Abstract
In this paper, we evaluate the performance of an enhanced cooperative MAC with busy tone (eBT-COMAC) protocol in mobile ad hoc networks via a combination of theoretical analysis and numerical simulation. Our previously proposed BT-COMAC protocol was enhanced by (1) redesigning the minislots used in the helper node selection procedure; (2) specifying complete frame formats for newly defined and modified control frames; and (3) using a new metric (the received SNR rather than the received power) in the helper node competition. In this eBT-COMAC protocol, cooperation probability is calculated based on a geometric analysis, and a Markov chain-based model is used to derive steady-state probabilities for backoff-related parameters. These results are used to analytically characterize two performance measures: system throughput and channel access delay. Numerical simulation of a mobile wireless network where all communication nodes are assumed to be uniformly distributed in space and move independently based on a random waypoint model is used to validate the analytical results and demonstrate the performance gains achieved by the proposed eBT-COMAC protocol.
Similar content being viewed by others
1 Introduction
With the remarkable development of wireless technologies, 4G mobile communication systems can support peak data transmission rates up to 3 Gbps [1]. However, when mobile nodes are located around a cell boundary or when two mobile nodes in a mobile ad hoc network [2] are located far away from each other, severe fading occurs, resulting in a large number of transmission errors. This form of wireless channel impairment can be overcome with multiple input multiple output (MIMO) technology. However, it is not always possible to include multiple antennas in a small mobile node. Cooperative communication is an alternative approach for overcoming the effect of channel fading [3]. An example of cooperative communication is shown in Fig. 1. If any node is located at an intermediate position between a sender and a receiver node, for example, in the shaded area in Fig. 1, this helper node can assist in the transmission process and help increase system throughput. In any cooperative communication scheme, finding the best helper node is critical. Helper node selection schemes are classified as two types: proactive and reactive schemes. In a proactive scheme, every mobile node maintains its relay table where wireless channel status with its neighboring nodes is stored [4–8, 23]. Each node shares a relay table with its neighboring nodes by periodically broadcasting some messages. Therefore, when a sender node wants to send a data packet to its destination node, it can find its helper node based on its relay table. In reactive schemes, the sender node begins the search for a helper node after the exchange of control frames [9, 10, 13–15, 20]. Although it takes time to select an optimal helper node, this reactive scheme guarantees that the newly selected helper node has a more conducive wireless channel than that in a proactive scheme. Initial studies in the area of cooperative medium access control (MAC) protocols focused on proactive schemes. However, reactive helper node selection schemes have gained popularity because (1) proactive schemes impose a greater load on both the network and processors within a node; and (2) there is no guarantee that the helper node chosen via a proactive scheme is optimal at data transmission time. In this work, we are interested in enhancing system performance with a new reactive helper node selection process in wireless local area networks (WLANs).
1.1 Related work
Most studies on cooperative MAC protocols follow the IEEE 802.11 WLAN design principle [11] and thus, only IEEE 802.11-based cooperative MAC protocols with link adaptation [12] are surveyed in this paper. There are three typical studies on reactive helper node selection schemes. In [13], three busy signals are used to find an optimal helper node, which is not energy efficient. A three-step helper node selection scheme was adopted in two previous studies [14, 15] consisting of GI (group indication), MI (member indication), and K minislot contention. The optimal cooperation region and system parameters were determined in [14] while an additional energy metric was used to select the best helper node in order to increase network lifetime in [15]. However, all three of these schemes use data transmission rates-related metrics for their helper node selection procedures, which has its drawbacks, as will be discussed in Section 1.2
There have also been several recent studies on cooperative MAC protocol design [16–19]. In [16], three transmisson modes are suggested where relay nodes were chosen based on proactive mechanisms: direct transmission, cooperative relay transmission, and two-hop relay transmission. Cooperative relay transmission mode is used for increasing system throughput while the two-hop relay transmission mode helps extend the service range. However, there is no suggested algorithm for choosing an appropriate mode. In [17], a new cooperative MAC protocol based on a three-way handshake with request to send (RTS), clear to send (CTS), and relay ready to send (RRTS) is proposed. Its reactive relay node selection scheme is based on the fact that the fastest relay candidate will reply to an RRTS frame earlier. However, [17] does not consider the possibility of relay node competition and approaches to deal with collisions. In [18], a helper node initiated cooperative MAC protocol is proposed. Helper nodes are decided in advance with the help of a relay table, and they initiate cooperative communication by sending a helper clear to send (HCTS) frame when the transmission rate between sender and receiver nodes falls below a threshold. In [19], three data transmission modes similar to those suggested in [16] are discussed. In contrast to [16], an algorithm to find a suitable transmission mode is suggested in [19]. It is described that the optimal helper node is chosen via the shortest path algorithm. However, there is no detailed discussion on how to select the optimal helper node. Therefore, issues such as helper node competition and whether the shortest path can be decided without additional control frame exchanges remain unanswered. In this paper, we aim to address these issues via the design and analysis of a new cooperative MAC protocol.
