Abstract
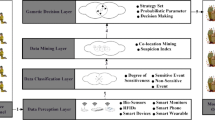
Developments in Internet of Things (IoT) Technology have been effectively utilized in different industrial sectors for monitoring, surveillance, and remote decision-making. The ability to acquire in-depth information about ubiquitous events has proliferated numerous opportunities for using this technology in sensitive domains like national defence security. In this paper, a comprehensive IoT-based framework is presented for analyzing national integrity of defence personnel with consideration to his/her daily activities. As reported by investigating agencies of many countries, routinely engagements of defence personnel are one of the premier reasons for vulnerability to national defence through intentional and unintentional information outflow of defence secrets. The work presented in this research is focused on monitoring various activities of defence personnel to determine his/her integral behavior in daily life. Specifically, Integrity Index Value is defined for every defence personnel based on different social engagements, and activities for detecting the vulnerability to national security. In addition to this, a probabilistic decision tree based automated decision making is presented to aid defence officials in analyzing various activities of a defence personnel for his/her integrity assessment. In order to validate the proposed framework, three challenging data sets have been considered for experimental evaluation. The computed results are compared with the state-of-the-art techniques for overall assessment. Results show that the proposed model achieves better performance in monitoring and analyzing activities of defence personnel for effective decision making.





Similar content being viewed by others
References
Aggarwal CC, Zhai C (2012) Mining text data. Springer
Al-Fuqaha A, Guizani M, Mohammadi M, Aledhari M, Ayyash M (2015) Internet of Things: a survey on enabling technologies, protocols and applications. IEEE Commun Surveys Tutor 17:2347–2376. doi:10.1109/COMST.2015.2444095
Antoni A, Marjanovi M, Pripui K, Arko IP (2016) A mobile crowd sensing ecosystem enabled by CUPUS: cloud-based publish/subscribe middleware for the Internet of Things. Futur Gener Comput Syst 56:607–622. doi:10.1016/j.future.2015.08.005
Baba AI, Lu H, Pedersen TB, Xie X (2013) A graph model for false negative handling in indoor RFID tracking data. In: 21st ACM International Conference on Advances in Geographic Information Systems. ACM. doi:10.1145/2525314.2525461
Bjelopera JP, Randol MA (2011) The federal bureau of investigation and terrorism investigations. Congressional Research Service, Library of Congress. https://fas.org/sgp/crs/terror/R41780.pdf. Accessed 10 Jan 2016
Bosch X (2012) Beyond 9/11: health consequences of the terror attacks outside the USA. Intern Emerg Med 7:159–161. doi:10.1007/s11739-011-0748-7
Chen T, Lehr J, Lavrova O, Martinez-Ramonz M (2016) Distribution-level peak load prediction based on Bayesian additive regression trees. In Power and Energy Society General Meeting (PESGM), IEEE. doi:10.1109/PESGM.2016.7741565
Chen Z, Xia F, Huang T, Bu F, Wang H (2013) A localization method for the Internet of Things. J Supercomput 63:657–674. doi:10.1007/s11227-011-0693-2
Chiremsel Z, Said RN, Chiremsel R (2016) Probabilistic fault diagnosis of safety instrumented systems based on fault tree analysis and Bayesian network. J Fail Anal Prevent 16:747–760. doi:10.1007/s11668-016-0140-z
Darwish M, Almouahed S, de Lamotte F (2017) The integration of expert-defined importance factors to enrich Bayesian fault tree analysis. Reliab Eng Syst Saf 162:81–90. doi:10.1016/j.ress.2017.01.007
De Martino B, Kumaran D, Seymour B, Dolan RJ (2006) Frames, biases, and rational decision-making in the human brain. Science 313:684–687. doi:10.1126/science.1128356
Dean J, Ghemawat S (2008) MapReduce: simplified data processing on large clusters. Commun ACM 51:107–113. doi:10.1145/1327452.1327492
Ding G, Guo Y, Zhou J, Gao Y (2016) Large-scale cross-modality search via collective matrix factorization hashing. IEEE Trans Image Process 25:5427–5440. doi:10.1109/TIP.2016.2607421
Fang S, Xu L, Pei H, Liu Y, Liu Z, Zhu Y, Zhang H (2014) An integrated approach to snowmelt flood forecasting in water resource management. IEEE Trans Ind Inf 10:548–558. doi:10.1109/TII.2013.2257807
Feng DG, Zhang M, Zhang Y, Xu Z (2011) Study on cloud computing security. J Softw 22:71–83
