Abstract
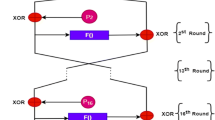
Blowfish, a new secret-key block cipher, is proposed. It is a Feistel network, iterating a simple encryption function 16 times. The block size is 64 bits, and the key can be any length up to 448 bits. Although there is a complex initialization phase required before any encryption can take place, the actual encryption of data is very efficient on large microprocessors.
Chapter PDF
Similar content being viewed by others
Keywords
- Encryption Algorithm
- Block Cipher
- Data Encryption Standard
- Linear Cryptanalysis
- Differential Cryptanalysis
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
References
E. Biham and A. Shamir, Differential Cryptanalysis of the Data Encryption Standard, Springer-Verlag, 1993.
T.W. Cusick and M.C. Wood, “The REDOC-II Cryptosystem,“ Advances in Cryptology-CRYPTO '90 Proceedings, Springer-Verlag, 1991, pp. 545–563.
J. Deamen, R. Govaerts, and J. Vandewalle, “Block Ciphers Based on Modular Arithmetic,” Proceedings of the 3rd Symposium on State and Progress of Research in Cryptography, Rome, Italy, 15–16 Feb 1993, pp. 80–89.
J.-H. Evertse, “Linear Structures in Blockciphers,” Advances in Cryptology-EUROCRPYT '87, Springer-Verlag, 1988, pp. 249–266.
H. Feistel, “Cryptography and Computer Privacy,” Scientific American, v. 228, n. 5, May 73, pp. 15–23.
GOST 28147-89, “Cryptographic Protection for Data Processing Systems,” “Cryptographic Transformation Algorithm,” Government Standard of the U.S.S.R., Inv. No. 3583, UDC 681.325.6:006.354. (in Russian)
X. Lai, J. Massey, and S. Murphy, “Markov Ciphers and Differential Cryptanalysis,” Advances in Cryptology-EUROCRYPT '91 Proceedings, Springer-Verlag, 1991, pp. 17–38.
J.L. Massey and X. Lai, “Device for Converting a Digital Block and the Use Thereof,” International Patent PCT/CH91/00117, 16 May 1991.
J.L. Massey and X. Lai, “Device for the Conversion of a Digital Block and Use of Same,” U.S. Patent 5,214,703, 25 May 1993.
M. Matsui, “Linear Cryptanalysis Method for DES Cipher,” Advances in Cryptology-CRYPTO '93 Proceedings, Springer-Verlag, 1994, in preparation.
R.C. Merkle, “Fast Software Encryption Functions,” Advances in Cryptology-CRYPTO '90 Proceedings, Springer-Verlag, 1991, pp. 476–501.
R.C. Merkle, “Method and Apparatus for Data Encryption,” U.S. Patent 5,003,597, 26 Mar 1991.
S. Miyaguchi, “The FEAL-8 Cryptosystem and Call for Attack,” Advances in Cryptology-CRYPTO '89 Proceedings, Springer-Verlag, 1990, pp. 624–627.
S. Miyaguchi, “Expansion of the FEAL Cipher,” NTT Review, v. 2, n. 6, Nov 1990.
S. Miyaguchi, “The FEAL Cipher Family,” Advances in Cryptology-CRYPTO '90 Proceedings, Springer-Verlag, 1991, pp. 627–638.
National Bureau of Standards, Data Encryption Standard, U.S. Department of Commerce, FIPS Publication 46, Jan 1977.
National Institute of Standards and Technology, “Clipper Chip Technology,” 30 Apr 1993.
RSA Laboratories, Answers to Frequently Asked Questions About Today's Cryptography, Revision 2.0, RSA Data Security Inc., 5 Oct 1993.
B. Schneier, “Data Guardians,” MacWorld, Feb 1993, 145–151.
B. Schneier, Applied Cryptography, John Wiley & Sons, New York, 1994.
J.L Smith, The Design of Lucifer, A Cryptographic Device for Data Communication, RC 3326, White Plains: IBM Research.
M.J. Weiner, “Efficient DES Key Search,” Advances in Cryptology-CRYPTO '93 Proceedings, Springer-Verlag, in preparation.
M.C. Wood, “Method of Cryptographically Transforming Electronic Digital Data from One Form to Another,” U.S. Patent 5,003,596, 26 Mar 1991.
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 1994 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Schneier, B. (1994). Description of a new variable-length key, 64-bit block cipher (Blowfish). In: Anderson, R. (eds) Fast Software Encryption. FSE 1993. Lecture Notes in Computer Science, vol 809. Springer, Berlin, Heidelberg. https://doi.org/10.1007/3-540-58108-1_24
Download citation
DOI: https://doi.org/10.1007/3-540-58108-1_24
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-58108-6
Online ISBN: 978-3-540-48456-1
eBook Packages: Springer Book Archive