1.2 Contributions
In this paper, a new cooperative MAC protocol, enhanced cooperative MAC with busy tone signal (eBT-COMAC) protocol is proposed and a mathematical analysis and simulation are carried out on it. This protocol is an enhanced version of our previously proposed MAC protocol [20]. The eBT-COMAC protocol includes a reactive helper node selection scheme with a three-step helper node selection scheme. The key difference between our proposed helper node selection scheme and prior work [14, 15] is that we use a received signal-to-noise ratio (SNR) value in the minislot contentions rather than transmission rates, which were used in two previous studies. In general, the received SNR is closely related to transmission rates. However, because the number of transmission rates is limited (i.e., in IEEE 802.11b, there are four data transmission rates: 1, 2, 5.5, and 11 Mbps), the previous schemes may have the problem that candidate helper nodes with the same transmission rates can experience continuous collisions in minislot contentions. The main contributions of our study include the following:
-
The use of a new reactive helper node selection scheme with received SNR as the selection metric;
-
Clear design of the packet formats for the required control frames for eBT-COMAC protocol in order to support the helper node selection scheme;
-
Presentation and validation (via computer simulation) of a comprehensive mathematical analysis of the throughput and delay associated with eBT-COMAC;
-
The provision of increased system throughput performance with the eBT-COMAC protocol that is 58% higher than IEEE 802.11 WLAN [11] and 6% higher than prior work [14];
-
Easy extension of the entire approach to current standards, although IEEE 802.11b WLAN is the standard considered in this work.
This paper consists of five sections. A detailed explanation of the eBT-COMAC protocol is presented in Section 2; the system model and performance analysis are discussed in Section 3. The numerical results from the analysis and simulation are described in Section 4, and Section 5 presents the conclusions.
2 eBT-COMAC protocol
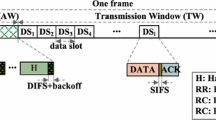
The frame exchange procedure for the eBT-COMAC protocol for cooperative communications is given in Fig. 2. Any sender node that has data to send begins its transmission by sending a cooperative request-to-send (CRTS) frame. When the receiver successfully receives the CRTS frame, it replies with a cooperative clear-to-send (CCTS) frame. After receiving the CRTS and CCTS frames, all mobile nodes located between the sender and receiver nodes can calculate two transmission rates, R S H ,R H R , based on the received SNR. The direct transmission rate R S R can be obtained from the physical layer convergence procedure (PLCP) header of the CCTS frame. Any candidate helper node whose two-hop effective rate (Re2) is greater than the one-hop effective rate (Re1) sends a short busy signal to notify all surrounding nodes that there is at least one eligible candidate helper node and thus, the helper node selection procedure will start. The helper node selection procedure consists of three steps: harsh contention (HC), exact contention (EC), and random contention (RC). Each contention consists of several minislots or slots. The size of each HC and EC minislot is the same as slot size (σ), as shown in Table 4, and the size of RC slots is the same as the request-to-help (RTH) frame transmission time at the basic rate. If any optimal node is decided from the helper node selection scheme, this node plays the role of the helper node, at which time two-hop communication begins. The effective transmission rate represents the ratio of DATA length in bits to the required time period in seconds from the end of the busy signal to the successful reception of the acknowledgement (ACK) frame. One- and two-hop effective transmission rates are calculated as follows [20]:
Here, L d is the DATA length in bits; NHC(EC) is the number of HC (EC) minislots; N R C is the number of RC slots; TACK,RTH,CTH are the transmission times of control frames ACK, RTH, and clear-to-help (CTH), respectively, and RSH(HR) corresponds to the DATA frame transmission rates between a sender and a helper (a helper and a receiver) node; SIFS is a MAC parameter representing short interframe space.
Detailed control frames used in the eBT-COMAC protocol are described in Fig. 3. The eBT-COMAC protocol is designed based on the IEEE 802.11 WLAN standard. Two control frames, the RTH and CTH frames, are newly suggested and the CRTS frame has a new field “PKT_LEN,” which stands for data packet length in bytes. The CTH frame has two different formats, namely, long CTH and short CTH. The long CTH is a full-sized frame with three optional fields, helper node address (HA), and two possible transmission rates between sender and helper nodes (R S H ) and helper and receiver nodes (R H R ). This long CTH is used when helper node selection competition is successful. On the other hand, the short CTH does not have three optional fields and it is used when the helper node selection competition fails. That is, long CTH is a positive response but short CTH is a negative response for RTH transmissions in HC, EC, and RC contention.
