Abstract
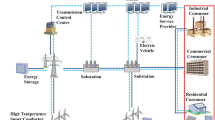
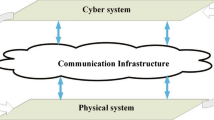
Power grids are among the primary targets for exploitation by cyber-attacks. Modern power and energy systems are controlled and monitored by a network of electrical and communication devices for reliability improvement and resilience enhancement. To increase the capability of remote control and monitoring, Wireless Sensor Networks (WSNs) are widely employed in modern power and energy systems. WSNs, as the foundation of Internet-of-Things (IoT), act as the essential enabling technologies for Cyber-Physical Power and Energy Systems (CPPES). Despite the benefits of WSNs in power and energy systems, such as high efficiency and low deployment costs, their security is a major challenge. In this paper, a systematic review of applications, challenges, and standards of WSNs in CPPES is presented, and various theoretical solutions are discussed. Finally, recommendations for future research are provided.


Similar content being viewed by others
Change history
15 April 2023
The abstract section has been updated.
References
Farooq H et al (2014) Choices available for implementing smart grid communication network. In: 2014 international conference on computer and information science
Feng Z et al (2011) Study on smart grid communications system based on new generation wireless technology. In: 2011 international conference on electronics, communications and control
Fang X et al (2012) Smart grid-the new and improved power grid: a survey. IEEE Comms Surv Tutor 14(4):944–980
Fan Z et al (2013) Smart grid communications: overview of research challenges, solutions, and standardization activities. IEEE Comms Surv Tutor 15(1):21–38
Mohammadi F (2021) Emerging challenges in smart grid cybersecurity enhancement: a review. Energies 14:1380
Mohammadi F, Saif M et al (2022) A review of cyber–resilient smart grid. In: 2022 World Automation Congress (WAC)
Jian PC (2015) Trends in smart power grid communication and networking. In: 2015 international conference on signal processing and communication
Mohammadi F et al (2019) A fast fault detection and identification approach in power distribution systems. In: 2019 International conference on power generation systems and renewable energy technologies
Giustina DD et al (2015) Hybrid communication network for the smart grid: validation of a field test experience. IEEE Trans Power Deliv 30(6):2492–2500
Goel N et al (2015) Smart grid networks: a state of the art review. In: 2015 international conference on signal processing and communication
Mulla A et al (2015) The wireless technologies for smart grid communication: a review. In: 2015 5th international conference on communication systems and network technologies
Kuzlu M et al (2015) Review of communication technologies for smart homes/building applications. In: 2015 IEEE innovative smart grid technologies-Asia
Musleh AS et al (2019) A prediction algorithm to enhance grid resilience toward cyber attacks in WAMCS applications. IEEE Syst J 13(1):710–719
Parvez I et al (2014) Frequency band for HAN and NAN communication in smart grid. In: 2014 IEEE symposium on computational intelligence applications in smart grid
Hiew Y-K et al (2014) Performance of cognitive smart grid communication in home area network. In: 2014 IEEE 2nd international symposium on telecommunications technologies
Aalamifar F et al (2012) Viability of powerline communication for the smart grid. In: 2012 26th Biennial Symp Comms
Hartmann T et al (2014) Generating realistic smart grid communication topologies based on real-data. In: 2014 IEEE Int Conf Smart Grid Comms
Parikh PP et al (2010) Opportunities and challenges of wireless communication technologies for smart grid applications. In: IEEE PES general meeting
Yan Y et al (2013) A survey on smart grid communication infrastructures: motivations, requirements and challenges. IEEE Comms Surv Tutor 15(1):5–20
Saputro N et al (2012) A survey of routing protocols for smart grid communications. Comput Netw 56(11):2742–2771
Gungor VC et al (2013) A survey on smart grid potential applications and communication requirements. IEEE Trans Ind Inform 9(1):28–42
Erol-Kantarci M et al (2011) Wireless multimedia sensor and actor networks for the next generation power grid. Ad Hoc Netw 9(4):542–551
