 with the additional use of a \([[n,1]]_p\) polynomial code that corrects \(t\) erasure errors, which exists by Lemma 4.
8 BoBW-MPQC-PVIA Without Trusted Setup
So far, we have demonstrated an BoBW-MPQC-PVIA protocol \(\varPi ^{{\textsf{BoBW}}}\) in the preprocessing model with a trusted setup \(\varSigma ^{{\textsf{BoBW}}}\). Now, we will illustrate how to instantiate the preprocessing phase without a trusted setup. Our approach involves using MPQC-SWIA e.g., [3] to implement the preprocessing phase. Note that [3] requires a post-quantum fully homomorphic encryption assumption to achieve the security; however, we do not need this assumption when we want to compute circuits that have no inputs and apply only Clifford gates to \(|0\rangle \)’s and \(|\textsf{T}\rangle \)’s. We defer the explicit MPQC-SWIA construction to the full version of this paper. We reformulate MPQC-SWIA as the following lemma.
Lemma 6
(MPQC-SWIA). There is a multi-party quantum computation \(\varPi ^{\textsf{SWIA}}\) secure with identifiable abort in the MPC-hybrid model that computes quantum circuit \({C}\), given that \({C}\) takes no inputs and only applies Clifford to ancillary \(|0\rangle \) and \(|\textsf{T}\rangle \) states. That is, for every non-uniform (qpt) adversary \({\mathcal {A}}\) corrupting party set I, there is a non-uniform (qpt) adversary \(\textsf{Sim}^{\textsf{SWIA}}_{{\mathcal {A}}}\) corrupting I, such that

We say an execution succeeds if every party receives their part of the circuit output. Whenever the execution fails, all parties get to know how they have been partitioned into two groups. An honest party can infer that the group he does not belong to (i.e., \(I_{ {\texttt {abort}}}\)) is the set of malicious parties who interfered the computation.
In contrast to [3] where the partition information serves the purpose of SWIA, we utilize the partition information to design a preprocessing procedure that always succeeds. Such a preprocessing procedure will be suitable for replacing the setup of MPQC-PVIA.
8.1 Protocol
First, we let the parties run MPQC-SWIA over the setup circuit \(\varSigma ^{{\textsf{BoBW}}}\) that the trusted setup is supposed to run. If the MPQC-SWIA fails, the parties will be divided into two groups. Each group will then ignore other groups and run MPQC-SWIA independently. By iterating this process, each party will eventually find a group in which the MPQC-SWIA succeeds and receive an output of the setup circuit. This constitutes our preprocessing procedure. Note that we do not publicly identify anyone during this stage.
After obtaining the output of the setup circuit, every party can run the protocol \(\varPi ^{{\textsf{BoBW}}}\) within their group to obtain their MPQC output. It is reasonable for each group to operate independently, as they view other groups as untrustworthy. Parties within a group can set the inputs of the parties outside the group as some default inputs such as \(|0\rangle \). Moreover, MPQC-SWIA guarantees that the honest parties are always in the same group, so they will jointly compute their outputs. Our approach circumvents the false accusation problem encountered in [3] because the parties in our protocol no longer accuse between groups. Instead, each group runs its own \(\varPi ^{{\textsf{BoBW}}}\), which only aborts dishonest members.


Theorem 8
\(\varPi ^{{\textsf{MPQC}}}\) is a best-of-both-worlds multi-party quantum computation with publicly verifiable identifiable abort of threshold \(t\) in the MPC-hybrid model.
Proof sketch
We want to show that the real world and the ideal world are indistinguishable using the following simulator. Let \(\textsf{Sim}^{{\textsf{BoBW}}}\) be the simulator for \((\varSigma ^{{\textsf{BoBW}}},\varPi ^{{\textsf{BoBW}}})\). We regard \({\mathcal {A}}\) as a stateful adversary throughout.