2.1 Helper Node Selection
The proposed eBT-COMAC protocol uses a reactive helper node selection scheme. Thus, the helper node selection procedure starts after the sender and the receiver nodes exchange CRTS and CCTS frames. The helper node selection scheme in eBT-COMAC consists of three steps. The goal of HC and EC minislot contention is to find the optimal helper node, and the RC slot contention is to select one helper node on a probabilistic basis. The metric used in this contention is a utility U, corresponding to the received SNR in the dB scale, i.e., \(U \equiv \log {SNR_{{{rcvd}}}}\). HC and EC consist of N H C and N E C minislots. The contention is carried out with the help of an RTH frame transmission in the appropriate minislot. Earlier, HC and EC minislots are assigned for the candidate helper nodes with greater utility values. In HC and EC minislot contention, if any candidate helper node observes that another node has transmitted an RTH frame earlier than itself, it exits the competition. The utility window between U m a x and U m i n is uniformly divided, and the mapping rule between the utility values and HC and EC minislot numbers can be explained by examining Fig. 4 when N H C = N E C = 3. Here, U i =U|rmmax−iU i n c ,i = 1,2, where \(U_{{{inc}}} = \frac {U_{{{max}}}-U_{{{min}}}}{3}\). If there is a collision in minislot 2 at HC minislot contention, those candidates involved in the collision begin their contention again at the EC minislots. In this case, U1 and U2 in the HC contention become U m a x and U m i n in the EC minislot contention. If there is a continuous collision in the EC minislot contention, those candidates involved in the collision move into the RC slot contention. The RC slot contention is based on random selection. Those candidate nodes that are involved in the RTH frame collision in the EC minislot contention generate a random number between 1 and N R C . Then, they transmit their RTH frame in the assigned slot. If there is more than one successful slot in this contention, the candidate that sent its RTH in the earlier slot has priority and then this candidate is chosen as the final helper node. The sender node decides the winner of the competition. If a helper node wins the competition, the sender node transmits a long CTH frame. Otherwise, the sender node transmits a short CTH frame. The “feedback” field in the CTH frame contains the competition result (C_result). “11” in “C_result” means that the competition was successful and “00” means failure in the competition. The flow chart for the operation at a candidate helper node is shown in Fig. 5.
3 Performance evaluation
Our goal is to analyze the eBT-COMAC protocol and quantify its throughput and channel access delay. The procedure to achieve this goal involves several intermediate results. First, cooperation probability and successful helper node selection probability are derived. Then, the steady-state probability for the three system state variables related to the backoff operation are evaluated. Finally, based on the calculation of average time slot size, the system throughput and channel access delay are derived. We begin by highlighting the assumptions underlying this process. First, nodes are assumed to be uniformly distributed within the communication area. Second, to calculate the success probability in the helper node selection competition, we use an approximate approach, the classical definition of probability. Actually, it is almost impossible to derive an exact equation for the success probability because of the dynamic characteristics of helper node selection competition. Therefore, Eq. (3) has a characteristic that is sensitive to the number of minislots and the number of helper nodes, which will be described in Section 4. Next, it is assumed that all frames, including the DATA frame are susceptible to packet transmission error, which is a more realistic consideration than in previous studies [5–15, 21, 22]. For completeness, several system variables required for the performance analysis of the IEEE 802.11b CSMA/CA and eBT-COMAC protocols are defined in Table 1.
We begin the analysis of the proposed protocol with the derivation of the cooperation probability. Let us consider an example in Fig. 1 where the sender and receiver nodes are far apart and thus can communicate with each other only at a rate of 1 Mbps. In this case, a helper node, located in the shaded area, can help increase the system throughput for communication between the sender and the receiver nodes.
Lemma 1
The cooperation probability p h corresponds to
where, r i ,p i , and p r are defined in Table 1, and S1(·) represents the size of overlapping area in Fig. 1.
Proof
The minimum participation criteria for cooperative communication is given in Table 2 when the relation between data transmission rates and ranges for IEEE 802.11b has those values in Table 3 [20]. The cooperation probability p h can be approximately expressed as the weighted sum of various ratios of the overlapped area to the transmission area of the sender node when the direct transmission rate is 1, 2, and 5.5 Mbps, respectively. For example, when the direct transmission rate is 1 Mbps with the probability p1, \(\pi r_{1}^{2}\) is the transmission area of the sender node and S1(r2,r5.5,r1) represents the overlapped area when the direct transmission rate between the sender and receiver nodes is 1 Mbps, the sender and the helper nodes transmit the DATA frame at 2 Mbps, and the helper and receiver nodes transmit the DATA frame at 5.5 Mbps. Please see Appendix 1 for the exact derivation of S1(). □
As described in Section 2, the helper node selection scheme consists of three steps: HC, EC, and RC competitions. The probability of successful helper node selection in each step is provided in Lemma 2.
