Abstract
Multi-signatures enable a group of signers to produce a joint signature on a joint message. Recently, Drijvers et al. (S&P’19) showed that all thus far proposed two-round multi-signature schemes in the pure DL setting (without pairings) are insecure under concurrent signing sessions. While Drijvers et al. proposed a secure two-round scheme, this efficiency in terms of rounds comes with the price of having signatures that are more than twice as large as Schnorr signatures, which are becoming popular in cryptographic systems due to their practicality (e.g., they will likely be adopted in Bitcoin). If one needs a multi-signature scheme that can be used as a drop-in replacement for Schnorr signatures, then one is forced to resort either to a three-round scheme or to sequential signing sessions, both of which are undesirable options in practice.
In this work, we propose \(\mathsf {MuSig2} \), a simple and highly practical two-round multi-signature scheme. This is the first scheme that simultaneously i) is secure under concurrent signing sessions, ii) supports key aggregation, iii) outputs ordinary Schnorr signatures, iv) needs only two communication rounds, and v) has similar signer complexity as ordinary Schnorr signatures. Furthermore, it is the first multi-signature scheme in the pure DL setting that supports preprocessing of all but one rounds, effectively enabling a non-interactive signing process without forgoing security under concurrent sessions. We prove the security of \(\mathsf {MuSig2} \) in the random oracle model, and the security of a more efficient variant in the combination of the random oracle and the algebraic group model. Both our proofs rely on a weaker variant of the OMDL assumption.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
Since we do not impose any constraint on the key setup, the adversary can choose corrupted public keys arbitrarily and duplicate public keys can appear in L.
- 2.
- 3.
We refer the interested reader to the full version [27] for a high-level explanation of why the meta-reduction cannot be adapted to work with our scheme.
- 4.
Observe that \(\mathsf {InsecureMuSig} \) is identical to an imaginary \(\mathsf {MuSig2} \) with a just a single nonce, i.e., \(\nu = 1\).
- 5.
- 6.
- 7.
In fact, it is easy to see that the adversary can only guess the value of the aggregate public key \(\widetilde{X}\) corresponding to L at random before making the relevant queries \(\mathsf {H}_{\mathrm {agg}}(L,X_i)\) for \(X_i\in L\), so that the query \(\mathsf {H}_{\mathrm {sig}}(\widetilde{X},R,m)\) can only come after the relevant queries \(\mathsf {H}_{\mathrm {agg}}(L,X_i)\) except with negligible probability.
- 8.
This computation can be saved by caching the result when handling the internal \(\mathsf {H}_{\mathrm {non}}\) query.
- 9.
Theorem 1 states the security of \(\mathsf {MuSig2} \) only for \(\nu =4\), because there is no reason to use more than four nonces in practice. The proof works for any \(\nu \ge 4\).
- 10.
For example, the adversary may have replied with different L, m or R values in different executions, or algorithm
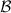 may have received different “\(h_{\mathrm {non}}\)” values.
may have received different “\(h_{\mathrm {non}}\)” values. - 11.
For example, all four executions (as visualized in Fig. 4) are in the same component if the corresponding \(T_{\mathrm {non}}\) value was set before the \(\mathsf {H}_{\mathrm {agg}}\) fork point, and two executions in the same branch of the \(\mathsf {H}_{\mathrm {agg}}\) fork are in the same component if the \(T_{\mathrm {non}}\) value was set before the \(\mathsf {H}_{\mathrm {sig}}\) fork point.
