Abstract
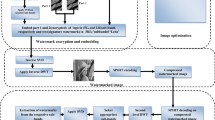
In this paper, we present a digital watermarking scheme in the discrete wavelet transform (DWT) domain that is highly secure to watermark only attacks (WOA). The main idea is that a proper combination of entropy criterion and DS-CDMA is applied to achieve a superior performance in terms of security. In this scheme, the entropy of a random variable is used to opt suitable wavelet blocks where the watermark is to embed. Afterwards, we employ a direct-sequence code division multiple access approach to encode the watermark image. The DS-CDMA encoded watermark is embedded into wavelet blocks, which are determined by entropy criterion. In this context, we quantify the security using an information-theoretic point of view via the equivocation of secret parameters. The resulting watermarking scheme is adequate for private watermarking applications, where the host image is available for watermark detection. To assess the performance of the presented algorithm, we draw an analogy between the security of the proposed watermarking scheme and several important DWT-based watermarking algorithms. Numerical experiments demonstrate that the proposed image watermarking scheme is more secure in comparison with other image watermarking algorithms.

Similar content being viewed by others
References
Simmons, G.J.: The prisoners problem and the subliminal channel. In: Proceedings of Advances Cryptology, pp. 51–67 (1984)
Cayre, F.; Bas, P.: Kerckhoffs-based embedding security class for WOA data hiding. In: IEEE Transactions on Information Forensics and Security, vol. 3, no. 1, pp. 1–15 (2008)
Hsieh, M.; Tseng, D.; Huang, Y.: Hiding digital watermarks using multiresolution wavelet transform. In: IEEE Transactions on Signal Process, vol. 48, no. 5, pp. 875–881 (2001)
Kalker, T.: Consideration on watermarking security. In: Proceedings of IEEE International Workshop on Multimedia Signal Processing, Cannes, pp. 201–206 (2007)
Comesaña P., Pérez-González F., Balado F.: Watermarking security: a survey. IEEE Trans. Signal Process. 54(2), 585–600 (2006)
Cayre, F.; Fontaine, C.; Furon, T.: Watermarking security: theory and practice. In: IEEE Transactions on Signal Processing, vol. 53, no. 10, pp. 3976–3987 (2005)
Barni, M.; Bartolini, F.; Furon, T.: A general frame work for robust watermarking security. In: IEEE Transactions on Signal Processing, vol. 83, no. 10, pp. 2069–2083 (2003)
Samee, M.K.; Gotze, J.: Increased robustness and security of digital watermarking using DS-CDMA. In: IEEE International Symposium on Signal Processing and Information Technology, pp. 185–189 (2007)
Cox I.J., Kilian J., Leighton F.T., Shamoon T.: Secured spread-spectrum watermarking for multimedia. IEEE Trans. Image Process 6(6), 1673–1678 (1997)
Fang, Y.; Huang, J.; Shi, Y.Q.: Image watermarking algorithm applying CDMA. In: IEEE International Symposium on System and Circuits, vol. 2, pp. 948–951 (2003)
Liu S.-C., Feng S., Lin D.: BCH code-based robust audio watermarking. J. Inf. Sci. Eng. 22(23), 535–543 (2006)
Tang C.W., Hang H.M.: A feature-based robust digital image watermarking scheme. IEEE Trans. Signal Process. 51(4), 950–959 (2003)
Cvejic, N.; Tujkovic, D.; Seppanen, T.: Increasing robustness of an audio watermark using turbo codes. In: International Conference on Multimedia and Expo, pp. 217–220 (2003)
Bahat, V.; Sengupta,I.; Das, A.: Audio Watermarking Based on BCH Coding using CT and DWT. In: International Conference on Information Technology, vol. 34, no. 10, pp. 49–51 (2009)
Gallager, R.: Low-density parity-check codes. In: IRE Transactions on Information Theory, vol. 8, no. 10, pp. 21–28 (1962)
Malvar H., Florencio D.: Improved spread spectrum: a new modulation technique for robust watermarking. IEEE Trans. Signal Process. 51(4), 898–905 (2003)
Zheng D., Wang S., Zhao J.: RST invariant image watermarking algorithm with mathematical modelling and analysis of the watermarking processes. IEEE Trans. Image Process. 18(5), 1055–1068 (2009)
Wong P.W., Memon N.: Secret and public image watermarking schemes for image authentication and ownership verification. IEEE Trans. Image Process. 10(10), 1593–1601 (2001)