Lemma 2
The probability that the optimal helper node is selected successfully from three-step competitions corresponds to
Proof
In the first step, let us define the possible number of candidates participating in HC the minislot contention as M1=p h N h . Then the probability ps1 that the best helper node is selected successfully in the HC minislot contention can be calculated as the ratio of the number of successful transmissions of the RTH frame to the total number of possible transmissions.
In the second step, let us define the possible number of candidates participating in the EC minislot contention as M2. Although an HC minislot is assigned to a candidate helper node based on its utility value, let us assume that the location of the HC minislot where the helper node competition is successful is uniformly distributed between 1 and N H C . Then, it is easy to see that M2 = M1/N H C . The probability ps2 that the best helper node is selected successfully in the EC minislot contention can be calculated as the ratio of the number of successful transmissions of the RTH frame to the total number of possible transmissions.
In the third step, the RC slot contention, let us define the possible number of candidates participating in the RC slot contention as M3, where M3 = M2/N E C . Then, the probability ps3 that the best helper node is selected successfully in the RC slot contention can be calculated as the ratio of the number of successful transmissions of the RTH frame to the total number of possible transmissions.
Finally, the probability that the optimal helper node is selected successfully is the weighted sum of the successful selection of helper nodes at each step, which is provided in Eq. (3). □
RTH frame transmission failure occurs when an optimal helper node is not decided from the three-step competitions. This failure probability p fr corresponds to
The frame transmission procedure in the eBT-COMAC protocol, including the backoff operation for each station, is modeled as a Markov chain with the system state vector:
-
b(t): backoff stage of the sender node, b(t)=0,1,⋯,r
-
c(t): value of the backoff counter, c(t)=0,1,⋯,Wb(t)−1
-
o(t): frame transmission phase, o(t)=0,1,⋯,7.
Here, the variable o(t) represents the sending phase for each frame, which is shown in Fig. 7: 0 represents the sending phase of a CRTS frame; 1 refers to a CCTS frame, 2,3,4, and 5 are for RTH, CTH, DATA1, and DATA2, repectively; 6 represents an ACK frame; and 7 is for DATA frame at direct transmission. We attempt to derive steady-state probabilities for this system state vector. Our mathematical analysis approach is carried out based on previous research in [21–23]. It is assumed that every sender node always has data frames to transmit in its buffer, which is known as a saturated traffic model.
The eBT-COMAC protocol uses the same retransmission scheme as IEEE 802.11b and thus, the contention window size at each retransmission is determined by the following rule:
Transmission failure for the CRTS frame could occur due to collisions with other frames or a bad wireless channel. Therefore, the CRTS frame transmission failure probability is given by
Let us define the steady-state probability as \(\alpha _{ijk} \equiv {\lim }_{t\to \infty } {{prob}}.\{b(t)=i, c(t)=j, o(t)=k\}\). State transition rate diagrams for eBT-COMAC are shown in Figs. 6, 7, and 8. Figure 6 shows the total state transition rate diagram, and the detailed descriptions of S i ,1≤i≤r located in the left side of Fig. 6 are shown in Figs. 7 and 8.
The balance equations for the eBT-COMAC protocol are given by
Here, A(i)≡(1−p r +p m p r )αi01+p m αi03+p d (αi04+αi05+αi07) and \(p_{r} = \pi r_{1}^{2} / A_{c}\) where A c refers to the size of the communication area.
By the iterative method, steady-state probabilities can be derived with the additional condition that the sum of all probabilities is one. That is,
In the calculation of the steady-state probabilities, the CRTS frame transmission probability τ and the transmission failure probability for a CRTS frame due to collision p c should be expressed as
Two performance measures were considered for the performance analysis. One is the system throughput in bps, and the other performance measure is the average channel access delay in seconds. In order to derive the system throughput, two types of average delays should be calculated in advance. The first one is D S , the average time delay from the transmission of the CCTS frame to the successful reception of the ACK frame, and the second one is D E , the average time delay from the transmission of the CCTS frame to transmission failure with the CCTS, RTH, CTS, DATA, or ACK frame.
