Abstract
Cloud-based services enable easy-to-use data-sharing between multiple parties, and, therefore, have been widely adopted over the last decade. Storage services by large cloud providers such as Dropbox or Google Drive as well as federated solutions such as Nextcloud have amassed millions of users. Nevertheless, privacy challenges hamper the adoption of such services for sensitive data: Firstly, rather than exposing their private data to a cloud service, users desire end-to-end confidentiality of the shared files without sacrificing usability, e.g., without repeatedly encrypting when sharing the same data set with multiple receivers. Secondly, only being able to expose complete (authenticated) files may force users to expose overmuch information. The receivers, as well as the requirements, might be unknown at issue-time, and thus the issued data set does not exactly match those requirements. This mismatch can be bridged by enabling cloud services to selectively disclose only relevant parts of a file without breaking the parts’ authenticity. While both challenges have been solved individually, it is not trivial to combine these solutions and maintain their security intentions.
In this paper, we tackle this issue and introduce selective end-to-end data-sharing by combining ideas from proxy re-encryption and redactable signature schemes. Proxy re-encryption provides us with the basis for end-to-end encrypted data-sharing, while redactable signatures enable to redact parts and selectively disclose only the remaining still authenticated parts. We overcome the issues encountered when naively combining these two concepts, introduce a security model, and present a modular instantiation together with implementations based on a selection of various building blocks. We conclude with an extensive performance evaluation of our instantiation.
S. Ramacher—Work done while the author was with Graz University of Technology.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
References
Ateniese, G., Benson, K., Hohenberger, S.: Key-private proxy re-encryption. In: Fischlin, M. (ed.) CT-RSA 2009. LNCS, vol. 5473, pp. 279–294. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-00862-7_19
Ateniese, G., Fu, K., Green, M., Hohenberger, S.: Improved proxy re-encryption schemes with applications to secure distributed storage. In: NDSS. The Internet Society (2005)
Ateniese, G., Fu, K., Green, M., Hohenberger, S.: Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. 9(1), 1–30 (2006)
Barbulescu, R., Duquesne, S.: Updating key size estimations for pairings. J. Cryptol. 32(4), 1298–1336 (2019)
Barker, E.: SP 800–57. Recommendation for Key Management, Part 1: General (Rev 4). Technical report, National Institute of Standards & Technology (2016)
Blaze, M., Bleumer, G., Strauss, M.: Divertible protocols and atomic proxy cryptography. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 127–144. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054122
Boneh, D., Sahai, A., Waters, B.: Functional encryption: definitions and challenges. In: Ishai, Y. (ed.) TCC 2011. LNCS, vol. 6597, pp. 253–273. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-19571-6_16
Brzuska, C., et al.: Redactable signatures for tree-structured data: definitions and constructions. In: Zhou, J., Yung, M. (eds.) ACNS 2010. LNCS, vol. 6123, pp. 87–104. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13708-2_6
Camenisch, J., Herreweghen, E.V.: Design and implementation of the idemix anonymous credential system. In: ACM CCS, pp. 21–30. ACM (2002)
Camenisch, J., Lysyanskaya, A.: An efficient system for non-transferable anonymous credentials with optional anonymity revocation. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 93–118. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44987-6_7
Camenisch, J., Lysyanskaya, A.: Dynamic accumulators and application to efficient revocation of anonymous credentials. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 61–76. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_5
