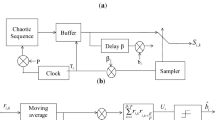
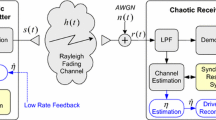
Abstract
There has been a growing interest in the use of chaotic techniques for enabling secure communication in recent years. This need has been motivated by the emergence of a number of wireless services which require the channel to provide very low bit error rates (BER) along with information security. As more and more information is transacted over wireless media, there has been increasing criminal activity directed against such systems. This paper investigates the feasibility of using chaotic communications over Multiple-Input-Multiple-Output (MIMO) channels. We have studied the performance of differential chaos shift keying (DCSK) with 2×2 Alamouti scheme and 2×1 Alamouti scheme for different chaotic maps over additive white Gaussian noise (AWGN) and channels disturbed by Rayleigh fading. Both the inherently wideband DCSK modulation and the space-time block code (STBC) are techniques that can mitigate the effect of multipath fading. The use of these schemes allows us to enhance security without degrading the BER performance for Rayleigh fading channels. We have employed an exact method to analyze the performances of DCSK communication system over fading channel. Our simulations indicate that the combination of the STC and tent map provides the best BER performance in addition to security when compared to the choice of other maps. Hence, this study shows that the use of these schemes can allow the user to enhance security without degrading the BER performance while communicating over these channels.
Similar content being viewed by others
References
D. R. Frey, “Chaotic digital encoding: An approach to secure communication,” IEEE Trans. Circuits Syst. II: Analog Digital Signal Process. 40, No. 10, 660 (1993). DOI: 10.1109/82.246168.
M. Itoh, H. Murakami, L. O. Chua, “Secure communication systems via Yamakawa’s chaotic chips and Chua’s circuits,” in Proc. of IEEE Third World Congress on Computational Intelligence “Fuzzy Systems,” 26–29 Jun. 1994, Orlando, FL (Orlando, 1994), Vol. 2, pp. 1293–1296. DOI: 10.1109/FUZZY.1994.343908.
Hong Zhou, Xie-Ting Ling, Jun Yu, “Secure communication via one-dimensional chaotic inverse systems,” in Proc. of IEEE Int. Symp. on Circuits and Systems, ISCAS’97, 9–12 Jun. 1997, Hong Kong (1997), Vol. 2, pp. 1029–1032. DOI: 10.1109/ISCAS.1997.621911.
G. Kaddoum, Mai Vu, Francois Gagnon, “Performance analysis of differential chaotic shift keying communications in MIMO systems,” in Proc. of IEEE Int. Symp. on Circuits and Systems, ISCAS, 15–18 May 2011, Rio de Janeiro, Brazil (Rio de Janeiro, 2011), pp. 1580–1583. DOI: 10.1109/ISCAS.2011.5937879.
Huanfei Ma and Haibin Kaan, “Space-time coding and processing with differential chaos shift keying scheme,” in Proc. of IEEE Int. Conf. on Communications, ICC’09, 14–18 June 2009, Dresden, Germany (Dresden, 2009), pp. 1–5. DOI: 10.1109/ICC.2009.5199469.
F. C. M. Lau, C. K. Tse, Ye. Ming, S. F. Hau, “Coexistence of chaos-based and conventional digital communication systems of equal bit rate,” IEEE Trans. Circuits Syst. 51, No. 2, 391 (2004). DOI: 10.1109/TCSI.2003.822398.
M. A. Ben Farah, A. Kachouri, M. Samet, “Design of secure digital communication systems using DCSK chaotic modulation,” in Proc. of IEEE Int. Conf. on Design and Test of Integrated Systems in Nanoscale Technology, DTIS, 5–7 Sept. 2006, Tunis (2006), pp. 200–204. DOI: 10.1109/DTIS.2006.1708656.
Yuu-Seng Lau and Z. M. Hussain, “A new approach in chaos shift keying for secure communication,” in Proc. of Third IEEE Int. Conf. on Information Technology and Applications, ICITA 2005, 4–7 July 2005 (2005), Vol. 2, pp. 630–633. DOI: 10.1109/ICITA.2005.30.
Jaejin Lee, Chungyong Lee, D. B. Williams, “Secure communication using chaos,” in Proc. of IEEE Global Telecommunication Conf. GLOBECOM’95, 14–16 Nov. 1995 (1995), Vol. 2, pp. 1183–1187. DOI: 10.1109/GLOCOM.1995.502590.