Lemma 3
The average time delays from the transmission of the CCTS frame to the successful reception of the ACK frame for direct and cooperative transmission, respectively, correspond to
where, \(D_{S}^{k}\) is the average time delay spent at phase k for successful frame transmission. \(D_{E}^{2}\) is the average time delay spent at phase 2 because of frame transmission error; it will be derived in the Lemma 4.
Proof
The average time delays for successful frame transmission at each phase, \(D_{S}^{k},~k=1,2, \cdots, 7\), should be derived first. According to the sequence of frame exchanges, these delays are given by
Here, P ts =ps1+(1−ps1)ps2+(1−ps1)(1−ps2)ps3. T H C and T E C are the average sizes of the HC and EC minislot contention periods. It is assumed that the location of the HC or EC minislot where the helper node competition is successful is uniformly distributed between 1 and N H C or N E C . Then, they can be expressed as \(T_{{{HC}}}= \frac {N_{{{HC}}} }{2} \sigma +T_{{{RTH}}}\) and \(T_{{{EC}}}= \frac {N_{EC}}{2} \sigma +T_{{{RTH}}}\), respectively. T B T refers to the time period of the busy tone signal. In the above equation, \(T_{{{DATA}}_{c(d)}}\phantom {\dot {i}\!}\) represents the data transmission period in the cooperative (direct) transmission at each data transmission rate. These values can be derived as follows:
Then, the average time delays from the CCTS transmission to successful reception of the ACK frame for direct transmission and two-hop transmission are as given in Eqs. (17) and (18). □
Lemma 4
The average time delay from the CCTS frame to any frame transmission failure corresponds to
where, the probability P t e is defined for its normalization condition and it corresponds to
Here, \(D_{E}^{k},~k=1,2, \cdots, 7\) are the average time delays spent at phase k because of frame transmission failure.
Proof
The average time delays \(D_{E}^{k},~k=1,2, \cdots, 7\), are given by
For example, the phase k=2 represents the transmission of RTH frames and it means helper node selection competition. Thus, \(D_{E}^{2}\) refers to the required time delay for complete failure of the helper node selection procedure. This delay consists of a busy tone signal, HC and EC contention periods, RC slots, and two short CTH frame transmissions in the HC and EC contentions, respectively. Then, the average time delay from the CCTS frame to complete transmission failure can be expressed as a weighted sum of consumed time delays until complete transmission failure in each phase. If complete failure occurs at the phase k=4, then, frame transmissions at phases 1, 2, and 3 should be successful. Thus, the time delay from the CCTS frame to DATA frame transmission failure is \(D_{S}^{1} + D_{S}^{2} + D_{S}^{3} + D_{E}^{4}\). Therefore, the average time delay from the CCTS frame to any frame transmission failure corresponds to Eq. (21). □
The following two theorems provide the expression for evaluating two performance measures of interest: system throughput and channel access delay.
Theorem 1
(system throughput) The system throughput is defined as the length of successfully transmitted data in bits during a unit of time, and corresponds to
where, L h is the sum of the MAC header and PLCP header, E[S] is the average slot time, P tr is the probability that there is at least one CRTS frame transmission by N s mobile users in the considered time duration, and P s is the probability that the transmitted CRTS frame is successfully received by the helper node without collision and transmission error. Pa1 and Pa2 are the probabilities that no transmission errors occur during the period from the CCTS frame to ACK frame transmission for direct and two-hop transmissions, respectively.
Proof
Since CRTS frame transmission by each sender node is modeled as a Beroulli distribution with the probability τ, two probabilities P tr and P s are derived as
The probabilities Pa1 and Pa2 correspond to
Let us define S as slot time, representing the time interval between two consecutive idle slots. There are four different types of slot times. First, when there is no transmission on the channel, the slot time means the slot duration T I =σ. Second, when the transmission of the CRTS frame results in failure due to collision or a bad wireless channel, the slot time becomes T F . Third, when the source node does not receive the ACK frame, even after successful transmission of the CRTS frame, the slot time becomes T E . Finally, if the total transmission scenario is successful, then this slot time is TS1 for direct transmission or TS2 for a two-hop transmission. These slot time types are indicated as
Then, the average value of S is the weighted sum of the four different slot times and is given by
The probability that the given DATA frame is transmitted successfully is the product of three probabilities derived in Eqs. (23)–(26): P t r , P s , and Pa1+Pa2. Because the system throughput can be expressed as the ratio of the total length of the DATA frame successfully transmitted in bits to the average time slot, it corresponds to Eq. (22). □
Theorem 2
(channel access delay) The average channel access delay, which is defined as the time period from the beginning of the backoff to the successful reception of the ACK frame, can be expressed as
Here, W represents the minimum contention window size, CW m i n and T A =T C R T S +SIFS+{DS1p f r +DS2(1−p f r )}, and P S (i) represents the probability that one sender node receives the ACK frame successfully at the i-th backoff stage.
