Abstract
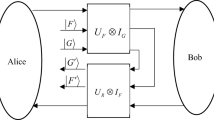
We investigate the possibility of eavesdropping on a quantum key distribution network by local sequential quantum unsharp measurement attacks by the eavesdropper. In particular, we consider a pure two-qubit state shared between two parties Alice and Bob, sharing quantum steerable correlations that form the one-sided device-independent quantum key distribution network. One qubit of the shared state is with Alice and the other one while going to Bob’s place is intercepted by multiple sequential eavesdroppers who perform quantum unsharp measurement attacks thus gaining some positive key rate while preserving the quantum steerable correlations for Bob. In this way, Bob will also have a positive secret key rate although reduced. However, this reduction is not that sharp and can be perceived due to the decoherence and imperfection of the measurement devices. We found that there is a possibility of sequential eavesdropping even after setting a minimum threshold on the observed secure key rate by Alice and Bob. In the end, we show that an unbounded number of eavesdroppers can also get secret information in some specific scenario.

Similar content being viewed by others
Data Availability Statement
This manuscript has associated data in a data repository. [Authors’ comment: The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.]
References
N. Gisin, G. Ribordy, W. Tittel, H. Zbinden, Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002). https://doi.org/10.1103/RevModPhys.74.145
C.H. Bennett, G. Brassard, Quantum Cryptography, Public Key Distribution and Coin Tossing, (IEEE Press, New York, 1984). https://researcher.watson.ibm.com/researcher/files/us-bennetc/BB84highest.pdf
C.H. Bennett, Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121 (1992). https://doi.org/10.1103/PhysRevLett.68.3121
A.K. Ekert, Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991). https://doi.org/10.1103/PhysRevLett.67.661
V. Scarani, H.B. Pasquinucci, N.J. Cerf, M. Dusek, N. Lütkenhaus, M. Peev, The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009). https://doi.org/10.1103/RevModPhys.81.1301
A. Aćin, N. Gisin, L. Masanes, From Bell’s Theorem to secure quantum key distribution. Phys. Rev. Lett. 97, 120405 (2006). https://doi.org/10.1103/PhysRevLett.97.120405
S. Gupta, D. Saha, Z.P. Xu, A. Cabello, A.S. Majumdar, Quantum contextuality provides communication complexity advantage, (2022), Preprint at arXiv:2205.03308. https://arxiv.org/abs/2205.03308
D. Mayers, Unconditionally secure quantum bit commitment is impossible. Phys. Rev. Lett. 78, 3414 (1997). https://doi.org/10.1103/PhysRevLett.78.3414
D. Mayers, Unconditional security in quantum cryptography. J. ACM 48, 351 (2001). https://doi.org/10.1145/382780.382781
D. Deutsch, A. Ekert, R. Jozsa, C. Macchiavello, S. Popescu, A. Sanpera, Quantum privacy amplification and the security of quantum cryptography over noisy channels. Phys. Rev. Lett. 77, 2818 (1996). https://doi.org/10.1103/PhysRevLett.77.2818
H.K. Lo, H.F. Chau, Is quantum bit commitment really possible? Phys. Rev. Lett. 78, 3410 (1997). https://doi.org/10.1103/PhysRevLett.78.3410
P.W. Shor, J. Preskill, Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441 (2000). https://doi.org/10.1103/PhysRevLett.85.441
G. Brassard, N. Lütkenhaus, T. Mor, B.C. Sanders, Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000). https://doi.org/10.1103/PhysRevLett.85.1330
N. Lütkenhaus, Security against individual attacks for realistic quantum key distribution. Phys. Rev. A. 61, 052304 (2000). https://doi.org/10.1103/PhysRevA.61.052304
