Abstract
Card-based cryptography provides simple and practicable protocols for performing secure multi-party computation (MPC) with just a deck of cards. For the sake of simplicity, this is often done using cards with only two symbols, e.g.,
 and
and
 . Within this paper, we target the setting where all cards carry distinct symbols, catering for use-cases with commonly available standard decks and a weaker indistinguishability assumption. As of yet, the literature provides for only three protocols and no proofs for non-trivial lower bounds on the number of cards. As such complex proofs (handling very large combinatorial state spaces) tend to be involved and error-prone, we propose using formal verification for finding protocols and proving lower bounds. In this paper, we employ the technique of software bounded model checking (SBMC), which reduces the problem to a bounded state space, which is automatically searched exhaustively using a SAT solver as a backend.
. Within this paper, we target the setting where all cards carry distinct symbols, catering for use-cases with commonly available standard decks and a weaker indistinguishability assumption. As of yet, the literature provides for only three protocols and no proofs for non-trivial lower bounds on the number of cards. As such complex proofs (handling very large combinatorial state spaces) tend to be involved and error-prone, we propose using formal verification for finding protocols and proving lower bounds. In this paper, we employ the technique of software bounded model checking (SBMC), which reduces the problem to a bounded state space, which is automatically searched exhaustively using a SAT solver as a backend.
Our contribution is twofold: (a) We identify two protocols for converting between different bit encodings with overlapping bases, and then show them to be card-minimal. This completes the picture of tight lower bounds on the number of cards with respect to runtime behavior and shuffle properties of conversion protocols. For computing
 , we show that there is no protocol with finite runtime using four cards with distinguishable symbols and fixed output encoding, and give a four-card protocol with an expected finite runtime using only random cuts. (b) We provide a general translation of proofs for lower bounds to a bounded model checking framework for automatically finding card- and length-minimal protocols and to give additional confidence in lower bounds. We apply this to validate our method and, as an example, confirm our new
, we show that there is no protocol with finite runtime using four cards with distinguishable symbols and fixed output encoding, and give a four-card protocol with an expected finite runtime using only random cuts. (b) We provide a general translation of proofs for lower bounds to a bounded model checking framework for automatically finding card- and length-minimal protocols and to give additional confidence in lower bounds. We apply this to validate our method and, as an example, confirm our new
 protocol to have a shortest run for protocols using this number of cards.
protocol to have a shortest run for protocols using this number of cards.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
This is known as the “dating problem”.
- 2.
Alice and Bob in the story might, e.g., use \(7\), \(8\), \(9\), \(10\) and a queen with any symbol.
- 3.
As an example, in a Duplicate Bridge tournament, one might prove that all sessions are handed the same cards, eliminating the need of a trusted dealer (no pun intended).
- 4.
Actually, the distribution does not matter, as long as \(\Pr [I = i] > 0\) for all
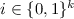 .
. - 5.
In order to keep the execution times still manageable for our experiments, we bound this amount by the (arguably quite reasonable) number 8.
- 6.
The program is available under https://github.com/mi-ki/cardCryptoVerification.
- 7.
In case of the decks being a subset of
 , we may use usual permutation notation. We require that if
, we may use usual permutation notation. We require that if
 maps \(x\) to \(y\), the cardinalities of \(x\) and \(y\) are equal in the deck.
maps \(x\) to \(y\), the cardinalities of \(x\) and \(y\) are equal in the deck.
References
Abe, Y., Hayashi, Y.-I., Mizuki, T., Sone, H.: Five-card AND protocol in committed format using only practical shuffles. In: Emura, K., et al. (ed.) APKC@AsiaCCS 2018 ACM, pp. 3–8 (2018). https://doi.org/10.1145/3197507.3197510
Avalle, M., Pironti, A., Sisto, R.: Formal verification of security protocol implementations: a survey. Formal Asp. Comput. 26(1), 99–123 (2014). https://doi.org/10.1007/s00165-012-0269-9
Blanchet, B.: Security protocol verification: symbolic and computational models. In: Degano, P., Guttman, J.D. (eds.) POST 2012. LNCS, vol. 7215, pp. 3–29. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-28641-4_2
Biere, A., Cimatti, A., Clarke, E., Zhu, Y.: Symbolic model checking without BDDs. In: Cleaveland, W.R. (ed.) TACAS 1999. LNCS, vol. 1579, pp. 193–207. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-49059-0_14
Crépeau, C., Kilian, J.: Discreet solitary games. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 319–330. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48329-2_27
Clarke, E., Kroening, D., Lerda, F.: A tool for checking ANSI-C programs. In: Jensen, K., Podelski, A. (eds.) TACAS 2004. LNCS, vol. 2988, pp. 168–176. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24730-2_15
Boer, B.: More efficient match-making and satisfiability The Five Card Trick. In: Quisquater, J.-J., Vandewalle, J. (eds.) EUROCRYPT 1989. LNCS, vol. 434, pp. 208–217. Springer, Heidelberg (1990). https://doi.org/10.1007/3-540-46885-4_23
