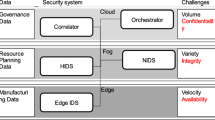
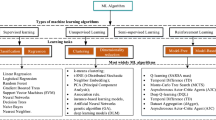
Abstract
Cybersecurity is a critical issue in additive manufacturing (AM), since AM relies on digital files and network connectivity. In this work, we first review several major cybersecurity risks and mitigation strategies in AM industry. Based on the review, we propose a new framework to detect threats and assess vulnerabilities in AM process. We also suggest a new technique of encrypting 3D model information using 2D images which may provide enhanced cybersecurity in AM process.







Similar content being viewed by others
References
Brown J, Ezzard J, Goldenberg S, Haid J (2017) 3D opportunity and cyber risk management. https://dupress.deloitte.com/dup-us-en/focus/3d-opportunity/3d-printing-cyber-risk-management.html
M. Cotteleer, Joyce J (2014) 3D opportunity: Additive manufacturing paths to performance, innovation, and growth,” Deloitte Review 14 http://dupress.com/articles/dr14-3d-opportunity/
D. Papadimitriou (2009) Future internet: the cross-ETP vision document. http://www.future-internet.eu/fileadmin/documents/reports/Cross-ETPs_FI_Vision_Document_v1_0.pdf Accessed 26 Dec 2017
X Yao, Z-T Lian, Y Yang, Jin H (2014) Wisdom manufacturing:new humans-computers-things collaborative manufacturing model. Comp Int Manuf Syst 20:1490–1498
RM Lee, MJ Assante, Conway T (2014) German steel mill cyber attack—SANS ICS https://ics.sans.org/media/ICS-CPPE-case-Study-2-German-Steelworks_Facility.pdf
LF Cómbita, J Giraldo, AA Cárdenas, Quijano N (2015) Response and reconfiguration of cyber-physical control systems: A survey. In: 2015 IEEE 2nd Colombian Conference on Automatic Control (CCAC). pp 1–6
Z DeSmit, AE Elhabashy, LJ Wells, Camelio JA (2016) Cyber-physical vulnerability assessment in manufacturing systems. Procedia Manuf 5:1060–1074 /01/01/ 2016.
LD Sturm, CB Williams, JA Camelio, J White, Parker R (2017) Cyber-physical vulnerabilities in additive manufacturing systems: a case study attack on the.STL file with human subjects. J Manuf Syst 44:154–164 /07/01/ 2017.
ESET (2017) ACAD/Medre.A 10000′s of AutoCAD Designs leaked in suspected industrial espionage. https://www.welivesecurity.com/media_files/white-papers/ESET_ACAD_Medre_A_whitepaper.pdf
SB Moore, WB Glisson, Yampolskiy M (2017) Implications of malicious 3D printer firmware. In: Proceedings of the 50th Hawaii International Conference on System Sciences (HICSS), pp. 6089–6098
S Moore, P Armstrong, T McDonald, Yampolskiy M, (2016) Vulnerability analysis of desktop 3D printer software. In: 2016 resilience week (RWS), pp 46–51
E Zeltmann, N Gupta, NG Tsoutsos, M Maniatakos, J Rajendran, Karri R (2016) Manufacturing and Security Challenges in 3D Printing JOM 68, pp 1872–1881
H Zhang, L Cai, M Golub, Y Zhang, X Yang, K Schlarman et al (2017) Tensile, creep, and fatigue behaviors of 3D printed acrylonitrile butadiene styrene. J Mater Eng Perform. https://doi.org/10.1007/s11665-017-2961-1-7
M Yampolskiy, A Skjellum, M Kretzschmar, RA Overfelt, KR Sloan, Yasinsac A (2016) Using 3D printers as weapons. Int J Crit Infrastruct Prot 14:58–71 /09/01/ 2016.
SR Chhetri, A Canedo, Faruque MAA (2016) KCAD: kinetic cyber-attack detection method for cyber-physical additive manufacturing systems. In: 2016 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), pp. 1–8
A Sinha, A Unmesh, Q Huang, Ramani K (2017) SurfNet: Generating 3D shape surfaces using deep residual networks (arXiv170304079S)
Acknowledgements
JZ acknowledges the financial support provided by Walmart Foundation (project title: Optimal Plastic Injection Molding Tooling Design and Production through Advanced Additive Manufacturing).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Rights and permissions
About this article
Cite this article
Padmanabhan, A., Zhang, J. Cybersecurity risks and mitigation strategies in additive manufacturing. Prog Addit Manuf 3, 87–93 (2018). https://doi.org/10.1007/s40964-017-0036-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40964-017-0036-9