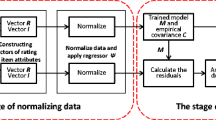
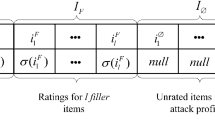
Abstract
Reliability of a recommender system is extremely substantial for the continuity of the system. Malicious users may harm the reliability of predictions by injecting fake profiles called shilling attacks into the system. Therefore, the detection of such attacks is vital for a recommender system. Thus, many shilling attack detection methods have been studied. However, the proposed solutions work only on numerical rating based recommender systems. On the other hand, it has been shown that collaborative filtering systems utilizing binary ratings are also vulnerable to shilling attacks. In this work, we propose a detection method, which finds out six well-known shilling attack models against binary ratings-based collaborative filtering systems. Besides deriving generic attributes from user profiles, we generate additional model-specific attributes in order to deal with fake profiles. Our empirical results show that the proposed method successfully detects attack profiles even with low attack size and filler size values.




Similar content being viewed by others
References
Batmaz Z (2015) Shilling attack design and detection on masked binary data. Master’s thesis, Anadolu University, Turkey
Bhaumik R, Williams C, Mobasher B, Burke R (2006) Securing collaborative filtering against malicious attacks through anomaly detection. In: Proceedings of the 4th workshop on intelligent techniques for web personalization, Boston, MA, USA
Bilge A, Ozdemir Z, Polat H (2014) A novel shilling attack detection method. Proc Comput Sci 31:165–174
Burke R, Mobasher B, Williams C, Bhaumik R (2006a) Classification features for attack detection in collaborative recommender systems. In: Proceedings of the 12th ACM SIGKDD international conference on knowledge discovery and data mining, Philadelphia, PA, USA, pp 542–547
Burke R, Mobasher B, Williams C, Bhaumik R (2006b) Detecting profile injection attacks in collaborative recommender systems. In: Proceedings of the 8th IEEE international conference on E-commerce technology and the 3rd IEEE international conference on enterprise computing, E-commerce, and E-services, San Francisco, CA, USA
Cai H, Zhang F (2018) An unsupervised method for detecting shilling attacks in recommender systems by mining item relationship and identifying target items. Comput J. https://doi.org/10.1093/comjnl/bxy124
Chen K, Chan PP, Yeung DS (2018a) Shilling attack detection using rated item correlation for collaborative filtering. In: IEEE international conference on systems, man, and cybernetics. Miyazaki, Japan, pp 3553–3558
Chen K, Chan PP, Yeung DS (2018b) Unsupervised shilling attack detection model based on rated item correlation analysis. In: 2018 International conference on machine learning and cybernetics, Chengdu, China, vol 2, pp 667–672
Chen K, Chan PP, Zhang F, Li Q (2018c) Shilling attack based on item popularity and rated item correlation against collaborative filtering. Int J Mach Learn Cybern. https://doi.org/10.1007/s13042-018-0861-2
Chirita PA, Nejdl W, Zamfir C (2005) Preventing shilling attacks in online recommender systems. In: Proceedings of the 7th annual ACM international workshop on web information and data management, Bremen, Germany, pp 67–74
Gao M, Yuan Q, Ling B, Xiong Q (2014) Detection of abnormal item based on time intervals for recommender systems. Sci World J. https://doi.org/10.1155/2014/845897
Gunes I, Kaleli C, Bilge A, Polat H (2014) Shilling attacks against recommender systems: a comprehensive survey. Artif Intell Rev 42(4):767–799. https://doi.org/10.1007/s10462-012-9364-9
Hao Y, Zhang P, Zhang F (2018) Multiview ensemble method for detecting shilling attacks in collaborative recommender systems. Secur Commun Netw. https://doi.org/10.1155/2018/8174603
He F, Wang X, Liu B (2010) Attack detection by rough set theory in recommendation system. In: Proceedings of the 2010 IEEE international conference on granular computing, San Jose, CA, USA, pp 692–695
Jiang L, Cheng Y, Yang L, Li J, Yan H, Wang X (2018) A trust-based collaborative filtering algorithm for e-commerce recommendation system. J Ambient Intel Humaniz Comput. https://doi.org/10.1007/s12652-018-0928-7
Kaleli C, Polat H (2013) Robustness analysis of naïve bayesian classifier-based collaborative filtering. Lect Notes Bus Inf 152:202–209. https://doi.org/10.1007/978-3-642-39878-0_19
Lam SK, Riedl J (2004) Shilling recommender systems for fun and profit. In: Proceedings of the 13th international conference on world wide web, New York, NY, USA, pp 393–402
Lee S (2019) Using entropy for similarity measures in collaborative filtering. J Ambient Intel Humaniz Comput. https://doi.org/10.1007/s12652-019-01226-0
