Abstract
Before starting to play a two-player board game such as Chess and Shogi (namely, Japanese chess), we have to determine who makes the first move. Players’ strategies of Chess and Shogi often rely on whether they will move first or not, and most players have their own preferences. Therefore, it would be nice if we can take their individual requests into account when determining who goes first. To this end, if the two players simply tell their preferable moves to each other, they will notice the other’s strategy. Thus, we want the players to determine the first move according to their requests while hiding any information about them. Note that this problem cannot be solved by a typical way done in Chess, namely, a coin-flipping. In this paper, we formalize this problem in a cryptographic perspective and propose a secure protocol that solves this problem using a deck of physical cards. Moreover, we extend this problem to the multi-player setting: Assume that there is a single prize in a lottery drawing among more than two players, each of who has an individual secret feeling ‘Yes’ or ‘No’ that indicates whether he/she really wants to get the prize or not. If one or more players have ‘Yes,’ we want to randomly and covertly choose a winner among those having ‘Yes.’ If all of them have ‘No,’ we want to randomly pick a winner among all the players. We solve this extended problem, which we call the “covert lottery” problem, by proposing a simple card-based protocol.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
If we make \(X_n\) be two free cards by a random bisection cut before Step 4, the number of cards can be reduced to \(3n+2\) while the number of shuffles becomes \(n+2\). If we apply the AND protocol based on the encode
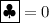 and
and 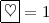 [17], we can have a \((3n+1)\)-card n-shuffle protocol or a 3n-card \((n+1)\)-shuffle protocol.
[17], we can have a \((3n+1)\)-card n-shuffle protocol or a 3n-card \((n+1)\)-shuffle protocol.
References
Abe, Y., Iwamoto, M., Ohta, K.: Efficient private PEZ protocols for symmetric functions. In: Hofheinz, D., Rosen, A. (eds.) TCC 2019. LNCS, vol. 11891, pp. 372–392. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-36030-6_15
Boer, B.: More efficient match-making and satisfiability The five card trick. In: Quisquater, J.J., Vandewalle, J. (eds.) EUROCRYPT 1989. LNCS, vol. 434, pp. 208–217. Springer, Heidelberg (1990). https://doi.org/10.1007/3-540-46885-4_23
Bultel, X., et al.: Physical zero-knowledge proof for Makaro. In: Izumi, T., Kuznetsov, P. (eds.) SSS 2018. LNCS, vol. 11201, pp. 111–125. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03232-6_8
Costiuc, M., MaimuŢ, D., Teşeleanu, G.: Physical cryptography. In: Simion, E., Géraud-Stewart, R. (eds.) Innovative Security Solutions for Information Technology and Communications, pp. 156–171. Springer International Publishing, Cham (2020)
Dumas, J.G., Lafourcade, P., Miyahara, D., Mizuki, T., Sasaki, T., Sone, H.: Interactive physical zero-knowledge proof for Norinori. In: Du, D.Z., Duan, Z., Tian, C. (eds.) COCOON 2019. LNCS, vol. 11653, pp. 166–177. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26176-4_14
Fagin, R., Naor, M., Winkler, P.: Comparing information without leaking it. Commun. ACM 39(5), 77–85 (1996). https://doi.org/10.1145/229459.229469
Gradwohl, R., Naor, M., Pinkas, B., Rothblum, G.N.: Cryptographic and physical zero-knowledge proof systems for solutions of Sudoku puzzles. Theory Comput. Syst. 44(2), 245–268 (2009). https://doi.org/10.1007/s00224-008-9119-9
Hashimoto, Y., Shinagawa, K., Nuida, K., Inamura, M., Hanaoka, G.: Secure grouping protocol using a deck of cards. In: Shikata, J. (ed.) ICITS 2017. LNCS, vol. 10681, pp. 135–152. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-72089-0_8
Ishikawa, R., Chida, E., Mizuki, T.: Efficient card-based protocols for generating a hidden random permutation without fixed points. In: Calude, C.S., Dinneen, M.J. (eds.) UCNC 2015. LNCS, vol. 9252, pp. 215–226. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-21819-9_16
