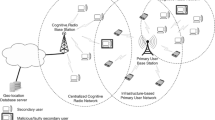
Abstract
Integrating cognitive radio (CR) with traditional wireless networks is helping solve the problem of spectrum scarcity in an efficient manner. The opportunistic and dynamic spectrum access features of CR provide the functionality to its unlicensed users to utilize the underutilized spectrum at the time of need because CR nodes can sense vacant bands of spectrum and can also access them to carry out communication. Various capabilities of CR nodes depend upon efficient and continuous reporting of data with each other and centralized base stations, which in turn can cause leakage in privacy. Experimental studies have shown that the privacy of CR users can be compromised easily during the cognition cycle, because they are knowingly or unknowingly sharing various personally identifiable information (PII), such as location, device ID, signal status, etc. In order to preserve this privacy leakage, various privacy preserving strategies have been developed by researchers, and according to us differential privacy is the most significant among them. In this article, we provide a thorough survey on how differential privacy can play an active role in preserving privacy of cognitive radio networks (CRN). Firstly, we provide a thorough comparison of our work with other similar studies to show its novelty and contribution, and afterwards, we provide a thorough analysis from the perspective of various CR scenarios which can cause privacy leakage. After that, we carry out an in-depth assessment from the perspective of integration of differential privacy at different levels of CRN. Then, we discuss various parameters which should be considered while integrating differential privacy in CRN alongside providing a comprehensive discussion about all integrations of differential privacy carried out till date. Finally, we provide discussion about prospective applications, challenges, and future research directions. The discussion about integration of differential privacy in different CR scenarios indicates that differential privacy is one of the most viable mechanisms to preserve privacy of CRN in modern day scenarios. From the discussion in the article, it is evident that the proposed integration of differential privacy can pave the way for futuristic CRN in which CR users will be able to share information during the cognition cycle without the risk of losing their private information.





Similar content being viewed by others
References
Statista. Number of mobile devices worldwide 2020–2024, [Online]: https://www.statista.com/statistics/245501/multiple-mobile-device-ownership-worldwide/.
Sharma RK, Rawat DB. Advances on security threats and countermeasures for cognitive radio networks: A survey. IEEE Comm Surveys Tutor. 2014;17(2):1023–43.
Ahmad A, Ahmad S, Rehmani MH, Hassan NU. A survey on radio resource allocation in cognitive radio sensor networks. IEEE Comm Surveys Tutor. 2015;17(2):888–917.
Ali A, Kwak KS, Tran NH, Han Z, Niyato D, Zeshan F, Gul MT, Suh DY. Raptorq-based efficient multimedia transmission over cooperative cellular cognitive radio networks. IEEE Trans Veh Technol. 2018;67(8):7275–89.
Mitola J, Maguire GQ. Cognitive radio: making software radios more personal. IEEE Pers Commun. 1999;6(4):13–8.
Boulogeorgos AAA, Salameh HAB, Karagiannidis GK. Spectrum sensing in full-duplex cognitive radio networks under hardware imperfections. IEEE Trans Veh Technol. 2017;66(3):2072–84.
Wei Z, Feng Z, Zhang Q, Li W. Three regions for space-time spectrum sensing and access in cognitive radio networks. IEEE Trans Veh Technol. 2015;64(6):2448–62.
Akhtar F, Rehmani MH, Reisslein M. White space: Definitional perspectives and their role in exploiting spectrum opportunities. Telecomm Policy. 2016;40(4):319–31.
Sharma SK, Bogale TE, Chatzinotas S, Ottersten B, Le LB, Wang X. Cognitive radio techniques under practical imperfections: A survey. IEEE Commun Surv Tutor. 2015;17(4):1858–84.
Grissa M, Hamdaoui B, Yavuza AA. Location privacy in cognitive radio networks: A survey. IEEE Commun Surv Tutor. 2017;19(3):1726–60.