Canetti, R., Hohenberger, S.: Chosen-ciphertext secure proxy re-encryption. In: ACM CCS, pp. 185–194. ACM (2007)
Chandran, N., Chase, M., Liu, F.-H., Nishimaki, R., Xagawa, K.: Re-encryption, functional re-encryption, and multi-hop re-encryption: a framework for achieving obfuscation-based security and instantiations from lattices. In: Krawczyk, H. (ed.) PKC 2014. LNCS, vol. 8383, pp. 95–112. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-642-54631-0_6
Chaum, D.: Untraceable electronic mail, return addresses, and digital pseudonyms. Commun. ACM 24(2), 84–88 (1981)
Chaum, D.: Security without identification: transaction systems to make big brother obsolete. Commun. ACM 28(10), 1030–1044 (1985)
Chow, S.S.M., Weng, J., Yang, Y., Deng, R.H.: Efficient unidirectional proxy re-encryption. In: Bernstein, D.J., Lange, T. (eds.) AFRICACRYPT 2010. LNCS, vol. 6055, pp. 316–332. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-12678-9_19
Demirel, D., Derler, D., Hanser, C., Pöhls, H.C., Slamanig, D., Traverso, G.: PRISMACLOUD D4.4: overview of functional and malleable signature schemes. Technical repoet, H2020 PRISMACLOUD (2015)
Derler, D., Hanser, C., Slamanig, D.: Revisiting cryptographic accumulators, additional properties and relations to other primitives. In: Nyberg, K. (ed.) CT-RSA 2015. LNCS, vol. 9048, pp. 127–144. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-16715-2_7
Derler, D., Hanser, C., Slamanig, D.: Revisiting cryptographic accumulators, additional properties and relations to other primitives. IACR ePrint 2015, 87 (2015)
Derler, D., Krenn, S., Lorünser, T., Ramacher, S., Slamanig, D., Striecks, C.: Revisiting proxy re-encryption: forward secrecy, improved security, and applications. In: Abdalla, M., Dahab, R. (eds.) PKC 2018. LNCS, vol. 10769, pp. 219–250. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-76578-5_8
Derler, D., Krenn, S., Slamanig, D.: Signer-anonymous designated-verifier redactable signatures for cloud-based data sharing. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 211–227. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_13
Derler, D., Pöhls, H.C., Samelin, K., Slamanig, D.: A general framework for redactable signatures and new constructions. In: Kwon, S., Yun, A. (eds.) ICISC 2015. LNCS, vol. 9558, pp. 3–19. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-30840-1_1
Derler, D., Ramacher, S., Slamanig, D.: Homomorphic proxy re-authenticators and applications to verifiable multi-user data aggregation. In: Kiayias, A. (ed.) FC 2017. LNCS, vol. 10322, pp. 124–142. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70972-7_7
European Commission: Regulation (EU) 2016/679 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation). Official Journal of the European Union L119/59, May 2016
Goyal, V., Pandey, O., Sahai, A., Waters, B.: Attribute-based encryption for fine-grained access control of encrypted data. In: ACM CCS, pp. 89–98. ACM (2006)
Hörandner, F., Krenn, S., Migliavacca, A., Thiemer, F., Zwattendorfer, B.: CREDENTIAL: a framework for privacy-preserving cloud-based data sharing. In: ARES, pp. 742–749. IEEE Computer Society (2016)
Johnson, R., Molnar, D., Song, D., Wagner, D.: Homomorphic signature schemes. In: Preneel, B. (ed.) CT-RSA 2002. LNCS, vol. 2271, pp. 244–262. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45760-7_17
Krenn, S., Lorünser, T., Salzer, A., Striecks, C.: Towards attribute-based credentials in the cloud. In: Capkun, S., Chow, S.S.M. (eds.) CANS 2017. LNCS, vol. 11261, pp. 179–202. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-02641-7_9
Kundu, A., Bertino, E.: Privacy-preserving authentication of trees and graphs. Int. J. Inf. Sec. 12(6), 467–494 (2013)
Libert, B., Vergnaud, D.: Unidirectional chosen-ciphertext secure proxy re-encryption. In: Cramer, R. (ed.) PKC 2008. LNCS, vol. 4939, pp. 360–379. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-78440-1_21
