Abstract
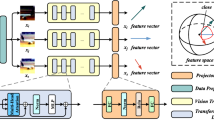
Image based anomaly detection (AD) refers to the task of predicting an unseen image as the normal class (inliers) or the anomalous classes (outliers) by learning only from normal class training images. Such task is of significant value in real-world applications like monitoring anomalous event from surveillance cameras since most captured data reflect normal conditions but identification of anomalous data is required. One pivot challenge for image anomaly (AD) detection is to learn discriminative information only from normal class training images. Most image reconstruction based AD methods rely on the discriminative capability of reconstruction error. This is heuristic as image reconstruction is unsupervised without incorporating normal-class-specific information. In this paper, we propose an AD method called dual deep reconstruction networks based image decomposition (DDR-ID). The networks are trained by jointly optimizing for three losses: the one-class loss, the latent space constrain loss and the reconstruction loss. After training, DDR-ID can decompose an unseen image into its normal class and the residual components, respectively. Two anomaly scores are calculated to quantify the anomalous degree of the image in either normal class latent space or reconstruction image space. Thereby, anomaly detection can be performed via thresholding the anomaly score. The experiments demonstrate that DDR-ID outperforms multiple related benchmarking methods in image anomaly detection using MNIST, CIFAR-10 and Endosome datasets and adversarial attack detection using GTSRB dataset.









Similar content being viewed by others
References
Afiq A, Zakariya M, Saad M, Nurfarzana A, Khir MHM, Fadzil A, Jale A, Gunawan W, Izuddin Z, Faizari M (2019) A review on classifying abnormal behavior in crowd scene. J Vis Commun Image Represent 58:285–303
Aileni RM, George S, Pasca S, Alberto VSC (2020) Data fusion-based ai algorithms in the context of iiots. Internet of Things for Industry 4.0. Springer, New York, pp 17–38
Amarbayasgalan T, Jargalsaikhan B, Ryu K (2018) Unsupervised novelty detection using deep autoencoders with density based clustering. Appl Sci 8(9):1468
An J, Cho S (2015) Variational autoencoder based anomaly detection using reconstruction probability. Special Lecture on IE 2:1–18
Bengio Y, Courville A, Vincent P (2013) Representation learning: a review and new perspectives. IEEE Trans Pattern Anal Mach Intell 35(8):1798–1828
Bradley AP (1997) The use of the area under the ROC curve in the evaluation of machine learning algorithms. Pattern Recognit 30(7):1145–1159
Chalapathy R, Menon AK, Chawla S (2018) Anomaly detection using one-class neural networks. arXiv preprint arXiv:180206360
Chandola V, Banerjee A, Kumar V (2009) Anomaly detection: a survey. ACM Comput Surv (CSUR) 41(3):15
Chen J, Sathe S, Aggarwal C, Turaga D (2017) Outlier detection with autoencoder ensembles. In: Proceedings of the SIAM international conference on data mining, SIAM, pp 90–98
Deecke L, Vandermeulen R, Ruff L, Mandt S, Kloft M (2018) Image anomaly detection with generative adversarial networks. In: Joint European conference on machine learning and knowledge discovery in databases, Springer, New York, pp 3–17
dos Santos FP, Ribeiro LS, Ponti MA (2019) Generalization of feature embeddings transferred from different video anomaly detection domains. J Vis Commun Image Represent 60:407–416
Goodfellow I, Pouget-Abadie J, Mirza M, Xu B, Warde-Farley D, Ozair S, Courville A, Bengio Y (2014) Generative adversarial nets. In: Advances in neural information processing systems, pp 2672–2680
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Ioffe S, Szegedy C (2015) Batch normalization: accelerating deep network training by reducing internal covariate shift. In: International conference on machine learning, pp 448–456
Kingma DP, Ba J (2014) Adam: a method for stochastic optimization. arXiv preprint arXiv:14126980
Krizhevsky A (2009) Learning multiple layers of features from tiny images. Technical report, Citeseer
Krizhevsky A, Sutskever I, Hinton GE (2012) Imagenet classification with deep convolutional neural networks. In: Advances in neural information processing systems, pp 1097–1105
LeCun Y, Cortes C, Burges C (2010) Mnist handwritten digit database. \(at\)&\(t\) labs
Li W, Wu G, Du Q (2017) Transferred deep learning for anomaly detection in hyperspectral imagery. IEEE Geosci Remote Sens Lett 14(5):597–601
Lin D, Lin Z, Cao J, Velmurugan R, Ward ES, Ober RJ (2019) A two-stage method for automated detection of ring-like endosomes in fluorescent microscopy images. PLoS One 14(6):e0218931
Liu FT, Ting KM, Zhou ZH (2008) Isolation forest. In: 2008 eighth IEEE international conference on data mining, IEEE, pp 413–422