Isa NBM et al (2015) Smart grid technology: communications, power electronics and control system. In: 2015 international conference on sustainable energy engineering and application
Gungor VC et al (2011) Smart grid technologies: communication technologies and standards. IEEE Trans Ind Inform 7(4):529–539
Amin R et al (2012) Smart grid communication using next generation heterogeneous wireless networks. In: 2012 IEEE 3rd international conference on smart grid communications
Bera S et al (2014) Energy-efficient smart metering for green smart grid communication. In: 2014 IEEE global communications conference
Batista NC et al (2014) Layered smart grid architecture approach and field tests by ZigBee technology. Energy Convers Manag 88:49–59
Käbisch S et al (2010) Interconnections and communications of electric vehicles and smart grids. In: 2010 1st IEEE international conference on smart grid communications
Wang B et al (2012) Intelligent DC microgrid with smart grid communications: control strategy consideration and design. IEEE Trans Smart Grid 3(4):2148–2156
Elkhorchani H et al (2013) Development of communication architecture for intelligent energy networks. In: 2013 international conference on electrical engineering and software applications
Elkhorchani H et al (2014) Smart micro grid power with wireless communication architecture. In: 2014 international conference on electrical sciences and technologies in Maghreb
Barroso S (2022) Towards a cyber-physical system for sustainable and smart building: a use case for optimising water consumption on a SmartCampus. J Ambient Intell Humaniz Comput
Darwish A et al (2017) Cyber physical systems design, methodology, and integration: the current status and future outlook. J Ambient Intell Humaniz Comput
Elarabi T et al (2015) Design and simulation of state-of-art Zigbee transmitter for IoT wireless devices. In: 2015 IEEE international symposium on signal processing and information technology
Mohammadi F, Nazri G-A et al (2020) An improved droop-based control strategy for MT-HVDC systems. Electronics 9(1):87
Mohammadi F, Mohammadi-Ivatloo B et al (2021) Robust control strategies for microgrids: a review. IEEE Syst J PP(99):1–12
Mohammadi F, Nazri G-A et al (2020) An improved mixed AC/DC power flow algorithm in hybrid AC/DC grids with MT-HVDC systems. Appl Sci 10(1):297
Abdollahi A et al (2020) Optimal power flow incorporating FACTS devices and stochastic wind power generation using Krill Herd algorithm. Electronics 9:1043
Moradzadeh A et al (2020) Short-term load forecasting of microgrid via hybrid support vector regression and long short-term memory algorithms. Sustainability 12(17):7076
Nguyen TT et al (2020) Optimal scheduling of large-scale wind-hydro-thermal systems with fixed-head short-term model. Appl Sci 10(8):2964
Mohammadi F, Nguyen TT (2020) Optimal placement of TCSC for congestion management and power loss reduction using multi-objective genetic algorithm. Sustainability 12(7):2813
Shojaei AH et al (2020) Multi-objective optimal reactive power planning under load demand and wind power generation uncertainties using ε-constraint method. Appl Sci 10(8):2859
Mohammadi F, Rouzbehi K et al (2021) HVDC circuit breakers: a comprehensive review. IEEE Trans Power Electron 36(12):13726–13739
Moradzadeh A et al (2021) Locating inter-turn faults in transformer windings using isometric feature mapping of frequency response traces. IEEE Trans Ind Inform PP(99):1–1
Elahi O et al (2022) Diagnosing disk-space variation in distribution power transformer windings using group method of data handling artificial neural networks. Energies 15(23):8885
Garcia-Hernandez J (2015) Recent progress in the implementation of AMI projects: standards and communications technologies. In: 2015 International conference on mechatronics, electronics and automotive engineering
Kour R et al (2020) Predictive model for multistage cyber-attack simulation. Int J Syst Assur Eng Manag 11:600–613
Li XX et al (2018) A cloud-terminal-based cyber-physical system architecture for energy efficient machining process optimization. J Ambient Intell Humaniz Comput 10:1
Mohammadi F et al (2019) A real-time cloud-based intelligent car parking system for smart cities. In: 2019 2nd IEEE international conference information communication signal processing
Line MB et al (2011) Cyber security challenges in smart grids. In: 2011 2nd IEEE PES international conference and exhibition on innovative smart grid technologies