Eén, N., Sörensson, N.: An extensible SAT-solver. In: Giunchiglia, E., Tacchella, A. (eds.) SAT 2003. LNCS, vol. 2919, pp. 502–518. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24605-3_37
Fisch, B., Freund, D., Naor, M.: Physical zero-knowledge proofs of physical properties. In: Garay, J.A., Gennaro, R. (eds.) CRYPTO 2014. LNCS, vol. 8617, pp. 313–336. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44381-1_18
Franz, M., Holzer, A., Katzenbeisser, S., Schallhart, C., Veith, H.: CBMC-GC: an ANSI C compiler for secure two-party computations. In: Cohen, A. (ed.) CC 2014. LNCS, vol. 8409, pp. 244–249. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-642-54807-9_15
Glaser, A., Barak, B., Goldston, R.J.: A zero-knowledge protocol for nuclear warhead verification. Nature 510, 497–502 (2014). https://doi.org/10.1038/nature13457
Koch, A.: The Landscape of Optimal Card-based Protocols (2018). Cryptology ePrint Archive, Report 2018/951 https://eprint.iacr.org/2018/951
Koch, A.: Cryptographic protocols from physical assumptions. Ph.D. thesis, Karlsruhe Institute of Technology (KIT) (2019). https://doi.org/10.5445/IR/1000097756
Kastner, J., et al.: The minimum number of cards in practical card-based protocols. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10626, pp. 126–155. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70700-6_5
Koch, A., Walzer, S.: Foundations for Actively Secure Card-based Cryptography (2017). Cryptology ePrint Archive, Report 2017/423 https://eprint.iacr.org/2017/423
Koch, A., Walzer, S., Härtel, K.: Card-based cryptographic protocols using a minimal number of cards. In: Iwata, T., Cheon, J.H. (eds.) ASIACRYPT 2015. LNCS, vol. 9452, pp. 783–807. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48797-6_32
Mizuki, T.: Efficient and secure multiparty computations using a standard deck of playing cards. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 484–499. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_29
Moran, T., Naor, M.: Basing cryptographic protocols on tamper-evident seals. Theor. Comput. Sci. 411(10), 1283–1310 (2010). https://doi.org/10.1016/j.tcs.2009.10.023
Mizuki, T., Sone, H.: Six-card secure AND and four-card secure XOR. In: Deng, X., Hopcroft, J.E., Xue, J. (eds.) FAW 2009. LNCS, vol. 5598, pp. 358–369. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-02270-8_36
Mizuki, T., Shizuya, H.: A formalization of card-based cryptographic protocols via abstract machine. Int. J. Inf. Sec. 13(1), 15–23 (2014). https://doi.org/10.1007/s10207-013-0219-4
Mizuki, T., Shizuya, H.: Computational model of card-based cryptographic protocols and its applications. IEICE Trans. 100(A.1), 3–11 (2017). https://doi.org/10.1587/transfun.E100.A.3
Niemi, V., Renvall, A.: Secure multiparty computations without computers. Theor. Comput. Sci. 191(1–2), 173–183 (1998). https://doi.org/10.1016/S0304-3975(97)00107-2
Niemi, V., Renvall, A.: Solitaire zero-knowledge. Fundam. Inform. 38(1–2), 181–188 (1999). https://doi.org/10.3233/FI-1999-381214
Rastogi, A., Swamy, N., Hicks, M.: \(Wys^\star \): a DSL for verified secure multi-party computations. In: Nielson, F., Sands, D. (eds.) POST 2019. LNCS, vol. 11426, pp. 99–122. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-17138-4_5
Swamy, N., et al.: Dependent types and multimonadic effects in F. In: Bodik, R., Majumdar, R. (eds.) POPL 2016, pp. 256–270. ACM (2016). https://doi.org/10.1145/2837614.2837655
Shinagawa, K., Mizuki, T.: Secure computation of any boolean function based on any deck of cards. In: Chen, Y., Deng, X., Lu, M. (eds.) FAW 2019. LNCS, vol. 11458, pp. 63–75. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-18126-0_6
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix: Further Protocols
Appendix: Further Protocols
This appendix contains the 8-card
 protocol of [M16] (Fig. 9) and a second four-card protocol which uses a number of 4.5 shuffles in expectation, which are, however, non-closed and hence, more impractical to implement, cf. Fig. 10.
protocol of [M16] (Fig. 9) and a second four-card protocol which uses a number of 4.5 shuffles in expectation, which are, however, non-closed and hence, more impractical to implement, cf. Fig. 10.
The eight-card finite-runtime
 protocol of [M16], with
protocol of [M16], with
 and uniform-closed shuffles. Output is in basis \(\{5,6\}\) or \(\{7,8\}\), each with probability 1/2.
and uniform-closed shuffles. Output is in basis \(\{5,6\}\) or \(\{7,8\}\), each with probability 1/2.
Rights and permissions
Copyright information
© 2019 International Association for Cryptologic Research
About this paper
Cite this paper
Koch, A., Schrempp, M., Kirsten, M. (2019). Card-Based Cryptography Meets Formal Verification. In: Galbraith, S., Moriai, S. (eds) Advances in Cryptology – ASIACRYPT 2019. ASIACRYPT 2019. Lecture Notes in Computer Science(), vol 11921. Springer, Cham. https://doi.org/10.1007/978-3-030-34578-5_18
Download citation
DOI: https://doi.org/10.1007/978-3-030-34578-5_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-34577-8
Online ISBN: 978-3-030-34578-5
eBook Packages: Computer ScienceComputer Science (R0)


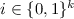 .
. , we may use usual permutation notation. We require that if
, we may use usual permutation notation. We require that if
 maps
maps 

 protocol with deck
protocol with deck
 and uniform shuffles. Note that
and uniform shuffles. Note that
 and
and
 . The output is in one of the bases
. The output is in one of the bases 