References
Alper, H.K., Burdges, J.: Two-round trip schnorr multi-signatures via delinearized witnesses. In: CRYPTO 2021, 2021. https://eprint.iacr.org/2020/1245
Bagherzandi, A., Cheon, J.H., Jarecki, S.: Multisignatures secure under the discrete logarithm assumption and a generalized forking lemma. In: Ning, P., Syverson, P.F., Jha, S. (eds.) ACM CCS 2008, pp. 449–458. ACM Press, October 2008. https://doi.org/10.1145/1455770.1455827
Bellare, M., Namprempre, C., Pointcheval, D., Semanko, M.: The one-more-RSA-inversion problems and the security of Chaum’s blind signature scheme. J. Cryptol. 16(3), 185–215 (2003). https://doi.org/10.1007/s00145-002-0120-1
Bellare, M., Neven, G.: Multi-signatures in the plain public-key model and a general forking lemma. In: Juels, A., Wright, R.N., De Capitani di Vimercati, S. (eds.) ACM CCS 2006, pp. 390–399. ACM Press, October/November 2006. https://doi.org/10.1145/1180405.1180453
Bellare, M., Palacio, A.: GQ and schnorr identification schemes: proofs of security against impersonation under active and concurrent attacks. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 162–177. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_11
Bellare, M., Shoup, S.: Two-tier signatures, strongly unforgeable signatures, and Fiat-Shamir without Random Oracles. In: Okamoto, T., Wang, X. (eds.) PKC 2007. LNCS, vol. 4450, pp. 201–216. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-71677-8_14
Benhamouda, F., Lepoint, T., Loss, J., Orrù, M., Raykova, M.: On the (in)security of ROS. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12696, pp. 33–53. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-77870-5_2
Boldyreva, A.: Threshold signatures, multisignatures and blind signatures based on the gap-Diffie-Hellman-group signature scheme. In: Desmedt, Y.G. (ed.) PKC 2003. LNCS, vol. 2567, pp. 31–46. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-36288-6_3
Boneh, D., Drijvers, M., Neven, G.: Compact multi-signatures for smaller blockchains. In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018. LNCS, vol. 11273, pp. 435–464. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03329-3_15
Chaum, D., Pedersen, T.P.: Wallet databases with observers. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 89–105. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_7
Drijvers, M., et al.: On the security of two-round multi-signatures. In: 2019 IEEE Symposium on Security and Privacy, pp. 1084–1101. IEEE Computer Society Press, May 2019. https://doi.org/10.1109/SP.2019.00050
Fuchsbauer, G., Kiltz, E., Loss, J.: The algebraic group model and its applications. In: Shacham, H., Boldyreva, A. (eds.) CRYPTO 2018. LNCS, vol. 10992, pp. 33–62. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-96881-0_2
Fuchsbauer, G., Plouviez, A., Seurin, Y.: Blind schnorr signatures and signed ElGamal encryption in the algebraic group model. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020. LNCS, vol. 12106, pp. 63–95. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45724-2_3
Gentry, C., Wichs, D.: Separating succinct non-interactive arguments from all falsifiable assumptions. In: Fortnow, L., Vadhan, S.P. (eds.) 43rd ACM STOC, pp. 99–108. ACM Press, June 2011. https://doi.org/10.1145/1993636.1993651
Goldwasser, S., Kalai, Y.T.: Cryptographic assumptions: A position paper. Cryptology ePrint Archive, Report 2015/907 (2015). https://eprint.iacr.org/2015/907
Horster, P., Michels, M., Petersen, H.: Meta-multisignature schemes based on the discrete logarithm problem. In: IFIP/Sec ’95, IFIP Advances in Information and Communication Technology, pp. 128–142. Springer (1995)
Itakura, K., Nakamura, K.: A public-key cryptosystem suitable for digital multisignatures. NEC Res. Dev. 71, 1–8 (1983)
Komlo, C., Goldberg, I.: FROST: flexible round-optimized schnorr threshold signatures. In: SAC 2020, 2020. To be published. https://eprint.iacr.org/2020/852
Langford, S.K.: Weaknesses in some threshold cryptosystems. In: Koblitz, N. (ed.) CRYPTO 1996. LNCS, vol. 1109, pp. 74–82. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68697-5_6
Ma, C., Weng, J., Li, Y., Deng, R.H.: Efficient discrete logarithm based multi-signature scheme in the plain public key model. Des. Codes Cryptogr. 54(2), 121–133 (2010). https://doi.org/10.1007/s10623-009-9313-z
