Abstract
The Internet of Things (IoT) enables increased connectivity between devices; however, this benefit also intrinsically increases cybersecurity risks as cyber attackers are provided with expanded network access and additional digital targets. To address this issue, this paper presents a holistic digital and physical cybersecurity user authentication method based on the Blockchain Random Neural Network. The Blockchain Neural Network connects increasing neurons in a chain configuration providing an additional layer of resilience against Cybersecurity attacks in the IoT. The proposed user access authentication covers holistically its digital access through the seven OSI layers and its physical user identity such as passport before the user is accepted in the IoT network. The user’s identity is kept secret codified in the neural weights, although in case of cybersecurity breach, its physical identity can be mined and the attacker identified, therefore enabling a safe decentralized confidentiality. The validation results show that the addition of the Blockchain Neural Network provides a user access control algorithm with increased cybersecurity resilience and decentralized user access and connectivity.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
In the Internet of Things (IoT), things are objects of the physical world (physical things) that can be sensed, or objects of the information world (virtual things) that can be digitalized; both are capable of being identified and integrated into information and transmitted via sensor and wired or wireless communication networks [1]. The IoT enables comprehensive connectivity between devices; however, this benefit also intrinsically increases cybersecurity risks as cyber attackers are provided with expanded network access and additional digital targets [2,3,4].
Blockchain enables the digitalization of contracts as it provides authentication between parties and information encryption of data that gradually increments while it is processed in a decentralized network such as the IoT [5]. Due to these features, Blockchain has been already applied in Cryptocurrency [6], Smart Contracts [7], Intelligent Transport Systems [8] and Smart Cities [9].
1.1 Research Motivation
To address the increased cybersecurity risk of the IoT, this paper proposes a holistic digital and physical cybersecurity user authentication method based on the Blockchain Random Neural Network [10]. The Blockchain Neural Network connects neurons in a chain configuration providing an additional layer of resilience against Cybersecurity attacks in the IoT. The Cybersecurity and IoT application presented on this paper can be generalized to emulate an Authentication, Authorization and Accounting (AAA) server where user access information is encrypted in the neural weights and stored decentralized servers.
The Blockchain Neural Network solution is equivalent to the Blockchain with the same properties: user authentication, data encryption and decentralization where user access credentials are gradually incremented and learned while travelling or roaming. The Neural Network configuration have analogue biological properties as the Blockchain where neurons are gradually incremented and chained through synapses as variable user access credentials increase; information is stored and codified in decentralized neural networks weights. The main advantage of this research proposal is the biological simplicity of the solution however it suffers high computational cost when the neurons increase.
1.2 Research Proposal
Internet of Things and the Blockchain related work is described in Sect. 2. The proposed user access authentication described in Sect. 3 covers holistically its digital access through the seven OSI layers and its physical user identity such as passport ID before the user is allowed to use IoT network resources. The method forces the user to be physically authenticated before establishing the connection that allows access to the IoT network, therefore cybersecurity is increased by reducing the likelihood of criminal network access. The user’s digital OSI layer identification such as MAC and IP address and physical identification such as biometrics generates the Private Key whereas there is no need for a Public Key, therefore this paper defines a truly decentralized solution with the same Blockchain validation process: mining the input neurons until the neural network solution is found as presented in Sect. 4.
Experimental results in Sect. 5 show that the additional Blockchain neural network provides increased cybersecurity resilience and decentralized confidentiality to user access and connectivity. The main conclusion presented in Sect. 6 proves that the user physical identity is kept secret codified in the neural weights although in case of cybersecurity breach the identity can be mined and the attacker identified by its passport ID or biometrics.