We show indistinguishability by gradually modifying the real world. Since the sub-protocols \(\varPi ^{\textsf{SWIA}}\) are executed sequentially, we can apply Lemma 6 to replace them with ideal executions of \({\textsf{Ideal}}^{\textsf{SWIA}}\) one by one, incurring only a negligible difference. Similarly, we can apply Theorem 7 to replace the real executions of \(\varPi ^{{\textsf{BoBW}}}\) with ideal executions of \({\textsf{Ideal}}^{{\textsf{MPQC}}}\) one by one. Next, we replace the ideal execution of \({\textsf{Ideal}}^{{\textsf{MPQC}}}\) that involves only the group S that contains all honest parties with an ideal execution of \({\textsf{Ideal}}^{{\textsf{MPQC}}}\) that involves all parties, where parties not in S always send default inputs. Also, for every corruption list output by a group other than S, we let the malicious parties in the list send \( {\texttt {abort}}\) to the above \({\textsf{Ideal}}^{{\textsf{MPQC}}}\). It is direct to see that such a replacement always produces the same outputs and abort decisions. Merging all the simulators and ideal functionalities except for \({\textsf{Ideal}}^{{\textsf{MPQC}}}\) in the last hybrid world gives us simulator 2. Thus, the real and ideal worlds are indistinguishable. \(\square \)
Notes
- 1.
There are different flavors of best-of-both-worlds security. For example, [8, 23] consider MPC protocols with full security against \(\lfloor \frac{n-1}{2} \rfloor \) malicious parties and \((1/p)\)-security with abort against \(n-1\) malicious parties. The notion of \((1/p)\)-security only requires an inverse polynomial error in distinguishing the real/ideal world.
- 2.
- 3.
Similar to previous subsection, this setup can be instantiated using MPQC-SWIA.
- 4.
Alternatively, one can assume a public bulletin board from which the observer can retrieve the broadcast information.
- 5.
The functionality can be equipped with an internal state that may be taken into account when it is called next time.
- 6.
Note that [7] additionally assumes a 2-correlation robust hash function for the practical efficiency of garbled circuits, which can be avoided if we only aim for feasibility.
References
Aharonov, D., Ben-Or, M.: Fault-tolerant quantum computation with constant error. In: Proceedings of the Twenty-ninth Annual ACM Symposium on Theory of Computing, pp. 176–188 (1997). https://doi.org/10.1145/258533.258579
Aharonov, D., Ben-Or, M., Eban, E., Mahadev, U.: Interactive proofs for quantum computations. arXiv preprint arXiv:1704.04487 (2017). https://doi.org/10.48550/arXiv.1704.04487
Alon, B., Chung, H., Chung, K.-M., Huang, M.-Y., Lee, Y., Shen, Y.-C.: Round efficient secure multiparty quantum computation with identifiable abort. In: Malkin, T., Peikert, C. (eds.) Advances in Cryptology – CRYPTO 2021: 41st Annual International Cryptology Conference, CRYPTO 2021, Virtual Event, August 16–20, 2021, Proceedings, Part I, pp. 436–466. Springer International Publishing, Cham (2021). https://doi.org/10.1007/978-3-030-84242-0_16
Ambainis, A., Buhrman, H., Dodis, Y., Rohrig, H.: Multiparty quantum coin flipping. In: Proceedings of 19th IEEE Annual Conference on Computational Complexity, 2004, pp. 250–259. IEEE (2004). https://doi.org/10.1109/CCC.2004.1313848
Barnum, H., Crépeau, C., Gottesman, D., Smith, A., Tapp, A.: Authentication of quantum messages. In: The 43rd Annual IEEE Symposium on Foundations of Computer Science, 2002. Proceedings, pp. 449–458. IEEE (2002). https://doi.org/10.1109/SFCS.2002.1181969
Bartusek, J., Coladangelo, A., Khurana, D., Ma, F.: On the round complexity of secure quantum computation. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12825, pp. 406–435. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84242-0_15
Baum, C., Orsini, E., Scholl, P., Soria-Vazquez, E.: Efficient constant-round MPC with identifiable abort and public verifiability. In: Micciancio, D., Ristenpart, T. (eds.) CRYPTO 2020. LNCS, vol. 12171, pp. 562–592. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-56880-1_20
Beimel, A., Lindell, Y., Omri, E., Orlov, I.: 1/p-Secure multiparty computation without an honest majority and the best of both worlds. J. Cryptol. 33(4), 1659–1731 (2020). https://doi.org/10.1007/s00145-020-09354-z
Ben-Or, M., Crepeau, C., Gottesman, D., Hassidim, A., Smith, A.: Secure multiparty quantum computation with (only) a strict honest majority. In: 2006 47th Annual IEEE Symposium on Foundations of Computer Science (FOCS’06). IEEE (2006). https://doi.org/10.1109/FOCS.2006.68
Bravyi, S., Kitaev, A.: Universal quantum computation with ideal clifford gates and noisy ancillas. Phys. Rev. A 71, 022316 (2005). https://doi.org/10.1103/PhysRevA.71.022316
Broadbent, A., Ji, Z., Song, F., Watrous, J.: Zero-knowledge proof systems for qma. In: 2016 IEEE 57th Annual Symposium on Foundations of Computer Science (FOCS), pp. 31–40. IEEE (2016). https://doi.org/10.1109/FOCS.2016.13
