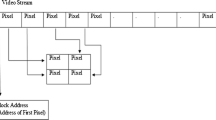
Abstract
In this paper, a new method for video authentication is proposed. The method is based on construction of watermark images, which serve as a secondary carrier for the binary sequence. A unique watermark image is embedded into the coefficients of Discrete Wavelet Transform of each video frame. The analysis of images extracted from video allows to detect spatial attacks, and the sequence carried by the extracted images provides the ability to determine the type of temporal attack and localize the frames, which are tampered. The experimental study on the method quality and efficiency is conducted. According to the results of experiments, the method is suitable for solving authentication tasks. Furthermore, the method is robust to compression and format re-encoding.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Dabhade, V., Bhople, Y.J., Chandrasekaran, K., Bhattacharya, S.: Video tamper detection techniques based on DCT-SVD and multi-level SVD. In: TENCON IEEE, pp. 1–6 (2015)
Ghimire, S., Choi, J., Lee, B.: Using blockchain for improved video integrity verification. IEEE Trans. Multimed. 22(1), 108–121 (2019)
Khelifi, F., Bouridane, A.: Perceptual video hashing for content identification and authentication. IEEE Trans. Circuits Syst. Video Technol. 29(1), 50–67 (2019)
Sitara, K., Babu, M.: Digital video tampering detection: an overview of passive techniques. Digit. Invest. 18, 8–22 (2016)
Aditya, B., Avaneesh, U., Adithya, K., Murthy, A., Sandeep, R., Kavyashree, B.: Invisible semi-fragile watermarking and steganography of digital videos for content authentication and data hiding. Int. J. Image Graph. 19(3), 1–19 (2019)
Shiddik, L., Novamizanti, L., Ramatryana, I., Hanifan, H.: Compressive sampling for robust video watermarking based on BCH code in SWT-SVD domain. In: International Conference on Sustainable Engineering and Creative Computing (ICSECC), pp. 223–227 (2019)
Sharma, C., Bagga, A.: Video watermarking scheme based on DWT, SVD, Rail fence for quality loss of data. In: 4th International Conference on Computing Sciences (ICCS), pp. 84–87 (2018)
Alenizi, F., Kurdahi, F., Eltawil, A.M., Al-Asmari, A.K.: Hybrid pyramid-DWT-SVD dual data hiding technique for videos ownership protection. Multimed. Tools Appl. 78(11), 14511–14547 (2018). https://doi.org/10.1007/s11042-018-6723-9
Barani, M.J., Ayubi, P., Valandar, M.Y., Irani, B.Y.: A blind video watermarking algorithm robust to lossy video compression attacks based on generalized Newton complex map and contourlet transform. Multimed. Tools Appl. 79(3), 2127–2159 (2020)
Guangxi, C., Ze, C., Daoshun, W., Shundong, L., Yong, H., Baoying, Z.: Combined DTCWT-SVD-based video watermarking algorithm using finite state machine. In: Eleventh International Conference on Advanced Computational Intelligence, pp. 179–183 (2019)
Rakhmawati, L., Wirawan, W., Suwadi, S.: A recent survey of self-embedding fragile watermarking scheme for image authentication with recovery capability. EURASIP J. Image Video Process. 2019(1), 1–22 (2019). https://doi.org/10.1186/s13640-019-0462-3
Solanki, N., Khandelwal, S., Gaur, S., Gautam, D.: A comparative analysis of wavelet families for invisible image embedding. In: Rathore, V.S., Worring, M., Mishra, D.K., Joshi, A., Maheshwari, S. (eds.) Emerging Trends in Expert Applications and Security. AISC, vol. 841, pp. 219–227. Springer, Singapore (2019). https://doi.org/10.1007/978-981-13-2285-3_27
Sujatha, C.N., Sathyanarayana, P.: DWT-based blind video watermarking using image scrambling technique. In: Satapathy, S.C., Joshi, A. (eds.) Information and Communication Technology for Intelligent Systems. SIST, vol. 106, pp. 621–628. Springer, Singapore (2019). https://doi.org/10.1007/978-981-13-1742-2_62
Wagdarikar, A., Senapati, R.: Optimization based interesting region identification for video watermarking. J. Inf. Secur. Appl. 49, 1–17 (2019)
Wagdarikar, A.M.U., Senapati, R.K., Ekkeli, S.: A secure video watermarking approach using CRT theorem in DCT domain. In: Panda, G., Satapathy, S.C., Biswal, B., Bansal, R. (eds.) Microelectronics, Electromagnetics and Telecommunications. LNEE, vol. 521, pp. 597–606. Springer, Singapore (2019). https://doi.org/10.1007/978-981-13-1906-8_61
Tian, L., Dai, H., Li, C.: A semi-fragile video watermarking algorithm based on chromatic residual DCT. Multimed. Tools Appl. 79(5), 1759–1779 (2020)
Wong, K., Chan, C., Maung, M.A.: Lightweight authentication for MP4 format container using subtitle track. IEICE Trans. Inf. Syst. E103.D(1), 2–10 (2020)
Maung, M.A.P., Tew, Y., Wong, K.: Authentication of Mp4 file By perceptual hash and data hiding. Malaysian J. Comput. Sci. 32(4), 304–314 (2019)
Vega-Hernandez, P., Cedillo-Hernandez, M., Nakano, M., Cedillo-Hernandez, A., Perez-Meana, H.: Ownership identification of digital video via unseen-visible watermarking. In: 7th International Workshop on Biometrics and Forensics (IWBF), pp. 1–6 (2019)
Cao, Z., Wang, L.: A secure video watermarking technique based on hyperchaotic Lorentz system. Multimed. Tools Appl. 78(18), 26089–26109 (2019). https://doi.org/10.1007/s11042-019-07809-5
Munir, R., Harlili: A secure fragile video watermarking algorithm for content authentication based on arnold cat map. In: 4th International Conference on Information Technology, pp. 32–37 (2019)
Vybornova, Y., Sergeev, V.: Method for vector map protection based on using of a watermark image as a secondary carrier. In: ICETE 2019 - Proceedings of the 16th International Joint Conference on e-Business and Telecommunications, pp. 284–293 (2019)
Lin, J.Y., Song, R., Wu, C.-H., Liu, T.-J., Wang, H., Kuo, C.-C.J.: MCL-V: a streaming video quality assessment database. J. Vis. Commun. Image Represent. 30, 1–9 (2015)
Acknowledgements
The reported study was funded by RFBR (Russian Foundation for Basic Research): projects No. 19-29-09045, No. 19-07-00474, No. 19-07-00138, No. 20-37-70053.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Vybornova, Y. (2020). A New Watermarking Method for Video Authentication with Tamper Localization. In: Chmielewski, L.J., Kozera, R., Orłowski, A. (eds) Computer Vision and Graphics. ICCVG 2020. Lecture Notes in Computer Science(), vol 12334. Springer, Cham. https://doi.org/10.1007/978-3-030-59006-2_18
Download citation
DOI: https://doi.org/10.1007/978-3-030-59006-2_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-59005-5
Online ISBN: 978-3-030-59006-2
eBook Packages: Computer ScienceComputer Science (R0)