Abstract
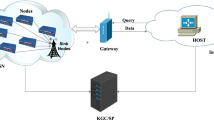
In the modern day world, the Internet of things (IoT) is not a new concept. IoT is getting deployed in various applications and fields. Hence with this fast-growing trend, it is essential to maintain the security in the IoT network. Digital Signature is one of the important ways to authenticate an electronic document or a message during communication. Multiple digital signatures are verified at once through the concept of batch verification. Batch verification of multiple digital signatures reduces the computation load and time. Hence this concept is beneficial in IoT environment where nodes have low computation power and operate in a real-time environment. In this paper, we have developed a Trust Model for IoT which helps the Gateway node to identify the trusted sensor nodes which perform batch verification. The sensor nodes receive a batch of signatures from the Gateway node and verify signatures through batch verification and accordingly send back the results. The trust model that we have developed in this paper significantly reduces the probability of selecting unreliable nodes for verification and also reduces the computation load at Gateway node. We have implemented our trust model and presented the results for batch verification of digital signatures.



Similar content being viewed by others
References
Antipa A, Brown D, Gallant R, Lambert R, Struik R, Vanstone S (2005) Accelerated verification of ecdsa signatures. In: International workshop on selected areas in cryptography, Springer, pp 307–318
Aspernäs A, Simonsson T (2015) Ids on raspberry pi: a performance evaluation
Bao F, Lee CC, Hwang MS (2006) Cryptanalysis and improvement on batch verifying multiple rsa digital signatures. Appl Math Comput 172(2):1195–1200
Boneh D, Gentry C, Lynn B, Shacham H (2003) Aggregate and verifiably encrypted signatures from bilinear maps. In: International conference on the theory and applications of cryptographic techniques, Springer, pp 416–432
Buzzanca M, Carchiolo V, Longheu A, Malgeri M, Mangioni G (2017) Direct trust assignment using social reputation and aging. J Ambient Intell Hum Comput 8(2):167–175
Chan H, Perrig A, Song D (2003) Random key predistribution schemes for sensor networks. In: Security and privacy, 2003. Proceedings. 2003 Symposium on, IEEE, pp 197–213
Changchien SW, Hwang MS, Hwang KF (2002) A batch verifying and detecting multiple rsa digital signatures. Int J Comput Numer Anal Appl 2(3):303–307
Chen H, Wu H, Zhou X, Gao C (2007) Agent-based trust model in wireless sensor networks. In: Eighth ACIS international conference on software engineering, artificial intelligence, networking, and parallel/distributed computing (SNPD 2007), vol 3. IEEE, Qingdao, pp 119–124. https://doi.org/10.1109/SNPD.2007.122
Du W, Deng J, Han YS, Varshney PK, Katz J, Khalili A (2005) A pairwise key predistribution scheme for wireless sensor networks. ACM Trans Inf Syst Secur (TISSEC) 8(2):228–258
Escolar S, Chessa S, Carretero J (2014) Energy management in solar cells powered wireless sensor networks for quality of service optimization. Pers Ubiquitous Comput 18(2):449–464
Fisher R, Ledwaba L, Hancke G, Kruger C (2015) Open hardware: a role to play in wireless sensor networks? Sensors 15(3):6818–6844
Frankel S, Krishnan S (2011) Ip security (ipsec) and internet key exchange (ike) document roadmap (No. RFC 6071)
Ganeriwal S, Balzano LK, Srivastava MB (2008) Reputation-based framework for high integrity sensor networks. ACM Trans Sens Netw (TOSN) 4(3):15
Kalra S, Sood SK (2015) Secure authentication scheme for iot and cloud servers. Pervasive Mob Comput 24:210–223
Kamvar SD, Schlosser MT, Garcia-Molina H (2003) The eigentrust algorithm for reputation management in p2p networks. In: Proceedings of the 12th international conference on World Wide Web, ACM, pp 640–651
Karati S, Das A, Roychowdhury D, Bellur B, Bhattacharya D, Iyer A (2012) Batch verification of ecdsa signatures. In: International conference on cryptology in Africa, Springer, pp 1–18
Kayalvizhi R, Vijayalakshmi M, Vaidehi V (2010) Energy analysis of rsa and elgamal algorithms for wireless sensor networks. In: International conference on network security and applications, Springer, pp 172–180
