Abstract
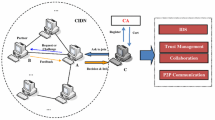
With cyber attacks becoming more complex and advanced, a separate intrusion detection system (IDS) is believed to be insufficient for protecting the whole computer networks. Thus, collaborative intrusion detection networks (CIDNs) are proposed aiming to improve the detection performance by allowing various nodes to share required information or messages with other nodes. To defeat insider threats during the sharing process (e.g., malicious information), trust management is a necessary security mechanism for CIDNs, where challenge-based CIDNs are a typical example that sends a special kind of message, called challenge, to evaluate the reputation of a node. The previous work has proven that challenge-based CIDNs can defeat most common insider threats, but it may still suffer from some advanced insider threats, e.g., passive message fingerprint attack (PMFA). In this work, we develop EnergyCIDN, an enhanced challenge-based CIDN by adopting an energy-aware trust management model against advanced insider attacks. In the evaluation, we study the performance of EnergyCIDN under both simulated and practical Internet of Things (IoT) environments. The results demonstrate that EnergyCIDN can perform better than many similar schemes in identifying advanced malicious nodes.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others


Notes
- 1.
It is also known as distributed intrusion detection system (DIDS) or collaborative intrusion detection system (CIDS).
- 2.
Marginal distribution of a subset of random variables is the probability distribution of the variables contained in the subset.
References
IoT Trends To Drive Innovation For Business In 2022 - MobiDev. https://mobidev.biz/blog/iot-technology-trends. Accessed 1 June 2022
Report: More than 1B IoT attacks in 2021. https://venturebeat.com/2022/04/25/report-more-than-1b-iot-attacks-in-2021/. Accessed 1 June 2022
IoT Security Global Market Report 2022. https://www.globenewswire.com/news-release/2022/03/22/2407932/0/en/IoT-Security-Global-Market-Report-2022.html. Accessed 3 May 2022
Ma, Z., Liu, L., Meng, W.: Towards multiple-mix-attack detection via consensus-based trust management in iot networks. Comput. Secur. 96, 101898 (2020)
Paniagua, C., Delsing, J.: Industrial frameworks for internet of things: a survey. IEEE Syst. J. 15(1), 1149–1159 (2021)
Cao, S., Dang, S., Zhang, Y., Wang, W., Cheng, N.: A blockchain-based access control and intrusion detection framework for satellite communication systems. Comput. Commun. 172, 216–225 (2021)
Chiu, W.Y., Meng, W.: BlockFW - towards blockchain-based rule-sharing firewall. In: Proceedings of the 16th International Conference on Emerging Security Information, Systems and Technologies (SECURWARE), IARIA 2022 (2022)
Duma, C., Karresand, M., Shahmehri, N., Caronni, G.: A trust-aware, P2P-based overlay for intrusion detection. In: DEXA Workshop, pp. 692–697 (2006)
Fadlullah, Z.M., Taleb, T., Vasilakos, A.V., Guizani, M., Kato, N.: DTRAB: combating against attacks on encrypted protocols through traffic-feature analysis. IEEE/ACM Trans. Network. 18(4), 1234–1247 (2010)
Friedberg, I., Skopik, F., Settanni, G., Fiedler, R.: Combating advanced persistent threats: from network event correlation to incident detection. Comput. Secur. 48, 35–47 (2015)
Fung, C.J., Baysal, O., Zhang, J., Aib, I., Boutaba, R.: Trust management for host-based collaborative intrusion detection. In: De Turck, F., Kellerer, W., Kormentzas, G. (eds.) DSOM 2008. LNCS, vol. 5273, pp. 109–122. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-87353-2_9
Fung, C.J.; Zhu, Q., Boutaba, R., Basar, T.: Bayesian decision aggregation in collaborative intrusion detection networks. In: NOMS, pp. 349–356 (2010)
Golomb, T., Mirsky, Y., Elovici, Y.: CIoTA: collaborative IoT anomaly detection via blockchain. In: Proceedings of Workshop on Decentralized IoT Security and Standards (DISS), pp. 1–6 (2018)
Khan, A.A., Khan, M.M., Khan, K.M., Arshad, J., Ahmad, F.: A blockchain-based decentralized machine learning framework for collaborative intrusion detection within UAVs. Comput. Netw. 196, 108217 (2021)
Han, Y., Hu, H., Guo, Y.: Energy-aware and trust-based secure routing protocol for wireless sensor networks using adaptive genetic algorithm. IEEE Access 10, 11538–11550 (2022)
