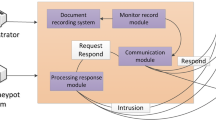
Abstract
As a traditional and impactful proactive defense technology, honeynet is used by network defender to imitate normal production process, which traps and captures the behavior of attackers in order to analyze the methods and tools, and also to forecast the attacking intention and situation. However, the data obtained from honeynet usually have problems such as multiple types, high redundancy and low semantics level, which make it difficult to indicate network security situation directly. Through studying biological immune mechanism, a honeynet security warning model based on Danger Theory (an “SWIM”) is proposed. By utilizing the dendritic cell algorithm, this article discusses in detail the definition and mapping for input signals, capture of honeynet antigens, fundamental analysis for output signals, as well as the security early warning. The simulation results show that, in the face of typical network attacks, SWIM accurately reflects the attacking strength, which is capable of implementing the efficient network early warning.
Similar content being viewed by others
References
Spitzner, L.: The honeynet project: trapping the hackers. IEEE Secur. Priv. 1(2), 15–23 (2003)
Olagunju A.O.; Samu F.: In search of effective honeypot and honeynet systems for real-time intrusion detection and prevention. In: Proceedings of the 5th Annual Conference on Research in Information Technology. Boston, pp. 41–46 (2016)
Thonnarda, O.; Dacierb, M.: A framework for attack patterns’ discovery in honeynet data. Digital Investig. 5, 128–139 (2008)
Kaur, R.; Nagpal, E.S.; Chamotra, S.: Malicious traffic detection in a private organizational network using honeynet system. In: 2015 Annual IEEE India Conference (INDICON), 176–182. IEEE Press, New York (2015)
Jiang, C.B.; Liu, I.; Chung, Y.N.: Novel intrusion prediction mechanism based on honeypot log similarity. Int. J. Netw. Manag. 26(3), 156–175 (2016)
Pan, X.; Yegneswaran. V.; Chen Y.; et. al.: HogMap: using sdns to incentivize collaborative security monitoring. In: 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, pp. 7-12. ACM Press (2016)
Barford, P.; Chen, Y.; Goyal, A.; et al.: Employing honeynets for network situational awareness. Adv. Inf. Secur. 46, 71–102 (2010)
Pham, V.; Dacier, M.: Honeypot trace forensics: the observation viewpoint matters. Future Gener. Comput. Syst. 27(5), 539–546 (2011)
Polly, M.: The danger model: a renewed sense of self. Science 296(12), 301–305 (2002)
Seresht, N.A.; Azmi, R.: MAIS-IDS: a distributed intrusion detection system using multi-agent AIS approach. Eng. Appl. Artif. Intell. 35(10), 286–298 (2014)
Oliveira, D.; Navarro, J.; Wetzel, N.; Bucci, M.: Ianus: secure and holistic coexistence with kernel extensions—an immune system-inspired approach. In: Proceedings of the 29th Annual ACM Symposium on Applied Computing, pp. 1672–1679 (2014)
John C.; Hala E.: Malware detection inspired by the human immune system and making use of honeytokens. In: Proceedings of the 18th Symposium on Communications & Networking, pp. 37–43 (2015)
Sun, F.X.: Artificial immune danger theory based model for network security evaluation. J. Netw. 6(2), 255–262 (2011)
Fan, W.; Fernández, D.; Du, Z.: Versatile virtual honeynet management framework. IET Inf. Secur. 11(1), 38–45 (2017)
Han, W.; Zhao, Z.; Doupé, A.; Ahn, G.: HoneyMix: Toward SDN-based Intelligent Honeynet. In: Proceedings of the 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization. ACM Press (2016)
Nurmi, J.; Kannisto, J.; Vajaranta, M.: Observing hidden service directory spying with a private hidden service honeynet. In: 2016 11th Asia Joint Conference on Information Security (AsiaJCIS), pp. 55–59 (2016)
Greensmith, J.; Aickelin, U.; Cayzer, S.: Introducing Dendritic Cells as a Novel Immune-Inspired Algorithm for Anomaly Detection. In: 4th International Conference on Artificial Immune Systems, pp. 15–167. Springer-Verlag (2010)
Lokesh, M.R.; Kumaraswamy, Y.S.: State awareness towards resiliency in cyber-physical system: a modified danger theory based deterministic Dendritic Cell Algorithm approach. In: Proceedings of IEEE International Conference on Computer Graphics, Vision and Information Security, pp. 201–208 (2015)
Wang, Y.; Wang, Z.; Zhang, L.; et al.: Situation assessment model for inter-domain routing system. IET Softw. 8, 53–61 (2013)
Suhair, A.; Joshua, L.: Danger theory concepts improving malware detection of intrusion detection systems that uses exact graphs. In: International Conference on Computational Science and Computational Intelligence (CSCI), pp. 232–237 (2015)
Mihai-Gabriel, I.; Victor-Valeriu, P.: Achieving DDoS resiliency in a software defined network by intelligent risk assessment based on neural networks and danger theory. In: 2014 IEEE 15th International Symposium on Computational Intelligence and Informatics (CINTI), pp. 319–324 (2014)
Aickelin, U.; Bentley, P.; Cayzer, S.; Kim, J.; McLeod, J.: Danger theory: the link between AIS and IDS? In: Proceedings ICARIS-2003, 2nd International Conference on Artificial Immune Systems, pp. 147–155 (2003)
Williams, C.A.; Harry, R.A.; Mcleod, J.D.: Apoptotic cells induce dendritic cell-mediated suppression via interferon-Y-induced IDO[J]. Immunology 124(1), 89–101 (2008)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, Y., Guo, Y., Zhang, L. et al. SWIM: An Effective Method to Perceive Cyberspace Situation from Honeynet. Arab J Sci Eng 43, 6863–6872 (2018). https://doi.org/10.1007/s13369-017-2904-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-017-2904-5