2 Related Work
2.1 Internet of Things
The IoT has provided new services and applications with additional Cybersecurity issues. Lee et al. [11] present the evolution of the IoT technology started from Machine to Machine to connect machines and devices, Interconnections of Things that connect any physical or virtual object and finally Web of Things that enables the collaboration between people and objects. The IoT is formed of three layers, as proposed by Jing et al. [12]: sensor, transportation and application that similar as traditional networks, also have security issues and integration challenges. Roman et al. [13] state that because physical, virtual and user private information is captured, transmitted and shared by the IoT sensors, Cybersecurity aspects on data confidentiality and authentication, access control within the IoT network, identity management, privacy and trust among users and things; the enforcement of security and privacy policies shall be also considered and implemented. Sicari et al. [14] declare that the dynamic IoT is formed by heterogeneous technologies to provide innovative services in various application domains which shall meet flexible security and privacy requirements where traditional security countermeasures cannot be directly applied due the different standards, communication protocols and scalability issues because of the high number of interconnected devices. An important challenge for supporting diverse multimedia applications in the IoT is the security heterogeneity of wired and wireless sensor and transmission networks that requires a balance between flexibility and efficiency, as presented by Zhou et al. [15]. Secure and Safe Internet of Things (SerIoT) was proposed by Gelenbe et al. [16] to improve the information and physical security of different operational IoT applications platforms in a holistic and cross-layered manner. SerIoT covers areas such as mobile telephony, networked health systems, the Internet of Things, Smart Cities, Smart Transportation Systems, Supply Chains and Industrial Informatics [17].
2.2 Neural Networks in Cryptography
Neural Networks have been already applied to Cryptography; Pointcheval [18] presents a linear scheme based on the Perceptron problem or N-P problem suited for smart cards applications. Kinzel et al. [19] train two multilayer neural networks on their mutual output bits with discrete weights to achieve a synchronization that can be applied to secret key exchange over a public channel. Klimov et al. [20] propose three cryptanalytic attacks (genetic, geometric and probabilistic) to the above neural network. Volna et al. [21] apply feed forward neural networks as an encryption and decryption algorithm with a permanently changing key. Yayık et al. [22] present a two-stage cryptography multilayered neural network where the first stage generates neural network-based pseudo random numbers and the second stage, a neural network encrypts information based on the non-linearity of the model. Schmidt [23] et al. present a review of the use of artificial neural networks in cryptography.
2.3 Blockchain in Security
Currently; there is a great research effort in Blockchain Algorithms applied to security applications. Xu et al. [24] propose a punishment scheme based on the action record on the blockchain to suppress the attack motivation of the edge servers and the mobile devices in the edge network. Cha et al. [25] utilize a blockchain network as the underlying communication architecture to construct an ISO/IEC 15408-2 compliant security auditing system. Gai et al. [26] propose a conceptual model for fusing blockchains and cloud computing over three deployment modes: Cloud over Blockchain, Blockchain over Cloud and Mixed Blockchain-Cloud. Gupta et al. [27] propose a Blockchain consensus model for implementing IoT security. Agrawal et al. [28] present a Blockchain mechanism that evaluates legitimate presence of user in valid IoT-Zone continuously without user intervention.
3 Blockchain Neural Network in the Internet of Things
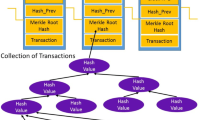
Blockchain [6] is based on cryptographic concepts which can be applied similarly by the use of Neural Networks. Information in the Blockchain is contained in blocks that also include a timestamp, the number of attempts to mine the block and the previous block hash. Decentralized miners then calculate the hash of the current block to validate it. Information contained in the Blockchain consists of transactions which are authenticated by a signature that uses the user private key, transaction origin, destination and value (Fig. 1).
3.1 The Random Neural Network
The proposed Blockchain configuration is based on the Random Neural Network (RNN) [29,30,31] which is a spiking neuronal model that represents the signals transmitted in biological neural networks, where they travel as spikes or impulses, rather than as analogue signal levels. The RNN is a spiking recurrent stochastic model for neural networks where its main analytical properties are the “product form” and the existence of the unique network steady state solution.
3.2 The Random Neural Network with Blockchain Configuration
The Random Neural Network with Blockchain configuration consists of L Input Neurons, M hidden neurons and N output neurons Network (Fig. 2). Information in this model is contained networks weights \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) rather than neurons xL, zM, yN.