Venkatesan, R.; Koon, S.-M.; Jakubowski, M.H.; Moulin, P.: Robust image hashing. In: Proceedings of IEEE International Conference on Image Processing’00, Vancouver, BC, Canada (2000)
Kutter, M.; Winkler, S.: A vision-based masking model for spread-spectrum image watermarking. IEEE Trans. Image Process. 11(1), 16–25 (2002)
Cheddad, A.; Condell, J.; Curran, K.: Digital image steganography: survey and analysis of current methods. Signal Process. 90(3), 727–752 (2010)
Sadasivam S., Moulin P., Coleman T.: A message-passing approach to combating desynchronization attacks. IEEE Trans. Inf. Forensics Secur. 6(1), 894–905 (2011)
Niu P.P., Wang X.Y., Yang Y.P.: A novel color image watermarking scheme in nonsampled contourlet-domain. Expert Syst. Appl. 38(3), 2081–2098 (2011)
Zhang H., Shu H., Gouenou C.: Affine Legendre moment invariants for image watermarking robust to geometric distortions. IEEE Trans. Image Process. 20(8), 2189–2199 (2011)
Peng, H.; Wang, J.; Wang, W.X.: Image watermarking method in multiwavelet domain based on support vector machines. J. Syst. Softw. 83(8), 1470–1477 (2010)
Tsai, J.S.; Huang, W.B.; Chen, C.L.; Kuo, Y.H.: A feature-based digital image watermarking for copyright protection and content authentication. In: Proceedings of IEEE International Conference on Image Processing, vol. 5, pp. 469–472 (2007)
Bouguezel, S.; Ahmad, M.O.; Swamy, M.N.S.: New Parametric Discrete Fourier and Hartley Transforms, and Algorithms for Fast Computation. IEEE Transactions on Circuits and Systems I: Regular Papers, vol. 58, no. 3 (2011)
Fang, W.; Chen, K.: A wavelet watermarking based on HVS and watermarking capacity analysis. In: International Conference on Multimedia Information Networking and Security (2009)
Zheng, X.: A multiwavelet based digital watermarking algorithm using texture measures. In: Proceedings of the 2010 International Conference on Wavelet Analysis and Pattern Recognition, Qingdao (2010)
Liu, P.; Zhu, Z.; Wang, H.-X.: A novel image fragile watermarking algorithm based on chaotic map. In: Proceedings of 1st International Congress on Image and Signal Processing, vol. 5, pp. 631–634 (2008)
Braci, S.; Boyer, R.; Delpha, C.: On the tradeoff between security and robustness of the trellis coded quantization scheme. In: IEEE International Conference on Accoustics, Speech and Signal Processing (ICASSP) (2008)
Zhu, L.; Zhao, L.: A digital watermarking scheme based on texture measures in wavelet domain. In: IEEE Image and Signal Processing (2009)
Elbasi E.: Robust multimedia watermarking: Hidden Markov model approach for video sequences. Turk. J. Electr. Eng. Comput. Sci. 18, 159–170 (2010)
Lee M.J., Im D.H., Lee H.Y., Kim K.S., Lee H.K.: Real-time video watermarking system on the compressed domain for high-definition video contents: practical issues. Digit. Signal Process. Rev. J. 22, 190–198 (2011)
Sleit A., Abusharkh S., Etoom R., Khero Y.: An enhanced semi-blind DWT-SVD-based watermarking technique for digital images. Imaging Sci. J. 60, 29–38 (2012)
Cao, L.; Men, C.; Sun, J.: A double zero-watermarking algorithm for 2D vector maps. Harbin Gongcheng Daxue Xuebao/Journal of Harbin Engineering University, vol. 32, pp. 340–344 (2011)
Rahmat, M.F.; Isa, M.D.; Raja Hussin, T.A.: A new image reconstruction method for electrical charge tomography system. Arab. J. Sci. Eng. 37, 1625–1643 (2012)
Sachnev, V.; Kim, H.; Zhang, R.: Less detectable JPEG steganography method based on heuristic optimization and BCH syndrome coding. In: Proceedings of ACM Workshop on Multimedia and Security, pp. 131–139. Princeton (2009)
Filler, T.; Fridrich, J.: Steganography using Gibbs random fields. In: Proceedings of ACM Multimedia and Security Workshop, pp. 199–212. Italy (2010)
Rifa-Pous, H.; Rifa, J.: Product perfect codes and steganography. Digital Signal Process. 19, 764–769 (2009)
Fridrich, J.: Minimizing the embedding impact in steganography. In: Proceedings of ACM Multimedia and Security Workshop, pp. 2–10. Geneva (2006)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Fazli, A.R., Sarbisheie, G. A High-Security Image Watermarking Scheme Against WOA Attacks Using DS-CDMA and Entropy Criterion. Arab J Sci Eng 39, 4853–4863 (2014). https://doi.org/10.1007/s13369-014-1075-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-014-1075-x