Hu, B., Zhou, C., Tian, Y.C., Qin, Y., Junping, X.: A collaborative intrusion detection approach using blockchain for multimicrogrid systems. IEEE Trans. Syst. Man Cybern. Syst. 49(8), 1720–1730 (2019)
Li, Z., Chen, Y., Beach, A.: Towards scalable and robust distributed intrusion alert fusion with good load balancing. In: Proceedings of the 2006 SIGCOMM Workshop on Large-Scale Attack Defense (LSAD), pp. 115–122 (2006)
Li, W., Meng, Y., Kwok, L.-F.: Enhancing trust evaluation using intrusion sensitivity in collaborative intrusion detection networks: feasibility and challenges. In: Proceedings of the 9th International Conference on Computational Intelligence and Security (CIS), pp. 518–522. IEEE (2013)
Li, W., Meng, W., Kwok, L.-F.: Design of intrusion sensitivity-based trust management model for collaborative intrusion detection networks. In: Zhou, J., Gal-Oz, N., Zhang, J., Gudes, E. (eds.) IFIPTM 2014. IAICT, vol. 430, pp. 61–76. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-43813-8_5
Li. W., Meng, W.: Enhancing collaborative intrusion detection networks using intrusion sensitivity in detecting pollution attacks. Inf. Comput. Secur. 24(3), 265–276 (2016). Emerald
Li, W., Meng, W., Kwok, L.F., Ip, H.H.S.: PMFA: toward passive message fingerprint attacks on challenge-based collaborative intrusion detection networks. In: Proceedings of the 10th International Conference on Network and System Security (NSS 2016), pp. 433–449 (2016)
Li, W., Meng, W., Kwok, L.F.: SOOA: exploring special on-off attacks on challenge-based collaborative intrusion detection networks. In: Proceedings of GPC, pp. 402–415 (2017)
Li, W., Meng, W., Kwok, L.-F.: Investigating the influence of special on-off attacks on challenge-based collaborative intrusion detection networks. Future Internet 10(1), 1–16 (2018)
Li, W., Tug, S., Meng, W., Wang, Y.: Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener. Comput. Syst. (in Press). Elsevier
Li, W., Kwok, L.-F.: Challenge-based collaborative intrusion detection networks under passive message fingerprint attack: a further analysis. J. Inf. Secur. Appl. 47, 1–7 (2019)
Li, W., Wang, Y., Li, J., Au, M.H.: Toward a blockchain-based framework for challenge-based collaborative intrusion detection. Int. J. Inf. Secur. 20(2), 127–139 (2021)
Li, W., Wang, Y., Li, J.: Enhancing blockchain-based filtration mechanism via IPFS for collaborative intrusion detection in IoT networks. J. Syst. Archit. 127, 102510 (2022)
Li, W., Meng, W., Kwok, L.-F.: Surveying trust-based collaborative intrusion detection: state-of-the-art, challenges and future directions. IEEE Commun. Surv. Tutor. 24(1), 280–305 (2022)
Li, W., Meng, W.: BCTrustFrame: enhancing trust management via blockchain and IPFS in 6G era. IEEE Netw. 36(4), 120–125 (2022)
Meng, Y., Kwok, L.F., Li, W.: Towards designing packet filter with a trust-based approach using Bayesian inference in network intrusion detection. In: Proceedings of the 8th International Conference on Security and Privacy in Communication Networks (SECURECOMM), pp. 203–221 (2012)
Meng, Y., Kwok, L.F.: Enhancing false alarm reduction using voted ensemble selection in intrusion detection. Int. J. Comput. Intell. Syst. 6(4), 626–638 (2013). Taylor & Francis
Meng, Y., Li, W., Kwok, L.F.: Towards adaptive character frequency-based exclusive signature matching scheme and its applications in distributed intrusion detection. Comput. Netw. 57(17), 3630–3640 (2013). Elsevier
Meng, W., Li, W., Kwok, L.-F.: An evaluation of single character frequency-based exclusive signature matching in distinct IDS environments. In: Proceedings of the 17th International Conference on Information Security (ISC), pp. 465–476 (2014)
Meng, W., Li, W., Kwok, L.-F.: EFM: enhancing the performance of signature-based network intrusion detection systems using enhanced filter mechanism. Comput. Secur. 43, 189–204 (2014). Elsevier
Meng, W., Li, W., Kwok, L.-F.: Design of intelligent KNN-based alarm filter using knowledge-based alert verification in intrusion detection. Secur. Commun. Netw. 8(18), 3883–3895 (2015). Wiley
Meng, W., Luo, X., Li, W., Li, Y.: Design and evaluation of advanced collusion attacks on collaborative intrusion detection networks in practice. In: Proceedings of the 15th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2016), pp. 1061–1068 (2016)