-
I = (ΛL, λL), a variable L-dimensional input vector \( {\text{I}} \in \, [ - 1,{ 1}]^{\text{L}} \) represents the pair of excitatory and inhibitory signals entering each input neuron respectively; where scalar L values range 1 < L < ∞;
-
X = (x1, x2, …, xL), a variable L-dimensional vector \( {\text{X}}\, \in \,[0,{ 1}]^{\text{L}} \) represents the input state qL for the neuron L; where scalar L values range 1 < L < ∞;
-
Z = (z1, z2, …, zM), a M-dimensional vector \( {\text{Z}}\, \in \,[0,{ 1}]^{\text{M}} \) that represents the hidden neuron state qM for the neuron M; where scalar M values range 1 < M < ∞;
-
Y = (y1, y2, …, yN), a N-dimensional vector \( {\text{Y}}\, \in \,[0,{ 1}]^{\text{N}} \) that represents the neuron output state qN for the neuron N; where scalar N values range 1 < N < ∞;
-
\( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) is the (L+M+N) x (L+M+N) matrix of weights that represents from the excitatory spike emission from neuron i to neuron j; where \( {\text{i}}\, \in \,\left[ {{\text{x}}_{\text{L}} ,{\text{ z}}_{\text{M}} ,{\text{ y}}_{\text{N}} } \right] \) and \( {\text{j}}\, \in \,\left[ {{\text{x}}_{\text{L}} ,{\text{ z}}_{\text{M}} ,{\text{ y}}_{\text{N}} } \right] \);
-
\( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) is the (L+M+N) x (L+M+N) matrix of weights that represents from the inhibitory spike emission from neuron i to neuron j; where \( {\text{i}}\, \in \,\left[ {{\text{x}}_{\text{L}} ,{\text{ z}}_{\text{M}} ,{\text{ y}}_{\text{N}} } \right] \) and \( {\text{j}}\, \in \,\left[ {{\text{x}}_{\text{L}} ,{\text{ z}}_{\text{M}} ,{\text{ y}}_{\text{N}} } \right] \).
The main concept of the Random Neural Network Blockchain configuration is that the neuron vector sizes, L, M and N are variable instead of fixed. Neurons or blocks are iteratively added where the value of the additional neurons consists on both the value of the additional information and the value of previous neurons therefore forming a neural chain. Information in this model is transmitted in the matrixes of network weighs, \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) rather than in the neurons. The input layer X represents the user’s incremental verification data; the hidden layer Z represents the values of the chain and the output layer Y represents the user Private Key.
4 Cybersecurity and the IoT Blockchain Model
Cybersecurity and the Internet of Things in the Neural Network Blockchain model described in this section is based on the main concepts shown on Fig. 3:
-
Private key, yN;
-
Roaming, R(t) and Verification, V;
-
Neural Chain network and Mining;
-
Decentralized information, \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \).
4.1 Private Key
The private key Y = (y1, y2, …, yN) consists on the user digital AAA authentication credentials that covers the seven layers of the OSI model and physical information such as a passport, biometrics or both. The private key is presented by the user every time its credentials require verification from the accepting roaming node (Table 1).
4.2 Roaming and Verification
Let’s define Roaming and Verification as:
-
Roaming, R(t) = {R(1), R(2), … R(t)} as a variable vector where t is the roaming number;
-
Verification, V = {v1, v2, … vt} as a set of t I-vectors where vo = (eo1, eo2, … eoI) and eo are the I different dimensions for o = 1, 2, … t.
The first Roaming R(1) has associated an input state X = xI which corresponds to v1 and represents the user verification data. The output state Y = yN corresponds to the user Private Key and the hidden layer Z = zM corresponds to the value of the neural chain that will be inserted in the input layer for the next roaming.
