Abstract
Java is a high-level, well-known and powerful object-oriented language, with a large support library and a comfortable toolbelt. Hence, it has been proposed for writing smart contracts in blockchain. However, its support library is non-deterministic, which is a blocking issue for its application to smart contracts. This paper discusses the kind of (non-)determinism of the methods of the Java library and how a deterministic fragment of that library can be specified. It shows that some relevant parts are deterministic only under specific conditions on run-time values. It concludes with the description of an instrumentation, for the Takamaka blockchain, that enforces such conditions, statically or dynamically, reporting experiments with its implementation.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
Java also allows so-called special calls, such as
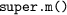 , that start the look-up from a given static type; as well as calls embedded in closures, such as method references (corresponding to
, that start the look-up from a given static type; as well as calls embedded in closures, such as method references (corresponding to
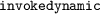 in Java bytecode). For simplicity, these calls are not discussed here, but our implementation deals with them.
in Java bytecode). For simplicity, these calls are not discussed here, but our implementation deals with them. - 2.
These signatures are copy and paste from the library source code. For the use of generics, wildcards and
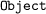 in these signatures, we refer to
[13].
in these signatures, we refer to
[13]. - 3.
The Java bytecode of the smart contract will contain an instruction
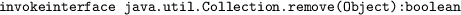 , or a similar one for a subtype of
, or a similar one for a subtype of
 .
.
References
Hello World...from the Aion Virtual Machine! https://aion.theoan.com/blog/hello-world-from-the-aion-virtual-machine/
How to Use Java to Write a NEO Smart Contract. https://docs.neo.org/docs/en-us/sc/devenv/getting-started-java.html
BCEL. https://commons.apache.org/proper/commons-bcel. Accessed December 2017
Androulaki, E., et al.: Hyperledger fabric: a distributed operating system for permissioned blockchains. In: Proceedings of the Thirteenth EuroSys Conference, EuroSys 2018, Porto, Portugal, pp. 30:1–30:15. ACM (2018)
Antonopoulos, A.M.: Mastering Bitcoin: Programming the Open Blockchain, 2nd edn. Oreilly & Associates Inc., Boston (2017)
Antonopoulos, A.M., Wood, G.: Mastering Ethereum: Building Smart Contracts and Dapps, 1st edn. Oreilly & Associates Inc., Boston (2018)
Banerjee, A., Naumann, D.A.: Stack-based access control and secure information flow. J. Funct. Program. 15(2), 131–177 (2005)
Barthe, G., Pichardie, D., Rezk, T.: A certified lightweight non-interference Java bytecode verifier. Math. Struct. Comput. Sci. 23(5), 1032–1081 (2013)
Chatterjee, K., Goharshady, A.K., Pourdamghani, A.: Probabilistic smart contracts: secure randomness on the blockchain. In: Proceedings of the IEEE International Conference on Blockchain and Cryptocurrency (ICBC 2019), Seoul, South Korea, pp. 403–412. IEEE (2019)
Cormen, T.H., Leiserson, C.E., Rivest, R.L., Stein, C.: Introduction to Algorithms, 3rd edn. MIT Press, Cambridge (2009)
Iyer, K., Dannen, C.: Building Games with Ethereum Smart Contracts. Apress, New York (2018)
Liskov, B., Wing, J.M.: A behavioral notion of subtyping. ACM Trans. Program. Lang. Syst. 16(6), 1811–1841 (1994)
Naftalin, M., Wadler, P.: Java Generics and Collections. O’Reilly, Cambridge (2006)
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system. https://bitcoin.org/bitcoin.pdf. Accessed October 2008
Nielson, F., Nielson, H.R., Hankin, C.: Principles of Program Analysis. Springer, Heidelberg (1999). https://doi.org/10.1007/978-3-662-03811-6
Rice, H.G.: Classes of recursively enumerable sets and their decision problems. Trans. Am. Math. Soc. 74(2), 358–366 (1953)
Spoto, F.: A Java framework for smart contracts. In: Bracciali, A., Clark, J., Pintore, F., Rønne, P.B., Sala, M. (eds.) FC 2019. LNCS, vol. 11599, pp. 122–137. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-43725-1_10
Vukolić, M.: Rethinking permissioned blockchains. In: Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts (BCC 2017), Abu Dhabi, United Arab Emirates, pp. 3–7. ACM, April 2017
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Spoto, F. (2020). Enforcing Determinism of Java Smart Contracts. In: Bernhard, M., et al. Financial Cryptography and Data Security. FC 2020. Lecture Notes in Computer Science(), vol 12063. Springer, Cham. https://doi.org/10.1007/978-3-030-54455-3_40
Download citation
DOI: https://doi.org/10.1007/978-3-030-54455-3_40
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-54454-6
Online ISBN: 978-3-030-54455-3
eBook Packages: Computer ScienceComputer Science (R0)


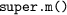 , that start the look-up from a given static type; as well as calls embedded in closures, such as method references (corresponding to
, that start the look-up from a given static type; as well as calls embedded in closures, such as method references (corresponding to
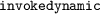 in Java bytecode). For simplicity, these calls are not discussed here, but our implementation deals with them.
in Java bytecode). For simplicity, these calls are not discussed here, but our implementation deals with them. in these signatures, we refer to
[
in these signatures, we refer to
[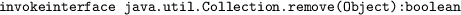 , or a similar one for a subtype of
, or a similar one for a subtype of
 .
.