Campbell, E.T., Anwar, H., Browne, D.E.: Magic-state distillation in all prime dimensions using quantum reed-muller codes. Phys. Rev. X 2(4), 041021 (2012). https://doi.org/10.1103/PhysRevX.2.041021
Chau, H.F.: Unconditionally secure key distribution in higher dimensions by depolarization. IEEE Trans. Inf. Theory 51(4), 1451–1468 (2005). https://doi.org/10.1109/TIT.2005.844076
Chung, K.M., Lee, Y., Lin, H.H., Wu, X.: Constant-round blind classical verification of quantum sampling. In: Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 707–736. Springer (2022). https://doi.org/10.1007/978-3-031-07082-2_25
Clark, S.: Valence bond solid formalism for d-level one-way quantum computation. J. Phys. A: Math. Gen. 39(11), 2701 (2006). https://doi.org/10.1088/0305-4470/39/11/010
Crépeau, C., Gottesman, D., Smith, A.: Secure multi-party quantum computation. In: Proceedings of the Thiry-fourth Annual ACM symposium on Theory of computing - STOC ’02. ACM Press (2002). https://doi.org/10.1145/509907.510000
Dulek, Y., Grilo, A.B., Jeffery, S., Majenz, C., Schaffner, C.: Secure multi-party quantum computation with a dishonest majority. In: Advances in Cryptology - EUROCRYPT 2020 (2020). https://doi.org/10.1007/978-3-030-45727-3_25
Dupuis, F., Nielsen, J.B., Salvail, L.: Actively secure two-party evaluation of any quantum operation. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 794–811. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_46
Gu, T., Yuan, X., Wu, B.: Efficient measurement schemes for bosonic systems. Quant. Sci. Technol. 8(4), 045008 (2023). https://doi.org/10.1088/2058-9565/ace6cd
Gunn, S., Ju, N., Ma, F., Zhandry, M.: Commitments to quantum states. In: Proceedings of the 55th Annual ACM Symposium on Theory of Computing, pp. 1579–1588 (2023). https://doi.org/10.1145/3564246.3585198
Ishai, Y., Katz, J., Kushilevitz, E., Lindell, Y., Petrank, E.: On achieving the “best of both worlds” in secure multiparty computation. SIAM J. Comput. 40(1), 122–141 (2011). https://doi.org/10.1137/100783224
Ishai, Y., Ostrovsky, R., Zikas, V.: Secure multi-party computation with identifiable abort. In: Garay, J.A., Gennaro, R. (eds.) CRYPTO 2014. LNCS, vol. 8617, pp. 369–386. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44381-1_21
Katz, J.: On achieving the “best of both worlds” in secure multiparty computation. In: Proceedings of the Thirty-ninth Annual ACM Symposium on Theory of Computing, pp. 11–20 (2007). https://doi.org/10.1145/1250790.1250793
Mahadev, U.: Classical verification of quantum computations. In: 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS), pp. 259–267. IEEE (2018). https://doi.org/10.1109/FOCS.2018.00033
Micali, S., Goldreich, O., Wigderson, A.: How to play any mental game. In: Proceedings of the Nineteenth ACM Symposium on Theory of Computing, STOC, pp. 218–229. ACM (1987). https://doi.org/10.1145/28395.28420
Rabin, T., Ben-Or, M.: Verifiable secret sharing and multiparty protocols with honest majority. In: Proceedings of the Twenty-first Annual ACM symposium on Theory of Computing, pp. 73–85 (1989). https://doi.org/10.1145/73007.73014
Van Den Berg, E.: A simple method for sampling random clifford operators. In: 2021 IEEE International Conference on Quantum Computing and Engineering (QCE), pp. 54–59. IEEE (2021). https://doi.org/10.1109/QCE52317.2021.00021
Yao, A.C.C.: How to generate and exchange secrets. In: 27th Annual Symposium on Foundations of Computer Science (sfcs 1986), pp. 162–167 (1986). https://doi.org/10.1109/SFCS.1986.25
Acknowledgement
The authors would like to thank Andrea Coladangelo for useful discussions. This research is supported by NSF CAREER award 2141536, the Air Force Office of Scientific Research under award number FA2386-20-1-4066, and NSTC TACC project under Grant no. NSTC 112-2634-F-001-001-MBK.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 International Association for Cryptologic Research
About this paper
Cite this paper
Chung, KM., Huang, MY., Tang, EC., Zhang, J. (2024). Best-of-Both-Worlds Multiparty Quantum Computation with Publicly Verifiable Identifiable Abort. In: Joye, M., Leander, G. (eds) Advances in Cryptology – EUROCRYPT 2024. EUROCRYPT 2024. Lecture Notes in Computer Science, vol 14656. Springer, Cham. https://doi.org/10.1007/978-3-031-58751-1_5
Download citation
DOI: https://doi.org/10.1007/978-3-031-58751-1_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-58750-4
Online ISBN: 978-3-031-58751-1
eBook Packages: Computer ScienceComputer Science (R0)



 respectively.
respectively. .
. .
. in the computational basis.
in the computational basis. and output the state on the receiving register
and output the state on the receiving register
 .
.

 applies
applies
 to
to
 and outputs
and outputs
 .
. applies
applies  and outputs
and outputs
 .
.


