Abstract
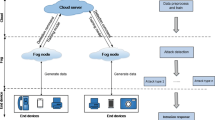
Internet of Things (IoT) is one of the significant emerging domains in computing. IoT structures the base of future infrastructures, developing the advancement of future smart cities that are naturally moderate. However, IoT is vulnerable to different cyber-attacks. The most critical issues of the IoT are security and privacy. In this research, the integration of IoT with cloud and fog computing can present an improved platform to support IoT smart city applications. Cloud computing can provide data storage at top-level management and fog computing can offer various services for supporting smart city applications based on IoT. The integrated architecture of the IoT-Fog-Cloud computing model is presented in this research. For the analysis based on Network-based Intrusion Detection System (NIDS) anomaly detection, the Improved Naïve Bayes (INB) classifier based on Principal Component Analysis (PCA) technique is proposed in this work. The UNSW-NB15 dataset is used for the evaluation of the attack detection model. The PCA technique is used to extract features of the dataset, and the INB classifier is used for the classification of attacks. This technique is proposed to enhance the efficiency of the anomaly detection and to improve the performance analysis in terms of accuracy, precision, recall, and detection rate. The INB-PCA achieved 92.48% accuracy and 95.35% detection rate.





Similar content being viewed by others
References
Afag SEB (2020) Classification of lung nodules using improved residual convolutional neural network. J Comput Sci Intell Technol 1(1):15–21
Anuroop G, Tim W, Maia A, Jyotheesh G (2020) Detecting sensor faults, anomalies, and outliers in the internet of things: a survey on the challenges and solutions. Electron 9(511):1–15
Eltigani AMY, Hassan IB (2020) Classification of diabetic retinopathy using stacked autoencoder-based deep neural network. J Comput Sci Intell Technol 1(1):09–14
Husam R, Tibor C (2018) IoT based Smart Cities. In: International Symposium on Networks, Computers, and Communications (ISNCC), pp 1–4
Ibrahim A, Ali A, Esam A, Raed A, Mohamed Z, Hua M (2019) AD-IoT: anomaly detection of IoT cyberattacks smart city using machine learning. In: IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), pp 305–310
Ioannis S, Panayiotis K, Mihalis P, Cristina A, Javier L (2018) A Survey of IoT-enabled cyberattacks: assessing attack paths to critical infrastructures and services. IEEE Commun Surv Tutor 20(4):3453–3495
Iqbal HS, Yoosef BA, Fawaz A, Asif IK (2020) IntruDTree: a machine learning-based cyber security intrusion detection model. Symmetry 12(754):1–15
Jadel A, Khalid A (2019) Internet of Things cyber attacks detection using machine learning. Int J Adv Comput Sci Appli 10(12):627–634
Joy D, Sarbani R (2017) IoT-Fog-Cloud based architecture for smart city: prototype of a smart building. In: 2017 7th International Conference on Cloud Computing, Data Science and Engineering–Confluence, pp 237–242
Junaid A, Muhammad AA, Roohi A, Khaled S, Mamoun A, Razi I (2020) A review of performance, energy, and privacy of intrusion detection systems for IoT. Electron 9(629):1–24
Kejun C, Shuai Z, Zhikun L, Yi Z, Qingxu D, Sandip R, Yier J (2018) Internet-of-things security and vulnerabilities: taxonomy, challenges, and practice. J Hardw Syst Sec 2:97–110
Mahmudul H, Md. Milon I, Md. Ishrak IZ, Hashem MMA (2019) Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 7:1–14
Mao VN, Hakima C, Tie L, Tony QSQ (2019) Adaptive anomaly detection for IoT data in hierarchical edge computing. AAAI Workshop Artif Intell Things (AIoT)
Moustafa N, Slay J (2015) UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, pp 1–6. https://www.unsw.adfa.edu.au/unsw-canberra-cyber/cybersecurity/ADFA-NB15-Datasets/. Accessed 16 Oct 2020
Muhammad B, Rana AR, Bilal K, Byung-Seo K (2018) IoT elements, layered architectures, and security issues: a comprehensive survey. Sensors 8(2796):1–37
Muneeshwari P, Kishanthini M (2020) A new framework for anomaly detection in NSL-KDD dataset using hybrid neuro-weighted genetic algorithm. J Comput Sci Intell Technol 1(1):29–36
Mustafa M, Eltayeb AR, Mustafa ES (2020) Hybrid convolutional neural network with PSO based severe dengue prognosis method in human genome data. J Comput Sci Intell Technol 1(1):22–28
Nader M, Jameela A J, Imad J (2019) Towards fault-Tolerant Fog computing for IoT-based smart city applications. In: IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), pp 752–757
Nadia C, Mohamed M, Akka Z, Cyrille S, Parvez F (2019) Network intrusion detection for IoT security based on learning techniques. IEEE Commun Surv Tutorials 21(3):2671–2701
Narmatha C, Eljack SM, Tuka AARM, Manimurgan S, Mustafa M (2020) A hybrid fuzzy brain-storm optimization algorithm for the classification of brain tumor MRI images. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-020-02470-5
Prajoona V, Sriramakrishnan P, Sridhar S, Charlyn Pushpa Latha G, Priya A, Ramkumar S, Robert Singh A, Rajendran T (2020) Knowledge based fuzzy c-means method for rapid brain tissues segmentation of magnetic resonance imaging scans with CUDA enabled GPU machine. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-020-02132-6
Pu L, Chen X, Xu J, Fu X (2016) D2D fogging: an energy-efficient and incentive-aware task offloading framework via network-assisted D2D collaboration. IEEE J Sel Areas Commun 34(12):3887–3901
Salaheldin LS, Lutfi AM (2020) A novel intrusion detection system in WSN using Hybrid Neuro-Fuzzy filter with ant colony algorithm. J Comput Sci Intell Technol 1(1):01–08
Shyara TR, Saroj H (2013) Enhanced Naïve Bayes algorithm for intrusion detection in data mining. Int J Comput Sci Inform Technol 4(6):960–962
Thavasimuthu R, Sridhar KP, Manimurugan S, Deepa S (2019) Recent innovations in soft computing applications. Curr Signal Transduct Ther 14(2):129–130
Tran V K, Yuris M S, Dinh T H, Nguyen L T, Diep N, Nguyen V H, Eryk D (2020) Collaborative Learning Model for Cyberattack Detection Systems in IoT Industry 4.0. IEEE Wireless Communications and Networking Conference (WCNC), pp 1–6
Xiaoyan H, Liancheng X, Min R, Weiping G (2015) A Naive Bayesian network intrusion detection algorithm based on Principal Component Analysis. In: 7th International Conference on Information Technology in Medicine and Education, pp 325–328
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Manimurugan, S. IoT-Fog-Cloud model for anomaly detection using improved Naïve Bayes and principal component analysis. J Ambient Intell Human Comput (2021). https://doi.org/10.1007/s12652-020-02723-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12652-020-02723-3