Proof
The probability P S (i) can be approximately modeled as a geometric distribution with the parameter p s t . Here, the probability p s t represents the successful transmissions from the CRTS frame to the ACK frame and is given by
Then, the probability P S (i) is given by
It is assumed that when the current system state of the sender node is {b(t)=i,c(t)=0,o(t)=k} as in Fig. 6, the next system state is determined based on uniform distribution. That is, the next possible system state will be (0,j,0) or (i+1,j,0) depending on whether the current frame transmission is successful or not. Here, the value j is uniformly distributed between 0 and W0−1 or Wi+1−1. Because the sender node stays in any state until the upcoming idle slot, the average time to stay in any state in Fig. 6 equals the average slot size E[ S]. Thus, the channel access delay corresponds to the weighted sum of the products of E[ S], and the number of states where the sender node stayed from the beginning of channel sensing to any state of (i,0,6),0≤i≤r when the ACK transmission is successful. Therefore, the expression of the channel access delay is given as Eq. (28). □
4 Network model and numerical results
4.1 Network model and environment
We consider the operation of the eBT-COMAC protocol over the IEEE 802.11b WLAN specification [11]. First, it is important to note that the proposed eBT-COMAC protocol can also be easily integrated into other current wireless networking standards. We assume that all mobile nodes are working in WLAN ad hoc mode. Therefore, any mobile node can directly communicate with the other mobile nodes. It is assumed that all mobile nodes are uniformly distributed within a 200m×200m square communication area and mobile nodes move independently within this communication area based on a random waypoint mobility model: (1) every mobile node determines its next location based on uniform distribution and then moves to its next location at the speed of v [m/sec], which is determined from the uniform distribution between 0 and V m a x ; (2) as soon as it arrives at its next location, it takes a pause during a period, which is also determined from the uniform distribution between 0 and T p a u s e ; (3) after its pause, it returns to step (1) and repeats the entire process. All mobile nodes are classified into one of three types: sender, receiver, or helper nodes. It is assumed that there are N s communication connection pairs between the sender and receiver nodes, and that these communication connections are fixed during the entire simulation period. The log-distance path loss model is used for modeling wireless channels, and the relationship between transmission distance and path loss is represented by Eq. (31) [24]:
where d0 is the reference distance and n is the path loss exponent (in this paper, we use n = 3).
The simulation code was programmed with a gnu C++ compiler using the SMPL library [25]. Computer simulation was conducted 10 times with a different seed each time, and we used the averaged data as simulation results. For simplicity, it was also assumed that transmission error probabilities for the control and DATA frames caused by a bad wireless channel were the same (p m =p d ). Mathematical analysis and computer simulations were conducted and compared in order to prove the correctness of the mathematical equations. The system parameters used in the performance evaluation are described in Table 4.
4.2 Numerical results
First, we will explain several abbreviations used in the legends of Figs. 9, 10, 11 and 12 for notifying each numerical result. “ana-ebtmac” and “sim-ebtmac” represent the analysis and simulation results for the eBT-COMAC protocol, respectively. Figure 9 shows the comparison of throughput performances by analysis and simulation results for the eBT-COMAC protocol and analysis results for the IEEE 802.11b DCF without cooperation. These numerical results were obtained when there were 40 helper nodes in the communication area. It is shown that the eBT-COMAC provides enhanced system performance about 58% higher than IEEE 802.11 WLAN (notified as “ana-dcf” in this figure). This coincides with our expectation that cooperative communication has explicit benefits over non-cooperative communication. Simulation results were consistent with the analytical results in all ranges. It is also shown that IEEE 802.11-related MAC protocols provide the best system performance when there are about five sender nodes in the communication area.
Figure 10 shows a comparison of delay performances by analysis and simulation when there are forty helper nodes in the communication area. This figure shows that the eBT-COMAC protocol has an obvious advantage over direct communication. The analytical and simulation results are consistent; although there is a discrepancy between the simulation and analysis of about 22% when N s = 100, the difference is negligible.
Figure 11 shows a comparison of throughput performances as a function of the number of helper nodes when N s = 10. According to the approximation that we used in deriving the probability p s r in Eq. (3), analytical results are sensitive to the number of helper nodes. According to Eqs. (4)–(6), when M1 = 1, M2 = 1, and M3 = 1, helper node competition becomes completely successful with p s r = 1. In addition, when M1,M2, and M3 is less than one, the probability that the best helper node is successfully decided becomes zero in Eqs. (4)–(6). Significant jumps in this figure occur when N h is about 15, 35, and 95. These values of N h corresponds to cases when M1,M2, and M3 are slightly greater than one, respectively, and this is why there are significant jumps in this figure.
