Abstract
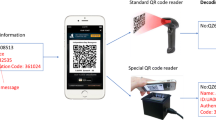
Quick response (QR) code has become one of the more popular two-dimensional barcodes because of its greater data capacity and higher damage resistance. The barcode scanners can easily extract the information hidden in the QR code while scanning the data modules. However, some sensitive data directly stored in QR codes are insecure in real-world QR applications, such as the e-ticket and e-coupon. To protect the sensitive data, this paper explores the characteristics of QR barcodes to design a secret hiding mechanism for the QR barcode with a higher payload compared to the past ones. For a normal scanner, a browser can only reveal the formal information from the marked QR code. The authorized user/scanner can further reveal the sensitive data from the marked QR tag. The experiments demonstrate a satisfactory secret payload and the feasibility of the proposed scheme.
Similar content being viewed by others
1 Introduction
Many multimedia applications, such as labeled street view images [1], video streaming [2], and consumer photos [3], add quick response (QR) codes to help readers to easily distribute and understand some related information. The QR code is a type of trademark barcode with a machine-readable optical label, in which the information of the barcode can be quickly extracted through scanning the label. Recently, the QR code is one of the most popular two-dimensional (2-D) barcodes that consists of black and white square modules [4–6]. With the wide range of matrix modules, the QR code can carry larger data content than the conventional one-dimensional (1-D) barcodes. There are 40 QR versions in the QR code standard [6]. The higher version of the QR code can carry a larger data capacity. For example, the data capacity is 208 modules for QR version 1 and is 29,648 modules for QR version 40. Moreover, the error correction capability of the QR code allows barcode readers to restore the QR data without any loss if the QR code becomes dirty or damaged [7].
With barcode readers, one can obtain the QR data easily and effectively. Nevertheless, the appearance of the confidential data in a QR code raises a security issue. In general, the common approach to protect the confidential data of the QR code is using the back-end database [8]. The QR data only provides the database website link, such as uniform resource locator (URL). An authorized user can login to the database via linking the URL and then achieves the confidential data. Such a mechanism, however, needs to maintain the database, the access control, and the online requirement. The online decoded, moreover, may expose the risks of database attacks.
Recently, the conventional digital secret hiding and watermarking techniques [9–11] are usually adopted to conceal the secret into the host image. The processes embed the secret into the pixels/coefficients and into the spatial/frequency domains of the host image. Such embedding algorithms, unfortunately, are unsuitable for the QR tag [9–15] due to the fact that the embedding schemes treat the QR tag as an image, in which the secret is concealed in the pixel or coefficients of the QR image without considering the characteristics of the QR modules. The decoding processes need further image processing, such as pixel and frequency transformation. The secret is incapable of being extracted by the barcode reader directly. The decoding of the schemes [9–15] limits the real-world applications of QR barcode readers.
To protect the confidential secret of the QR tag and the decoding by a barcode reader directly, we designed a secret QR hiding approach based on the property of the QR standard [5, 16] in this article. The proposed scheme can enhance the embeddable secret capacity of the QR tag than that of the related scheme [16]. To increase the hiding payload, this paper considers the characteristics of QR codes to propose a novel data hiding method, which is an extended version of [17]. The proposed scheme can convey a higher payload of the sensitive data for QR tags by modifying the data modules directly. The QR data of the generated marked QR tag, especially, is readable. That is, one can use the barcode reader to exhibit the QR data, such as the URL. The ability of exhibiting the QR data from the marked QR tag can reduce the suspicions of attackers and intruders. Only the authorized user can further extract the confidential secret from the same generated QR tag via the barcode reader. The designed approach can satisfy the essentials of steganography, secret protection, and feasibility for low-power barcode readers and mobile devices.
This paper is organized as follows: related works are briefly described in Section 2. The proposed secret hiding scheme for the QR code is presented in Section 3. The experimental results are shown in Section 4. Finally, conclusions are made in Section 5.
2 Related works
The concepts of the QR barcode [5] and the least significant bit (LSB) matching revisited embedding scheme [18] are briefly introduced in this section.
2.1 QR barcode
According to the QR standard [5], there are 40 versions of the QR tag, and each has four error correction levels, L, M, Q, and H. Table 1 lists the error correction capability of the QR tag. The higher level of error correction represents the QR tag which has the ability to resist larger damage. For instance, level L means that the barcode reader can successfully restore the QR data while the distortion of the QR tag is limited within 7%. Level H indicates that the QR data is decodable by the barcode reader while 30% of the QR tag is damaged.
