Abstract
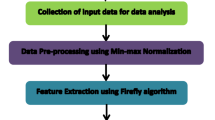
The poor security and larger number of IoT devices are highly possible to be snatched and results in Distributed Denial of Service attack. The IoT attacks corrupt the availability of particular nodes or the whole network by jamming the signal or exhausting the resource nodes’ battery. The devices of IoT are facing security problems because of the increase in attacks which are launched by violators during data transmission via internet. To detect such attacks, a hybrid optimization approach usinga hybrid Metaheuristic lion optimization algorithm and Firefly optimization algorithm (ML-F) is proposed. The NSL-KDD and NBaIoT datasets are used where the input data is pre-processed to remove the noises and the missing data. After preprocessing the data, feature extraction is undergone using Recursive feature elimination (RFE).The low rate attacks are selected after splitting the data using a hybrid ML-F optimization algorithm. After selecting the features,a random forest classifier is used for the process of classifying the attacks. The proposed hybrid ML-F method achieves higher performance than the existing gradient boost classifier method,in classifying the attacks. The proposed hybrid ML-F method achieved an accuracy of 99.98%, precision of 99.87%, recall of 100% and f-measure of 99.73%. The existing gradient boosting classifier method shows the Accuracy of 50.93%, Precision of 54.87%, Recall of 77.67% and F-measure of 64.34%.












Similar content being viewed by others
References
Aldaej A (2019) Enhancing cyber security in modern internet of things (IoT) Using intrusion prevention algorithm for IoT (IPAI). IEEE Access. https://doi.org/10.1109/ACCESS.2019.2893445
Alzubi JA, Selvakumar J, Alzubi O, Manikandan R et al (2019) Decentralized internet of things. Indian J Pub Health Res & Dev 10(2):1513–1524
Chen W, Xiao S, Liu L, Jiang X, Tang Z (2020) A ddos attacks traceback scheme for sdn-based smart city. Comput & Electr Eng 81:106503
Doriguzzi-Corin R, Millar S, Scott-Hayward S, Martinez-del Rincon J, Siracusa D (2020) Lucid: A practical, lightweight deep learning solution for ddos attack detection. IEEE Trans Netw Serv Manag 17(2):876–889
Elmasry W, Akbulut A, Zaim AH (2020) Evolving deep learning architectures for network intrusion detection using a double pso metaheuristic. Comput Netw 168:107042
Galeano-Brajones J, Carmona-Murillo J, Valenzuela-Valdés JF, Luna-Valero F (2020) Detection and mitigation of dos and ddos attacks in iot-based stateful sdn: an experimental approach. Sensors 20(3):816
Jia Y, Zhong F, Alrawais A, Gong B, Cheng X (2020) Flowguard: an intelligent edge defense mechanism against iot ddos attacks. IEEE Int Things J 7(10):9552–9562
Ko I, Chambers D, Barrett E (2020) Feature dynamic deep learning approach for ddos mitigation within the isp domain. Int J Inf Secur 19(1):53–70
Kumar CO, Bhama PRS (2019) Detecting and confronting flash attacks from iot botnets. J Supercomput 75(12):8312–8338
Kumar P, Kumar R, Gupta GP, Tripathi R (2020) A distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT systems by leveraging Fog computing. Trans Emerging Tel Tech. https://doi.org/10.1002/ett.4112
Li J, Liu M, Xue Z, Fan X, He X (2020) Rtvd: A real-time volumetric detection scheme for ddos in the internet of things. IEEE Access 8:36191–36201
Liu G, Quan W, Cheng N, Zhang H, Yu S (2019) Efficient ddos attacks mitigation for stateful forwarding in internet of things. J Netw Comput Appl 130:1–13
McDermott CD, Majdani F, Petrovski AV (2018) Botnet detection in the internet of things using deep learning approaches. In: 2018 international joint conference on neural networks (IJCNN), pp 1–8. https://doi.org/10.1109/IJCNN.2018.8489489
Meidan Y, Bohadana M, Mathov Y, Mirsky Y, Shabtai A, Breitenbacher D, Elovici Y (2018) N-baiot-network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput 17(3):12–22
Murugan NS, Devi GU (2018) Detecting streaming of twitter spam using hybrid method. Wirel Pers Commun 103(2):1353–1374
Murugan NS, Devi GU (2019) Feature extraction using lr-pca hybridization on twitter data and classification accuracy using machine learning algorithms. Cluster Comput 22(6):13965–13974
Ravi N, Shalinie SM (2020) Learning-driven detection and mitigation of ddos attack in iot via sdn-cloud architecture. IEEE Int Things J 7(4):3559–3570
Roopak M, Tian GY, Chambers J (2020) Multi-objective-based feature selection for ddos attack detection in iot networks. IET Netw 9(3):120–127
Tuan TA, Long HV, Son LH et al (2020) Performance evaluation of Botnet DDoS attack detection using machine learning. Evol Intel 13:283–294. https://doi.org/10.1007/s12065-019-00310-w
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Krishna, E.S.P., Thangavelu, A. Attack detection in IoT devices using hybrid metaheuristic lion optimization algorithm and firefly optimization algorithm. Int J Syst Assur Eng Manag (2021). https://doi.org/10.1007/s13198-021-01150-7
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13198-021-01150-7