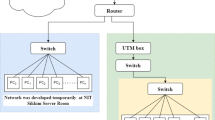
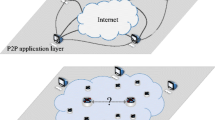
Abstract
With the wide application of wireless sensor networks, network security has been a terrible problem when it provides many more services and applications. Rapid usage of internet and connectivity demands a network anomaly system combating cynical network attacks. Meanwhile, it is a common approach for acquiring, which can be used by network operators to carry out network management and configuration. Moreover, a great number of evaluations have been proposed to simulate and analyse the Wireless Sensor Network traffic, it is still a remarkable challenge since, and network traffic characterization has been tremendously changed, in particular, for a sensor computing network. Bayesian Based Network Traffic Prediction (BNTP) is proposed to solve the deep learning of statistical features of network traffic flow so that all the packets were sent to the receiver properly without any traffic density. Bayesian network-based peer-to-peer network traffic design is proposed to determine the spatial structure of traffic flow. PVM fault localization feature is proposed to remove the accuracy measure issues and performance problems. The co-existence mechanism is used to minimize the inference and overlap problem in wireless network devices. This paper avoids the conflicts in traffic analysis and statistical features of the network. The performance of the network is increased to 80% when compared to the existing methods.














Similar content being viewed by others
Change history
06 June 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-04079-2
References
Arafah M, Alhindi H, Mathkour H, Faisal M, Lytras MD (2018) Smart systems approach for development of explicit congestion marking and traffic engineering model for Diffserv/MPLS networks. J Ambient Intell Hum Comput pp 1–11
Bai Y, Du Z, Zhang C, Zhao X (2019) Sentinel surveillance of traffic conditions with multilayer network. J Ambient Intell Hum Comput 10(8):3123–3131
Bao F, Chen C, Cho M (2011) Trust-based intrusion detection in wireless sensor networks. In: Proceedings of the 2011 IEEE international conference on communications (ICC), pp 1–6
Biswas S, Morris R (2004) Opportunistic routing in multi-hop wireless networks. ACM SIGCOMM Comput Commun Rev 34(1):69–74
Bouchaala L, Masmoudi A, Gargouri F (2010) Improving algorithms for structure learning in Bayesian networks using a new implicit score. Expert Syst Appl 37(7):5470–5475
Cao XM, Han ZJ, Chen GH (2007) Dos attack detection scheme for sensor networks based on traffic prediction. Chin J Comput 30:1798–1805 (In Chinese)
Chen, Wu H, Hu H, Gao J (2008) Event-based trust framework model in wireless sensor networks. In: Proceedings of the international conference on networking, architecture, and storage (NAS), pp 359–364
Fan Y, Shelton CR (2008) Sampling for approximate inference in continuous time Bayesian networks. In: Tenth international symposium on artificial intelligence and mathematics, pp 1–8
Fonseca C, Ferreira H (2012) Stability and contagion measures for spatial extreme value analyses. arXiv:1206.1228
Guo J, Marshall A, Zhou B (2011) A new trust management framework for detecting malicious and selfish behaviour for mobile ad hoc networks. In: Proceedings of the 10th IEEE international conference on trust, security and privacy in computing and communications (Trust Com), pp 142–149
Heckerman GD, Chickering DM (1995) Learning Bayesian networks: the combination of knowledge and statistical data. Mach Learn 20:197–243
Hooper E (2006) Experimental validation and analysis of an intelligent detection and response strategy to false positives and network attacks. In: Mehrotra S, Zeng DD, Chen H, Thuraisingham B, Wang FY (eds) Intelligence and security informatics. ISI 2006. Lecture notes in computer science, vol 3975. Springer, Berlin, Heidelberg. https://doi.org/10.1007/11760146_101
Hu W, Liao Y, Vemuri VR (2003) Robust support vector machines for anomaly detection in computer security. In: ICMLA, pp 168–174