Mehta B, Nejdl W (2009) Unsupervised strategies for shilling detection and robust collaborative filtering. User Model User Adapt Interact 19(1–2):65–97. https://doi.org/10.1007/s11257-008-9050-4
Mehta B, Hofmann T, Fankhauser P (2007) Lies and propaganda: detecting spam users in collaborative filtering. In: Proceedings of the 12th international conference on intelligent user interfaces, Honolulu, HI, USA, pp 14–21
Miyahara K, Pazzani MJ (2000) Collaborative filtering with the simple bayesian classifier. In: Proceedings of the 6th pacific rim international conference on artificial intelligence, Melbourne, Australia, pp 679–689
Mobasher B, Burke R, Williams C, Bhaumik R (2006) Analysis and detection of segment-focused attacks against collaborative recommendation. In: Proceedings of the 7th international conference on knowledge discovery on the web: advances in web mining and web usage analysis, Chicago, IL, USA, pp 96–118
Mobasher B, Burke RD, Bhaumik R, Williams C (2007) Toward trustworthy recommender systems: an analysis of attack models and algorithm robustness. ACM Trans Internet Technol 7(4):23. https://doi.org/10.1145/1278366.1278372
Morid MA, Shajari M, Hashemi AR (2014) Defending recommender systems by influence analysis. Inf Retr 17(2):137–152. https://doi.org/10.1007/s10791-013-9224-5
Si M, Li Q (2018) Collaborative recommendation: a robustness analysis. Artif Intell Rev. https://doi.org/10.1145/1031114.1031116
Verstrepen K (2015) Collaborative filtering with binary, positive-only data. PhD thesis, Antwerp University, Belgium
Williams CA, Mobasher B (2006) Profile injection attack detection for securing collaborative recommender systems. DePaul University CTI Technical Report pp 1–47
Williams CA, Mobasher B, Burke R (2007) Defending recommender systems: detection of profile injection attacks. Serv Oriented Comput Appl 1(3):157–170. https://doi.org/10.1007/s11761-007-0013-0
Wu Z, Cao J, Wang Y, Wang Y, Zhang L, Wu J (2018) hPSD: a hybrid PU-learning-based spammer detection model for product reviews. IEEE Trans Cybern. https://doi.org/10.1109/TCYB.2018.2877161
Xia H, Fang B, Gao M, Ma H, Tang Y, Wen J (2015) A novel item anomaly detection approach against shilling attacks in collaborative recommendation systems using the dynamic time interval segmentation technique. Inf Sci 306(C):150–165. https://doi.org/10.1016/j.ins.2015.02.019
Yang F, Gao M, Yu J, Song Y, Wang X (2018) Detection of shilling attack based on bayesian model and user embedding. In: IEEE 30th international conference on tools with artificial intelligence. Volos, Greece, pp 639–646
Yang L, Huang W, Niu X (2017) Defending shilling attacks in recommender systems using soft co-clustering. IET Inf Secur 11(6):319–325. https://doi.org/10.1049/iet-ifs.2016.0345
Yang Z, Cai Z (2017) Detecting abnormal profiles in collaborative filtering recommender systems. J Intell Inf Syst 48(3):499–518. https://doi.org/10.1007/s10844-016-0424-5
Yang Z, Xu L, Cai Z, Xu Z (2016) Re-scale adaboost for attack detection in collaborative filtering recommender systems. Knowl Based Syst 100:74–88. https://doi.org/10.1016/j.knosys.2016.02.008
Zhang F, Chen H (2016) An ensemble method for detecting shilling attacks based on ordered item sequences. Secur Commun Netw 9(7):680–696. https://doi.org/10.1002/sec.1389
Zhang F, Zhou Q (2014) HHT-SVM: an online method for detecting profile injection attacks in collaborative recommender systems. Knowl Based Syst 65:96–105. https://doi.org/10.1016/j.knosys.2014.04.020
Zhang F, Zhou Q (2015) Ensemble detection model for profile injection attacks in collaborative recommender systems based on bp neural network. IET Inf Secur 9(1):24–31. https://doi.org/10.1049/iet-ifs.2013.0145
Zhang F, Deng ZJ, He ZM, Lin XC, Sun LL (2018a) Detection of shilling attack in collaborative filtering recommender system by pca and data complexity. In: 2018 international conference on machine learning and cybernetics, Chengdu, China, vol 2, pp 673–678
Zhang F, Zhang Z, Zhang P, Wang S (2018b) UD-HMM: an unsupervised method for shilling attack detection based on hidden markov model and hierarchical clustering. Knowl Based Syst 148:146–166. https://doi.org/10.1016/j.knosys.2018.02.032
Zhou W, Wen J, Xiong Q, Gao M, Zeng J (2016) SVM-TIA a shilling attack detection method based on svm and target item analysis in recommender systems. Neurocomputing 210:197–205. https://doi.org/10.1016/j.neucom.2015.12.137
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Batmaz, Z., Yilmazel, B. & Kaleli, C. Shilling attack detection in binary data: a classification approach. J Ambient Intell Human Comput 11, 2601–2611 (2020). https://doi.org/10.1007/s12652-019-01321-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01321-2