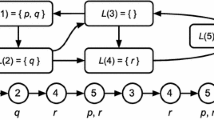
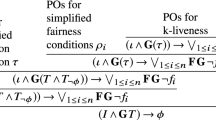
Abstract
We formalize a notion of witnesses for satisfaction of linear temporal logic specifications by infinite state programs. We show how such witnesses may be constructed via predicate abstraction, and validated by generating verification conditions and proving them. We propose the use of SAT-based theorem provers and resolution proofs in proving these verification conditions. In addition to yielding extremely compact proofs, a SAT-based approach overcomes several limitations of conventional theorem provers when applied to the verification of programs written in real-life programming languages. We also formalize a notion of witnesses of simulation conformance between infinite state programs and finite state machine specifications. We present algorithms to construct simulation witnesses of minimal size by solving pseudo-Boolean constraints. We present experimental results on several non-trivial benchmarks which suggest that a SAT-based approach can yield extremely compact proofs, in some cases by a factor of over 105, when compared to existing non-SAT-based theorem provers.
Chapter PDF
Similar content being viewed by others
Keywords
- Ranking Function
- Linear Temporal Logic
- Label Transition System
- Simulation Relation
- Strongly Connect Component
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
References
Aloul, F., Ramani, A., Markov, I., Sakallah, K.: PBS: A backtrack search pseudo Boolean solver. In: Proc. of SAT (2002)
Appel, A.: Foundational proof-carrying code. In: Proc. of LICS (2001)
Balaban, I., Pnueli, A., Zuck, L.D.: Shape analysis by predicate abstraction. In: Cousot, R. (ed.) VMCAI 2005. LNCS, vol. 3385, pp. 164–180. Springer, Heidelberg (2005)
Ball, T., Rajamani, S.: Automatically validating temporal safety properties of interfaces. In: Proc. of SPIN (2001)
Bernard, A., Lee, P.: Temporal logic for proof-carrying code. In: Voronkov, A. (ed.) CADE 2002. LNCS (LNAI), vol. 2392, p. 31. Springer, Heidelberg (2002)
Chaki, S.: SAT-based Software Certification. Technical report CMU/SEI-2006-TN-004, Carnegie Mellon Software Engineering Institute, Pittsburgh, USA (2006)
Chaki, S., Clarke, E., Groce, A., Jha, S., Veith, H.: Modular verification of software components in C. IEEE TSE 30(6), 388–402 (2004)
Chaki, S., Clarke, E., Jha, S., Veith, H.: An iterative framework for simulation conformance. Journal of Logic and Computation 15(4) (2005)
Chaki, S., Clarke, E.M., Ouaknine, J., Sharygina, N., Sinha, N.: State/Event-based software model checking. In: Boiten, E.A., Derrick, J., Smith, G.P. (eds.) IFM 2004. LNCS, vol. 2999, pp. 128–147. Springer, Heidelberg (2004)
Chaki, S., Ivers, J., Sharygina, N., Wallnau, K.: The comFoRT reasoning framework. In: Etessami, K., Rajamani, S.K. (eds.) CAV 2005. LNCS, vol. 3576, pp. 164–169. Springer, Heidelberg (2005)
Clarke, E., Emerson, E.A.: Synthesis of synchronization skeletons for branching time temporal logic. In: Proceedings of WLP (1981)
Clarke, E., Grumberg, O., Jha, S., Lu, Y., Veith, H.: Counterexample-guided abstraction refinement for symbolic model checking. J. ACM 50(5) (2003)
Clarke, E., Grumberg, O., Peled, D.: Model Checking. MIT Press, Cambridge (2000)
Clarke, E., Kröning, D., Lerda, F.: A tool for checking ANSI-C programs. In: Jensen, K., Podelski, A. (eds.) TACAS 2004. LNCS, vol. 2988, pp. 168–176. Springer, Heidelberg (2004)
Cook, B., Kroening, D., Sharygina, N.: Symbolic model checking for asynchronous boolean programs. In: Proc. of SPIN (2005)
Cook, B., Podelski, A., Rybalchenko, A.: Abstraction refinement for termination. In: Proc. of SAS (2005)
Graf, S., Saïdi, H.: Construction of abstract state graphs with PVS. In: Grumberg, O. (ed.) CAV 1997. LNCS, vol. 1254. Springer, Heidelberg (1997)
Hamid, N., Shao, Z., Trifonov, V., Monnier, S., Ni, Z.: A syntactic approach to foundational proof-carrying code. In: Proc. of LICS (2002)
Henzinger, T.A., Jhala, R., Majumdar, R., Necula, G.C., Sutre, G., Weimer, W.: Temporal-safety proofs for systems code. In: Brinksma, E., Larsen, K.G. (eds.) CAV 2002. LNCS, vol. 2404, p. 526. Springer, Heidelberg (2002)
Henzinger, T., Jhala, R., Majumdar, R., Sutre, G.: Lazy abstraction. In: POPL 2002 (2002)
Kroening, D.: Application specific higher order logic theorem proving. In: VERIFY 2002 (2002)
Kupferman, O., Y. Vardi, M.: From complementation to certification. In: Jensen, K., Podelski, A. (eds.) TACAS 2004. LNCS, vol. 2988, pp. 591–606. Springer, Heidelberg (2004)
Magill, S., Nanevski, A., Clarke, E., Lee, P.: Simulation-based safety proofs by MAGIC (in preparation)
Michael, N., Appel, A.: Machine instruction syntax and semantics in higher order logic. In: McAllester, D. (ed.) CADE 2000. LNCS, vol. 1831, p. 519. Springer, Heidelberg (2000)
Moskewicz, M., Madigan, C., Zhao, Y., Zhang, L., Malik, S.: Chaff: Engineering an efficient SAT solver. In: Proc. of DAC (2001)
Namjoshi, K.S.: Certifying model checkers. In: Berry, G., Comon, H., Finkel, A. (eds.) CAV 2001. LNCS, vol. 2102, p. 2. Springer, Heidelberg (2001)
Namjoshi, K.S.: Lifting temporal proofs through abstractions. In: Zuck, L.D., Attie, P.C., Cortesi, A., Mukhopadhyay, S. (eds.) VMCAI 2003. LNCS, vol. 2575, pp. 174–188. Springer, Heidelberg (2002)
Necula, G.: Proof-carrying code. In: POPL 1997 (1997)
Necula, G., Lee, P.: Efficient representation and validation of proofs. In: LICS 1998 (1998)
Necula, G., Lee, P.: Safe kernel extensions without run-time checking. In: OSDI 1996 (1996)
Necula, G., Lee, P.: Safe, untrusted agents using proof-carrying code. In: Proc. of Mobile Agents and Security (1998)
Necula, G., Rahul, S.P.: Oracle-based checking of untrusted software. In: POPL 2001 (2001)
Nelson, G.: Techniques for Program Verification. PhD thesis (1980)
Zhang, L., Malik, S.: Validating sat solvers using an independent resolutionbased checker: Practical implementations and other applications. In: DATE 2003 (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2006 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Chaki, S. (2006). SAT-Based Software Certification. In: Hermanns, H., Palsberg, J. (eds) Tools and Algorithms for the Construction and Analysis of Systems. TACAS 2006. Lecture Notes in Computer Science, vol 3920. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11691372_10
Download citation
DOI: https://doi.org/10.1007/11691372_10
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-33056-1
Online ISBN: 978-3-540-33057-8
eBook Packages: Computer ScienceComputer Science (R0)