The second Roaming R(2) has associated an input state X = xI which corresponds to the user verification data v1 for the first Roaming R(1), the chain (or the value of the hidden layer zM) and the additional user data v2. The output state Y = yN still corresponds the user Private Key and the hidden layer Z = zM corresponds to the value of the neural chain for the next transaction. This process iterates as more user verification data is inserted. The neural chain can be formed of the values of the entire hidden layer neurons, a selection of neurons, or any other combination to avoid the reverse engineering of the user identity from the stored neural weights.
4.3 Neural Chain Network and Mining
The first Roaming R(1) calculates the Random Neural Network neural weights with an Ek < Y for the input data I = (ΛL, λL) and the user private key Y = yN. The calculated network weights \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) are stored in the decentralized network and are retrieved in the mining process. After the first Roaming; the user requires to be validated at each additional Roaming with its private key where its verification data is validated and verification data vt from Roaming R(t) are added to the user.
Verification data is validated or mined by calculating the outputs of the Random Neural Network using the transmitted network weighs, \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) at variable random inputs i, or following any other method. The solution is found or mined when quadratic error function Ek is lesser than determined minimum error or threshold T:
where Ek is the minimum error or threshold, \( {\text{y}}_{\text{n}}^{\prime } \) is the output of the Random Neural Network with mining or random input I and yn is the user Private Key. The mining complexity can be tuned by adjusting Ek. The Random Neural Network with Blockchain configuration is mined when an Input I is found that delivers an output Y with an error Ek lesser than a threshold T for the retrieved user network weights \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \).
When the solution is found, or mined, the user data can be processed; the potential value of the neural hidden layer Z = zM is added to form the Neural Chain as the input of the next transaction where more user data is added. Then, the system calculates the Random Neural Network with gradient descent learning algorithm for the new pair (I, Y) where the new generated network weights \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) are stored in the decentralized network. The more roaming and verification data; the validation or mining process increases on complexity.
4.4 Decentralized Information
The user network weights \( {\text{w}}^{ + } \left( {{\text{j}},{\text{i}}} \right) \) and \( {\text{w}}^{ - } \left( {{\text{j}},{\text{i}}} \right) \) are stored in the decentralized network rather than its data I directly where I is calculated with the mining process. The network weights expand as more verification data is inserted creating an adaptable method. In addition; only the user Data can be extracted when the user presents its biometric key therefore making secure to store information in a decentralized system.
5 Neural Blockchain in Cybersecurity and IoT Validation
This section proposes a practical validation of the Neural Blockchain model in the Internet of Things and Cybersecurity using the network simulator Omnet++ with Java for a network of ten nodes. The three independent experiments will emulate a Bluetooth network with roaming validation of MAC addresses, WLAN network with roaming validation of MAC and IP addresses and LTE Mobile network with a roaming validation of MAC and IP and user Passport (Table 2).
The user is assigned a private key yN that requires validation before is allowed to transmit. When the user travels through the space, the credential private key is validated by the roaming node; the decentralized system retrieves the neural weights associated to the private key; mines the block, adds the node code and stores back the network weights in the decentralized system. This validation considers mining as the selection of random neuron values until Ek < T. When the user roams, the private key is presented and the information of the node (MAC and IP address) vt is added to the neural chain once it is mined. Each bit is codified as a neuron however rather than the binary 0–1, neuron potential is codified as 0.25–0.75 (Fig. 4); this approach removes overfitting in the learning algorithm as neurons only represent binary values.
The simulations are run 100 times for a Bluetooth MAC Network (Table 3). The information shown is the number of iterations the Random Neuron Network with Blockchain configuration requires to achieve an Ek < 1.0E−10; the error Ek, the number of iterations to mine the Blockchain and the number of neurons for each layer; input xL, hidden zM and output yN.
With four neurons in the hidden layer, the number of learning iterations gradually decreases while the number of input neurons increases due the additional information added when roaming between nodes. The results for the mining iteration are not as linear as expected because mining is performed using random values (Fig. 5). Surprisingly; mining is easier in some Roaming stages when it would have been expected harder as the number of neurons increases.