Liu W, Anguelov D, Erhan D, Szegedy C, Reed S, Fu CY, Berg AC (2016) SSD: single shot multibox detector. In: European conference on computer vision, Springer, New York, pp 21–37
Long J, Shelhamer E, Darrell T (2015) Fully convolutional networks for semantic segmentation. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 3431–3440
Maaten LVD, Hinton G (2008) Visualizing data using t-SNE. J Mach Learn Res 9(Nov):2579–2605
Matteoli S, Diani M, Theiler J (2014) An overview of background modeling for detection of targets and anomalies in hyperspectral remotely sensed imagery. IEEE J Sel Top Appl Earth Obs Remote Sens 7(6):2317–2336
Nayak R, Pati UC, Das SK (2020) A comprehensive review on deep learning-based methods for video anomaly detection. Image Vis Comput 104078
Pang G, Shen C, Cao L, Hengel Avd (2020) Deep learning for anomaly detection: a review. arXiv preprint arXiv:200702500
Parzen E (1962) On estimation of a probability density function and mode. Ann Math Stat 33(3):1065–1076. http://www.jstor.org/stable/2237880
Paszke A, Gross S, Chintala S, Chanan G, Yang E, DeVito Z, Lin Z, Desmaison A, Antiga L, Lerer A (2017) Automatic differentiation in pytorch. In: NIPS-W
Pimentel MA, Clifton DA, Clifton L, Tarassenko L (2014) A review of novelty detection. Signal Process 99:215–249
Radford A, Metz L, Chintala S (2015) Unsupervised representation learning with deep convolutional generative adversarial networks. arXiv preprint arXiv:151106434
Ren S, He K, Girshick R, Sun J (2015) Faster R-CNN: towards real-time object detection with region proposal networks. In: Advances in neural information processing systems, pp 91–99
Ronneberger O, Fischer P, Brox T (2015) U-net: Convolutional networks for biomedical image segmentation. In: International conference on medical image computing and computer-assisted intervention. Springer, New York, pp 234–241
Ruff L, Görnitz N, Deecke L, Siddiqui SA, Vandermeulen R, Binder A, Müller E, Kloft M (2018) Deep one-class classification. In: International conference on machine learning, pp 4390–4399
Sabokrou M, Fayyaz M, Fathy M, Moayed Z, Klette R (2018a) Deep-anomaly: fully convolutional neural network for fast anomaly detection in crowded scenes. Comput Vis Image Underst 172:88–97
Sabokrou M, Khalooei M, Fathy M, Adeli E (2018b) Adversarially learned one-class classifier for novelty detection. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 3379–3388
Sakurada M, Yairi T (2014) Anomaly detection using autoencoders with nonlinear dimensionality reduction. In: Proceedings of the MLSDA 2014 2nd workshop on machine learning for sensory data analysis, ACM, p 4
Schlegl T, Seeböck P, Waldstein SM, Schmidt-Erfurth U, Langs G (2017) Unsupervised anomaly detection with generative adversarial networks to guide marker discovery. In: International conference on information processing in medical imaging. Springer, New York, pp 146–157
Schölkopf B, Platt JC, Shawe-Taylor JC, Smola AJ, Williamson RC (2001) Estimating the support of a high-dimensional distribution. Neural Comput 13(7):1443–1471. https://doi.org/10.1162/089976601750264965
Seeböck P, Waldstein S, Klimscha S, Gerendas BS, Donner R, Schlegl T, Schmidt-Erfurth U, Langs G (2016) Identifying and categorizing anomalies in retinal imaging data. arXiv preprint arXiv:161200686
Stallkamp J, Schlipsing M, Salmen J, Igel C (2011) The German traffic sign recognition benchmark: a multi-class classification competition. IJCNN 6:7
Szegedy C, Liu W, Jia Y, Sermanet P, Reed S, Anguelov D, Erhan D, Vanhoucke V, Rabinovich A (2015) Going deeper with convolutions. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 1–9
Tax DM, Duin RP (2004) Support vector data description. Mach Learn 54(1):45–66. https://doi.org/10.1023/B:MACH.0000008084.60811.49
Wieland B, Jonas R, Matthias B (2018) Decision-based adversarial attacks: reliable attacks against black-box machine learning models. In: International conference on learning representations. https://openreview.net/forum?id=SyZI0GWCZ
Xia Y, Cao X, Wen F, Hua G, Sun J (2015) Learning discriminative reconstructions for unsupervised outlier removal. In: The IEEE international conference on computer vision (ICCV)
Xie J, Girshick R, Farhadi A (2016) Unsupervised deep embedding for clustering analysis. In: International conference on machine learning, pp 478–487
Zeiler MD, Krishnan D, Taylor GW, Fergus R (2010) Deconvolutional networks. In: Proceedings of the IEEE conference on computer vision and pattern recognition, IEEE, pp 2528–2535
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lin, D., Li, Y., Xie, S. et al. DDR-ID: dual deep reconstruction networks based image decomposition for anomaly detection. J Ambient Intell Human Comput 14, 2125–2139 (2023). https://doi.org/10.1007/s12652-021-03425-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-021-03425-0