S. Bera, S. Gupta, A.S. Majumdar, Device-independent quantum key distribution using random quantum states (2022), Preprint at arXiv:2205.07464
C. Branciard, E.G. Cavalcanti, S.P. Walborn, V. Scarani, H.M. Wiseman, One-sided device-independent quantum key distribution: Security, feasibility, and the connection with steering. Phys. Rev. A. 85, 010301(R) (2012). https://doi.org/10.1103/PhysRevA.85.010301
R. Uola, A.C.S. Costa, H.C. Nguyen, O. Guhne, Quantum steering. Rev. Mod. Phys. 92, 015001 (2020). https://doi.org/10.1103/RevModPhys.92.015001
E. Schrödinger, Discussion of probability relations between separated systems. Proc. Cambridge Philos. Soc. 31, 553 (1935). https://www.cambridge.org/core/journals/mathematical-proceedings-of-the-cambridge-philosophical-society/article/discussion-of-probability-relations-between-separated-systems/C1C71E1AA5BA56EBE6588AAACB9A222D
E. Schrödinger, Probability relations between separatedsystems. Proc. Cambridge Philos. Soc. 32, 446 (1936). https://www.cambridge.org/core/journals/mathematical-proceedings-of-the-cambridge-philosophical-society/article/probability-relations-between-separated-systems/641DDDED6FB033A1B190B458E0D02F22
H.M. Wiseman, S.J. Jones, A.C. Doherty, Steering, entanglement, nonlocality, and the Einstein–Podolsky–Rosen Paradox. Phys. Rev. Lett. 98, 140402 (2007). https://doi.org/10.1103/PhysRevLett.98.140402
S.J. Jones, H.M. Wiseman, A.C. Doherty, Entanglement, Einstein–Podolsky–Rosen correlations, Bell nonlocality, and steering. Phys. Rev. A 76, 052116 (2007). https://doi.org/10.1103/PhysRevA.76.052116
E.G. Cavalcanti, S.J. Jones, H.M. Wiseman, M.D. Reid, Experimental criteria for steering and the Einstein–Podolsky–Rosen paradox. Phys. Rev. A 80, 032112 (2009). https://doi.org/10.1103/PhysRevA.80.032112
J. Schneeloch, C.J. Broadbent, S.P. Walborn, E.G. Cavalcanti, J.C. Howell, Einstein–Podolsky–Rosen steering inequalities from entropic uncertainty relations. Phys. Rev. A 87, 062103 (2013). https://doi.org/10.1103/PhysRevA.87.062103
S. Gupta, D. Das, A.S. Majumdar, Distillation of genuine tripartite Einstein–Podolsky–Rosen steering. Phys. Rev. A 104, 022409 (2021). https://doi.org/10.1103/PhysRevA.104.022409
S. Gupta, D. Das, C. Jebarathinam, A. Roy, S. Datta, A.S. Majumdar, “All-versus-nothing’’ proof of genuine tripartite steering and entanglement certification in the two-sided device-independent scenario. Quantum Stud. Math. Found. 9, 175–198 (2022). https://doi.org/10.1007/s40509-021-00261-x
A. Einstein, B. Podolsky, N. Rosen, Can quantum-mechanical description of physical reality be considered complete? Phys. Rev. 47, 777 (1935). https://doi.org/10.1103/PhysRev.47.777
T. Pramanik, M. Kaplan, A.S. Majumdar, Fine-grained Einstein–Podolsky–Rosen steering inequalities. Phys. Rev. A 90, 050305(R) (2014). https://doi.org/10.1103/PhysRevA.90.050305
S. Sasmal, D. Das, S. Mal, A.S. Majumdar, Steering a single system sequentially by multiple observers. Phys. Rev. A 98, 012305 (2018). https://doi.org/10.1103/PhysRevA.98.012305
S. Gupta, A.G. Maity, D. Das, A. Roy, A.S. Majumdar, Genuine Einstein–Podolsky–Rosen steering of three-qubit states by multiple sequential observers. Phys. Rev. A 103, 022421 (2021). https://doi.org/10.1103/PhysRevA.103.022421
F.J. Curchod, M. Johansson, R. Augusiak, M.J. Hoban, P. Wittek, A. Acín, Unbounded randomness certification using sequences of measurements. Phys. Rev. A 95, 020102(R) (2017). https://doi.org/10.1103/PhysRevA.95.020102
S. Pironio, A. Acín, N. Brunner, N. Gisin, S. Massar, V. Scarani, Device-independent quantum key distribution secure against collective attacks. New J. Phys. 11, 045021 (2009). https://doi.org/10.1088/1367-2630/11/4/045021/pdf