Yan Y et al (2012) A survey on cyber security for smart grid communications. IEEE Comms Surv Tutor 14(4):5–20
Jahan S et al (2015) An analysis of smart grid communication infrastructure & cyber security in smart grid. In: 2015 International conference on advances in electrical engineering
Dzung D et al (2005) Security for industrial communication systems. Proc IEEE 93(6):1152–1172
Jameel F (2016) Network security challenges in smart grid. In: 2016 19th international multi-topic conference
Lee E-K et al (2012) Physical layer security in wireless smart grid. IEEE Comms Mag 50(8):90–97
Wang W et al (2013) Cyber security in the smart grid: survey and challenges. Comp Netw 57(5):1344–1371
Shapsough S et al (2015) Smart grid cyber security: challenges and solutions. In: 2015 international conference on smart grid and clean energy technologies
Saponara S et al (2012) Network architecture, security issues, and hardware implementation of a home area network for smart grid. J Comput Netw Comms 2012
Hahn A et al (2013) Cyber-physical security testbeds: architecture, application, and evaluation for smart grid. IEEE Trans Smart Grid 4(2):847–855
Monshi MM et al (2013) A study on the efficient wireless sensor networks for operation monitoring and control in smart grid applications. In: 2013 Proceedings of IEEE Southeastcon
Gungor VC et al (2010) Opportunities and challenges of wireless sensor networks in smart grid. IEEE Trans Ind Electron 57(10):3557
Brak ME, Brak SE, Essaaidi M, Benhaddou D (2014) Wireless sensor network applications in smart grid. In: 2014 International renewable and sustainable energy conference
Zhang Y et al (2012) Wireless sensor network in smart grid: applications and issue. In: 2012 world congress on information and communication technologies
Mohammadi F et al (2020) Emerging issues and challenges with the integration of solar power plants into power systems. In: Solar energy conversion in communities–Springer proceedings in energy. Springer, Cham
Amjad S et al (2010) Review of design considerations and technological challenges for successful development and deployment of plug-in hybrid electric vehicles. Renew Sust Energy Rev 14(3):1104–1110
Gibbons PB et al (2003) IrisNet: an architecture for a worldwide sensor web. IEEE Pervasive Comput 2(4):22–33
Moodley D et al (2006) A new architecture for the sensor web: the SWAP-framework. In: 5th international semantic web conference
Martinez-Sandoval R et al (2014) A comprehensive WSN-based approach to efficiently manage a smart grid. Sensors 14(10):18748–18783
Namboodiri V et al (2014) Toward a secure wireless-based home area network for metering in smart grids. IEEE Systems J 8(2):509–520
Kumar A et al (2021) Cyber physical systems-reliability modelling: critical perspective and its impact. Int J Syst Assur Eng Manag 12:1334–1347
Mishra A et al (2022) Emerging technologies and design aspects of next generation cyber physical system with a smart city application perspective. Int J Syst Assur Eng Manag
Mohammadi F et al (2019) A bidirectional power charging control strategy for plug-in hybrid electric vehicles. Sustainability 11(16):4317
Kim KJ et al (2010) Energy scavenging for energy efficiency in networks and applications. Bell Labs Tech J 15(2):62–72
Sallabi FM et al (2014) Evaluation of ZigBee wireless sensor networks under high power disturbances. IEEE Trans Power Deliv 29(1):13–20
Brak ME et al (2014) Wireless sensor network applications in smart grid. In: 2014 international renewable and sustainable energy conference
Erol-Kantarci M et al (2010) Using wireless sensor networks for energy-aware homes in smart grids. In: The IEEE symposium on computer and communications
Mohammadi F, Rashidzadeh R (2021) An overview of IoT-enabled monitoring and control systems for electric vehicles. IEEE Instrum Meas Mag 24:91–97
Mohammadi F, Rashidzadeh R (2022) Impact of stealthy false data injection attacks on power flow of power transmission lines—a mathematical verification. Int J Electr Power Energy Syst 142:108293
Sadeghian O et al (2022) Protecting power transmission systems against intelligent physical attacks: a critical systematic review. Sustainability 14(19):12345
Brak ME et al (2012) Wireless sensor network in smart grid technology: challenges and opportunities. In: 2012 6th Int. Conf. Sci. Electron., Tech. Info. Telecom.