Kittur AS, Pais AR (2017) Batch verification of digital signatures: approaches and challenges. J Inf Secur Appl 37:15–27
Kittur AS, Jain A, Pais AR (2017) Fast verification of digital signatures in iot. In: International symposium on security in computing and communication, Springer, pp 16–27
Li CT, Hwang MS, Chen S (2010) A batch verifying and detecting the illegal signatures. Int J Innov Comput Inf Control 6(12):5311–5320
Liao YP, Hsiao CM (2014) A secure ecc-based rfid authentication scheme integrated with id-verifier transfer protocol. Ad Hoc Netw 18:133–146
Lim CH, Lee PJ (1994) Security of interactive dsa batch verification. Electron Lett 30(19):1592–1592
Manuel P (2015) A trust model of cloud computing based on quality of service. Ann Oper Res 233(1):281–292
Mármol FG, Pérez GM (2011) Providing trust in wireless sensor networks using a bio-inspired technique. Telecommun Syst 46(2):163–180
Maurya M, Shukla SR (2013) Current wireless sensor nodes (motes): performance metrics and constraints. Int J Adv Res Electron Commun Eng 2(1):045
Miller VS (2004) The weil pairing, and its efficient calculation. J Cryptol 17(4):235–261
Mitra N, Lafon Y et al (2003) Soap version 1.2 part 0: primer. W3C Recomm 24:12
Naccache D, M’RaÏhi D, Vaudenay S, Raphaeli D (1994) Can dsa be improved?—complexity trade-offs with the digital signature standard. In: Workshop on the theory and application of of cryptographic techniques, Springer, pp 77–85
Pastuszak J, Michałek D, Pieprzyk J, Seberry J (2000) Identification of bad signatures in batches. In: International workshop on public key cryptography, Springer, pp 28–45
Peukert D (1987) Die Weimarer Republik, vol 9. VEB Deutscher Verlag für Musik, Leipzeg
Pham C (2014) Communication performances of ieee 802.15. 4 wireless sensor motes for data-intensive applications: a comparison of waspmote, arduino mega, telosb, micaz and imote2 for image surveillance. J Netw Comput Appl 46:48–59
Ren Y, Wang S, Zhang X, Hwang MS (2015) An efficient batch verifying scheme for detecting illegal signatures. IJ Netw Secur 17(4):463–470
Rescorla E, Modadugu N (2012) Rfc 6347, datagram transport layer security version 1.2. Internet Eng Task Force 13:101
Selcuk AA, Uzun E, Pariente MR (2004) A reputation-based trust management system for p2p networks. In: ccgrid, IEEE, pp 251–258
Vu QAN, Canal R, Gaudou B, Hassas S, Armetta F (2012) Trustsets: using trust to detect deceitful agents in a distributed information collecting system. J Ambient Intell Hum Comput 3(4):251–263
Wander AS, Gura N, Eberle H, Gupta V, Shantz SC (2005) Energy analysis of public-key cryptography for wireless sensor networks. In: Pervasive computing and communications, 2005. PerCom 2005. Third IEEE international conference on, IEEE, pp 324–328
Wu F, Rüdiger C, Yuce MR (2017a) Real-time performance of a self-powered environmental iot sensor network system. Sensors 17(2):282
Wu F, Xu L, Kumari S, Li X (2017b) A privacy-preserving and provable user authentication scheme for wireless sensor networks based on internet of things security. J Ambient Intell Hum Comput 8(1):101–116
Wu F, Xu L, Kumari S, Li X, Das AK, Shen J (2018) A lightweight and anonymous rfid tag authentication protocol with cloud assistance for e-healthcare applications. J Ambient Intell Hum Comput 9(4):919–930
Xiong L, Liu L (2004) Peertrust: supporting reputation-based trust for peer-to-peer electronic communities. IEEE Trans Knowl Data Eng 16(7):843–857
Zhang Y, Deng RH, Han G, Zheng D (2018) Secure smart health with privacy-aware aggregate authentication and access control in internet of things. J Netw Comput Appl 123:89–100
Zhiwei G, Yingxin H, Kai L (2015) Cptias: a new fast pki authentication scheme based on certificate path trust index. J Ambient Intell Hum Comput 6(6):721–731
Zhou R, Hwang K (2007) Powertrust: a robust and scalable reputation system for trusted peer-to-peer computing. IEEE Trans Parallel Distrib Syst 4:460–473
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kittur, A.S., Pais, A.R. A trust model based batch verification of digital signatures in IoT. J Ambient Intell Human Comput 11, 313–327 (2020). https://doi.org/10.1007/s12652-019-01289-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01289-z