Abstract
This paper presents new speed records for multiprecision multiplication on the AVR ATmega family of 8-bit microcontrollers. For example, our software takes only 1,969 cycles for the multiplication of two 160-bit integers; this is more than 15 % faster than that demonstrated in previous work. For 256-bit inputs, our software is not only the first to break through the 6,000-cycle barrier; with only 4,771 cycles it also breaks through the 5,000-cycle barrier and is more than 21 % faster than previous work. We achieve these speed records by carefully optimizing the Karatsuba multiplication technique for AVR ATmega. One might expect that subquadratic-complexity Karatsuba multiplication is only faster than algorithms with quadratic complexity for large inputs. This paper shows that it is in fact faster than fully unrolled product-scanning multiplication already for surprisingly small inputs, starting at 48 bits. Our results thus make Karatsuba multiplication the method of choice for high-performance implementations of elliptic-curve cryptography on AVR ATmega microcontrollers.
Similar content being viewed by others
Notes
The source code is available at http://cryptojedi.org/crypto/#avrmul and at http://mhutter.org/research/avr/#karatsuba.
References
Barrett, P.: Implementing the Rivest Shamir and Adleman public key encryption algorithm on a standard digital signal processor. In: Andrew, O.M. (ed.) Advances in Cryptology—CRYPTO ’86. Lecture Notes in Computer Science, vol. 263, pp. 311–323. Springer, Berlin (1987)
Bernstein, D.J.: Batch binary Edwards. In: Halevi, S. (ed.) Advances in Cryptology—CRYPTO 2009, vol. 5677 of Lecture Notes in Computer Science, pp. 317–336. Springer, Berlin (2009). http://cr.yp.to/papers.html#bbe
Brent, R., Zimmermann, P.: Modern Computer Arithmetic. Cambridge University Press (2010). http://www.loria.fr/~zimmerma/mca/pub226.html
Comba, P.G.: Exponentiation cryptosystems on the IBM PC. IBM Syst. J. 29(4), 526–538 (1990). http://lyle.smu.edu/~seidel/courses/cse8351/papers/CombaCRYPTO.pdf
Fürer, M.: Faster integer multiplication. SIAM J. Comput. 39(3), 979–1005 (2009)
Gouvêa, C.P. L., López, J.: Software implementation of pairing-based cryptography on sensor networks using the MSP430 microcontroller. In: Bimal Roy, N.S. (ed.) Progress in Cryptology—INDOCRYPT 2009, vol. 5922 of Lecture Notes in Computer Science, pp. 248–262. Springer, Berlin (2009). http://conradoplg.cryptoland.net/files/2010/12/indocrypt09.pdf
Gouvêa, C.P.L., Oliveira, L.B., López, J.: Efficient software implementation of public-key cryptography on sensor networks using the MSP430X microcontroller. J. Cryptogr. Eng. 2(1), 19–29 (2012). http://conradoplg.cryptoland.net/files/2010/12/jcen12.pdf
Großschädl, J., Avanzi, R.M., Savaş, E., Tillich, S.: Energy-efficient software implementation of long integer modular arithmetic. In: Rao, J.R., Sunar, B. (eds.) Cryptographic Hardware and Embedded Systems—CHES 2005, vol. 3659 of Lecture Notes in Computer Science, pp. 75–90. Springer, Berlin (2005). www.iacr.org/archive/ches2005/006.pdf
Gura, N., Patel, A., Wander, A., Eberle, H., Shantz, S.C.: Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In: Joye, M. (ed.) Cryptographic Hardware and Embedded Systems—CHES 2004, vol. 3156 of Lecture Notes in Computer Science, pp. 119–132. Springer, Berlin (2004). www.iacr.org/archive/ches2004/31560117/31560117.pdf
Gura, N., Spracklen, L.A.: Hybrid multi-precision multiplication. United States Patent 7650374, 2010. Application filed Nov. 23 (2004). http://www.freepatentsonline.com/7650374.html
Hutter, M., Schwabe, P.: NaCl on 8-bit AVR microcontrollers. In: Youssef, A., Nitaj, A. (eds) Progress in Cryptology—AFRICACRYPT 2013, vol. 7918 of Lecture Notes in Computer Science, pp. 156–172. Springer, Berlin (2013). http://cryptojedi.org/papers/#avrnacl
Hutter, M., Wenger, E.: Fast multi-precision multiplication for public-key cryptography on embedded microprocessors. In: Preneel, B., Takagi, T. (eds) Cryptographic Hardware and Embedded Systems—CHES 2011, vol. 6917 of Lecture Notes in Computer Science, pp. 459–474. Springer, Berlin (2011). http://mhutter.org/papers/Hutter2011FastMultiPrecision.pdf
Hutter, M., Wenger, E.: Multiplication of large operands. WIPO Patent Application WO/2013/044276, 2013. Application filed Sep. 27 (2011). http://www.freepatentsonline.com/WO2013044276A1.html