Figure 12 shows a comparison of delay performances as a function of the number of helper nodes when N s = 10. The discrepancy between the simulation and analysis results may be due to our approximation when deriving Eqs. (2) and (3). However, Fig. 12 shows that the simulation results show a slight increase, although it is a little, in the section where the analysis results show a consistent increase.
Figure 13 shows a throughput comparison of the eBT-COMAC protocol with the reference [14], denoted as “clmac”. When N H C = N E C = 3, it seems that the eBT-COMAC protocol provides slightly lower throughput than the reference [14]. This means that the optimal candidate helper node was not properly selected in the HC and EC minislot contentions of the eBT-COMAC protocol with this number of minislots. However, when N H C and N E C are greater than 5, the eBT-COMAC protocol provides approximately 6% higher system throughput performance than the reference [14] when N H C = 8. A greater number of minislots contributes to choosing one optimal helper node because helper node candidates with different received SNR values can be classified more clearly. However, the system throughput performance results for reference [14] are almost the same when N H C and N E C are 3 and 5, respectively. This is because the cooperative MAC protocol in [14] uses transmission rates as a metric in the helper node selection. There are only four different transmission rates in IEEE 802.11b and thus, more minislots are useless for this MAC scheme.
5 Conclusions
In this paper, we presented for the first time, a comprehensive theoretical performance analysis of an enhanced BT-COMAC protocol and validated the analytical results via numerical simulations. The new helper node selection scheme in the eBT-COMAC protocol is based on received SNR values at each candidate node. This results in a dynamic characteristic that presents challenges in analytical modeling. In this paper, two probabilities, the cooperation probability and the probability that a helper node is successfully selected, were derived based on a geometric analysis. These probabilities, along with steady-state probabilities of backof-related parameters (derived based on a Markov analysis), are used to derive theoretical expressions for the system throughput and channel access delay of the eBT-COMAC protocol. Although the analytical results are not exact and are based on approximations that provide theoretical tractability, they are for the most part consistent with the numerical simulations. Future work will involve the design of an energy-aware eBT-COMAC protocol that can provide throughput gains while improving network lifetime.
6 \thelikesection Appendix 1: calculation of cooperative area
Let us consider two circles, the radii of which are a and b, respectively, with an overlapped area, as shown in Fig. 14. The distance between the origins of the two circles is d. Using the theory of the segment of a circle and its radius, the overlapped area S can be derived as follows:
According to a cosine formula, the following relation can be simply derived.
Then, combining Eq. (33) with Eq. (32), the overlapped area can be derived as follows:
As shown in Table 3, the transmission range of 1 Mbps, for example, is 74.7≤r1≤100 m. Then, the equation of S1(r2,r5.5,r1) used in Eqs. (2), (19), (20) is calculated as the average of two transmission areas by the transmission rate R1 and the one level higher rate R2.
Abbreviations
- ACK:
-
Acknowledgement
- BT-COMAC:
-
Cooperative MAC with busy tone
- CCTS:
-
Cooperative clear to send
- CRTS:
-
Cooperative request to send
- CTH:
-
Clear to help
- CTS:
-
Clear to send
- eBT-COMAC:
-
Enhanced BT-COMAC
- EC:
-
Exact contention
- GI:
-
Group indication
- HA:
-
Helper node address
- HC:
-
Harsh contention
- HCTS:
-
Helper clear to send
- MAC:
-
Medium access control
- MI:
-
Member indication
- MIMO:
-
Multiple input multiple output
- PLCP:
-
Physical layer convergence procedure
- RC:
-
Random contention
- RRTS:
-
Relay ready to send
- RTH:
-
Request to help
- RTS:
-
Request to send
- SIFS:
-
Short interframe space
- SNR:
-
Signal-to-noise ratio
- WLAN:
-
Wireless local area network
References
3GPP LTE-Advanced specification release 10 (2009). http://www.3gpp.org/technologies/keywords-acronyms/97-lte-advanced. Accessed June 2013.
IETF MANET Working Group. https://datatracker.ietf.org/wg/manet/about/. Accessed Nov 2016.
A Nosratinia, TE Hunter, A Hedayat, Cooperative communication in wireless networks. IEEE Commun. Mag. 42(10), 74–89 (2004).
N Sai Shankar, C Chun-Ting, G Monisha, in IEEE Int. Conf. on Wireless Networks. Cooperative communication MAC (CMAC)- A new MAC protocol for next generation wireless LANs (Hawaii, 2005), pp. 1–6.