Kastner, J., et al.: The minimum number of cards in practical card-based protocols. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10626, pp. 126–155. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70700-6_5
Koch, A., Schrempp, M., Kirsten, M.: Card-based cryptography meets formal verification. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019. LNCS, vol. 11921, pp. 488–517. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34578-5_18
Koch, A., Walzer, S.: Foundations for actively secure card-based cryptography. In: 10th International Conference on Fun with Algorithms (FUN 2020), pp. 1–27. Leibniz International Proceedings in Informatics (LIPIcs), Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik, Dagstuhl, Germany. https://doi.org/10.4230/LIPIcs.FUN.2021.17
Lafourcade, P., Miyahara, D., Mizuki, T., Sasaki, T., Sone, H.: A physical ZKP for Slitherlink: how to perform physical topology-preserving computation. In: Heng, S.H., Lopez, J. (eds.) ISPEC 2019. LNCS, vol. 11879, pp. 135–151. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34339-2_8
Miyahara, D., Hayashi, Y., Mizuki, T., Sone, H.: Practical card-based implementations of Yao’s millionaire protocol. Theoretical Comput. Sci. 803, 207–221 (2020). https://doi.org/10.1016/j.tcs.2019.11.005
Miyahara, D., et al.: Card-based ZKP protocols for Takuzu and Juosan. In: Farach-Colton, M., Prencipe, G., Uehara, R. (eds.) 10th International Conference on Fun with Algorithms (FUN 2020). Leibniz International Proceedings in Informatics (LIPIcs), vol. 157, pp. 20:1–20:21. Schloss Dagstuhl-Leibniz-Zentrum für Informatik, Dagstuhl, Germany (2020). https://drops.dagstuhl.de/opus/volltexte/2020/12781
Miyahara, D., Sasaki, T., Mizuki, T., Sone, H.: Card-based physical zero-knowledge proof for Kakuro. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E102A(9), 1072–1078 (2019). https://doi.org/10.1587/transfun.E102.A.1072
Mizuki, T.: Card-based protocols for securely computing the conjunction of multiple variables. Theoretical Comput. Sci. 622(C), 34–44 (2016). https://doi.org/10.1016/j.tcs.2016.01.039
Mizuki, T., Kugimoto, Y., Sone, H.: Secure multiparty computations using the 15 puzzle. In: Dress, A., Xu, Y., Zhu, B. (eds.) COCOA 2007. LNCS, vol. 4616, pp. 255–266. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-73556-4_28
Mizuki, T., Shizuya, H.: A formalization of card-based cryptographic protocols via abstract machine. Int. J. Inf. Secur. 13(1), 15–23 (2014). https://doi.org/10.1007/s10207-013-0219-4
Mizuki, T., Shizuya, H.: Computational model of card-based cryptographic protocols and its applications. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E100A(1), 3–11 (2017). https://doi.org/10.1587/transfun.E100.A.3
Mizuki, T., Sone, H.: Six-card secure AND and four-card secure XOR. In: Deng, X., Hopcroft, J.E., Xue, J. (eds.) FAW 2009. LNCS, vol. 5598, pp. 358–369. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-02270-8_36
Murata, S., Miyahara, D., Mizuki, T., Sone, H.: Public-PEZ cryptography. In: Susilo, W., Deng, R.H., Guo, F., Li, Y., Intan, R. (eds.) Information Security, pp. 59–74. Springer International Publishing, Cham (2020)
Nakai, T., Shirouchi, S., Iwamoto, M., Ohta, K.: Four cards are sufficient for a card-based three-input voting protocol utilizing private permutations. In: Shikata, J. (ed.) ICITS 2017. LNCS, vol. 10681, pp. 153–165. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-72089-0_9
Nakai, T., Tokushige, Y., Misawa, Y., Iwamoto, M., Ohta, K.: Efficient card-based cryptographic protocols for Millionaires’ problem utilizing private permutations. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 500–517. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_30
Nishida, T., Hayashi, Y., Mizuki, T., Sone, H.: Securely computing three-input functions with eight cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E98A(6), 1145–1152 (2015). https://doi.org/10.1587/transfun.E98.A.1145
