Abstract
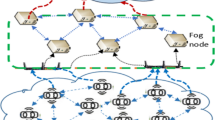
Military tasks constitute the most important and significant applications of Wireless sensor networks (WSNs). In military, Sensor node deployment increases activities, efficient operation, saves loss of life, and protects national sovereignty. Usually, the main difficulties in military missions are energy consumption and security in the network. Another major security issues are hacking or masquerade attack. To overcome the limitations, the proposed method modified DBSCAN with OSPREY optimization Algorithm (OOA) using hybrid classifier Long Short-Term Memory (LSTM) with Extreme Gradient Boosting (XGBOOST) to detect attack types in the WSN military sector for enhancing security. First, nodes are deployed and modified DBSCAN algorithm is used to cluster the nodes to reduce energy consumption. To select the cluster head optimally by using the OSPREY optimization Algorithm (OOA) based on small distance and high energy for transfer data between the base station and nodes. Hybrid LSTM-XGBOOST classifier utilized to learn the parameter and predict the four assault types such as scheduling, flooding, blackhole and grayhole assault. Classification and network metrics including Packet Delivery Ratio (PDR), Throughput, Average Residual Energy (ARE), Packet Loss Ratio (PLR), Accuracy and F1_score are used to evaluate the performance of the model. Performance results show that PDR of 94.12%, 3.2 Mbps throughput at 100 nodes, ARE of 8.94J, PLR of 5.88%, accuracy of 96.14%, and F1_score of 95.04% are achieved. Hence, the designed model for assault prediction types in WSN based on modified DBSCAN clustering with a hybrid classifier yields better results.





















Similar content being viewed by others
REFERENCES
Rajakumaran, G., Venkataraman, N., and Mukkamala, R.R., Denial of service attack prediction using gradient descent algorithm, SN Comput. Sci., 2020, vol. 1, pp. 1–8.
Preethi, R. and Anbuselvi, R., Energy Efficient Cluster Based Technique for Resource Allocation in MANET, International Journal of Science and Research (IJSR), 2015, vol. 6, no. 6, pp. 1951–1957.
Preethi, R. and Anbuselvi, R., A Game Theory Approach for Efficient Node Clustering Based on Unstable Ranging Transmission in MANET, International Journal of Engineering & Technology, 2018, vol. 7, no. 2.22, pp. 21–26.
Preethi, R. and Sughasiny, M., Pbgtr: Price based game theory routing for minimum cost routing path in manet. In 2018 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC) IEEE, 2018, pp. 469–474.
Preethi, R. and Sughasiny, M., AKCSS: An Asymmetric Key Cryptography Based on Secret Sharing in Mobile. In Intelligent Systems Design and Applications: 18th International Conference on Intelligent Systems Design and Applications (ISDA 2018) held in Vellore, India, 2018, vol. 940, p. 73.
Preethi, R. and Sughasiny, M., RBMD: Reward Based Malicious Detection in Mobile Ad hoc Network, International Journal of Scientific & Engineering Research, 2018, vol. 9, no. 9, pp. 2057–2061.
Anand, C. and Vasuki, N., Trust based DoS attack detection in wireless sensor networks for reliable data transmission, Wireless Pers. Communs., 2021, vol. 121, no. 4, pp. 2911–2926.
Alsulaiman, L. and Al-Ahmadi, S., Performance evaluation of machine learning techniques for DOS detection in wireless sensor network, arXiv preprint arXiv:2104.01963, 2021.
Salmi, S. and Oughdir, L., Cnn-lstm based approach for dos attacks detection in wireless sensor networks, Int. J. Adv. Comput. Sci. Appl., 2022, vol. 13, no. 4.
Hemanand, D., Reddy, G.V., Babu, S.S., Balmuri, K.R., Chitra, T., and Gopalakrishnan, S., An intelligent intrusion detection and classification system using CSGO-LSVM model for wireless sensor networks (WSNs), Int. J. Intell. Syst. Appl. Eng., 2022, vol. 10, no. 3, pp. 285–293.
Rezvi, M.A., Moontaha, S., Trisha, K.A., Cynthia, S.T., and Ripon, S., Data mining approach to analyzing intrusion detection of wireless sensor network, Indones. J. Electr. Eng. Comput. Sci., 2021, vol. 21, no. 1, pp. 516–523.
Tan, X., Su, S., Huang, Z., Guo, X., Zuo, Z., Sun, X., and Li, L., Wireless sensor networks intrusion detection based on SMOTE and the random forest algorithm, Sensors, 2019, vol. 19, no. 1, p. 203.
Alruhaily, N.M. and Ibrahim, D.M., A multi-layer machine learning-based intrusion detection system for wireless sensor networks, Int. J. Adv. Comput. Sci. Appl., 2021, vol. 12, no. 4, pp. 281–288.
Srinivas, D., Adaptive density-based localization algorithm using particle swarm optimization and DBSCAN clustering approach, Turk. J. Comput. Math. Educ. (TURCOMAT), 2021, vol. 12, no. 11, pp. 5053–5062.
Liu, Y. and Wu, Y., Employ DBSCAN and neighbor voting to screen selective forwarding attack under variable environment in event-driven wireless sensor networks, IEEE Access, 2021, vol. 9, pp. 77090–77105.
Dehghani, M. and Trojovský, P., Osprey optimization algorithm: A new bio-inspired metaheuristic algorithm for solving engineering optimization problems, Front. Mech. Eng., 2023, vol. 8, p. 1126450.
Turkoglu, M., Hanbay, D., and Sengur, A., Multi-model LSTM-based convolutional neural networks for detection of apple diseases and pests, J. Ambient Intell. Humanized Comput., 2019, pp. 1–11.
Gouveia, A. and Correia, M., Network intrusion detection with XGBoost, Recent Advances in Security, Privacy, and Trust for Internet of Things (IoT) and Cyber-Physical Systems (CPS), 2020, vol. 137.
KIRAN, Kaggle, 2019. https://www.kaggle.com/datasets/kiranmahesh/nslkdd?select=kdd. Accessed October 16, 2023.
Funding
This work was supported by ongoing institutional funding. No additional grants to carry out or direct this particular research were obtained.
Author information
Authors and Affiliations
Contributions
The author claims the major contribution of the paper including formulation, analysis and editing and provides guidance to verify the analysis result and manuscript editing.
Corresponding author
Ethics declarations
CONFLICT OF INTEREST
The author of this work declares that he has no conflicts of interest.
CODE AVAILABILITY
Not applicable.
Additional information
Publisher’s Note.
Allerton Press remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
About this article
Cite this article
Preethi, R. Assault Type Detection in WSN Based on Modified DBSCAN with Osprey Optimization Using Hybrid Classifier LSTM with XGBOOST for Military Sector. Opt. Mem. Neural Networks 33, 53–71 (2024). https://doi.org/10.3103/S1060992X24010089
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S1060992X24010089