Mahmood A et al (2015) A review of wireless communications for smart grid. Renew Sust Energy Rev 41:248–260
Do TT et al (2022) A direct reinforcement learning approach for nonautonomous thermoacoustic generator. Math Probl Eng 2022
Ji X-P et al (2020) Optimal attack strategy selection of an autonomous cyber-physical micro-grid based on attack-defense game model. J Ambient Intell Humaniz Comput
Oliveira L et al (2019) MAC layer protocols for internet of things: a survey. Future Internet 11(1):16
Krishnamurthy L et al (2005) Design and deployment of industrial sensor networks: experiences from a semiconductor plant and the North Sea. In: 3rd international conference on embedded networked sensor
Horvath P et al (2015) Efficient evaluation of wireless real-time control networks. Sensors 15(2):4134–4153
Rodenas-Herraiz D et al (2013) Current trends in wireless mesh sensor networks: a review of competing approaches. Sensors 13(5):5958–5995
Kumar S et al. (2022) Sensor network driven novel hybrid model based on feature selection and SVR to predict indoor temperature for energy consumption optimisation in smart buildings. Int J Syst Assur Eng Manag
S. Han, et al (2011) Reliable and real-time communication in industrial wireless mesh networks. In: 2011 17th IEEE real-time and embedded technology and applications symposium
Lu Z et al (2010) Review and evaluation of security threats on the communication networks in the smart grid. In: 2010 IEEE international military communications conference
Dini G et al (2013) On simulative analysis of attack impact in wireless sensor networks. In: 2013 IEEE 18th conference on emerging technologies & factory automation
Radmand P et al. (2010) Taxonomy of wireless sensor network cyber security attacks in the oil and gas industries. In: 2010 24th IEEE international conference on advanced information networking and applications
Jithish J et al (2020) A decision-centric approach for secure and energy-efficient cyber-physical systems. J Ambient Intell Humaniz Comput
Mahmood A et al (2014) Threats in end to end commercial deployments of wireless sensor networks and their cross layer solution. In: 2014 conference on information assurance and cyber security
Barsocchi P et al (2011) A cyber-physical approach to secret key generation in smart environments. J Ambient Intell Humaniz Comput
Neogy S (2015) Security management in wireless sensor networks. In: 2015 international conference on cyber situational awareness, data analytics and assessment
Agrawal S et al (2019) Detection of node capture attack in wireless sensor networks. IEEE Syst J 13(1):238–247
Padmavathi G et al (2009) A survey of attacks, security mechanisms and challenges in wireless sensor networks. Int J Comput Sci Inf Sec 4(1–2):15
Yasir Malik M (2013) An outline of security in wireless sensor networks: threats, countermeasures and implementations. In: Wireless sensor networks and energy efficiency: protocols, routing and management
Shukla J et al (2013) Security threats and defense approaches in wireless sensor networks: an overview. Int J Appl Innov Eng Manag 2:3
Nguyen HL et al (2008) A study of different types of attacks on multicast in mobile ad hoc networks. Ad Hoc Netw 6(1):32–46
Chowdhury M et al (2013) Security issues in wireless sensor networks: a survey. Int J Future Gen Comms Netw 6(5):97–116
Riaz MN et al (2018) Classification of attacks on wireless sensor networks: a survey. Int J Wirel Microw Techn 8(6):15–39
Desnitsky VA et al (2020) Neural network based classification of attacks on wireless sensor networks. In: 2020 IEEE conference of Russian young researchers in electrical and electronic engineering
Lupu T-G (2009) Main types of attacks in wireless sensor networks. Recent Adv Sig Syst 5:1–9
Karlof C et al (2003) Secure routing in wireless sensor networks: attacks and countermeasures. Ad Hoc Netw 1(2–3):293–315
