Abstract
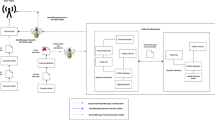
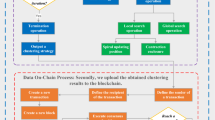
In past years with upgrades in sensor technology, new networking streams and wireless communication with fast networks are applied to the Wireless Sensor Networks (WSN). It raised the region of WSN to a wide reach that led to its massive usage in areas like biotechnology, military applications, IoT, etc. Because of the self-administering nature of sensors in WSN environments, the sensor hubs are also open to compromise. Exactly when a hub is compromised, a few attacks are possible, for instance, spoofing and sinkhole attacks. In this work, the sinkhole attack in WSN is designed and Artificial Bee Colony – Attack Detection (ABC-AD) mechanism for perceiving the sinkhole attack in WSN is proposed. The combination of blockchain and the Artificial Bee Colony is used for evaluating the precedented area of sinkhole attack using the rule-based identical methodology and voting-based methodology. The proposed method shows good resistance and detects sinkholes with a 2% increase in performance when compared with other techniques. The proposed methodology is intuited by the shortfalls of the existing algorithms and the effectiveness of Gestalt consciousness algorithms in the recent era leading to an optimized Artificial Bee Colony exchange security mechanism with blockchain.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Rashid, B., & Rehmani, M. H. (2016). Applications of wireless sensor networks for urban areas: A survey. Journal of Network and Computer Applications, 60, 192–219.
Shafiei, H., Khonsari, A., Derakhshi, H., & Mousavi, P. (2014). Detection and mitigation of sinkhole attacks in wireless sensor networks. Journal of Computer and System Sciences, 80(3), 644–653.
Dallas, D., Leckie, C., & Rao, K. R. (2007). Hop-count monitoring: Detecting sinkhole attacks in wireless sensor networks. In 15th IEEE international conference on Networks, 2007. ICON 2007 (pp. 176–181). IEEE.
Salehi, S. A., Razzaque, M. A., Naraei, P., & Farrokhtala, A. (2013). Detection of sinkhole attack in wireless sensor networks. In 2013 IEEE international conference on Space Science and Communication (IconSpace) (pp. 361–365). IEEE.
Keerthana, G., & Padmavathi, G. (2016). Detecting sinkhole attack in wireless sensor network using enhanced particle swarm optimization technique. International Journal of Security and Its Applications, 10(3), 41–54.
Zhang, F.-J., Zhai, L.-D., Yang, J.-C., & Cui, X. (2014). Sinkhole attack detection based on redundancy mechanism in wireless sensor networks. Procedia Computer Science, 31, 711–720.
Singh, T., & Arora, H. K. (2013). Detection and correction of sinkhole attack with the novel method in WSN using NS2 tool. International Journal of Advanced Computer Science and Applications, 4(2).
Bahekmat, M., Yaghmaee, M. H., Yazdi, A. S. H., & Sadeghi, S. (2012). A novel algorithm for detecting sinkhole attacks in WSNs. International Journal of Computer Theory and Engineering, 4(3), 418.
Ngai, E. C. H., Liu, J., & Lyu, M. R. (2007). An efficient intruder detection algorithm against sinkhole attacks in wireless sensor networks. Elsevier Computer Communications, 30, 2353–2364.
Xie, M., Han, S., Tian, B., & Parvin, S. (2011). Anomaly detection in wireless sensor networks: A survey. Journal of Network and Computer Applications, 34(4), 1302–1325.
Wazid, M., Das, A. K., Kumari, S., & Khan, M. K. (2016). Design of sinkhole node detection mechanism for hierarchical wireless sensor networks. Security and Communication Networks, 9(17), 4596–4614.
Soni, V., Modi, P., & Chaudhri, V. (2013). Detecting sinkhole attack in a wireless sensor network. International Journal of Application or Innovation in Engineering & Management, 2(2), 29–32.
Sharmila, S., & Umamaheswari, G. (2011). Detection of sinkhole attack in wireless sensor networks using message digest algorithms. In 2011 International conference on Process Automation, Control and Computing (PACC) (pp. 1–6). IEEE.
Jahandoust, G., & Ghassemi, F. (2017). An adaptive sinkhole aware algorithm in wireless sensor networks. Ad Hoc Networks. https://doi.org/10.1016/j.adhoc.2017.01.002
Guo, Q., Li, X., Xu, G., & Feng, Z. (2016). MP-MID: Multi-Protocol Oriented Middleware-level intrusion detection method for wireless sensor networks. Future Generation Computer Systems. https://doi.org/10.1016/j.future.2016.06.010
Xie, J., Yang, T., Yang, F., Pan, L., Xu, J., & Yao, H. (2018). Intrusion detection system for hybrid dos attacks using energy Trust in wireless sensor networks. Procedia Computer Science, 131, 1188–1195.
Borkara, G. M., Patil, L. H., Dalgadec, D., & Hutke, A. (2019). A novel clustering approach and adaptive SVM classifier for intrusion detection in WSN: A data mining concept. Sustainable Computing: Informatics and Systems, 23, 120–135.
Hajiheidari, S., Wakil, K., Badri, M., & Navimipour, N. J. (2019). Intrusion detection systems in the Internet of Things: A comprehensive investigation. Computer Networks, 160, 165–191.
Pundir, S., Wazid, M., Singh, D. P., Das, A. K., Rodrigues, J. J. P. C., & Park, Y. (2020). Designing efficient sinkhole attack detection mechanism in edge-based IoT deployment. Sensors, 20, 1300. https://doi.org/10.3390/s20051300
Sejaphala, L. C., & Velempini, M. The design of a defense mechanism to mitigate sinkhole attack in software-defined wireless sensor cognitive radio networks. Wireless Personal Communications, 113, 977–993. https://doi.org/10.1007/s11277-020-07263-9
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Cite this chapter
Gaya, D., Parthiban, L., Nithiyanandam, N. (2024). Blockchain-Based Sinkhole Attack Detection in Wireless Sensor Network. In: Goundar, S., Anandan, R. (eds) Integrating Blockchain and Artificial Intelligence for Industry 4.0 Innovations. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-031-35751-0_19
Download citation
DOI: https://doi.org/10.1007/978-3-031-35751-0_19
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-35750-3
Online ISBN: 978-3-031-35751-0
eBook Packages: EngineeringEngineering (R0)