Abstract
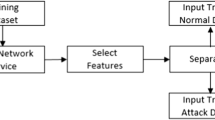
Machine learning (ML) techniques are essential in the detection of network attacks and enhancing network security. A device or software that recognizes any unusual pattern in the network and alerts the user about the same is an intrusion detection system (IDS). In this chapter, we have described the use of ML classification algorithms on the UNSW-NB15 dataset, leading to the generation of a network intrusion detection model which classifies incoming traffic into malicious or non-malicious traffic and issues an alert to the user. We have implemented the following ML algorithms – support vector machine, artificial neural network, and one-class support vector machine with an average accuracy of 89.25%, 91.54%, and 93.05%, respectively. Two graphical user interfaces (online and offline versions) have been developed for the system. Thus, the chapter proposes an optimized intrusion detection system that improves upon the existing intrusion detection systems which detect malicious packets in the network.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
N. Moustafa, J. Slay, UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). 2015 military communications and information systems conference (MilCIS) (IEEE, 2015)
S. Meftah, T. Rachidi, N. Assem, Network based intrusion detection using the UNSW-NB15 dataset. Int. J. Comput. Digital Syst. 8(5), 478–487 (2019)
M. Al-Zewairi, S. Almajali, A. Awajan, Experimental evaluation of a multi-layer feed-forward artificial neural network classifier for network intrusion detection system. 2017 International Conference on New Trends in Computing Sciences (ICTCS) (IEEE, 2017)
D. Pérez, et al., Comparison of network intrusion detection performance using feature representation. International Conference on Engineering Applications of Neural Networks (Springer, Cham, 2019)
S. Kaiser, K. Ferens, Machine learning classifiers for network intrusion detection (2018)
M. Zamani, M. Movahedi, Machine learning techniques for intrusion detection. arXiv preprint arXiv:1312.2177 (2013)
E. Hodo, X. Bellekens, A. Hamilton, C. Tachtatzis, R. Atkinson, Shallow and deep networks intrusion detection system: a taxonomy and survey. arXiv preprint arXiv:1701.02145 (2017)
L.A. Maglaras, J. Jiang, T. Cruz, Integrated OCSVM mechanism for intrusion detection in SCADA systems. Electr. Lett. 50(25), 1935–1936 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Nayak, S., Patil, A.A., Renganathan, R., Lakshmisudha, K. (2021). Optimizing Network Intrusion Detection Using Machine Learning. In: Stahlbock, R., Weiss, G.M., Abou-Nasr, M., Yang, CY., Arabnia, H.R., Deligiannidis, L. (eds) Advances in Data Science and Information Engineering. Transactions on Computational Science and Computational Intelligence. Springer, Cham. https://doi.org/10.1007/978-3-030-71704-9_40
Download citation
DOI: https://doi.org/10.1007/978-3-030-71704-9_40
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-71703-2
Online ISBN: 978-3-030-71704-9
eBook Packages: Mathematics and StatisticsMathematics and Statistics (R0)