Flouvat F, Nguyen Van Soc JF, Desmier E, Selmaoui-Folcher N (2015) Domain-driven co-location mining. Geoinformatica 19:147–183. doi:10.1007/s10707-014-0209-3
Ganz F, Barnaghi P, Carrez F (2013) Information abstraction for heterogeneous real world internet data. IEEE Sens J 13:3793–3805. doi:10.1109/JSEN.2013.2271562
Gubbi J, Buyya R, Marusic S, Palaniswami M (2013) Internet of Things (IoT): a vision, architectural elements, and future directions. Futur Gener Comput Syst 29:1645–1660. doi:10.1016/j.future.2013.01.010
Harte N, Gillen E (2015) TCD-TIMIT: an audio-visual corpus of continuous speech. IEEE Trans Multimed 17:603–615. doi:10.1109/TMM.2015.2407694
Harwood B, Drummond T (2016) FANNG: fast approximate nearest neighbour graphs. IEEE Conf Comput Vis Patt Recognit (CVPR). doi:10.1109/CVPR.2016.616
Hirsch M, Carli P, Nizard R, Riou B, Baroudjian B, Baubet T, Fontaine JP (2015) The medical response to multisite terrorist attacks in Paris. Lancet 386:2535–2538. doi:10.1016/S0140-6736(15)01063-6
Holmes G, Donkin A, Witten IH (1994) Weka: a machine learning workbench. IEEE, In Intelligent Information Systems. doi:10.1109/ANZIIS.1994.396988
Hsieh CK, Tangmunarunkit H, Alquaddoomi F, Jenkins J, Kang J, Ketcham C, Estrin D (2013) Lifestreams: a modular sense-making toolset for identifying important patterns from everyday life. In: Proceedings of the 11th ACM Conference on Embedded Networked Sensor Systems. ACM. doi:10.1145/2517351.2517368
Keller JM, Gray MR, Givens JA (1985) A fuzzy k-nearest neighbor algorithm. IEEE Trans Syst Man Cybern 4:580–585
Kelly SDT, Suryadevara NK, Mukhopadhyay SC (2013) Towards the implementation of IoT for environmental condition monitoring in homes. IEEE Sens J 13:3846–3853. doi:10.1109/JSEN.2013.2263379
Kontschieder P, Fiterau M, Criminisi A, Rota Bulo S (2015) Deep neural decision forests. IEEE Int Conf Comput Vis (ICVR). doi:10.1109/ICCV.2015.172
Kronstadt KA (2008) Terrorist attacks in Mumbai, India, and implications for US interests. Library of Congress Washington DC Congressional Research Service. http://www.dtic.mil/get-tr-doc/pdf?AD=ADA492902. Accessed 2 Jan 2016
Kumar S, Udupa R (2011) Learning hash functions for cross-view similarity search. Int Joint Conf Artif Intel. doi:10.5591/978-1-57735-516-8/IJCAI11-230
Le Bas C, Sahuguede S, Julien-Vergonjanne A (2017) Theoretical and experimental approach for the design of an optical wireless physical activity monitoring system. Int J Wirel Inf Netw. doi:10.1007/s10776-017-0337-4
Lee J, Fan Y, Sisson SA (2015) Bayesian threshold selection for extremal models using measures of surprise. Comput Stat Data Anal 85:84–99. doi:10.1016/j.csda.2014.12.004
Lee L, Romano R, Stein G (2000) Monitoring activities from multiple video streams: establishing a common coordinate frame. IEEE Trans Patt Anal Mach Intell 22:758–767. doi:10.1109/34.868678
Li J, Stones RJ, Wang G, Liu X, Li Z, Xu M (2017) Hard drive failure prediction using Decision Trees. Reliab Eng Syst Saf 164:55–65. doi:10.1016/j.ress.2017.03.004
Li S, Da Xu L, Wang X (2013) Compressed sensing signal and data acquisition in wireless sensor networks and internet of things. IEEE Trans Ind Inf 9:2177–2186. doi:10.1109/TII.2012.2189222
Liang M, Hu X (2015) Recurrent convolutional neural network for object recognition. IEEE Conf Comput Vis Patt Recognit (CVPR). doi:10.1109/CVPR.2015.7298958
Lin J, Keogh E, Wei L, Lonardi S (2007) Experiencing sax: a novel symbolic representation of time series. Data Min Knowl Disc 15:107–144. doi:10.1007/s10618-007-0064-z
Lin Z, Ding G, Han J, Wang J (2016) Cross-view retrieval via probability-based semantics-preserving hashing. IEEE Trans Cybern. doi:10.1109/TCYB.2016.2608906
Liu Y, Xu L, Li M (2016) The parallelization of back propagation neural network in MapReduce and spark. Int J Parallel Program. doi:10.1007/s10766-016-0401-1
Lu G, Yan Y, Sebe N, Kambhamettu C (2014) Knowing where i am: exploiting multi-task learning for multi-view indoor image-based localization. BMVC. doi:10.5244/C.28.125
Manikonda L, Mangalampalli A, Pudi V (2010) UACI: Uncertain associative classifier for object class identification in images. Image Vis Comput N Z (IVCNZ). doi:10.1109/IVCNZ.2010.6148859
Maurer U, Smailagic A, Siewiorek DP, Deisher M (2006) International Workshop on Wearable and Implantable Body Sensor Networks. In: IEEE, Activity recognition and monitoring using multiple sensors on different body positions. doi:10.1109/BSN.2006.6