Maxwell, G., Poelstra, A., Seurin, Y., Wuille, P.: Simple Schnorr multi-signatures with applications to Bitcoin. IACR Cryptology ePrint Archive, 2018/068, Version 20180118:124757, 2018. Preliminary obsolete version of [22]. https://eprint.iacr.org/2018/068/20180118:124757
Maxwell, G., Poelstra, A., Seurin, Y., Wuille, P.: Simple Schnorr multi-signatures with applications to Bitcoin. Des. Codes Cryptogr. 87(9), 2139–2164 (2019). https://eprint.iacr.org/2018/068.pdf
Micali, S., Ohta, K., Reyzin, L.: Accountable-subgroup multisignatures: extended abstract. In: Reiter, M.K., Samarati, P., (eds.) ACM CCS 2001, pp. 245–254. ACM Press, November 2001. https://doi.org/10.1145/501983.502017
Michels, M., Horster, P.: On the risk of disruption in several multiparty signature schemes. In: Kim, K., Matsumoto, T. (eds.) ASIACRYPT 1996. LNCS, vol. 1163, pp. 334–345. Springer, Heidelberg (1996). https://doi.org/10.1007/BFb0034859
Naor, M.: On cryptographic assumptions and challenges. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 96–109. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45146-4_6
Nick, J.: Insecure shortcuts in MuSig (2019). https://medium.com/blockstream/insecure-shortcuts-in-musig-2ad0d38a97da
Nick, J., Ruffing, T., Seurin, Y.: MuSig2: simple two-round schnorr multi-signatures. Cryptology ePrint Archive, Report 2020/1261 (2020). https://eprint.iacr.org/2020/1261
Nick, J., Ruffing, T., Seurin, Y., Wuille, P.: MuSig-DN: schnorr multi-signatures with verifiably deterministic nonces. In: Ligatti, J., Ou, X., Katz, J., Vigna, G., (eds.) ACM CCS 20, pp. 1717–1731. ACM Press, November 2020. https://doi.org/10.1145/3372297.3417236
Nicolosi, A., Krohn, M.N., Dodis, Y., Mazières, D.: Proactive two-party signatures for user authentication. In: NDSS 2003. The Internet Society, February 2003. https://www.ndss-symposium.org/ndss2003/proactive-two-party-signatures-user-authentication/
Pointcheval, D., Stern, J.: Security arguments for digital signatures and blind signatures. J. Cryptol. 13(3), 361–396 (2000). https://doi.org/10.1007/s001450010003
Ristenpart, T., Yilek, S.: The power of proofs-of-possession: securing multiparty signatures against rogue-key attacks. In: Naor, M. (ed.) EUROCRYPT 2007. LNCS, vol. 4515, pp. 228–245. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-72540-4_13
Schnorr, C.-P.: Efficient signature generation by smart cards. J. Cryptol. 4(3), 161–174 (1991). https://doi.org/10.1007/BF00196725
Schnorr, C.P.: Security of blind discrete log signatures against interactive attacks. In: Qing, S., Okamoto, T., Zhou, J. (eds.) ICICS 2001. LNCS, vol. 2229, pp. 1–12. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-45600-7_1
Shoup, V.: Lower bounds for discrete logarithms and related problems. In: Fumy, W. (ed.) EUROCRYPT 1997. LNCS, vol. 1233, pp. 256–266. Springer, Heidelberg (1997). https://doi.org/10.1007/3-540-69053-0_18
Stinson, D.R., Strobl, R.: Provably secure distributed schnorr signatures and a (t, n) threshold scheme for implicit certificates. In: Varadharajan, V., Mu, Y. (eds.) ACISP 2001. LNCS, vol. 2119, pp. 417–434. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-47719-5_33
Syta, E., et al.: Keeping authorities “honest or bust” with decentralized witness cosigning. In: 2016 IEEE Symposium on Security and Privacy, pages 526–545. IEEE Computer Society Press, May 2016. https://doi.org/10.1109/SP.2016.38
Wagner, D.: A generalized birthday problem. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 288–304. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_19
Wuille, P., Nick, J., Ruffing, T.: Schnorr signatures for secp256k1. Bitcoin Improvement Proposal 340 (2020). https://github.com/bitcoin/bips/blob/master/bip-0340.mediawiki
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Nick, J., Ruffing, T., Seurin, Y. (2021). MuSig2: Simple Two-Round Schnorr Multi-signatures. In: Malkin, T., Peikert, C. (eds) Advances in Cryptology – CRYPTO 2021. CRYPTO 2021. Lecture Notes in Computer Science(), vol 12825. Springer, Cham. https://doi.org/10.1007/978-3-030-84242-0_8
Download citation
DOI: https://doi.org/10.1007/978-3-030-84242-0_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-84241-3
Online ISBN: 978-3-030-84242-0
eBook Packages: Computer ScienceComputer Science (R0)


 may have received different “
may have received different “