Zhingguo Li, Kun Li, Changyun Wen, Yeng Chai Soh, “A new chaotic communication system,” IEEE Trans. Commun. 51, No. 8, 1306 (2003). DOI: 10.1109/TCOMM.2003.815058.
Guoping Tang, Xiaofeng Liao, Di Xiao, Chuandong Li, “A secure communication scheme based on symbolic dynamics,” in Proc. of IEEE Int. Conf. on Communications, Circuits and Systems, ICCCAS 2004, 27–29 June 2004 (2004), Vol. 1, pp. 13–17. DOI: 10.1109/ICCCAS.2004.1345929.
Yuu-Seng Lau, Kevin H. Lin, Z. M. Hussain, “Space-time encoded secure chaos communications with transmit beamforming,” in Proc. of IEEE Region 10, TENCON, 21–24 Nov. 2005, Melbourne, Qld. (2005), pp. 1–5. DOI: 10.1109/TENCON.2005.301120.
G. Kaddoum, Mai Vu, F. Gagnon, “On the performance of chaos shift keying in MIMO communications systems,” in Proc. of IEEE Wireless Communication and Networking Conf. WCNC, 28–31 March 2011, Cancun, Quintana Roo (Cancun, 2011), pp. 1432–1437. DOI: 10.1109/WCNC.2011.5779370.
Huanfei Ma and Haibin Kan, “Space-time coding and processing with differential chaos shift keying scheme,” in Proc. of IEEE Int. Conf. on Communications, ICC’09, 14–18 June 2009, Dresden, Germany (Dresden, 2009), pp. 1–5. DOI: 10.1109/ICC.2009.5199469.
Georges Kaddoum, Francois Gagnon, Pascal Charge, Daniel Roviras, “A generalized BER prediction method for differential chaos shift keying system through different communication channels,” Wireless Personal Commun. 64, No. 2, 425 (2012). DOI: 10.1007/s11277-010-0207-1.
G. Kaddoum, P. Charge, D. Roviras, D. Fournier-Prunaret, “A methodology for bit error rate prediction in chaos-based communication systems,” Circuits, Syst. Signal Process. 28, No. 6, 925 (2009). DOI: 10.1007/s00034-009-9124-5.
W. M. Tam, F. C. M. Lau, C. K. Tse, A. J. Lawrance, “Exact analytical bit error rates for multiple access chaos-based communication systems,” IEEE Trans. Circuits Syst. 51, No. 9, 473 (Sept. 2004). DOI: 10.1109/TCSII.2004.832773.
A. Dornbusch and J. P. de Gyvez, “Chaotic generation of PN sequences: A VLSI implementation,” in Proc. of IEEE Int. Symp. on Circuits and Systems, ISCAS’99, 1999, Orlando, FL (1999), Vol. 5, pp. 454–457. DOI: 10.1109/ISCAS.1999.777607.
Abir Awad, Safwan El Assad, Wang Qianxue, Calin Vladeanu, Bassem Bakhache, “Comparative study of 1-D chaotic generators for digital data encryption,” IAENG Int. J. Computer Sci. 35, No. 4, 1 (Dec. 2008).
P. Stavroulakis, Chaos Applications in Telecommunications (Taylor & Francis Group, 2006).
Zhibo Zhou, Tong Zhou, Jinxiang Wang, “Exact BER analysis of differential chaos shift keying communication system in fading channels,” in Proc. of 4th IEEE Int. Conf. on Wireless Communication, Networking and Mobile Computing, WiCOM’08, 12–14 Oct. 2008, Dalian, China (Dalian, 2008), pp. 1–4. DOI: 10.1109/WiCom.2008.516.
Author information
Authors and Affiliations
Additional information
Original Russian Text © L.F. Abdulameer, J.D. Jokhakar, U. Sripati, M. Kulkarni, 2013, published in Izv. Vyssh. Uchebn. Zaved., Radioelektron., 2013, Vol. 56, No. 10, pp. 28–41.
About this article
Cite this article
Abdulameer, L.F., Jokhakar, J.D., Sripati, U. et al. BER performance enhancement for secure wireless communication systems based on DCSK-MIMO techniques under Rayleigh fading channel. Radioelectron.Commun.Syst. 56, 481–492 (2013). https://doi.org/10.3103/S0735272713100038
Revised:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0735272713100038