The Blockchain Random Neural Network algorithm shall detect tampering to be effective (Table 4) where Δ represents the number of tampered bits.
The effects of tampering the Neural Block Chain (Fig. 6) is detected by the learning algorithm even when the tampered values only differ in a bit, Δ = 1.0, although this error reduces with an incrementing roaming as the number of neurons increases. Both Bluetooth and WLAN Networks perform similarly.
6 Conclusions
This paper has presented the application of the Blockchain Random Neural Network in Cybersecurity and the IoT where neurons are gradually incremented as user validation data increases through travelling and roaming, although this research can be generalized to any AAA server or Access Control solution. This configuration provides the proposed algorithm the same properties as the Blockchain: security and decentralization with the same validation process: mining the input neurons until the neural network solution is found.
The Random Neural Network in Blockchain configuration has been applied to an IoT AAA server that covers the digital seven layers of the OSI Model and the physical user credentials such as Passport or biometrics. Experimental results show that Blockchain applications can be successfully implemented using neural networks with a gradually increased mining effort, user authentication and data encryption in a decentralized network therefore removing centralized validation mechanisms.
This paper has provided a holistic physical and digital Cybersecurity application in the IoT where access to the network in an area requires prior user physical verification between decentralized parties. User data is encrypted, information is decentralized where attackers can be identified if a criminal attack is delivered.
References
International Telecommunication Union. Overview of the Internet of Things. Y.2060, 1–22 (2012)
Andrea, I., Chrysostomou, C., Hadjichristofi, G.: Internet of Things: security vulnerabilities and challenges. In: IEEE Symposium on Computers and Communication, pp. 180–187 (2015)
Deogirikar, J., Vidhate, A.: Security attacks in IoT: a survey. In: IEEE International Conference on IoT in Social, Mobile, Analytics and Cloud, pp. 32–37 (2017)
Granjal, J., Monteiro, E., Sá Silva, J.: Security for the Internet of Things: a survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 17(3), 1294–1312 (2015)
Huh, S., Cho, S., Kim, S.: Managing IoT devices using Blockchain platform. In: International Conference on Advanced Communication Technology, pp. 464–467 (2017)
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system, pp. 1–9 (2008). Bitcoin.org
Watanabe, H., Fujimura, S., Nakadaira, A., Miyazaki, Y., Akutsu, A., Kishigami, J.: Blockchain contract: securing a Blockchain applied to smart contracts. In: International Conference on Consumer Electronics, pp. 467–468 (2016)
Yuan, Y., Wang, F.-Y.: Towards Blockchain-based intelligent transportation systems. In: International Conference on Intelligent Transportation Systems, pp. 2663–2668 (2016)
Biswas, K., Muthukkumarasamy, V.: Securing smart cities using Blockchain technology. In: International Conference High Performance Computing and Communications/SmartCity/Data Science and Systems, pp. 1392–1393 (2016)
Serrano, W.: The random neural network with a BlockChain configuration in digital documentation. In: Czachórski, T., Gelenbe, E., Grochla, K., Lent, R. (eds.) ISCIS 2018. CCIS, vol. 935, pp. 196–210. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-00840-6_22
Lee, G.M., Crespi, N., Choi, J.K., Boussard, M.: Internet of Things. In: Bertin, E., Crespi, N., Magedanz, T. (eds.) Evolution of Telecommunication Services. LNCS, vol. 7768, pp. 257–282. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-41569-2_13
Jing, Q., Vasilakos, A., Wan, J., Lu, J., Qiu, D.: Security of the Internet of Things: perspectives and challenges. Wireless Netw. 20, 2481–2501 (2014)