Meng, W., Li, W., Xiang, Y., Choo, K.K.R.: A Bayesian inference-based detection mechanism to defend medical smartphone networks against insider attacks. J. Netw. Comput. Appl. 78, 162–169 (2017). Elsevier
Meng, W., Li, W., Kwok, L.-F.: Towards effective trust-based packet filtering in collaborative network environments. IEEE Trans. Netw. Serv. Manag. 14(1), 233–245 (2017)
Meng, W., Tischhauser, E.W., Wang, Q., Wang, Y., Han, J.: When intrusion detection meets blockchain technology: a review. IEEE Access 6(1), 10179–10188 (2018)
Meng, W., Li, W., Jiang, L., Choo, K.K.R., Su, C.: Practical Bayesian poisoning attacks on challenge-based collaborative intrusion detection networks. In: Proceedings of the ESORICS, pp. 493–511 (2019)
Meng, W., Li, W., Yang, L.T., Li, P.: Enhancing challenge-based collaborative intrusion detection networks against insider attacks using blockchain. Int. J. Inf. Secur. 19(3), 279–290 (2020)
Papadopoulos, C., Lindell, R., Mehringer, J., Hussain, A., Govindan, R.: COSSACK: coordinated suppression of simultaneous attacks. In: Proceedings of the 2003 DARPA Information Survivability Conference and Exposition (DISCEX), pp. 94–96 (2003)
Porras, P.A., Neumann, P.G.: Emerald: event monitoring enabling responses to anomalous live disturbances. In: Proceedings of the 20th National Information Systems Security Conference, pp. 353–365 (1997)
Scarfone, K., Mell, P.: Guide to Intrusion Detection and Prevention Systems (IDPS). NIST Special Publication 800-94 (2007)
Snapp, S.R., et al.: DIDS (distributed intrusion detection system) - motivation, architecture, and an early prototype. In: Proceedings of the 14th National Computer Security Conference, pp. 167–176 (1991)
Shi, Q., Qin, L., Ding, Y., Xie, B., Zheng, J., Song, L.: Information-aware secure routing in wireless sensor networks. Sensors 20(1), Article 165 (2020)
Snort: An an open source network intrusion prevention and detection system (IDS/IPS). http://www.snort.org/
Steichen, M., Hommes, S., State, R.: ChainGuard - a firewall for blockchain applications using SDN with OpenFlow. In: Proceedings of International Conference on Principles, Systems and Applications of IP Telecommunications (IPTComm), pp. 1–8 (2017)
Tug, S., Meng, W., Wang, Y.: CBSigIDS: towards collaborative blockchained signature-based intrusion detection. In: Proceedings of The 1st IEEE International Conference on Blockchain (Blockchain) (2018)
Tuan, T.A.: A game-theoretic analysis of trust management in P2P systems. In: Proceedings of ICCE, pp. 130–134 (2006)
Vasilomanolakis, E., Karuppayah, S., Muhlhauser, M., Fischer, M.: Taxonomy and Survey of Collaborative Intrusion Detection. ACM Computing Surveys 47(4), pp. 55:1–55:33 (2015)
Wang, Y., Meng, W., Li, W., Liu, Z., Liu, Y., Xue, H.: Adaptive machine learning-based alarm reduction via edge computing for distributed intrusion detection systems. Concurr. Comput. Pract. Exp. (2019). Wiley
Wu, Y.-S., Foo, B., Mei, Y., Bagchi, S.: Collaborative intrusion detection system (CIDS): a framework for accurate and efficient IDS. In: Proceedings of the 2003 Annual Computer Security Applications Conference (ACSAC), pp. 234–244 (2003)
Yenugunti, C., Yau, S.S.: A blockchain approach to identifying compromised nodes in collaborative intrusion detection systems. In: Proceedings of DASC/PiCom/CBDCom/CyberSciTech, pp. 87–93 (2020)
Yegneswaran, V., Barford, P., Jha, S.: Global intrusion detection in the DOMINO overlay system. In: Proceedings of the 2004 Network and Distributed System Security Symposium (NDSS), pp. 1–17 (2004)
Acknowledgments
This work was partially supported by the start-up fund in the Department of Electronic and Information Engineering, The Hong Kong Polytechnic University.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 Springer Nature Switzerland AG
About this paper
Cite this paper
Li, W., Rosenberg, P., Glisby, M., Han, M. (2023). EnergyCIDN: Enhanced Energy-Aware Challenge-Based Collaborative Intrusion Detection in Internet of Things. In: Meng, W., Lu, R., Min, G., Vaidya, J. (eds) Algorithms and Architectures for Parallel Processing. ICA3PP 2022. Lecture Notes in Computer Science, vol 13777. Springer, Cham. https://doi.org/10.1007/978-3-031-22677-9_16
Download citation
DOI: https://doi.org/10.1007/978-3-031-22677-9_16
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-22676-2
Online ISBN: 978-3-031-22677-9
eBook Packages: Computer ScienceComputer Science (R0)