Sinha P et al (2017) Security vulnerabilities, attacks and countermeasures in wireless sensor networks at various layers of OSI reference model: a survey. In: 2017 international conference on communication and signal processing
Chen X et al (2009) Sensor network security: a survey. IEEE Comms Surv Tutor 11(2):52–73
Mohammadi S et al (2011) A comparison of link layer attacks on wireless sensor networks. Int J Appl Graph Theory Wirel Ad Hoc Netw Sens Netw 3(1):69–84
Can O et al (2015) A survey of intrusion detection systems in wireless sensor networks. In: 2015 6th international conference on modeling, simulation, and applied optimization
Rajkumar VBA et al (2014) Security attacks and its countermeasures in wireless sensor networks. Int J Eng Res Apps 4(10):4–15
Tamil K et al (2010) Security vulnerabilities in wireless sensor networks: a survey. J Inf Assur Sec 5(1):31–44
Butun I et al (2014) A survey of intrusion detection systems in wireless sensor networks. IEEE Commun Surv Tutor 16(1):4–30
Granjal J et al (2015) Security for the internet of things: a survey of existing protocols and open research issues. IEEE Comms Surv Tutor 17(3):1294–1312
Diaz A et al (1932) Simulation of attacks for security in wireless sensor network. Sensors 16(11):2016
Sun C-C et al (2016) Cyber-physical system security of a power grid: state-of-the-art. Electronics 5(3):40
Wang Y et al (2016) Detection of intelligent intruders in wireless sensor networks. Future Internet 8(1):2
Chelli K (2015) Security issues in wireless sensor networks: attacks and countermeasures. In: Proceedings of world congress on engineering, vol 1
Zhang Y et al (2015) A network topology control and identity authentication protocol with support for movable sensor nodes. Sensors 15(12):29958–29969
Di Pietro R et al (2004) Connectivity properties of secure wireless sensor networks. In: 2nd ACM workshop sec. ad‐hoc and sensor network
Di Pietro R et al (2008) Redoubtable sensor networks. ACM Trans Inf Syst Sec
Yagan O (2012) Performance of the Eschenauer-Gligor key distribution scheme under an ON/OFF channel. IEEE Trans Inf Theory 58(6):3821–3835
Jutla CS (2001) Encryption modes with almost free message integrity. International conference on the theory and applications of cryptographic techniques
Blackburn SR et al (2008) Connectivity of the uniform random intersection graph. Discrete Math 309(16):5130–5140
Bloznelis M (2013) Degree and clustering coefficient in sparse random intersection graphs. Ann Appl Probab 23(3):1254–1289
Krishnan BS et al (2013) On connectivity thresholds in superposition of random key graphs on random geometric graphs. In: 2013 IEEE international symposium on information theory
Krzywdziński K et al (2012) Geometric graphs with randomly deleted edges—connectivity and routing protocols. In: International symposium on mathematical foundations of computer science
Ahmed M et al (2009) NIDS: a network based approach to intrusion detection and prevention. In: 2009 international association of computer science and information technology
Yousufi RM et al (2017) A network-based intrusion detection and prevention system with multi-mode counteractions. In: 2017 International conference on innovations in information, embedded and communication systems
Wattanapongsakorn N et al (2012) A practical network-based intrusion detection and prevention system. In: 2012 IEEE 11th international conference on trust, security and privacy in computing and communications
Zhang L et al (2016) A survey on security and privacy in emerging sensor networks: from viewpoint of close-loop. Sensors 16(4):443
Salehian S et al (2012) Energy-efficient intrusion detection in wireless sensor network. In: 2012 international conference on cyber security, cyber warfare and digital forensic
Farraj A et al (2016) A game-theoretic analysis of cyber switching attacks and mitigation in smart grid systems. IEEE Trans Smart Grid 7(4):1846–1855
Ten C-W et al (2010) Cybersecurity for critical infrastructures: attack and defense modeling. IEEE Trans Syst Man Cybernet Part A Syst Hum 40(4):17