Mavroforakis ME, Theodoridis S (2005) IEEE, Support Vector Machine (SVM) classification through geometry
Meucci F, Pierucci L, Prasad N (2011) Identity theft detection based on neural network non-linearity identification in OFDM system. In: 2011 IEEE International Conference on Communications (ICC). IEEE
Najafi B, Aminian K, Paraschiv-Ionescu A, Loew F, Bula CJ, Robert P (2003) Ambulatory system for human motion analysis using a kinematic sensor: monitoring of daily physical activity in the elderly. IEEE Trans Biomed Eng 50:711–723. doi:10.1109/TBME.2003.812189
Narula S, Jain A (2015) Cloud computing security: Amazon web service. Adv Comput Commun Technol (ACCT) IEEE. doi:10.1109/ACCT.2015.20
ONS Database. https://www.ons.gov.uk/. Accessed 17 March 2017
Panahi N, Shayesteh MG, Mihandoost S, Varghahan BZ (2011) Recognition of different datasets using PCA, LDA, and various classifiers. In: Application of Information and Communication Technologies (AICT). IEEE. doi:10.1109/ICAICT.2011.6110912
Payal A, Rai CS, Reddy BVR (2014) Artificial neural networks for developing localization framework in wireless sensor networks. In: Data Mining and Intelligent Computing (ICDMIC),IEEE. doi:10.1109/ICDMIC.2014.6954228
Qian F, Yin L, He Q, He J (2009) Mining spatio-temporal co-location patterns with weighted sliding window. IEEE Int Conf Intell Comput Intell Syst 3:181–185. doi:10.1109/ICICISYS.2009.5358192
Rokach L, Maimon O (2014) Data mining with decision trees: theory and applications. World scientific
Schmid H (2013) Probabilistic part-ospeech tagging using decision trees. In: New methods in language processing. Routledge
Song J, Yang Y, Yang Y, Huang Z, Shen HT (2013) Inter-media hashing for large-scale retrieval from heterogeneous data sources. Int Conf Manag Data. doi:10.1145/2463676.2465274
Sparapani RA, Logan BR, McCulloch RE, Laud PW (2016) Nonparametric survival analysis using bayesian additive regression trees (bart). Stat Med. doi:10.1002/sim.6893
St J, Oniga S, Buchman A (2015) Real time human activity monitoring. Ann Math Inf 44:187–196. http://ami.ektf.hu/uploads/papers/finalpdf/AMI44 from187to196.pdf. Accessed 10 Jan 2016
Sundaram VM, Paneer P (2012) Discovering co-location patterns from spatial domain using a delaunay approach. Proc Eng 38:2832–2845. doi:10.1016/j.proeng.2012.06.332
Tong S, Chang E (2001) Support vector machine active learning for image retrieval. Ninth ACM Int Conf Multimed. doi:10.1145/500141.500159
Vale L, Brito M, Henriques J, Carvalho P, Pena A, Santiago F (2010) LifeStream: real-time bio-signal remote monitoring system. In: 4th International Conference In Bioinformatics and Biomedical Engineering (ICBBE). IEEE. doi:10.1109/ICBBE.2010.5514665
Wang L, Tao J, Ranjan R, Marten H, Streit A, Chen J, Chen D (2013) G-Hadoop: MapReduce across distributed data centers for data-intensive computing. Futur Gener Compu Syst 29:739–750. doi:10.1016/j.future.2012.09.001
Xia Y, Liu C, Li Y, Liu N (2017) A boosted decision tree approach using Bayesian hyper-parameter optimization for credit scoring. Expert Syst Appl 78:225–241. doi:10.1016/j.eswa.2017.02.017
Xu L, He W, Li S (2014) Internet of Things in industries: a survey. IEEE Trans Ind Inf 10:2233–2243. doi:10.1109/TII.2014.2300753
Xu Y, Agyemang B, Wu S, Liu M (2017) Procedure graph model for automatic RFID data processing service management. IEEE Internet Things J. doi:10.1109/JIOT.2017.2661326
Yang CC, Hsu YL (2010) A review of accelerometry-based wearable motion detectors for physical activity monitoring. Sensors 10:7772–7788. doi:10.3390/s100807772
Zhang GA, Gu JY, Bao ZH, Xu C, Zhang SB (2014) Joint routing and channel assignment algorithms in cognitive wireless mesh networks. Trans Emerg Telecommun Technol 25:294–307. doi:10.1002/ett.2560
Zhao S, Yao H, Sun X (2013) Video classification and recommendation based on affective analysis of viewers. Neurocomputing 119:101–110. doi:10.1016/j.neucom.2012.04.042
Zhao S, Yao H, Gao Y, Ji R, Ding G (2016) Continuous probability distribution prediction of image emotions via multi-task shared sparse regression. IEEE Trans Multimed. doi:10.1109/TMM.2016.2617741
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Bhatia, M., Sood, S.K. Internet of Things based activity surveillance of defence personnel. J Ambient Intell Human Comput 9, 2061–2076 (2018). https://doi.org/10.1007/s12652-017-0507-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-017-0507-3