Abstract
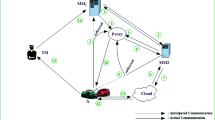
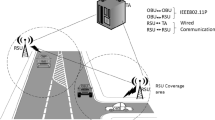
Intelligent transportation is one of the most anticipated projects of cyber-physical systems (CPS), and complete implementation of vehicular ad hoc network (VANET) on road is a fictional reality of the future. Security risks are the major limiting factor in VANET implementation in real life. The intrusion of any unwanted or unauthorized person in a vehicular network leads to significant damage to other authorized vehicles in the network. To prevent this, we propose a secure and privacy-preserving signRecryption protocol which also embeds group signature with a complete authentication protocol. Signcryption increases efficiency, re-encryption provides robustness, group signature ensures privacy, and authentication restricts unauthorized access in the network. All these properties are integrated to deliver the final protocol which is highly efficient, robust and secure. Security of the algorithm has been verified using Burrows-Abadi-Needham (BAN) logic and Automated Validation of Internet Security Protocols and Applications (AVISPA) tool.






Similar content being viewed by others
References
Armando A et al. (2005) The AVISPA tool for the automated validation of internet security protocols and applications. In: International conference on computer aided verification. Springer, Berlin, Heidelberg, pp 281–285
Baheti R, Gill H (2011) Cyber-physical systems. Impact Control Technol 12(1):161–166
Barreto PS, Libert B, McCullagh N, Quisquater JJ (2005) Efficient and provably-secure identity-based signatures and signcryption from bilinear maps. In: International conference on the theory and application of cryptology and information security. Springer, Berlin, Heidelberg, pp 515–532
Bayat M et al (2015) A secure authentication scheme for VANETs with batch verification. Wireless Netw 21(5):1733–1743
Blaze M et al (1998) Divertible protocols and atomic proxy cryptography. In: International Conference on the Theory and Applications of Cryptographic Techniques. Springer, Berlin, Heidelberg, pp 127–144
Burrows M, Abadi M, Needham RM (1989) A logic of authentication. Proc Royal Soc London A Math Phys Sci 426(1871):233–271
Canetti R, Hohenberger S (2007) Chosen-ciphertext secure proxy re-encryption. In: Proceedings of the 14th ACM conference on Computer and communications security, pp 185-194
Chen L et al (2016) Private reputation retrieval in publica privacy-aware announcement scheme for VANETs. IET Inf Secur 11(4):204–210
Deka L et al (2018) Transportation Cyber-Physical System and its importance for future mobility. In: Transportation Cyber-Physical Systems, pp 1–20
Feng X et al (2017) A method for defensing against multi-source Sybil attacks in VANET. Peer-to-Peer Netw Appl 10(2):305–314
Ateniese G, Kevin F, Green M, Hohenberger S (2006) Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans Inf Syst Secur 9:1–30
Han Y, Fang D, Yue Z, Zhang J (2014) SCHAP: The aggregate signCryption based hybrid authentication protocol for VANET. In: International conference on Internet of vehicles, Springer, pp 218-226
Hong Z, Tang F, Luo W (2018) Privacy-Preserving Aggregate Signcryption for Vehicular Ad Hoc Networks. In: Proceedings of the 2nd international conference on cryptography, security and privacy, ACM
Jeong J, Lee E (2014) Vcps: Vehicular cyber-physical systems for smart road services. In: 28th International conference on advanced information networking and applications workshops (WAINA), IEEE, pp 133-138
Jia D et al (2016) A survey on platoon-based vehicular cyber-physical systems. IEEE Commun Surv Tutor 18(1):263–284
Jianhong Z, Min X, Liying L (2014) On the security of a secure batch verification with group testing for VANET. Int J Netw Secur 16(5):351–358
Jinila YB, Komathy K (2013) A privacy preserving authentication framework for safety messages in VANET, IET, pp 456-461
Kalaiarasy C, Sreenath N, Amuthan A (2020) An effective variant ring signature-based pseudonym changing mechanism for privacy preservation in mixed zones of vehicular networks. J Ambient Intell Human Comput 11:1669–1681
Kanchan S, Chaudhari NS (2016) Integrating group signature scheme with Non-transitive Proxy Re-encryption in VANET. In: International conference on computing. Analytics and Security Trends (CAST), IEEE, pp 227–231
Kanchan S, Singh G, Chaudhari NS (2018) Re-encrypting secure and efficient routing in VANET groups using sharable clouds. In: 4th International conference on recent advances in information technology (RAIT). IEEE, pp 1-6
Kumari S, Khan MK (2014) More secure smart cardbased remote user password authentication scheme with user anonymity. Secur Commun Netw 7(11):2039–2053
Lin Xiaodong et al (2007) GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans Veh Technol 56(6):3442–3456
Lu R et al (2013) A lightweight conditional privacy-preservation protocol for vehicular traffic-monitoring systems. IEEE Intell Syst 28(3):62–65
Ma C, Ao J (2009) Group-based Proxy Re-encryption Scheme Secure Against Chosen Ciphertext Attack. IJ Netw Secur 8(3):266–270
Mekki T et al (2017) Vehicular cloud networks: Challenges, architectures, and future directions. Veh Commun 9:268–280
Parne BL, Gupta S, Chaudhari NS (2018) Segb: Security enhanced group based aka protocol for m2m communication in an iot enabled lte/lte-a network. IEEE Access 6:3668–3684
Rawat DB, Bajracharya C, Yan G (2015) Towards intelligent transportation cyber-physical systems: Real-time computing and communications perspectives. In: 2015 SoutheastCon IEEE, pp 1-6
Savu L (2012) Signcryption scheme based on schnorr digital signature. arXiv preprint arXiv:1202.1663
Selvi M, Ramakrishnan B (2015) Prioritized and secured data dissemination technique in VANET based on optimal blowfish algorithm and signcryption method. Int J Comput Netw Appl 2(4):165–172
Singh Sumitkumar, Vijayan R (2011) Enhanced security for information flow in vanet using signcryption and trust level. Int J Comput Appl 16(5):0975–8887
Sneha K, Chaudhari NS (2018) SRCPR: SignReCrypting Proxy Re-signature in secure VANET Groups. IEEE Access 6:59282–59295
Sun X, Lin X, Ho P-H (2007) Secure vehicular communications based on group signature and ID-based signature scheme, In: International Conference on communications, IEEE, pp 1539-1545
Sur C, Park Y, Rhee KH (2016) An efficient and secure navigation protocol based on vehicular cloud. Int J Comput Math 93(2):325–344
Wan C, Zhang J (2018) Efficient identity-based data transmission for VANET. J Ambient Intell Humaniz Comput 9(6):1861–1871
Wessels Jan, CMG FINANCE BV (2001) Application of BAN-logic, CMG FINANCE BV 19 : 1-23
Zheng Y (1997) Digital signcryption or how to achieve cost (signature & encryption) cost (signature)+ cost (encryption). In: Annual International Cryptology Conference, Springer, Berlin, Heidelberg
Zhao H et al (2018) Dynamic trust model for vehicular cyber-physical systems. Int J Netw Secur 20(1):157–167
Zhou Y, Liu S, Xiao M, Deng S, Wang X (2018) An efficient V2I authentication scheme for VANETs. Mob Inf Syst 2018:4070283
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kanchan, S., Singh, G. & Chaudhari, N.S. SPSR-VCP: secure and privacy preserving SignRecryption in vehicular cyber physical systems. J Ambient Intell Human Comput 13, 1–20 (2022). https://doi.org/10.1007/s12652-020-02859-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02859-2