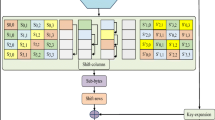
Abstract
In this digital information era, data transmitted over internet is vulnerable to several types of attacks. To preserve our information over internet, it is necessary to use some cryptographic methods. advanced encryption standard is a strong symmetric, non-fiestel cryptographic algorithm which preserves the information transmitted in internet from piracy or attacks. In this research article, a new and an efficient key dependent AES algorithm is presented for securing the data over internet or digitally stored in any remote location. This proposed work gives better avalanche effect and strict avalanche effect on comparing with the original existing AES algorithm. Results of the proposed algorithm are obtained after testing 1000 pairs of samples of different secret key. And it shows that 58% of the times, new proposed algorithm have better avalanche effect than the existing algorithm.


Similar content being viewed by others
References
National Institute of Standards and Technology. Advanced Encryption Standard (AES). Federal Information Processing Standards Publications—FIPS 197. http: //csrc.nist.gov/publications/fips/ fips197/fips-197.pdf. November 2001
Daemen J, Rijmen V (2002) The design of Rijndael. Springer, Berlin
Stallings W (2014) Cryptography and network security, 5th edn. Pearson Education Inc, London
Juremi J et al (2012) Enhancing advanced encryption standard s-box generation based on round key. International Journal of Cyber-Security and Digital Forensics 1(3):183–188
Krishnamurthy GN et al (2011) Study of effect of removal of shiftrows and mixcolumns stages of AES and AES-KDS on their encryption quality and hence security in international scholarly and scientific research & innovation 5(2):143–156
Mathew SK, Sheikh F, Kounavis M, Gueron S, Agarwal A, Hsu SK et al (2011) 53 Gbps GF(24) native composite-field AES-encrypt/decrypt accelerator for content-protection in 45 nm high performance microprocessors. IEEE J Solid State Circuits 46(4):767–776
Wadi SM, Zainal N (2013) Rapid encryption method based on AES algorithm for grey scale HD image encryption in Elsevier. In: Proceedings of the 4th international conference on electrical engineering and informatics (ICEEI 2013), vol 11, pp 51–56
Zhang X, Parhi KK (2006) On the optimum constructions of composite field for the AES algorithm. IEEE Trans Circuits Syst 53(10):1153–1157
Rahimunnisa K, Karthigaikumar P, Rasheed S, Jayakumar J (2012) FPGA implementation of AES algorithm for high throughput using folded parallel architecture. Secur Commun Netw 7(11):2225–2236
Granado Criado JM, Vega Rodriguez MA, Sanchez Perez JM, Gomez Pulido JA (2010) A new methodology to implement the AES algorithm using partial and dynamic reconfiguration. Integr VLSI J 43:72–80
Jyrwa B, Paily R (2009) An area-throughput efficient FPGA implementation of block cipher aes algorithm. In: International conference on advances in computing, control and telecommunication technologies, pp 328–332
Morioka S, Satoh A (2003) An optimized s-box circuit architecture for low power AES design. Springer, Berlin
Koradia VC et al (2013) Modification in advanced encryption standard. J Inf Knowl Res Comput Eng 2(2):356–358
Oyshee B et al (2012) An optimized s-box for advanced encryption standard (AES) design. In: The proceedings of 2012 international conference on advances in computing and communications, pp 154–157.
Manoj Kumar T, Karthigaikumar P (2018) FPGA implementation of an optimized key expansion module of AES algorithm for secure transmission of personal ECG signals. Des Autom Embed Syst 22(1–2):13–24
Manojkumar T, Karthigaikumar P, Ramachandran V (2019) An optimized s-box circuit for high speed AES design with enhanced PPRM architecture to secure mammographic images. J Med Syst 43:31
Karthigaikumar P, Christy NA, Mangai NMS (2015) PSP CO2: an efficient hardware architecture for AES algorithm for high throughput. Wirel Personal Commun 85(1):305–323
Rahimunnisa K, Karthigaikumar P, Christy N, Kumar S, Jayakumar J (2013) PSP: parallel sub-pipelined architecture for high throughput AES on FPGA and ASIC. Eur J Comput Sci 3(4):173–186
Mangard S, Aigner M, Moninikus S (2003) A highly regular and scalable AES hardware architecture. IEEE Trans Comput 52(4):483–491
Abuelyman ES, Alsehibani AAS (2008) An optimized implementation of the s-box using residue of prime numbers. Int J Comput Sci Netw Secur 8(4):304–309
Itoh T, Tsujii S (1988) A fast algorithm for computing multiplicative inverses in GF(2m) using normal bases. Inf Comput 78(3):171–177
Good T, Benaissa M (2006) Very small FPGA application-specific instruction processor for AES. IEEE Trans Circuits Syst I Regul Pap 53(7):1477–1486
Good T, Benaissa M (2010) 692-nW advanced encryption standard (AES) on a 0.13-m CMOS. IEEE Trans Very Large Scale Integr VLSI Syst 18(12):1753–1757
Huang J, Lai X (2012) Transposition of AES key schedule. Int Assoc Cryptol Res 260:1–13
Paul A, Victoire TAA, Jeyakumar AE (2003) Particle swarm approach for retiming in VLSI. In: IEEE 46th midwest symposium on 3 circuits and systems, 2003, pp 1532–1535.
Helion. www.heliontech.com.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Manoj Kumar, T., Karthigaikumar, P. A novel method of improvement in advanced encryption standard algorithm with dynamic shift rows, sub byte and mixcolumn operations for the secure communication. Int. j. inf. tecnol. 12, 825–830 (2020). https://doi.org/10.1007/s41870-020-00465-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-020-00465-1