Abstract
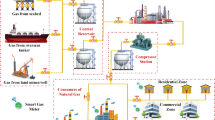
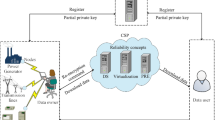
The smart gas grid (SGG) implies to enhance current gas distribution grids by establishing continuous on-request and bidirectional data interchange between metering devices, gas flow instrument’s, utilities, and end clients. SGG integrates IoT in gas distribution system and improves the management in hazard minimization for gas infrastructure. As a result, the security and privacy of this type of vital infrastructure are frequently overlooked during the design process. Cloud reserves are frequently researched to store data from smart meters. Regardless of SGG’s exemplary service, this raises concerns about the unpredictable and long-term connections between cloud data hubs and smart meters. To address this issue, the integration of fog computing with SGG emerges as a promising solution. This chapter proposed a hyperelliptic curve (HYEC)-based proxy signcryption scheme based on identities of data owners and data users in fog computing environment (IBPSC-SGG-FCE). The use of fog computing layer provides excellent response times, reliability, and enhanced privacy. HYEC enhances network computation efficiency. Formal security analysis is used to assess the toughness of security measures. Under OFMC and CL-Atse backend, the simulation study using Automated Validation of Internet Security-sensitive Protocols and Applications (AVISPA) tool shows that the proposed scheme is safe. The computation and communication costs of the proposed scheme have also been compared to those of the relevant existing schemes in the performance analysis. The security and performance evaluations show that the proposed scheme is superior.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
M. Sheha, K. Mohammadi, K. Powell, Techno-economic analysis of the impact of dynamic electricity prices on solar penetration in a smart grid environment with distributed energy storage. Appl. Energy 282, 116168 (2021)
O.M. Butt, M. Zulqarnain, T.M. Butt, Recent advancement in smart grid technology: future prospects in the electrical power network. Ain Shams Eng. J. 12(1), 687–695 (2021)
A. Panayiotou, N.P. Stavrou, E. Stergiou, Applying the industry 4.0 in a smart gas grid: the Greek Gas Distribution Network case, in 2021 International Symposium on Electrical, Electronics and Information Engineering, (2021), pp. 180–184
A.R. Al-Ali, T. Landolsi, M.H. Hassan, M. Ezzeddine, M. Abdelsalam, M. Baseet, An IoT-based smart utility meter, in 2018 2nd International Conference on Smart Grid and Smart Cities (ICSGSC), (IEEE, 2018), pp. 80–83
H. Lund, Renewable heating strategies and their consequences for storage and grid infrastructures comparing a smart grid to a smart energy systems approach. Energy 151, 94–102 (2018)
F. Dababneh, L. Li, Integrated electricity and natural gas demand response for manufacturers in the smart grid. IEEE Trans. Smart Grid 10(4), 4164–4174 (2018)
Kamrani, F., Fattaheian-Dehkordi, Sajjad; Gholami, Mohammad; Abbaspour, Ali; Fotuhi-Firuzabad, Mahmud; Lehtonen, Matti 2021. A Two-Stage Flexibility-Oriented Stochastic Energy Management Strategy for Multi-Microgrids Considering Interaction With Gas Grid
S. Colombo, Y. Lim, F. Casalegno, Deep vision shield: assessing the use of hmd and wearable sensors in a smart safety device, in Proceedings of the 12th ACM International Conference on PErvasive Technologies Related to Assistive Environments, (2019), pp. 402–410
A. Elmrini, A.G. Amrani, Wireless sensors network for traffic surveillance and management in smart cities, in 2018 IEEE 5th International Congress on Information Science and Technology (CiSt), (IEEE, 2018), pp. 562–566
S. Surnov, I. Bychkovskiy, G. Surnov, S. Krasnov, Smart Monitoring: remote-monitoring technology of power, gas, and water consumption in Smart Cities. arXiv preprint arXiv:1910.08759 (2019)
J. Qiu, J. Zhao, H. Yang, D. Wang, Z.Y. Dong, Planning of solar photovoltaics, battery energy storage system and gas micro turbine for coupled micro energy grids. Appl. Energy 219, 361–369 (2018)
