Abstract
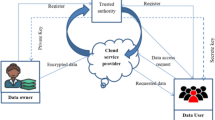
Cloud environment improves the utilization of spread sources by sharing them with others in an open platform. Security is an important concern, since, the data is being managed by cloud service providers and data is produced by owners. The gap between these two give chances to imposters to access the data. Hybrid cloud cryptographic algorithms helps to the users and service providers to manage this security issue. The proposed medical cloud model transmits the data in a hybrid cloud using two fish data encryption algorithm and ring model which improves the dynamicity and data security along with finger print authentication. To generate security keys, finger print virtual machines are used in the research model, which is non traceable, and helps to improve the security efficiency of the proposed model. The experimental results are compared with conventional AES and DES algorithms to validate the results.











Similar content being viewed by others
Change history
15 June 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-04135-x
References
Alizadeh M, Abolfazli S, Zamani M, Baharun S, Sakurai K (2016) Authentication in mobile cloud computing: a survey. J Netw Comput App 61:59–80
Bendiab G, Shiaeles S, Boucherkha S, Ghita B (2019) FCMDT: a novel fuzzy cognitive maps dynamic trust model for cloud federated identity management. Comput Secur 86:270–290
Benzekki K, El Fergougui A, ElBelrhiti A (2018) A context-aware authentication system for mobile cloud computing. Procedia Comput Sci 127:379–387
Caesarendra W, Wijaya T, Tjahjowidodo T, Pappachan BK, Rosla MI (2018) Adaptive neuro-fuzzy inference system for deburring stage classification and prediction for indirect quality monitoring. Applied Soft Computing 72:565–578
Coutinho EF, de Carvalho Sousa FR, Rego PA, Gomes DG, Souza JN (2015) Elasticity in cloud computing: a survey. Ann Telecommun 70(7–8):289–309
Elgazzar SE, Saleh AA, El-Bakry HM (2017) Overview of using private cloud model with GIS. Int J Electron Inf Eng 7(2):68–78
El-Makkaoui K, Ezzati A, Beni-Hssane A (2017) Cloud-RSA: An enhanced homomorphic encryption scheme. Europe and MENA Cooperation Advances in Information and Communication Technologies, Springer, pp 471–480
Gumaei A, Sammouda R, Al-Salman AMS, Alsanad A (2019) Anti-spoofing cloud-based multi-spectral biometric identification system for enterprise security and privacy-preservation. J Parallel Distrib Comput 124:27–40
Kumar S, Saranya N (2017) A complete public auditing for data sharing in hybrid cloud using tri degree coalition (TDC) architecture. Int J Pure Appl Math 117(21):925–929
Lamiche I, Bin G, Lamiche I, Bin G, Jing Y, Yu Z, Hadid A (2019) A continuous smartphone authentication method based on gait patterns and keystroke dynamics. J Ambient Intell Human Comput 10:4417–4430. https://doi.org/10.1007/s12652-018-1123-6
Ma Xu, Zhang F, Chen X, Shen J (2018) Privacy preserving multi-party computation delegation for deep learning in cloud computing. Inf Sci 459:103–116
Mitra A, Kundu A, Chattopadhyay M, Chattopadhyay S (2017) A cost-efficient one-time password-based authentication in cloud environment using equal length cellular automata. J Ind Inf Integr 5:17–25
Moganarangan S, Balaji B (2017) Efficient multilevel authentication in an integrated pervasive healthcare environment. J Adv Res Dyn Control Syst 9:1661–1672
Muniasamy K, Srinivasan S, Vain J, Sethumadhavan M (2019) Formal methods based security for cloud-based manufacturing cyber physical system. IFAC-Papers Online 52(13):1198–1203
Peng Y, Zhao W, Xie F, Dai Z-H, Chen D-Q (2012) Secure cloud storage based on cryptographic techniques. J China Univ Posts Telecommun 19(2):182–189
Sajay KR, Babu SS, Vijayalakshmi Y (2019) Enhancing the security of cloud data using hybrid encryption algorithm. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-019-01403-1
Sukumaran C, Misbahuddin M (2018) DNA cryptography for secure data storage in cloud. Int J Netw Secur 20(3):447–454
Surendar A (2017a) Evolution of gait biometric system and algorithms- A review. Biomed Pharmacol J 10(1):467–472
Surendar A (2017b) FPGA based parallel computation techniques for bioinformatics application. Int J Res Pharmaceut Sci 8(2):124–128
Yi X, Tari Z, Hao F, Chen L, Zomaya AY (2019) Efficient threshold password-authenticated secret sharing protocols for cloud computing. J Parallel Distrib Comput 128:57–70
Zhendong Wu, Tian L, Li P, Ting Wu, Chunming Wu (2018) Generating stable biometric keys for flexible cloud computing authentication using finger vein. Inf Sci 433–434:431–447
Acknowledgements
This work is for the research purpose and no funding is provided.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail: https://doi.org/10.1007/s12652-022-04135-x
About this article
Cite this article
Jaikumar, V., Venkatachalapathy, K. RETRACTED ARTICLE: Integrative optimization with Qos using multi-level security in medical cloud. J Ambient Intell Human Comput 12, 6923–6931 (2021). https://doi.org/10.1007/s12652-020-02337-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02337-9