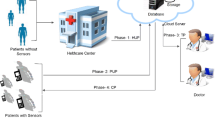
Abstract
In this paper, we have developed cloud-based authentication protocol for e-health care monitoring system which provides a secure platform to the patients. By using this system, the patients can get best medical facilities and treatment from the doctors via mobile phones without physically visiting the hospitals. To provide the privacy of patients and the guarantee of the reliability of the system, we have done an informal security analysis of the proposed protocol which validates that it is defending various kinds of security threats. Apart from it, the security of the proposed protocol is also analyzed by using popular automated pro-verif tool. In addition, we compared the proposed protocol with other existing protocols in terms of performance evaluation. The performance evaluation is measured in the context of security features, communication and computation cost as well as execution time also which proves that the same protocol is more efficient, cost effective and applicable for real-life application.










Similar content being viewed by others
References
Alanizy N, Alanizy A, Baghoza N, Al Ghamdi M, Gutub A (2018) 3-layer PC text security via combining compression, AES cryptography 2LSB image steganography. J Res Eng Appl Sci (JREAS) 3(4):118–124
Alassaf N, Alkazemi B, Gutub A (2003) Applicable light-weight cryptography to secure medical data in IoT systems. J Res Eng Appl Sci (JREAS) 2(2):50–58
Alassaf N, Gutub A, Parah SA, Al Ghamdi M (2018) Enhancing speed of simon: a light-weight-cryptographic algorithm for IoT applications. Multimed Tools Appl. https://doi.org/10.1007/s11042-018-6801-z
Al-Ghamdi M, Al-Ghamdi M, Gutub A (2019) Security enhancement of shares generation process for multimedia counting-based secret-sharing technique. Multimed Tools Appl 78(12):16283–16310
Al-Juaid NA, Gutub AA, Khan EA et al. (2018) Enhancing PC data security via combining RSA cryptography and video based steganography. J Inf Secur Cybercrimes Res (JISCR) 1(1):1–11
Ali R, Pal AK (2018) Cryptanalysis and biometric-based enhancement of a remote user authentication scheme for e-healthcare system. Arab J Sci Eng 43(12):7837–7852
Ali R, Pal AK, Kumari S, Sangaiah AK, Li X, Wu F (2018) An enhanced three factor based authentication protocol using wireless medical sensor networks for healthcare monitoring. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-018-1015-9
Alsaidi A, Al-lehaibi K, Alzahrani H, AlGhamdi M, Gutub A (2018) Compression multi-level crypto stego security of texts utilizing colored email forwarding. J Comput Sci Comput Math (JCSCM) 8(3):33–42
Chandrakar P, Om H (2018) An extended ECC-based anonymity-preserving 3-factor remote authentication scheme usable in TMIS. Int J Commun Syst 31(8):e3540
Chaudhry SA, Naqvi H, Khan MK (2018) An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimed Tools Appl 77(5):5503–5524
Chen C-L, Yang T-T, Chiang M-L, Shih T-F (2014a) A privacy authentication scheme based on cloud for medical environment. J Med Syst 38(11):143
Chen C-L, Yang T-T, Shih T-F (2014b) A secure medical data exchange protocol based on cloud environment. J Med Syst 38(9):112
Chiou S-Y, Ying Z, Liu J (2016) Improvement of a privacy authentication scheme based on cloud for medical environment. J Med Syst 40(4):101
Gutub A, Al-Ghamdi M (2019) Image based steganography to facilitate improving counting-based secret sharing. 3D Res 10(1):6
Gutub A, Al-Juaid N (2018) Multi-bits stego-system for hiding text in multimedia images based on user security priority. J Comput Hardw Eng 1(2):1–9
Gutub A, Al-Juaid N, Khan E (2019) Counting-based secret sharing technique for multimedia applications. Multimed Tools Appl 78(5):5591–5619
Kalra S, Sood SK (2015) Secure authentication scheme for IOT and cloud servers. Perv Mob Comput 24:210–223
Khan AA, Kumar V, Ahmad M (2019) An elliptic curve cryptography based mutual authentication scheme for smart grid communications using biometric approach. J King Saud Univ Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2019.04.013
Kumar V, Jangirala S, Ahmad M (2018) An efficient mutual authentication framework for healthcare system in cloud computing. J Med Syst 42(8):142
Kumar V, Ahmad M, Kumar P (2019a) An identity-based authentication framework for big data security. In: Proceedings of 2nd international conference on communication, computing and networking. Springer, pp 63–71
Kumar V, Ahmad M, Kumari A (2019b) A secure elliptic curve cryptography based mutual authentication protocol for cloud-assisted TMIS. Telemat Inform 38:100–117
Kumari S, Karuppiah M, Das AK, Li X, Wu F, Kumar N (2017a) A secure authentication scheme based on elliptic curve cryptography for IOT and cloud servers. J Supercomput 74(12):6428–6453
Kumari S, Li X, Wu F, Das AK, Choo K-KR, Shen J (2017b) Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Future Gen Comput Syst 68:320–330
Li C-T, Shih D-H, Wang C-C (2018) Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput Methods Prog Biomed 157:191–203
Mishra D, Mukhopadhyay S, Chaturvedi A, Kumari S, Khan MK (2014a) Cryptanalysis and improvement of yan et al.’s biometric-based authentication scheme for telecare medicine information systems. J Med Syst 38(6):24
Mishra D, Mukhopadhyay S, Kumari S, Khan MK, Chaturvedi A (2014b) Security enhancement of a biometric based authentication scheme for telecare medicine information systems with nonce. J Med Syst 38(5):41
Mohit P, Amin R, Karati A, Biswas G, Khan MK (2017) A standard mutual authentication protocol for cloud computing based health care system. J Med Syst 41(4):50
Tan Z et al (2013) An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204
Wu F, Xu L, Kumari S, Li X (2015) A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client–server networks. Comput Electr Eng 45:274–285
Yan X, Li W, Li P, Wang J, Hao X, Gong P (2013) A secure biometrics-based authentication scheme for telecare medicine information systems. J Med Syst 37(5):9972
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chandrakar, P., Sinha, S. & Ali, R. Cloud-based authenticated protocol for healthcare monitoring system. J Ambient Intell Human Comput 11, 3431–3447 (2020). https://doi.org/10.1007/s12652-019-01537-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01537-2