Bhattacharjee S, Sengupta S, Chatterjee M. Vulnerabilities in cognitive radio networks: A survey. Comput Commun. 2013;36(13):1387–98.
Wang W, Zhang Q. Location privacy preservation in cognitive radio networks. Springer. 2014.
Hamamreh JM, Furqan HM, Arslan H. Classifications and applications of physical layer security techniques for confidentiality: A comprehensive survey. IEEE Commun Surv Tutor. 2018;21(2):1773–828.
Salahdine F, Kaabouch N. Security threats, detection, and countermeasures for physical layer in cognitive radio networks: A survey. Physical Commun. 2020;39:101001.
Errapotu SM, Wang J, Li X, Lu Z, Li W, Pan M, Han Z. Bid privacy preservation in matching-based multiradio multichannel spectrum trading. IEEE Trans Veh Technol. 2018;67(9):8336–47.
Grissa M, Yavuz A, Hamdaoui B. An efficient technique for protecting location privacy of cooperative spectrum sensing users. In IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). 2016:915–920.
Wen T, Zhu Y, Liu T. P2: A location privacy-preserving auction mechanism for mobile crowd sensing. In 2016 IEEE Global Communications Conference (GLOBECOM). 2016:1–6.
Grissa M, Yavuz AA, Hamdaoui B. Location privacy in cognitive radios with multi-server private information retrieval. IEEE Trans Cogn Comm Network. 2019;5(4):949–62.
Gao Z, Zhu H, Liu Y, Li M, Cao Z. Location privacy in database-driven cognitive radio networks: Attacks and countermeasures. In Proceedings IEEE INFOCOM. 2013:2751–2759.
Grissa M, Yavuz AA, Hamdaoui B. When the hammer meets the nail: Multi-server pir for database-driven crn with location privacy assurance. In IEEE Conference on Communications and Network Security (CNS). 2017:1–9.
Xin J, Li M, Luo C, Li P. Privacy-preserving spectrum query with location proofs in database-driven crns. in IEEE Global Communications Conference (GLOBECOM). 2016:1–6.
Dwork C. Differential privacy: A survey of results. In International conference on theory and applications of models of computation. Springer. 2008:1–19.
Amjad M, Rehmani MH, Mao S. Wireless multimedia cognitive radio networks: A comprehensive survey. IEEE Comm Surveys Tutor. 2018;20(2):1056–103.
Amjad M, Akhtar F, Rehmani MH, Reisslein M, Umer T. Full-duplex communication in cognitive radio networks: A survey. IEEE Comm Surveys Tutor. 2017;19(4):2158–91.
Naeem A, Rehmani MH, Saleem Y, Rashid I, Crespi N. Network coding in cognitive radio networks: A comprehensive survey. IEEE Comm Surveys Tutor. 2017;19(3):1945–73.
Palguna DS, Love DJ, Pollak I. Secondary spectrum auctions for markets with communication constraints. IEEE Trans Wireless Commun. 2016;15(1):116–30.
Akyildiz IF, Lee W-Y, Vuran MC, Mohanty S. Next generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Comput Netw. 2006;50(13):2127–59.
Martinez Alonso R, Plets D, Deruyck M, Martens L, Guillen Nieto G, Joseph W. Multi-objective optimization of cognitive radio networks. Comput Netw. 2021;184:107651. https://www.sciencedirect.com/science/article/pii/S138912862031269X
Ding G, Jiao Y, Wang J, Zou Y, Wu Q, Yao Y-D, Hanzo L. Spectrum inference in cognitive radio networks: Algorithms and applications. IEEE Comm Surveys Tutor. 2017;20(1):150–82.
Khalek NA, Hamouda W. From cognitive to intelligent secondary cooperative networks for the future internet: Design, advances, and challenges. IEEE Network in Print. 2020:1–8.
Prathima A, Gurjar DS, Nguyen HH, Bhardwaj A. Performance analysis and optimization of bidirectional overlay cognitive radio networks with hybrid-swipt. IEEE Trans Veh Technol. 2020;69(11):13467–81.