In general, the binary QR data, such as the URL, is decoded into the corresponding white and black modules. The white and black modules are equal to the binary values 0 and 1, respectively. To achieve the recover ability of QR data, the error correction codewords corresponding to the QR data can be computed [5]. The gray area in Fig. 1 displays the data and error correction codewords of the QR tag. Here, a codeword refers to eight modules.
Specifically, the QR data with a larger capacity is normally divided into non-overlapping data blocks according to its QR version to withstand damage without loss. The error correction codewords corresponding to each QR data block thereby can be generated individually. For example, the block number is 1 for QR versions 3-L and 3-M, and the block numbers are 2 for QR versions 3-Q and 3-H. That is, the higher QR version and error correction level, the larger number of QR data blocks.
2.2 LSB matching revisited embedding scheme [18]
The image is divided into several groups, and each group is the size of 2 pixels (i.e., p i and p i + 1). Two secret bits, s i and s i+ 1, could be hidden in a group. The two secret bits can be extracted according to Eqs. (1) and (2), respectively, where LSB(x) extracts the last significant bit of the x value.
If the first secret bit (or the second bit) is not equal to the value of f 1(·) function (or the value of f 2(·) function), the pixel p i must be updated with an embedding algorithm complying with Eqs. (3) and (4).

3 The proposed scheme
The steganography scheme for the QR tag is spilt into a secret embedding procedure and extracting procedure, and their corresponding flowcharts are shown in Figs. 2 and 3, respectively.
3.1 Secret embedding procedure
Given an original QR tag and the confidential secret S, the proposed scheme embeds the secret into the data codewords of the QR tag and retains the remaining unmodified QR regions. The steps are listed below:
-
Step 1.
The tolerant capacity, tc, of the secret is defined as
$$ t c=\left\lfloor \frac{ecc}{2}\right\rfloor \times 8. $$(5)The value of tc is determined according to the QR version and the error correction level of the given QR tag. Here, the value of ecc is the number of error correction codewords of the QR tag.
-
Step 2.
The QR data codewords is divided into several pairs, in which two data modules are a pair, and the black data module and the white one are as values 1 and 0, respectively. The pair can be presented as the digit d i , where d i is the range of 0 and 3, and be denoted as \( {\left({d}_i^1\kern1em {d}_i^2\right)}_2 \). Put the digit d i into a pool.
-
Step 3.
A secret key, K, is used to randomly choose two digit pairs, denoted as d x and d y from the pool, where x ≠ y.
-
Step 4.
Four secret bits (denoted as s 1, s 2, s 3, and s 4) are embedded into the digit pairs d x and d y with Eq. (6). Here, the |w| function is to get the absolute value of w.
$$ \begin{array}{l}{d}_x^1={s}_{1,}\hfill \\ {}{d}_x^2={s}_{2,}\hfill \\ {}{d}_y^2={s}_{4,}\hfill \\ {}{d}_y^1=\left|{s}_3-\left\lfloor {d}_x/2\right\rfloor \right|.\hfill \end{array} $$(6) -
Step 5.
Update the corresponding data modules in the QR codes according to the values of \( {d}_x^1 \), \( {d}_x^2 \), \( {d}_y^1 \), and \( {d}_y^2 \) after secret embedding. If the value is 1, the data module is a black one; otherwise, it is a white one.
-
Step 6.
Accumulate the number of the changed data module. That is, if no data modules are changed, keep the tc value. If the module is changed from the black module to the white one or white one to black one, the tc is updated as tc–1. The total changed data module is counted to reduce the tc value.
-
Step 7.
Remove the digit from the pool.
-
Step 8.
Repeat steps 3 to 7 until the tc value is identical to 0 or the pool is empty.
-
Step 9.
After secret embedding to the QR modules, the proposed scheme produces the marked QR tag.
3.2 Secret extracting procedure
During the secret extracting process, the authorized receiver can extract the secret S from the marked QR code with the secret key K. The detailed extracting steps are listed as follows:
-
Step 1.
Steps 1 to 3 of the secret embedding procedure are applied to this step.
-
Step 2.
A secret key is used to select the digit pairs d x and d y from the pool.
-
Step 3.
The secrets can be extracted by using Eq. (7).
$$ \begin{array}{l}{s}_1={d}_x^1,\hfill \\ {}{s}_2={d}_x^2,\hfill \\ {}{s}_4={d}_y^2,\hfill \\ {}{s}_3= f\left({d}_{x,}{d}_y\right).\hfill \end{array} $$(7) -
Step 4.
