Abstract
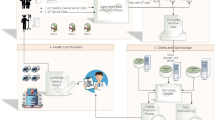
The application of IoT in the several fields is extending due to its simple and robust functionality. Especially, with the advent of the IoT-cloud based devices, IoT are established in the field that process very high amount of data. The health care system is one of the emerging applications of the IoT-Cloud. Many research works are carried out in ensuring the privacy of the patient data. The main issues in the IoT-cloud based health system remains on the security of data along with computation overheads. Predicting disease using patient data from the IoT device is another demanding aspect of health systems. In this research work, a novel Homomorphic Encryption with Random Diagonal Elliptical curve cryptography integrated with Multi-nomial smoothing Naive Bayes (HERDE-MSNB) is proposed to provide the effective security and predict the disease over patient data in the IoT Health Cloud system. The cryptic framework in the proposed architecture involves the encryption and decryption of the patient data along with key words through the HERDE algorithm. The Medicinal person deciphers the encrypted data and performs the prediction through the MSNB model. The UCI repository dataset is employed to predict the performance of the security and prediction model. From the analysis it is observed that the proposed architecture is effective in providing security and disease prediction than the existing models with less processing time, computational cost and increased accuracy. The future work may include all aspects of the dataset with robust prediction model.








Similar content being viewed by others
Change history
20 June 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-04173-5
References
Abidi B, Jilbab, A, Haziti ME (2017) Wireless sensor networks in biomedical: Wireless body area networks. In: Europe and MENA Cooperation Advances in Information and Communication Technologies. Springer: Berlin/Heidelberg, Germany, pp. 321–329.
Ahmed TM (2016) Developing a predicted model for diabetes type 2 treatment plans by using data mining. J Theoret Appl Inf Technol 90(2):181
Ambika M, Raghuraman G, SaiRamesh L, Ayyasamy A (2020) Intelligence–based decision support system for diagnosing the incidence of hypertensive type. J Intell Fuzzy Syst 38(2):1811–1825
Ankita S, Nisheeth S (2013) Elliptic curve cryptography: an efficient approach for encryption and decryption of a data sequence. Int J Sci Res 2(5):2013
Azeez NA, Van der Vyver C (2018). Security and privacy issues in e-health cloud-based system: A comprehensive content analysis. Egypt Inf J
Baharon MR, Shi Q, Abdollah MF, Yassin SWMS, Idris A (2018) An improved fully homomorphic encryption scheme for cloud computing. Int J Commun Netw Inf Secur 10(3):502
Bai TDP, Jerald AV, Rabara SA (2015) Elliptic curve cryptography based security framework for internet of things and cloud computing. Int J Comput Sci Technol 6:223–229
Bhati M, Rani P (2015) Review of passive security measure on trusted cloud computing. Int J Sci Eng Appl Sci (IJSEAS) 1(3):551–556
Bost R, Popa RA, Tu S, Goldwasser S (2015) Machine learning classification over encrypted data. NDSS 4324:4325
Darwish A, Hassanien AE, Elhoseny M, Sangaiah AK, Muhammad K (2019) The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: opportunities, challenges, and open problems. J Ambient Intell Hum Comput 10:4151–4166
Graepel T, Lauter K, Naehrig M (2012) ML confidential: Machine learning on encrypted data. In: International Conference on Information Security and Cryptology (pp. 1–21). Springer, Berlin, Heidelberg.
Khedr A, Gulak G, Vaikuntanathan V (2015) SHIELD: scalable homomorphic implementation of encrypted data-classifiers. IEEE Trans Comput 65(9):2848–2858
Liu G, Wang L, Wang Q, Zhou G, Wang Y, Jiang Q (2014) A new approach to detect congestive heart failure using shortterm heart rate variability measures. PLoS ONE 9(4):e93399
Liu Y, Dong B, Guo B, Yang J, Peng W (2015) Combination of cloud computing and internet of things (IOT) in medical monitoring systems. Int J Hybrid Inf Technol 8(12):367–376
Manikanda Kumaran K, Chinnadurai M (2020) Cloud-based robotic system for crowd control in smart cities using hybrid intelligent generic algorithm. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-020-01758-w
Miao Y, Ma J, Liu X, Liu Z, Shen L, Wei F (2018) VMKDO: Verifiable multi-keyword search over encrypted cloud data for dynamic data-owner. Peerto-Peer Netw Appl 11(2):287–297
Olaniyi EO, Oyedotun OK (2015) Heart diseases diagnosis using neural networks arbitration. In J Intell Syst Appl 7(12):75–82
Pecarina J, Pu S, Liu J-C (2012) “SAPPHIRE: Anonymity for enhanced control and private collaboration in healthcare clouds. In: Proc. IEEE 4th Int. Conf. Cloud Comput. Technol. Sci.
Polat K, Güneş S, Arslan A (2008) A cascade learning system for classification of diabetes disease: generalized discriminant analysis and least square support vector machine. Expert Syst Appl 34(1):482–487
Prabal V, Sood SK, Kalra S (2018) Cloud-centric IoT based student healthcare monitoring framework. J Ambient Intell Humaniz Comput 9:1293–1309
Renuka M, Shyla J (2016) Analysis of various data mining techniques to predict diabetes mellitus. Int J Appl Eng Res 11(1):727–730
Rumsfeld JS, Joynt KE, Maddox TM (2016) Big data analytics to improve cardiovascular care: promise and challenges. Nat Rev Cardiol 13(6):350
Sanjay S, Sood SK, Gupta SK (2018) IoT-based cloud framework to control Ebola virus outbreak. J Ambient Intell Hum Comput 9:459–476
Stergiou C, Psannis KE, Kim BG, Gupta B (2018) Secure integration of IoT and cloud computing. Future Gener Comput Syst 78:964–975
Wu DN, Gan QQ, Wang XM (2018) Verifiable public key encryption with keyword search based on homomorphic encryption in multi-user setting. IEEE Access 6:42445–42453
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail: https://doi.org/10.1007/s12652-022-04173-5
About this article
Cite this article
Vedaraj, M., Ezhumalai, P. RETRACTED ARTICLE: HERDE-MSNB: a predictive security architecture for IoT health cloud system. J Ambient Intell Human Comput 12, 7333–7342 (2021). https://doi.org/10.1007/s12652-020-02408-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02408-x