H Zhu, G Cao, rDCF: a relay-enabled medium access control protocol for wireless ad hoc networks. IEEE Trans. Mob. Comput. 5(9), 1201–1214 (2006).
P Liu, Z Tao, S Narayanan, T Korakis, SS Panwar, CoopMAC: a cooperative MAC for wireless LANs. IEEE J. Sel. Areas Commun. 25(2), 340–353 (2007).
K Tan, Z Wan, H Zhu, J Andrian, in 4th IEEE Conf. on Sensor, Mesh, and Ad hoc Comm. and Networks. CODE: cooperative medium access for multi-rate wireless ad hoc network (San Diego, 2007), pp. 1–10.
H Jin, X Wang, H Yu, Y Xu, Y Guan, X Gao, in IEEE WCNC-2009. C-MAC: a MAC protocol supporting cooperation in wireless LANs (Budapest, 2009), pp. 1–6.
H Shan, W Zhuang, Z Wang, Distributed cooperative MAC for multihop wireless networks. IEEE Commun. Mag. 47(2), 126–133 (2009).
H Shan, W Zhuang, Z Wang, in IEEE ICC-2009. Cooperation or not in mobile ad hoc networks: A MAC perspective (Dresden, 2009), pp. 1–6.
IEEE Standards, in Part 11: Wireless LAN medium access control (MAC) and physical layer (PHY) specifications. IEEE Std 802.11-2012, (2012).
G Holland, N Vaidya, P Bahl, in ACM/IEEE MOBICOM-2001. A rate-adaptive MAC protocol for multi-hop wireless networks (Rome, 2001), pp. 236–251.
H Shan, P Wang, W Zhuang, Z Wang, in IEEE GLOBECOM-2008. Cross-layer cooperative triple busy tone multiple access for wireless networks (New Orleans, 2008), pp. 1–5.
H Shan, HT Cheng, W Zhuang, Cross-layer cooperative MAC protocol in distributed wireless networks. IEEE Trans. Wirel. Commun. 10(8), 2603–2615 (2011).
Z Yong, L Ju, Z Lina, Z Chao, C Chen, Link-utility-based cooperative MAC protocol for wireless multi-hop networks. IEEE Trans. Wirel. Commun. 10(3), 995–1005 (2011).
T Zhou, H Sharif, M Hempel, P Mahasukhon, W Wang, T Ma, A novel adaptive distributed cooperative relaying MAC protocol for vehicular networks. IEEE J. Sel. Areas Commun. 29(1), 72–82 (2011).
J Sheu, J Chang, C Ma, C Leong, in IEEE WCNC. A cooperative MAC protocol based on 802.11 in wireless ad hoc networks (Shanghai, 2013), pp. 416–421.
MdR Amin, SS Moni, SA Shawkat, MdS Alam, in Int’l Conf. Computer and Information Technology. A helper initiated distributed cooperative MAC protocol for wireless networks (Khulna, 2014), pp. 302–308.
AFMS Shah, MdS Alam, SA Showkat, in IEEE TENCON. A new cooperative MAC protocol for the distributed wireless networks (Macao, 2015), pp. 1–6.
J Jang, Performance evaluation of a new cooperative MAC protocol with a helper node selection scheme in ad hoc networks. J. Inf. Commun. Converg. Eng. 12(4), 199–207 (2014).
G Bianchi, Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Selec. Areas Commun. 19(3), 535–547 (2000).
JW Tantra, CH Foh, AB Mnaouer, in IEEE ICC-2005. Throughput and delay analysis of the IEEE 802.11e EDCA saturation (Seoul, 2005), pp. 3450–3454.
J Jang, SW Kim, S Wie, Throughput and delay analysis of a reliable cooperative MAC protocol in ad hoc networks. J. Commun. Netw. 5(3), 524–532 (2012).
TS Rappaport, Wireless communications: principles and practice (Prentice-Hall, 2002).
MH MacDougall, Simulating computer systems: techniques and tools (The MIT Press, 1992).
Acknowledgements
The authors would like to thank the reviewers for their thorough reviews and helpful suggestions.
Funding
This research work was funded by a grant from Inje University for the research in 2016 (20160432).
Availability of data and materials
Not applicable.
Author information
Authors and Affiliations
Contributions
JJ proposed the system model, derived the mathematical equations, and performed the simulation and manuscript writing. BN contributed in manuscript revision and correction. Both authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Author’s information
Not applicable.
Competing interests
The authors declare that they have no competing interests.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License(http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Jang, J., Natarajan, B. Performance analysis of an enhanced cooperative MAC protocol in mobile ad hoc networks. J Wireless Com Network 2018, 76 (2018). https://doi.org/10.1186/s13638-018-1088-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-018-1088-3