Menezes, A., Sarkar, P., Singh, S.: Challenges with assessing the impact of NFS advances on the security of pairing-based cryptography. In: Phan, R.C.-W., Yung, M. (eds.) Mycrypt 2016. LNCS, vol. 10311, pp. 83–108. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-61273-7_5
Nguyen, L.: Accumulators from bilinear pairings and applications. In: Menezes, A. (ed.) CT-RSA 2005. LNCS, vol. 3376, pp. 275–292. Springer, Heidelberg (2005). https://doi.org/10.1007/978-3-540-30574-3_19
Paquin, C., Zaverucha, G.: U-prove cryptographic specification v1.1 (revision 3). Technical report, Microsoft, December 2013
Pirretti, M., Traynor, P., McDaniel, P.D., Waters, B.: Secure attribute-based systems. In: ACM CCS, pp. 99–112. ACM (2006)
Sahai, A., Waters, B.: Fuzzy identity-based encryption. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005). https://doi.org/10.1007/11426639_27
Samelin, K., Pöhls, H.C., Bilzhause, A., Posegga, J., de Meer, H.: Redactable signatures for independent removal of structure and content. In: Ryan, M.D., Smyth, B., Wang, G. (eds.) ISPEC 2012. LNCS, vol. 7232, pp. 17–33. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29101-2_2
Steinfeld, R., Bull, L., Zheng, Y.: Content extraction signatures. In: Kim, K. (ed.) ICISC 2001. LNCS, vol. 2288, pp. 285–304. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45861-1_22
Weng, J., Deng, R.H., Ding, X., Chu, C., Lai, J.: Conditional proxy re-encryption secure against chosen-ciphertext attack. In: AsiaCCS, pp. 322–332. ACM (2009)
Acknowledgments
This work was supported by the H2020 EU project credential under grant agreement number 653454.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Proof of Theorem 1
A Proof of Theorem 1
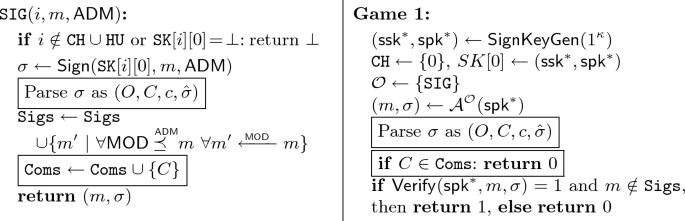
We prove Theorem 1 by proving Lemma 1–4 to show the properties unforgeability, proxy privacy, receiver privacy, and, finally, transparency. For proofs using a sequence of games, we denote the event that an adversary wins game i by \(S_i\).
Lemma 1
If \(\mathsf {RSS}\) is unforgeable and \(\mathsf {C}\) is binding, then Scheme 1 is unforgeable.
Proof
We prove this lemma using a sequence of games.
-
Game 0: The original \(\mathsf {SEEDS}\) unforgeability game.
-
Game 1: We adapt Game 0 to also abort when the signatures were generated by \(\mathtt {SIG} \).
-
Transition \(0 \Rightarrow 1\): Game 1 behaves the same as Game 0 unless \(\mathcal {A} \) returned a valid pair \((m, \sigma )\) where the included \(\mathsf {RSS} \) signature \(\hat{\sigma }\) on \(\{C \}\mathord {\cup }c \) was generated by \(\mathtt {SIG}\). We denote this failure event as F, thus \(\left| \Pr [S_0] - \Pr [S_1] \right| \le \Pr [F]\). In this case, since \(C \), \(c \), and \(\hat{\sigma }\) are fixed, two different messages can only be obtained, by decrypting with different keys \(k_1\) and \(k_2\). From the fixed \(C \), different keys can only be recovered with different opening informations \(O _1\) and \(O _2\). To achieve this, the adversary would have to break the binding property of \(\mathsf {C}\), therefore \(\Pr [F] = \epsilon _{\mathsf {C}}^{Bind}(\kappa )\).
Finally, we build an efficient adversary \(\mathcal {B} \) from an adversary \(\mathcal {A} \) winning Game 1 for the unforgeability of \(\mathsf {RSS}\) in \(\mathcal {R} _{\mathsf {RSS}}^{Unf}\rightarrow {G_1}\). We can simulate \(\mathtt {SIG} \) except for \(i = 0\), where we obtain the \(\mathsf {RSS}\) signatures using its signing oracle. Note that all values are consistently distributed. Now, if we obtain a forgery (\(m, \sigma )\) from \(\mathcal {A} \), then parse \(\sigma \) as \((O, C, c, \hat{\sigma })\) and forward \(\{ C \} \cup c, \hat{\sigma }\) as a forgery. Therefore, \(\Pr [S_1] = \epsilon _{\mathsf {RSS}}^{Unf}(\kappa )\), resulting in \(\Pr [S_0] = \epsilon _{\mathsf {C}}^{Bind}(\kappa ) + \epsilon _{\mathsf {RSS}}^{Unf}(\kappa ) \), which is negligible.