E.A.M. Ceseña, P. Mancarella, Energy systems integration in smart districts: robust optimisation of multi-energy flows in integrated electricity, heat and gas networks. IEEE Trans. Smart Grid 10(1), 1122–1131 (2018)
J. Savickis, L. Zemite, I. Bode, L. Jansons, Natural gas metering and its accuracy in the smart gas supply systems. Latv. J. Phys. Tech. Sci. 57(5), 39–50 (2020)
X. Li, K. Chen, Identity based proxy-signcryption scheme from pairings, in IEEE International Conference on Services Computing, 2004 (SCC 2004). Proceedings, vol. 2004, (IEEE, 2004), pp. 494–497
Q. Wang, Z. Cao, Efficient ID-based proxy signature and proxy signcryption form bilinear pairings, in International Conference on Computational and Information Science, (Springer, Berlin/Heidelberg, 2005), pp. 167–172
M. Wang, H. Li, Z. Liu, Efficient identity based proxy-signcryption schemes with forward security and public verifiability, in International Conference on Networking and Mobile Computing, (Springer, Berlin/Heidelberg, 2005), pp. 982–991
H.M. Elkamchouchi, Y. Abouelseoud, A new proxy identity-based signcryption scheme for partial delegation of signing rights. IACR Cryptol. ePrint Arch. 2008, 41 (2008)
X.X. Tian, J.P. Xu, H.J. Li, Y. Peng, A.Q. Zhang, Secure ID-based proxy signcryption scheme with designated proxy signcrypter, in 2009 International Conference on Multimedia Information Networking and Security, vol. 1, (IEEE, 2009), pp. 351–355
C.C. Tsai, K.C. Liao, T.H. Chen, W.B. Lee, Security enhancement of a novel proxy key generation protocol, in 31st Annual International Computer Software and Applications Conference (COMPSAC 2007), vol. 2, (IEEE, 2007), pp. 681–688
G. Swapna, P.V.S.S.N. Gopal, T. Gowri, P.V. Reddy, An efficient ID-based proxy signcryption scheme. Int. J. Inf. Netw. Secur. 1(3), 200 (2012)
H.M. Elkamchouchi, Y. Abouelseoud, E.F.A. Elkhair, K. Elsheikh, An efficient ID-based proxy signcryption scheme without bilinear pairings. Int. J. Comput. Appl. 975, 8887 (2013)
N.W. Lo, J.L. Tsai, A provably secure proxy signcryption scheme using bilinear pairings. J. Appl. Math., 2014 (2014)
H.Y. Lin, T.S. Wu, S.K. Huang, Y.S. Yeh, Efficient proxy signcryption scheme with provable CCA and CMA security. Comput. Math. Appl. 60(7), 1850–1858 (2010)
C. Zhou, Y. Zhang, L. Wang, A provable secure identity-based generalized proxy signcryption scheme. Int. J. Netw. Secur. 20(6), 1183–1193 (2018)
H. Yu, Z. Wang, J. Li, X. Gao, Identity-based proxy signcryption protocol with universal composability. Secur. Commun. Netw. 2018 (2018)
N.W. Hundera, Q. Mei, H. Xiong, D.M. Geressu, A secure and efficient identity-based proxy signcryption in cloud data sharing. KSII Trans. Internet Inf. Syst. (TIIS) 14(1), 455–472 (2020)
H. Guo, L. Deng, An identity based proxy signcryption scheme without pairings. Int. J. Netw. Secur. 22(4), 561–568 (2020)
P.R. Yogesh, Formal verification of secure evidence collection protocol using BAN logic and AVISPA. Proc. Comput. Sci. 167, 1334–1344 (2020)
P.R. Yogesh, Backtracking tool root-tracker to identify true source of cyber crime. Proc. Comput. Sci. 171, 1120–1128 (2020)
R.Y. Patil, S.R. Devane, Network forensic investigation protocol to identify true origin of cyber crime. J. King Saud Univ. Comput. Inf. Sci. (2019)
C. Zhou, Z. Zhao, W. Zhou, Y. Mei, Certificateless key-insulated generalized signcryption scheme without bilinear pairings. Secur. Commun. Netw. 2017 (2017)
Y. Ming, Y. Wang, Proxy signcryption scheme in the standard model. Secur. Commun. Netw. 8(8), 1431–1446 (2015)
H. Yu, Z. Wang, Construction of certificateless proxy signcryption scheme from CMGs. IEEE Access 7, 141910–141919 (2019)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Cite this chapter
Patil, R., Patil, Y.H., Bannore, A., Karati, A., Kachhoriya, R., Ranjanikar, M. (2023). A Provably Secure Data Sharing Scheme for Smart Gas Grid in Fog Computing Environment. In: Daimi, K., Alsadoon, A., Peoples, C., El Madhoun, N. (eds) Emerging Trends in Cybersecurity Applications. Springer, Cham. https://doi.org/10.1007/978-3-031-09640-2_13
Download citation
DOI: https://doi.org/10.1007/978-3-031-09640-2_13
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-09639-6
Online ISBN: 978-3-031-09640-2
eBook Packages: Computer ScienceComputer Science (R0)