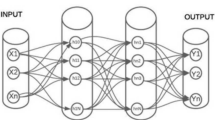
Abstract
Honeypots and data mining are the major methods used as a safeguard of assets or for classifying the data. Each technique has positives and disadvantages of its own and is best applied in a particular position. Hybrid approach uses aspects of both techniques to upgrade performance and shortcomings. In this paper, we propose a hybrid approach based on Honeypot and Data Mining based Support Vector Machine technique, implemented in the dot net framework for preventing Denial of Service Attack. The proposed approach, HoneyDos tested in three interfaces. This paper presents an empirical comparison of the hybrid approach to the earlier methods used for preventing Denial of Service attack and draw useful conclusions upon their performance.



Similar content being viewed by others
References
Selvaraj R, Kuthadi VM, Marwala T (2016) Ant based distributed denial of service detection technique using roaming virtual honeypots. IET J. https://doi.org/10.1049/iet-com.2015.0497
Djanali S, Arunanto FX, Pratomo AB et al (2014) Aggressive web application honeypot for exposing attacker’s identity. 1st International Conference on Information Technology 212–216
Buvaneswari M, Subha T (2013) IHONEYCOL: A distributed collaborative approach for mitigation of Ddos attack. International Conference on Information Communication and Embedded Systems (ICICES). https://doi.org/10.1109/icices.2013.6508281
Akiyama M, Kawakoya Y, Hariu T (2012) Scalable and performance-efficient client honeypot on high interaction system. 12th International Symposium on Applications and the Internet 40–50. https://doi.org/10.1109/saint.2012.15
Almotairi S, Clark A, Mohay G, Zimmermann J (2009) A technique for detecting new attacks in low-interaction honeypot traffic. Fourth International Conference on Internet Monitoring and Protection, pp 7–13. https://doi.org/10.1109/icimp.2009.9
Zhan Z, Xu M, Xu S (2013) Characterizing honeypot-captured cyber attacks: statistical framework and case study. IEEE Trans Inf Forens Secur 8(11):1775–1798
Agarwal P.K., Gupta B.B., Jain Satbir (2011) SVM Based scheme for Predicting Number of Zombies in a DDoS Attack. In: European Intelligence and Security Informatics Conference, 178–182. https://doi.org/10.1109/EISIC.2011.19
Vargas IRJS, Kleinschmidt JH (2015) Capture and analysis of malicious Traffic in VoIP environments using a low interaction honeypot. IEEE Latin Am Trans 13(3):777–783
Singh G, Sharma S, Singh P (2013) Design and develop a honeypot for small scale organization. Int J Innov Technol Explor Eng (IJITEE) 2(3):170–174
Wang J, Zeng J (2011) Construction of large scale honeynet based on honeyd. Advanced in Control Engineering and Information Science, Elsevier, pp 3260–3264
Li Zhu Yu, Ruixi Gaun Xiaohong (2007) Accurate classification of the internet traffic based on the SVM method. IEEE Int Conf. https://doi.org/10.1109/ICC.2007.231
Poongothai M, Sathyakala M (2012) Simulation and Analysis of DDoS Attacks. International Conference on Emerging Trends in Science, Engineering and Technology 78–85
Leu F-Y, Li Z-Y (2009) Detecting DoS and DDoS attacks by using an intrusion detection and remote prevention system. Fifth International Conference on Information Assurance and Security. https://doi.org/10.1109/ias.2009.294
Garcia-Teodoro P, Diaz-Verdejo J et al (2009) Anomaly-based network intrusion detection: techniques systems and challenges. Elsevier J. Comput Secur 28:18–28
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sharma, P., Nagpal, B. HONEYDOS: a hybrid approach using data mining and honeypot to counter denial of service attack and malicious packets. Int. j. inf. tecnol. 14, 837–846 (2022). https://doi.org/10.1007/s41870-018-0182-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-018-0182-4