Find the corresponding data modules of the digit pairs d x and d y and then check each of the four data modules. The corresponding QR code can be recovered by using the error correction. If a module is flipped from the black module to be a white one or from a white one to be black one after the error correction, let tc=tc–1. For example, if four data modules are all flipped, tc=tc–4.
-
Step 5.
Remove the digit pairs d x and d y from the pool.
-
Step 6.
Repeat steps 2 to 5 until tc is equal to 0.
The secret extracting procedure is with a low computation load. The proposed method is feasible to be applied to QR applications. The marked QR codes can be recovered by error correction. Thus, barcode readers can scan the corrected QR codes to extract the information for the users.
4 Experimental results
In a simulation environment, the proposed secret hiding scheme is developed by the ZXing library [19] with C#.NET language. ZXing is an open-source library and is applied to generate the original test QR tag.
The result of the secret embedding procedure is shown in Fig. 4. Figure 4a is the original QR tag with the QR data “EURASIP Journal on Image and Video Processing.” Here, the QR version is 3 and the error correction level is L. According to Eq. (5), we can learn that the tolerant capacity of the secret embedding procedure is 24 bits. That is, the new scheme can embed at least 24 secret bits into Fig. 4a. The generated marked QR tag is shown in Fig. 4b by the secret embedding procedure. Figure 4b has the error correction capability for later recovering the error modules.
The pattern of the QR tag is composed of square modules (i.e., white and black dots), which are meaningless to users. That is, the marked QR tag cannot be easily observed by hackers if it is an embedded secret.
With barcode readers, the original QR data can be retrieved from the marked QR tag by the error correction capability. One can obtain the same QR data “EURASIP Journal on Image and Video Processing” from Fig. 4b. The meaningful QR data of the marked QR tag can effectively reduce the attention of general users and intruders.
Figure 5 demonstrates the original QR tag with larger QR data “HIGH PAYLOAD SECRET HIDING SCHEME FOR QR CODES…” The QR version and error correction level of Fig. 5a are 12-L. According to the estimation of Eq. (5), the tolerant secret capacity can be increased and is larger than 384 bits. The corresponding generated marked QR tag is shown in Fig. 5b. Only the authorized receivers with the secret keys can thereby retrieve the corresponding secrets from Figs. 4b and 5b.
Table 2 lists the capacities of the QR data under different QR versions and error correction levels. Table 3 shows the tolerant secret capacity tc, under different QR versions and error correction levels. The proposed scheme can embed at least the tc secret bits into the QR tag. Here, the maximum secret capacity is limited within the QR data payload. For instance, in QR version 1-L, the new scheme can embed at least 24 secret bits into the QR tag (lower bound), and the upper bound of the secret payload is 152 bits.
To demonstrate the performance of the hiding scheme, we generated a random secret stream and then embedded the secret into the selected modules by the random secret key according to the embedding procedure. The average experiment results are listed in Table 4 with 100 embedding iterations. Comparing the secret capacities in Table 3 with Table 4, we can observe that the new scheme can effectively enhance the capacity of embeddable secret. For instance, the original secret capacity is 24 bits in 1-L, and we can enhance and conceal in the average 50 secret bits at the same QR tag.
Table 5 lists the statistical analysis of the embeddable secret capacity under different QR versions and error correction levels. The probabilities of bits 0 and 1 for the secret stream and QR data are 1/2 with normal distribution. According to the experimental results and the statistical results in Tables 4 and 5, the new hiding scheme can achieve a higher secret capacity into a QR tag than the original embedding manner [16].
The number of error correction capability and the QR version are the measure metrics for evaluating the performances of the generated QR tags. The higher setting of the error correction level and QR version, the larger the secret capacity is. Moreover, the proposed scheme can preserve the original QR content by exploring the characteristic of the error correction capability of the QR tag.
Table 6 displays the overall comparison between the related schemes [12–16] and the proposed scheme. Unlike the conventional hiding and watermarking schemes [9–15], the new scheme embeds the secret into the modules of the QR tag directly [16]. Hence, the secret extracting procedure of the proposed scheme is feasible for barcode readers. The new scheme is of low computational complexity and can be applied to mobile device applications.
The secret payload of the proposed scheme is dynamic and can be increased according to the higher settings of QR versions and error correction levels. According to the secret embedding procedure in Subsection 3.1, the designed algorithm can embed more than tc secret bits into a QR tag as shown in Table 4. Therefore, the proposed scheme can enhance the embeddable secret payload more than the recent article [16].
