Abstract
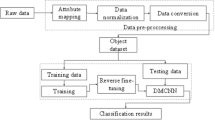
In this paper we propose an intrusions detection technique using Deep Learning approach that can classify different types of attacks based on user behavior and not on attacks signatures. The Deep Learning approach used is Supervised Learning model called Convolutional Neural Networks (CNN) coupled with Tree Structure whose set is named Tree-CNN. This structure allows for incremental learning. This makes the model capable of learning how to detect and classify new types of attacks as new data arrives. The model was implemented with TensorFlow and trained with the CSE-CIC-IDS2018 dataset. We evaluated the performance of our proposed model and we made comparisons with other approaches considered in related works. The experimental results show that the model can detect and classify intrusions with a score of 99.94% for the detection and 97.54% for the classification.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Shenfield, A., Day, D., Ayesh, A.: Intelligent intrusion detection systems using artificial neural networks. ICT Express 4(2), 95–99 (2018). SI on Artificial Intelligence and Machine Learning
Chockwanich, N., Visoottiviseth, V.: Intrusion detection by deep learning with TensorFlow. In: 2019 21st International Conference on Advanced Communication Technology (ICACT), pp. 654–659 (2019)
Mohammadpour, C.S.L.L., Ling, T.C., Chong, C.Y.: A convolutional neural network for network intrusion detection system. In: Asia-Pacific Advanced Network (APAN) (2018)
Lin, P., Ye, K., Xu, C.-Z.: Dynamic network anomaly detection system by using deep learning techniques. In: Da Silva, D., Wang, Q., Zhang, L.-J. (eds.) CLOUD 2019. LNCS, vol. 11513, pp. 161–176. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-23502-4_12
Kanimozhi, V., Prem Jacob, T.: Calibration of various optimized machine learning classifiers in network intrusion detection system on the realistic cyber dataset CSE-CIC-IDS 2018 using cloud computing. Int. J. Eng. Appl. Sci. Technol. 4, 2455–2143 (2019)
Kanimozhi, V., Jacob, T.P.: Artificial intelligence based network intrusion detection with hyper-parameter optimization tuning on the realistic cyber dataset CSE-CIC-IDS 2018 using cloud computing. In: 2019 International Conference on Communication and Signal Processing (ICCSP), pp. 0033–0036 (2019)
Giraud-Carrier, C.: A note on the utility of incremental learning. AI Commun. 13(4), 215–223 (2000)
Ring, M.B.: Child: a first step towards continual learning. In: Thrun, S., Pratt, L. (eds.) Learning to Learn, pp. 261–292. Springer, Boston (1998). https://doi.org/10.1007/978-1-4615-5529-2_11
Polikar, R., Upda, L., Upda, S.S., Honavar, V.: Learn++: an incremental learning algorithm for supervised neural networks. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 31(4), 497–508 (2001)
Shin, H., Lee, J.K., Kim, J., Kim, J.: Continual learning with deep generative replay. In: Advances in Neural Information Processing Systems, pp. 2990–2999 (2017)
Zenke, F., Poole, B., Ganguli, S.: Continual learning through synaptic intelligence. Proc. Mach. Learn. Res. 70, 3987 (2017)
XIao, T., Zhang, J., Yang, K., et al.: Error-driven incremental learning in deep convolutional neural network for large-scale image classification. In: Proceedings of the 22nd ACM International Conference on Multimedia, pp. 177–186 (2014)
Goodfellow, I.J., Mirza, M., Xiao, D., et al.: An empirical investigation of catastrophic forgetting in gradient-based neural networks. arXiv preprint arXiv:1312.6211 (2013)
Roy, D., Panda, P., Roy, K.: Tree-CNN: a hierarchical deep convolutional neural network for incremental learning. Neural Netw. 121, 148–160 (2020)
Chawla, N.V., Bowyer, K.W., Hall, L.O., Kegelmeyer, W.P.: Smote: synthetic minority over-sampling technique. J. Artif. Intell. Res. 16, 321–357 (2002)
Le, T., Kim, J., Kim, H.: An effective intrusion detection classifier using long short-term memory with gradient descent optimization. In: 2017 International Conference on Platform Technology and Service (PlatCon), pp. 1–6 (2017)
Zeng, Y., Gu, H., Wei, W., Guo, Y.: Deep-full-range: a deep learning based network encrypted traffic classification and intrusion detection framework. IEEE Access 7, 45182–45190 (2019)
Javaid, A., Niyaz, Q., Sun, W., Alam, M.: A deep learning approach for network intrusion detection system. In: Proceedings of the 9th EAI International Conference on Bio-inspired Information and Communications Technologies (Formerly BIONETICS), pp. 21–26 (2016)
Potluri, S., Ahmed, S., Diedrich, C.: Convolutional neural networks for multi-class intrusion detection system. In: Groza, A., Prasath, R. (eds.) MIKE 2018. LNCS (LNAI), vol. 11308, pp. 225–238. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-05918-7_20
Ding, Y., Zhai, Y.: Intrusion detection system for NSL-KDD dataset using convolutional neural networks. In: Proceedings of the 2018 2nd International Conference on Computer Science and Artificial Intelligence, pp. 81–85 (2018)
Potluri, S., Henry, N.F., Diedrich, C.: Evaluation of hybrid deep learning techniques for ensuring security in networked control systems. In: 2017 22nd IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), pp. 1–8 (2017)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 ICST Institute for Computer Sciences, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Sawadogo, L.M., Bassolé, D., Koala, G., Sié, O. (2021). Intrusions Detection and Classification Using Deep Learning Approach. In: Faye, Y., Gueye, A., Gueye, B., Diongue, D., Nguer, E.H.M., Ba, M. (eds) Research in Computer Science and Its Applications. CNRIA 2021. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 400. Springer, Cham. https://doi.org/10.1007/978-3-030-90556-9_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-90556-9_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-90555-2
Online ISBN: 978-3-030-90556-9
eBook Packages: Computer ScienceComputer Science (R0)