Ono, H., Manabe, Y.: Efficient card-based cryptographic protocols for the millionaires’ problem using private input operations. In: 2018 13th Asia Joint Conference on Information Security (AsiaJCIS), pp. 23–28, August 2018. https://doi.org/10.1109/AsiaJCIS.2018.00013
Ono, H., Manabe, Y.: Card-based cryptographic protocols with the minimum number of rounds using private operations. In: Pérez-Solà, C., Navarro-Arribas, G., Biryukov, A., Garcia-Alfaro, J. (eds.) DPM/CBT 2019. LNCS, vol. 11737, pp. 156–173. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-31500-9_10
Ono, H., Manabe, Y.: Card-based cryptographic logical computations using private operations. New Gener. Comput. 1, 1–22 (2020). https://doi.org/10.1007/s00354-020-00113-z
Robert, L., Miyahara, D., Lafourcade, P., Mizuki, T.: Physical zero-knowledge proof for Suguru puzzle. In: Devismes, S., Mittal, N. (eds.) SSS 2020. LNCS, vol. 12514, pp. 235–247. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-64348-5_19
Ruangwises, S., Itoh, T.: Physical zero-knowledge proof for numberlink puzzle and k vertex-disjoint paths problem. New Gener. Comput. 1, 1–15 (2020). https://doi.org/10.1007/s00354-020-00114-y
Sasaki, T., Miyahara, D., Mizuki, T., Sone, H.: Efficient card-based zero-knowledge proof for Sudoku. Theoretical Comput. Sci. 839, 135–142 (2020). https://doi.org/10.1016/j.tcs.2020.05.036
Shinagawa, K., Nuida, K.: A single shuffle is enough for secure card-based computation of any Boolean circuit. Discrete Appl. Math. 289, 248–261 (2021). https://doi.org/10.1016/j.dam.2020.10.013
Takashima, K., et al.: Card-based secure ranking computations. In: Li, Y., Cardei, M., Huang, Y. (eds.) COCOA 2019. LNCS, vol. 11949, pp. 461–472. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-36412-0_37
Takashima, K., et al.: Card-based protocols for secure ranking computations. Theoretical Comput. Sci. 845, 122–135 (2020). https://doi.org/10.1016/j.tcs.2020.09.008
Toyoda, K., Miyahara, D., Mizuki, T., Sone, H.: Six-card finite-runtime XOR protocol with only random cut. In: Proceedings of the 7th ACM on ASIA Public-Key Cryptography Workshop, pp. 1–7. APKC 2020. ACM, New York, NY, USA. https://doi.org/10.1145/3384940.3388961
Ueda, I., Miyahara, D., Nishimura, A., Hayashi, Y., Mizuki, T., Sone, H.: Secure implementations of a random bisection cut. Int. J. Inf. Secur. 19(4), 445–452 (2019). https://doi.org/10.1007/s10207-019-00463-w
Ueda, I., Nishimura, A., Hayashi, Y., Mizuki, T., Sone, H.: How to implement a random bisection cut. In: Martín-Vide, C., Mizuki, T., Vega-Rodríguez, M.A. (eds.) TPNC 2016. LNCS, vol. 10071, pp. 58–69. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-49001-4_5
Watanabe, Y., Kuroki, Y., Suzuki, S., Koga, Y., Iwamoto, M., Ohta, K.: Card-based majority voting protocols with three inputs using three cards. In: 2018 International Symposium on Information Theory and Its Applications (ISITA), pp. 218–222 (2018). https://doi.org/10.23919/ISITA.2018.8664324
Yasunaga, K.: Practical card-based protocol for three-input majority. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E103A(11), 1296–1298 (2020). https://doi.org/10.1587/transfun.2020EAL2025
Acknowledgements
We thank the anonymous referees, whose comments have helped us to improve the presentation of the paper. We thank the anonymous reviewer at some conference who have inspired us to present the protocol shown in Sect. 3. This work was supported in part by JSPS KAKENHI Grant Numbers JP19J21153 and JP20J01192.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Shinoda, Y., Miyahara, D., Shinagawa, K., Mizuki, T., Sone, H. (2021). Card-Based Covert Lottery. In: Maimut, D., Oprina, AG., Sauveron, D. (eds) Innovative Security Solutions for Information Technology and Communications. SecITC 2020. Lecture Notes in Computer Science(), vol 12596. Springer, Cham. https://doi.org/10.1007/978-3-030-69255-1_17
Download citation
DOI: https://doi.org/10.1007/978-3-030-69255-1_17
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-69254-4
Online ISBN: 978-3-030-69255-1
eBook Packages: Computer ScienceComputer Science (R0)





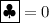 and
and 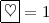 [
[