Darwish I et al (2015) Experimental and theoretical modeling of DNP3 attacks in smart grids. In: 2015 36th IEEE Sarnoff symposium
Patil A et al (2022) Data-driven approaches for impending fault detection of industrial systems: a review. Int J Syst Assur Eng Manag
Albashear AMM et al (2018) Detection of man-in-the-middle attacks by using the TCP retransmission timeout: key compromise impersonation attack as study case. In: 2018 international conference computing, control, electrical, electronics engineering
Yang X et al (2017) Toward a Gaussian-mixture model-based detection scheme against data integrity attacks in the smart grid. IEEE Internet Things J 4(1):674
Zhou Y et al (2019) Robust energy-efficient resource allocation for IoT-powered cyber-physical-social smart systems with virtualization. IEEE Internet Things J 6(2):2413–2426
Li F et al (2019) System statistics learning-based IoT security: feasibility and suitability. IEEE Internet Things J 6(4):6396–6403
Tian J et al (2021) TOTAL: optimal protection strategy against perfect and imperfect false data injection attacks on power grid cyber–physical systems. IEEE Internet Things J 8(2):1001–1015
Zou T et al (2020) Smart grids cyber-physical security: Parameter correction model against unbalanced false data injection attacks. Electr Power Syst Res 187:99
Rivas AEL et al (2020) Faults in smart grid systems: Monitoring, detection and classification. Electr Power Syst Res 189:106602
Bowker D et al (2020) The role of Blockchain technologies in power markets. In: CIGRE WG C5.30 Technical Brochure
Mohammadi F, Sanjari M et al (2022) A real-time Blockchain-based state estimation system for battery energy storage systems. In: 2022 IEEE Kansas power and energy conference (KPEC)
Mohammadi F, Sanjari M et al (2022) A real-time Blockchain-based multifunctional integrated smart metering system. In: 2022 IEEE Kansas Power and Energy Conference (KPEC)
Bowker D et al (2022) The applications of Blockchain technologies to electricity markets. In: CIGRE session
Mohammadi F, Saif M (2023) Blockchain technology in modern power systems: a systematic review. IEEE Syst Man Cybernet Mag
Bowker D et al (2023) Trading electricity with Blockchain systems. In: CIGRE WG C5.33 Technical Brochure
Funding
This research received no external funding.
Author information
Authors and Affiliations
Contributions
The authors confirm contributions to the paper as follows: TTN was responsible for conceptualization, review and editing; and FM was responsible for conceptualization, methodology, formal analysis and investigation, collecting resources, data analysis, writing—original draft preparation, and writing—review and editing. Both authors have read and agreed to the current version of the manuscript. Both authors have read and agreed to the current version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Ethical approval
The research has not been submitted to more than one journal for simultaneous consideration. The submitted work is original and has not been published elsewhere in any form or language (partially or in full). This research has not been split up into several parts to increase the quantity of submissions and submitted to various journals or to one journal over time. Results are presented clearly, honestly, and without fabrication and falsification or inappropriate data manipulation (including image-based manipulation). No data, text, or theories by others are presented and if words have been taken from other sources, proper referencing has been given in the references section.
Informed consent
This research does not involve human and/or animals participants.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Nguyen, T.T., Mohammadi, F. Cyber-Physical Power and Energy Systems with Wireless Sensor Networks: A Systematic Review. J. Electr. Eng. Technol. 18, 4353–4365 (2023). https://doi.org/10.1007/s42835-023-01482-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s42835-023-01482-3