Abstract
Murphy, Murky, Mopey, Moody, and Morose decide to write a paper together over the Internet and submit it to the prestigious CRYPTO’19 conference that has the most amazing PC. They encounter a few problems. First, not everyone is online every day: some are lazy and go skiing on Mondays; others cannot use git correctly and they are completely unaware that they are losing messages. Second, a small subset of the co-authors may be secretly plotting to disrupt the project (e.g., because they are writing a competing paper in stealth).
Suppose that each day, sufficiently many honest co-authors are online (and use git correctly); moreover, suppose that messages checked into git on Monday can be correctly received by honest and online co-authors on Tuesday or any future day. Can the honest co-authors successfully finish the paper in a small number of days such that they make the CRYPTO deadline; and perhaps importantly, can all the honest co-authors, including even those who are lazy and those who sometimes use git incorrectly, agree on the final theorem?
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
This is necessary because if a single proposer made a proposal after being elected, the adversary could make the proposer offline in that precise round.
- 2.
Later in our \({\mathsf{VSS}}\) and \({\mathsf{LE}}\) protocols that invoke \({\mathsf{RBC}}\), the fact that the \({\mathsf{RBC}}\) ’s environment
 is admissible is guaranteed by construction.
is admissible is guaranteed by construction. - 3.
Note that (a) implies that if \({{{\mathcal {E}}}}\) outputs \(\bot \), then no honest node will ever output a reconstructed secret.
- 4.
Specifically, when honest nodes running inside
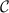 want to send messages, the messages are forwarded to
want to send messages, the messages are forwarded to 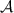 , and
, and 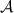 tells
tells  when each honest node receives what message.
when each honest node receives what message. - 5.
For simplicity, we omit writing the randomness consumed by \({\mathsf{PKE}}.\mathsf{Enc}\) which is also part of the witness.
- 6.
Recall that the \({\mathsf{LE}}\) instance deals with its own message signing internally.
References
Gmail and Google Drive are experiencing issues, and naturally people are complaining about it on Twitter. https://www.huffingtonpost.com/entry/gmail-issue_n_3099988
Abraham, I., Devadas, S., Dolev, D., Nayak, K., Ren, L.: Efficient synchronous Byzantine consensus. In: Financial Crypto (2019)
Badrinarayanan, S., Jain, A., Manohar, N., Sahai, A.: Secure MPC: laziness leads to GOD. Cryptology ePrint Archive, Report 2018/580 (2018)
Ben-Or, M., Goldwasser, S., Wigderson, A.: Completeness theorems for non-cryptographic fault-tolerant distributed computation. In: STOC, pp. 1–10 (1988)
Cachin, C., Kursawe, K., Petzold, F., Shoup, V.: Secure and efficient asynchronous broadcast protocols. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 524–541. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44647-8_31
Canetti, R., Rabin, T.: Fast asynchronous Byzantine agreement with optimal resilience. In: STOC, pp. 42–51 (1993)
Castro, M., Liskov, B.: Practical Byzantine fault tolerance. In: OSDI (1999)
Dolev, D., Strong, H.R.: Authenticated algorithms for Byzantine agreement. SIAM J. Comput. SIAMCOMP 12(4), 656–666 (1983)
Dwork, C., Lynch, N., Stockmeyer, L.: Consensus in the presence of partial synchrony. J. ACM 35, 288–323 (1988)
Feldman, P., Micali, S.: An optimal probabilistic protocol for synchronous Byzantine agreement. SIAM J. Comput. 26, 873–933 (1997)
Goldreich, O., Micali, S., Wigderson, A.: How to play ANY mental game. In: ACM Symposium on Theory of Computing (STOC) (1987)
Dov Gordon, S., Liu, F.-H., Shi, E.: Constant-round MPC with fairness and guarantee of output delivery. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015. LNCS, vol. 9216, pp. 63–82. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48000-7_4
Groth, J., Ostrovsky, R.: Cryptography in the multi-string model. In: Menezes, A. (ed.) CRYPTO 2007. LNCS, vol. 4622, pp. 323–341. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74143-5_18
Guo, Y., Pass, R., Shi, E.: Synchronous, with a chance of partition tolerance. https://eprint.iacr.org/2019/179.pdf
Katz, J., Koo, C.-Y.: On expected constant-round protocols for Byzantine agreement. J. Comput. Syst. Sci. 75(2), 91–112 (2009)
Lamport, L.: The part-time parliament. ACM Trans. Comput. Syst. 16, 133–169 (1998)
Lamport, L., Shostak, R., Pease, M.: The Byzantine generals problem. ACM Trans. Program. Lang. Syst. 4, 382–401 (1982)
Micali, S., Vaikuntanathan, V.: Optimal and player-replaceable consensus with an honest majority. MIT CSAIL Technical report, 2017-004 (2017)
Pass, R., Shi, E.: The sleepy model of consensus. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10625, pp. 380–409. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70697-9_14
Pass, R., Shi, E.: Thunderella: blockchains with optimistic instant confirmation. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018. LNCS, vol. 10821, pp. 3–33. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78375-8_1
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 International Association for Cryptologic Research
About this paper
Cite this paper
Guo, Y., Pass, R., Shi, E. (2019). Synchronous, with a Chance of Partition Tolerance. In: Boldyreva, A., Micciancio, D. (eds) Advances in Cryptology – CRYPTO 2019. CRYPTO 2019. Lecture Notes in Computer Science(), vol 11692. Springer, Cham. https://doi.org/10.1007/978-3-030-26948-7_18
Download citation
DOI: https://doi.org/10.1007/978-3-030-26948-7_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-26947-0
Online ISBN: 978-3-030-26948-7
eBook Packages: Computer ScienceComputer Science (R0)


 is admissible is guaranteed by construction.
is admissible is guaranteed by construction.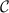 want to send messages, the messages are forwarded to
want to send messages, the messages are forwarded to 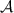 , and
, and 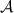 tells
tells  when each honest node receives what message.
when each honest node receives what message.