5 Conclusions
The proposed secret hiding scheme effectively improves the embeddable secret capacity more than the related QR scheme. Moreover, based on the error correction capability of the QR characteristic, the generated marked QR tag can still preserve the readability of the QR data. According to the experimental analysis, the designed scheme is feasible to hide the secrets into a tiny QR tag as the purpose of steganography. Only the authorized user with the private key can further reveal the concealed secret successfully.
References
TH Tsai, WH Cheng, CW You, MC Hu, AW Tsai, HY Chi, Learning and recognition of on-premise signs (OPSs) from weakly labeled street view images. IEEE Trans Image Process 23(3), 1047–1059 (2014)
HH Shuai, DN Yang, WH Cheng, MS Chen, MobiUP: an upsampling-based system architecture for high quality video streaming on mobile devices. IEEE Trans. Multimedia 13(5), 1077–1091 (2011)
TH Tsai, WC Jhou, WH Cheng, MC Hu, IC Shen, T Lim, KL Hua, A Ghoneim, MA Hossain, SC Hidayati, Photo sundial: estimating the time of capture in consumer photos. Neurocomputing 177, 529–542 (2016)
Psytec QR code editor software, [Online]. Available: http://www.psytec.co.jp/docomo.html
ISO/IEC 18004, Information Technology Automatic Identification and Data Capture Techniques Bar Code Symbology QR Code, 2000
Denso-wave, [Online]. Available: http://www.qrcode.com/en/index.html
IS Reed, G Solomon, Polynomial codes over certain finite fields. J. Soc. Ind. Appl. Math 8(2), 300–304 (1960)
JC Chuang, YC Hu, HJ Ko, A novel secret sharing technique using QR code. International Journal of Image Processing 4, 468–475 (2010)
D. Buczynski, (2002-09-05), MSB/LSB tutorial, [Online]. Available: http://www.buczynski.com/Proteus/msblsb.html
S Katzenbeisser, FA Petitcolas, Information hiding techniques for steganography and digital watermarking. Artech House, Inc. Norwood, MA, USA, 2000
XP Zhang, SZ Wang, Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett 10(11), 781–783 (2006)
CH Chung, WY Chen, CM Tu, Image Hidden Technique Using QR-Barcode. Fifth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, 2009, pp. 522–525
WY Chen, JW Wang, Nested image steganography scheme using QR-barcode technique. Opt. Eng. 48(5), 057004-01–057004-10 (2009)
HC Huang, FC Chang, WC Fang, Reversible data hiding with histogram-based difference expansion for QR code applications. IEEE Trans. Consum. Electron. 57(2), 779–787 (2011)
S Dey, K Mondal, J Nath, A Nath, Advanced steganography algorithm using randomized intermediate QR host embedded with any encrypted secret message: ASA_QR algorithm. International Journal of Modern Education and Computer Science 6, 59–67 (2012)
YJ Chiang, PY Lin, RZ Wang, YH Chen, Blind QR code steganographic approach based upon error correction capability. KSII Trans. Internet Inf. Syst. 7(10), 2527–2543 (2013)
PY Lin, YH Chen, QR Code Steganography with Secret Payload Enhancement. the 3rd IEEE International Workshop on Mobile Multimedia Computing (MMC), 2016
J Mielikainen, LSB matching revisited. IEEE Signal Process Lett 13(5), 285–287 (2006)
Z. Xing (“Zebra Crossing”), [Online]. Available: http://code.google.com/p/zxing/
Acknowledgements
The authors thank the support from the Ministry of Science and Technology, Taiwan. In addition, our gratitude also goes to Michael Burton, Asia University.
Funding
This research was supported by the Ministry of Science and Technology, Taiwan, under contract No. MOST 105-2221-E-155-048, MOST 105-2218-E-155-010, MOST 104-2221-E-468-005, and 104-2221-E-009-109.
Authors’ contributions
PL drafted the manuscript and implemented the experiments for verifying the feasibility of the proposed scheme. YC participated in the design of the proposed scheme and drafted the manuscript. Both authors read and approved the final manuscript.
Competing interests
The authors declare that they have no competing interests.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Lin, PY., Chen, YH. High payload secret hiding technology for QR codes. J Image Video Proc. 2017, 14 (2017). https://doi.org/10.1186/s13640-016-0155-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13640-016-0155-0