Hu M, Chun Y, Perr A (2005) Ariadne: a secure on-dem for ad hoc networks I. Journal, 11
Jiang D, Yuan Z, Zhang P (2015) A traffic anomaly detection approach in communication networks for applications of multimedia medical devices. Multimed Tools Appl
Jongsawat N, Decharoenchitpong J (2015) Creating behavior-based rules for snort based on Bayesian network learning algorithms. In: The international conference on science and technology (TICST), pp 267–70
Kottas WZ, Rodrguez A (2012) Spatial modeling for risk assessment of extreme values from environmental time series: a Bayesian nonparametric approach. Environmetrics 23(8):649–662
Lakhina A, Crovella M, Diot C (2005) Mining anomalies using traffic feature distributions. ACM SIGCOMM Comput Commun Rev 35(4):217–228
Li D, Hu YH (2003) Energy-based collaborative source localization using acoustic microsensor array. EURASIP J Appl Signal Process 4:321–337
Meng Y, Kwok LF, Li W (2012) Towards designing packet filter with a trust-based approach using bayesian inference in network intrusion detection. In: Proceedings of the 8th international conference on security and privacy in communication networks (SECURECOMM), Lecture Notes in ICST, Springer, New York, pp 203–221
Niu R, Varshney PK (2006) Target location estimation in sensor networks with quantized data. IEEE Trans Signal Process 54(12):4519–4528
Nor AK, Quan B, Adnan A-A (2019) Adaptive trust-based routing protocol for large scale WSNs. IEEE Access 7:143539–143549
Onat A, Miri A (2005) An intrusion detection system for wireless sensor networks. In: Proceeding of the IEEE international conference on wireless and mobile computing, networking and communications, vol. 3, Montreal, Canada, pp 253–259
Pearl JF (1986) Propagation and structuring in belief networks. Artif Intell 29:241–288
Polverini M, Iacovazzi A, Cianfrani A, (2015) Traffic Matrix Estimation Enhanced by SDNs Nodes in Real Network Topology. Proceedings of 2015 I.E. Conference on Computer Communications Workshops
Rajasegarar S, Zhang P, Zhou Y, Karunasekera S, Leckie C, Palaniswami M (2014) High-resolution Spatio-temporal monitoring of air pollutants using wireless sensor networks. In: Proceedings of IEEE 9th International conference on intelligent sensors, sensor network information process (ISSNIP), pp 1–6
Sanzgiri K, Dahill BR (2002) A secure ro hoc networks. In: Proceedings of on network protocols, pp 78–87
Soule A, Lakhina A, Taft N (2005) Traffic matrices: balancing measurements, inference, and modeling. Proceed Sigmetrics 2005:362–373
Stoleru R, Stankovic JA (2015) Probability grid: a location estimation scheme for wireless sensor network. In: Conference of IEEE sensor and ad hoc communications and networks, pp 430–438
Sun B, Osborne L, Xiao Y, Guizani S (2007) Intrusion detection techniques in mobile ad hoc and wireless sensor networks. IEEE Wirel Commun 10:56–63
Thesiya K, Viraj D (2015) Novel clustering approach to reduce energy consumption in wireless sensor network based on LEACH. Int J Comput Sci Mob Comput (IJCSMC) 4(6)
Waltenegus D (2019) A quantitative measure of reliability for wireless sensor networks. IEEE Sens Lett 3:8
Xu K, Zhang ZL, Bhattacharyya S (2005) Profiling internet backbone traffic: behavior models and applications. ACM SIGCOMM Comput Commun Rev 35(4):169–180
Zaineb TA-A, Ahmed LQ, Taisir E-G, Jaafar MHE (2019) Energy efficient IoT virtualization framework with peer to peer networking and processing. IEEE Access
Zhihua C, Fei X, Shiqiang Z, Xingjuan C, Yang C, Wensheng Z, Jinjun C (2020) A hybrid blockchain-based identity authentication scheme for multi-WSN. IEEE
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail: https://doi.org/10.1007/s12652-022-04079-2
About this article
Cite this article
Geepthi, D., Columbus, C.C. RETRACTED ARTICLE: Network traffic detection for peer-to-peer traffic matrices on bayesian network in WSN. J Ambient Intell Human Comput 12, 6975–6986 (2021). https://doi.org/10.1007/s12652-020-02355-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02355-7