Lemma 2
If the \(\mathsf {PRE}\) is IND-RCCA-2 secure, \(\mathsf {C}\) is hiding, \(\mathsf {S}\) is IND-CPA secure, and \(\mathsf {RSS}\) is unforgeable, then Scheme 1 is proxy private.
Proof
We prove proxy privacy using a sequence of games.
-
Game 0: The original \(\mathsf {SEEDS}\) proxy privacy game.
-
Game 1: We restrict the decryption oracles to ciphertexts that contain messages signed by the signature oracle. Therefore, we adapt \(\mathtt {SE} \) as \(\mathtt {SIG} \) in Lemma 1 to track the generated commitments,
 . Also, we adapt \(\mathtt {D} \) to
. Also, we adapt \(\mathtt {D} \) to
 and
and
 .
. -
Transition \(0 \Rightarrow 1\): The two games proceed identically unless the adversary submits a valid signature to \(\mathtt {D}\). In that case the adversary produced a forgery, i.e. \(|\Pr [S_0] - \Pr [S_1]| \le \epsilon ^{Unf}_{\mathsf {SEEDS}}(\kappa )\).
-
Game 2: In the used \(\mathsf {Encrypt}\) algorithm, we replace the opening information with a random r from the same domain, and simulate the oracles accordingly:


-
Transition \(1 \Rightarrow 2\): From a distinguisher \(\mathcal {D}^{1 \rightarrow 2}\), we build an IND-RCCA-2 adversary against the \(\mathsf {PRE}\) scheme. Indeed, let \(\mathcal {C}\) be an IND-RCCA-2 challenger. We modify \(\mathsf {Encrypt}\) in the following way: Simulate everything honestly, but sample
 uniformly at random from the domain of openings of \(\mathsf {C}\) and run
uniformly at random from the domain of openings of \(\mathsf {C}\) and run
 , where \(c \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge ciphertext with respect to \(m_0\) and \(m_1\). The \(\mathtt {RE} \) oracle calls the challenger’s \(\mathtt {RE} \) oracle instead of \(\mathsf {PRE}.\mathsf {ReEnc} \). Consequently, \(|\Pr [S_1] - \Pr [S_2]| \le \epsilon ^{IND-RCCA-2}_{\mathsf {PRE}}(\kappa )\).
, where \(c \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge ciphertext with respect to \(m_0\) and \(m_1\). The \(\mathtt {RE} \) oracle calls the challenger’s \(\mathtt {RE} \) oracle instead of \(\mathsf {PRE}.\mathsf {ReEnc} \). Consequently, \(|\Pr [S_1] - \Pr [S_2]| \le \epsilon ^{IND-RCCA-2}_{\mathsf {PRE}}(\kappa )\). -
Game 3: For the signature contained in the challenge ciphertext, we commit to a random value, i.e., we set
 and
and
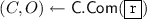 .
. -
Transition \(2 \Rightarrow 3\): From a distinguisher \(\mathcal {D}^{2 \rightarrow 3}\), we obtain a hiding adversary against \(\mathsf {C} \). Let \(\mathcal {C}\) be a hiding challenger. We modify \(\mathsf {Sign}\) in the following way: Simulate everything honestly, but choose
 uniformly at random from the same domain as the \(\mathsf {S}\) keys and run
uniformly at random from the same domain as the \(\mathsf {S}\) keys and run
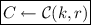 , where \(C \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge commitment with respect to \(m_0\) and \(m_1\). Therefore, \(|\Pr [S_2] - \Pr [S_3]| \le \epsilon ^{Hide}_{\mathsf {C}}(\kappa )\).
, where \(C \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge commitment with respect to \(m_0\) and \(m_1\). Therefore, \(|\Pr [S_2] - \Pr [S_3]| \le \epsilon ^{Hide}_{\mathsf {C}}(\kappa )\). -
Game 4: In the challenge ciphertext, we replace the message parts with random values drawn from an identical domain with the same corresponding lengths, i.e.
 and
and
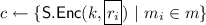 .