Roman, R., Najera, P., Lopez, J.: Securing the Internet of Things. IEEE Comput. Soc. 0018–9162, 51–58 (2011)
Sicari, S., Rizzardi, A., Grieco, L.A., Coen-Porisini, A.: Security, privacy and trust in Internet of Things: the road ahead. Comput. Netw. 76, 146–164 (2015)
Zhou, L., Chao, H.: Multimedia traffic security architecture for the Internet of Things. IEEE Netw. 0890–8044, 35–40 (2011)
Gelenbe, E., Domanska, J., Czàchorski, T., Drosou, A., Tzovaras, D.: Security for Internet of Things: the SerIoT project. In: IEEE International Symposium on Networks, Computers and Communications, pp. 1–5 (2018)
Domańska, J., Nowak, M., Nowak, S., Czachórski, T.: European cybersecurity research and the SerIoT project. In: Czachórski, T., Gelenbe, E., Grochla, K., Lent, R. (eds.) ISCIS 2018. CCIS, vol. 935, pp. 166–173. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-00840-6_19
Pointcheval, D.: Neural networks and their cryptographic applications. Livre des resumes In: Eurocode Institute for Research in Computer Science and Automation, pp. 1–7 (1994)
Kinzel, W., Kanter, I.: Interacting neural networks and cryptography secure exchange of information by synchronization of neural networks. In: Advances in Solid State Physic, vol. 42, 383–391 (2002)
Klimov, A., Mityagin, A., Shamir, A.: Analysis of neural cryptography. In: Zheng, Y. (ed.) ASIACRYPT 2002. LNCS, vol. 2501, pp. 288–298. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-36178-2_18
Volna, E., Kotyrba, M., Kocian, V., Janosek, M.: Cryptography based on the neural network. In: European Conference on Modelling and Simulation, pp. 1–6 (2012)
Yayık, A., Kutlu, Y.: Neural network based cryptography. Int. J. Neural Mass Parallel Comput. Inf. Syst. 24(2), 177–192 (2014)
Schmidt, T., Rahnama, H., Sadeghian, A.: A review of applications of artificial neural networks in cryptosystems. In: World Automation Congress, pp. 1–6 (2008)
Xu, D., Xiao, L., Sun, L., Lei, M.: Game theoretic study on Blockchain based secure edge networks. In: IEEE International Conference on Communications in China, pp. 1–5 (2017)
Cha, S.-C., Yeh, K.-H.: An ISO/IEC 15408-2 compliant security auditing system with Blockchain technology. In: IEEE Conference on Communications and Network Security, pp. 1–2 (2018)
Gai, K., Raymond, K.-K., Zhu, L.: Blockchain-enabled reengineering of cloud datacenters. IEEE Cloud Comput. 5(6), 21–25 (2018)
Gupta, Y., Shorey, R., Kulkarni, D., Tew, J.: The applicability of Blockchain in the Internet of Things. In: IEEE International Conference on Communication Systems & Networks, pp. 561–564 (2018)
Agrawal, R., Verma, P., Sonanis, R., Goel, U., De, A., Anirudh, S., Shekhar, S.: Continuous security in IoT using Blockchain. In: IEEE International Conference on Acoustics, Speech and Signal Processing, pp. 6423–6427 (2018)
Gelenbe, E.: Random neural networks with negative and positive signals and product form solution. Neural Comput. 1, 502–510 (1989)
Gelenbe, E.: Learning in the recurrent random neural network. Neural Comput. 5, 154–164 (1993)
Gelenbe, E.: G-networks with triggered customer movement. J. Appl. Prob. 30, 742–748 (1993)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix
Appendix

Rights and permissions
Copyright information
© 2019 IFIP International Federation for Information Processing
About this paper
Cite this paper
Serrano, W. (2019). The Blockchain Random Neural Network in Cybersecurity and the Internet of Things. In: MacIntyre, J., Maglogiannis, I., Iliadis, L., Pimenidis, E. (eds) Artificial Intelligence Applications and Innovations. AIAI 2019. IFIP Advances in Information and Communication Technology, vol 559. Springer, Cham. https://doi.org/10.1007/978-3-030-19823-7_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-19823-7_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-19822-0
Online ISBN: 978-3-030-19823-7
eBook Packages: Computer ScienceComputer Science (R0)