R. Silva, N. Gisin, Y. Guryanova, S. Popescu, Multiple observers can share the nonlocality of half of an entangled pair by using optimal weak measurements. Phys. Rev. Lett. 114, 250401 (2015). https://doi.org/10.1103/PhysRevLett.114.250401
S. Mal, A.S. Majumdar, D. Home, Sharing of nonlocality of a single member of an entangled pair of qubits is not possible by more than two unbiased observers on the other wing. Mathematics 4, 48 (2016). http://www.mdpi.com/2227-7390/4/3/48/htm
P. Busch, Unsharp reality and joint measurements for spin observables. Phys. Rev. D 33, 2253 (1986). https://doi.org/10.1103/PhysRevD.33.2253
P. Busch, M. Grabowski, P.J. Lahti, Operational Quantum Physics (Springer-Verlag, Berlin, 1997)
M. Banik, Md.R. Gazi, S. Ghosh, G. Kar, Degree of complementarity determines the nonlocality in quantum mechanics. Phys. Rev. A 87, 052125 (2013). https://doi.org/10.1103/PhysRevA.87.052125
P. Busch, T. Heinosaari, J. Schultz, N. Stevens, Comparing the degrees of incompatibility inherent in probabilistic physical theories. Europhys. Lett. 103, 10002 (2013). https://doi.org/10.1209/0295-5075/103/10002
S.K. Choudhary, T. Konrad, H. Uys, Implementation schemes for unsharp measurements with trappedions. Phys. Rev. A 87, 012131 (2013). https://doi.org/10.1103/PhysRevA.87.012131
M.-J. Hu, Z.-Y. Zhou, X.-M. Hu, C.-F. Li, G.-C. Guo, and Y.-S. Zhang, Observation of non-locality sharing among three observers with one entangled pair via optimal weak measurement. NPJ Quantum Inf. 4, 63 (2018). https://www.nature.com/articles/s41534-018-0115-x
M. Schiavon, L. Calderaro, M. Pittaluga, G. Vallone, P. Villoresi, Three-observer Bell inequality violation on a two-qubit entangled state. Quantum Sci. Technol. 2, 015010 (2017). https://doi.org/10.1088/2058-9565/aa62be/meta
Y.-H. Choi, S. Hong, T. Pramanik, H.-T. Lim, Y.-S. Kim, H. Jung, S.-W. Han, S. Moon, and Y.-W. Cho, Demonstration of simultaneous quantum steering by multiple observers via sequential weak measurements. Optica 7, 675 (2020). https://www.osapublishing.org/optica/fulltext.cfm?uri=optica-7-6-675 &id=432421
G. Foletto, L. Calderaro, G. Vallone, P. Villoresi, Experimental demonstration of sequential quantum random access codes. Phys. Rev. Res. 2, 033205 (2020). https://doi.org/10.1103/PhysRevResearch.2.033205
H. Anwer, S. Muhammad, W. Cherifi, N. Miklin, A. Tavakoli, M. Bourennane, Experimental characterization of unsharp qubit observables and sequential measurement incompatibility via quantum random access codes. Phys. Rev. Lett. 125, 080403 (2020). https://doi.org/10.1103/PhysRevLett.125.080403
E.G. Cavalcanti, C.J. Foster, M. Fuwa, and H.M. Wiseman, Analog of the Clauser–Horne–Shimony-Holt inequality for steering. J. Opt. Soc. Am. B 32, A74 (2015). https://www.osapublishing.org/josab/abstract.cfm?uri=josab-32-4-A74
M. Hillery, V. Buzek, A. Berthiaume, Quantum secret sharing. Phys. Rev. Lett. 68, 3121 (1992). https://doi.org/10.1103/PhysRevLett.68.3121
Acknowledgements
SG acknowledges S. N. Bose National Centre for Basic Sciences, Kolkata, for the financial support. Authors acknowledge QWorld for organizing QIntern 2021. SG thanks Shiladitya Mal for fruitful discussion.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wath, Y., Hariprasad, M., Shah, F. et al. Eavesdropping a quantum key distribution network using sequential quantum unsharp measurement attacks. Eur. Phys. J. Plus 138, 54 (2023). https://doi.org/10.1140/epjp/s13360-023-03664-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1140/epjp/s13360-023-03664-4