Karatsuba, A., Ofman, Y.: Multiplication of multidigit numbers on automata. Sov. Phys. Doklady, 7, 595–596 (1963). Translated from Doklady Akademii Nauk SSSR, 145(2), pp. 293–294, July 1962. Scanned version on http://cr.yp.to/bib/1963/karatsuba.html
Karatsuba, A.A.: The complexity of computations. Proc. Steklov Inst. Math. 211, 169–183 (1995). http://www.ccas.ru/personal/karatsuba/divcen.pdf
Lederer, C., Mader, R., Koschuch, M., Großschädl, J., Szekely, A., Tillich, S.: Energy-efficient implementation of ECDH key exchange for wireless sensor networks. In: Markowitch, O., Bilas, A., Hoepman, J.-H., Mitchell, C.J., Quisquater, J.-J. (eds) Information Security Theory and Practice, vol. 5746 of Lecture Notes in Computer Science, pp. 112–127. Springer, Berlin (2009). http://www.cs.bris.ac.uk/Publications/Papers/2001061.pdf
Liu, Z., Großschädl, J.: New speed records for Montgomery modular multiplication on 8-bit AVR microcontrollers. Cryptology ePrint Archive, Report 2013/882 (2013). https://eprint.iacr.org/2013/882/
Liu, Z., Großschädl, J., Kizhvatov, I.: Efficient and side-channel resistant RSA implementation for 8-bit AVR microcontrollers. In: Proceedings of the 1st International Workshop on the Security of the Internet of Things—SECIoT’10 (2010). https://www.nics.uma.es/seciot10/files/pdf/liu_seciot10_paper.pdf
Liu, Z., Seo, H., Großschädl, J., Kim, H.: Efficient implementation of NIST-compliant elliptic curve cryptography for sensor nodes. In: Qing, S., Zhou, J., Liu, D. (eds) Information and Communications Security, vol. 8233 of Lecture Notes in Computer Science, pp. 302–317. Springer, Berlin (2013). http://orbilu.uni.lu/bitstream/10993/12934/1/ICICS2013.pdf
Patwardhan, K.S., Naimpally, S.A., Singh S.L.: Lilavati of Bhāskarācārya. Motilal Banarsidass Publishers (2001). http://books.google.com/books?id=AoX5q7JjM2kC
Schönhage, A., Strassen, V.: Schnelle Multiplikation großer Zahlen. Computing 7(3), 281–292 (1971)
Scott, M., Szczechowiak, P.: Optimizing multiprecision multiplication for public key cryptography. Cryptology ePrint Archive, Report 2007/299 (2007). https://eprint.iacr.org/2007/299/
Seo, H., Kim, H.: Multi-precision multiplication for public-key cryptography on embedded microprocessors. In: MotiYung, D.H.L. (ed) Information Security Applications, vol. 7690 of Lecture Notes in Computer Science, pp. 55–67. Springer, Berlin (2012). http://isaa.sch.ac.kr/wisa2012/%EB%85%BC%EB%AC%B8/Session%202/1-130_Multi-precision%20Multiplication%20for%20Public-Key%20Cryptography%20on%20Embedded%20Microprocessors.pdf
Seo, H., Kim, H.: Optimized multi-precision multiplication for public-key cryptography on embedded microprocessors. Int. J. Comput. Commun. Eng. 2(3), 255–259 (2013). http://www.ijcce.org/papers/183-J034.pdf
Sigler, L.E.: Fibonacci’s Liber Abaci–Leonardo Pisano’s Book of Calculation. Springer, New York (2003). http://books.google.com/books?id=PilhoGJeKBUC
Swetz, F.J.: Capitalism and Arithmetic: the new math of the 15th century. Open Court (1987)
Toom, A.L.: The complexity of a scheme of functional elements realizing the multiplication of integers. Sov. Math. Dokl. 3, 714–716 (1963).www.de.ufpe.br/~toom/my-articles/engmat/MULT-E.PDF
Yen, S.-M., Joye, M.: Checking before output may not be enough against fault-based cryptanalysis. IEEE Trans. Comput. 49, 967–970 (2000). http://joye.site88.net/papers/YJ00chkb.pdf
Author information
Authors and Affiliations
Corresponding author
Additional information
The work was done while Michael Hutter was with Graz University of Technology, Austria. This work was supported by the Austrian Science Fund (FWF) under the Grant number TRP251-N23, by the Netherlands Organisation for Scientific Research (NWO) through Veni 2013 project 13114, and by the European Cooperation in Science and Technology (COST) Action IC1204 (Trustworthy Manufacturing and Utilization of Secure Devices-TRUDEVICE). Part of the work was done while the authors visited Academia Sinica, Taiwan. They wish to thank Bo-Yin Yang for his hospitality. Permanent ID of this document: 102fe77c6d1003e5694ac04543a52410.
Appendices
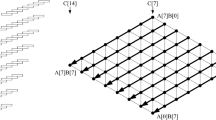
Appendix A: Karatsuba multiplication of two \(48\)-bit numbers

Appendix B: Small multiprecision multiplications




Rights and permissions
About this article
Cite this article
Hutter, M., Schwabe, P. Multiprecision multiplication on AVR revisited. J Cryptogr Eng 5, 201–214 (2015). https://doi.org/10.1007/s13389-015-0093-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13389-015-0093-2