. -
Transition \(3 \Rightarrow 4\): A distinguisher \(\mathcal {D}^{3 \rightarrow 4}\) is a (hybrid) IND-CPA adversary against \(\mathsf {S}\). Let \(\mathcal {C}\) be an IND-CPA challenger. We modify \(\mathsf {Sign}\) in the following way: Simulate everything honestly, but for each message part choose
 uniformly at random from the message space and run
uniformly at random from the message space and run
 , where \(c \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge ciphertext with respect to \(m_0\) and \(m_1\). Therefore, \(|\Pr [S_4] - \Pr [S_3]| \le |m | \cdot \epsilon ^{IND-CPA}_{\mathsf {S}}(\kappa )\), with \(|m |\) polynomial in the security parameter \(\kappa \).
, where \(c \leftarrow \mathcal {C}(m_0, m_1)\) denotes a challenge ciphertext with respect to \(m_0\) and \(m_1\). Therefore, \(|\Pr [S_4] - \Pr [S_3]| \le |m | \cdot \epsilon ^{IND-CPA}_{\mathsf {S}}(\kappa )\), with \(|m |\) polynomial in the security parameter \(\kappa \).
Finally, we have that
 , since the adversary now cannot do better than guessing. Combining the claims, we see that the following is negligible:
, since the adversary now cannot do better than guessing. Combining the claims, we see that the following is negligible:

Lemma 3
If \(\mathsf {RSS}\) is private, then Scheme 1 is receiver private.
Proof
Assuming there is an efficient adversary \(\mathcal {A} \) against the receiver privacy of Scheme 1, we build an adversary \(\mathcal {B} \) against the privacy of \(\mathsf {RSS} \):

The reduction extends the \(\mathsf {RSS} \) public key to a \(\mathsf {SEEDS} \) public key, and forwards it to \(\mathcal {A} \). The oracle \(\mathtt {LoRRedact}\) sets up everything honestly and obtains signatures from \(\mathtt {LoRRedact}\) of \(\mathsf {RSS}\). All values are distributed consistently, and \(\mathcal {B}\) wins the privacy experiment of \(\mathsf {RSS}\) with the same probability as \(\mathcal {A} \) breaks the \(\mathsf {SEEDS}\) receiver privacy of Scheme 1.
Lemma 4
If \(\mathsf {RSS}\) is transparent, then Scheme 1 is transparent.
Proof
Assuming there is an efficient adversary \(\mathcal {A} \) against the transparency of Scheme 1, we construct an adversary \(\mathcal {B} \) against the transparency of the RSS:

The reduction extends the RSS public key to a \(\mathsf {SEEDS} \) public key honestly, and forwards it together with the secret encryption key to \(\mathcal {A} \). Similarly, \(\mathtt {RedactOrNot}\) sets up everything honestly and queries the RSS oracle \(\mathcal {O} ^{Sign/Redact}\) to obtain the signature. Finally, it outputs a consistent ciphertext, hence, \(\mathcal {B} \) wins with the same probability as \(\mathcal {A} \).
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Hörandner, F., Ramacher, S., Roth, S. (2019). Selective End-To-End Data-Sharing in the Cloud. In: Garg, D., Kumar, N., Shyamasundar, R. (eds) Information Systems Security. ICISS 2019. Lecture Notes in Computer Science(), vol 11952. Springer, Cham. https://doi.org/10.1007/978-3-030-36945-3_10
Download citation
DOI: https://doi.org/10.1007/978-3-030-36945-3_10
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-36944-6
Online ISBN: 978-3-030-36945-3
eBook Packages: Computer ScienceComputer Science (R0)



 . Also, we adapt
. Also, we adapt  and
and
 .
.

 uniformly at random from the domain of openings of
uniformly at random from the domain of openings of  , where
, where  and
and
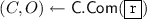 .
. uniformly at random from the same domain as the
uniformly at random from the same domain as the 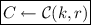 , where
, where  and
and
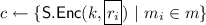 .
. uniformly at random from the message space and run
uniformly at random from the message space and run
 , where
, where