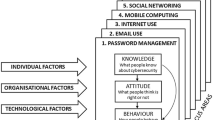
Abstract
The increasing interest arising around the field of security becomes a pragmatic issue when we consider the behavior of the employees of large organizations involved in critical infrastructures. As a matter of common knowledge, the human factor is the weakest link in the security chain. This introduces the topic of the security awareness of employees in large organizations. In this paper, we describe the results of a survey designed and delivered to large organizations in Europe, to understand how the topic of security is perceived and implemented and which are the security awareness initiatives held by organizations to instruct their employees. Moreover, we evaluate 23 methods to increase the security awareness, on the basis of several indicators describing their effectiveness, cost, implementation time, and other relevant aspects, to emphasize their pros and cons and their areas of applicability. Finally, we describe a tool developed to support the design of a security awareness campaign respecting the constraints imposed by the needs of each organization.














Similar content being viewed by others
Notes
Responders are allowed to provide fractional points.
References
Al-Awadi M (2009) A study of employees’ attitudes towards organisational information security policies in the UK and Oman (Doctoral dissertation, University of Glasgow)
Allport GW (1935) Attitudes. In: Murchison C (ed) Handbook of social psychology. Clark University Press, Worcester, pp 789–844
Bullock J, Haddow G, Coppola DP (2011) Introduction to homeland security: principles of all-hazards risk management. Butterworth-Heinemann, Oxford
Cacciabue PC (2004) Human error risk management for engineering systems: a methodology for design, safety assessment, accident investigation and training. Reliab Eng Syst Saf 83(2):229–240
Cobbina JE, Nalla MK, Bender KA (2013) Security officers’ attitudes towards training and their work environment. Secur J 29:385–399
Council ECR (2004) The economic impacts of the August 2003 blackout. Washington, DC
De Maggio MC, Mastrapasqua M, Setola R (2015) The Professional Figure of the Security Liaison Officer in the Council Directive 2008/114/EC. In: International Conference on Critical Information Infrastructures Security (pp. 211-222). Springer International Publishing
Dekker S (2004) Ten questions about human error: A new view of human factors and system safety. CRC Press, Boca Roton
Dubois D, Prade H (1982) A class of fuzzy measures based on triangular norms: a general framework for the combination of uncertain information. Int J Gen Syst 8(1):43–61
Fishbein M, Ajzen I (1975) Belief, attitude, intention, and behavior: an introduction to theory and research. Mass: Addison-Wesley, Boston
Greitzer FL, Kangas LJ, Noonan CF, Brown CR, Ferryman T (2013) Psychosocial modeling of insider threat risk based on behavioral and word use analysis. e-Serv J 9(1):106–138
Hills M, Anjali A (2017) A human factors contribution to countering insider threats: practical prospects from a novel approach to warning and avoiding. Secur J 30(1):142–152
Huston T (2001) Security issues for implementation of e-medical records. Commun ACM 44(9):89–94
Kirschenbaum AA, Rapaport C (2012) Does training improve security decisions? A case study of airports. Secur J 30:184–198
Krombholz K et al (2015) Advanced social engineering attacks. J Inform Secur Appl 22:113–122
Liscouski B, Elliot W (2004) Final report on the august 14, 2003 blackout in the United States and Canada: Causes and recommendations. A report to US Department of Energy, 40(4)
Manzo J (2009) Security officers’ perspectives on training 1. Can J Criminol Criml Justice 51(3):381–410
Pastor V, Díaz G, Castro M (2010) State-of-the-art simulation systems for information security education, training and awareness. In: Education Engineering (EDUCON), 2010 IEEE. IEEE, pp 1907–1916
Perrow C (2011) Normal accidents: Living with high risk technologies. Princeton University Press, Princeton
Ryan RM, Deci EL (2000) Self-determination theory and the facilitation of intrinsic motivation, social development, and well-being. Am Psychol 55(1):68
Saaty TL (1988) What is the analytic hierarchy process? In: Mitra G, Greenberg HJ, Lootsma FA, Rijkaert MJ, Zimmermann HJ (eds) Mathematical models for decision support. Springer, Berlin, Heidelberg, pp 109–121
Schein EH (2006) Organizational culture and leadership, vol 356. Wiley, Hoboken
Setola R, Mastrapasqua M, Tesei M, De Maggio MC, Corradini I, Pantaleo C, Capitello ME, De Simio F (2015) Study on security awareness in gas infrastructure. Final report
Siponen MT (2000) A conceptual foundation for organizational information security awareness. Inform Manag Comput Secur 8(1):31–41
Stackpole B, Oksendahl E (2010) Security strategy: from requirements to reality. CRC Press, Boca Roton
Swain AD and Guttmann HE (1983) Handbook of human-reliability analysis with emphasis on nuclear power plant applications. Final report (No. NUREG/CR-1278; SAND-80-0200). Sandia National Labs., Albuquerque, NM (USA)
Weinberg A, Kaplan J, Bailey T (2014) The $3,000 bn threat from cyber attacks. Financial, Times, p 28
Workman M (2007) Gaining access with social engineering: an empirical study of the threat. Inform Syst Secur 16(6):315–331
Acknowledgements
The authors would like to thank the Security Study Group of GIE—Gas Infrastructure Europe—for the commitment and the support.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
De Maggio, M.C., Mastrapasqua, M., Tesei, M. et al. How to Improve the Security Awareness in Complex Organizations. Eur J Secur Res 4, 33–49 (2019). https://doi.org/10.1007/s41125-017-0028-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41125-017-0028-2