Martin JH, Dooley LS, Wong KCP. New dynamic spectrum access algorithm for tv white space cognitive radio networks. IET Commun. 2016;10(18):2591–7.
Jiang B, Li J, Yue G, Song H. Differential privacy for industrial internet of things: Opportunities, applications and challenges. IEEE Internet Things J. In Print. 2021:1–1.
Wang T, Zheng Z, Rehmani MH, Yao S, Huo Z. Privacy preservation in big data from the communication perspective-a survey. IEEE Comm Surveys Tutor. 2018;21(1):753–78.
Soria-Comas J, Domingo-Ferrer J, Sanchez D, Meguas D. Individual differential privacy: A utility-preserving formulation of differential privacy guarantees. IEEE Trans Inf Forensics Secur. 2017;12(6):1418–29.
Hassan MU, Rehmani MH, Chen J. Differential privacy techniques for cyber physical systems: a survey. IEEE Comm Surveys Tutor. 2020;22(1):746–89.
Grissa M, Yavuz AA, Hamdaoui B. Preserving the location privacy of secondary users in cooperative spectrum sensing. IEEE Trans Inf Forensics Secur. 2017;12(2):418–31.
Tashman DH, Hamouda W. An overview and future directions on physical-layer security for cognitive radio networks. IEEE Netw. 2020:1–7.
Zhang X-G, Yang G-H, Wasly S. Man-in-the-middle attack against cyber-physical systems under random access protocol. Inf Sci. 2021;576:708–24.
Clark MA, Psounis K. Trading utility for privacy in shared spectrum access systems. IEEE/ACM Trans Networking. 2018;26(1):259–73.
Weiss MBH, Werbach K, Sicker DC, Bastidas CEC. On the application of blockchains to spectrum management. IEEE Trans Cogn Commun Netw. 2019;5(2):193–205.
Vakilinia I, Sengupta S. Vulnerability market as a public-good auction with privacy preservation. Comput Secur. 2020;93:101807.
Mundhe P, Verma S, Venkatesan S. A comprehensive survey on authentication and privacy-preserving schemes in vanets. Comp Sci Rev. 2021;41:100411.
Zhang R, Xue R, Liu L. Searchable encryption for healthcare clouds: A survey. IEEE Trans Serv Comput. 2018;11(6):978–96.
Alahmadi A, Abdelhakim M, Ren J, Li T. Defense against primary user emulation attacks in cognitive radio networks using advanced encryption standard. IEEE Trans Inf Forensics Secur. 2014;9(5):772–81.
Cai Y, Chen X, Tian L, Wang Y, Yang H. Enabling secure nvm-based in-memory neural network computing by sparse fast gradient encryption. IEEE Trans Comput. 2020;69(11):1596–610.
Kasiri B, Lambadaris I, Yu FR, Tang H. Privacy-preserving distributed cooperative spectrum sensing in multi-channel cognitive radio manets, in. IEEE International Conference on Communications (ICC). 2015;2015:7316–21.
Teng Z, Du W. Comparisons of k-anonymization and randomization schemes under linking attacks. In Sixth International Conference on Data Mining (ICDM’06). 2006:1091–1096.
Ouafae B, Mariam R, Oumaima L, Abdelouahid L. Data anonymization in social networks state of the art, exposure of shortcomings and discussion of new innovations. In 1st International Conference on Innovative Research in Applied Science, Engineering and Technology (IRASET). 2020:1–10.
Kalamkar SS, Jeyaraj JP, Banerjee A, Rajawat K. Resource allocation and fairness in wireless powered cooperative cognitive radio networks. IEEE Trans Commun. 2016;64(8):3246–61.
Zhu R, Li Z, Wu F, Shin K, Chen G. Differentially private spectrum auction with approximate revenue maximization. In Proceedings of the 15th ACM international symposium on mobile ad hoc networking and computing. 2014:185–194.
Liu J, Zhang C, Lorenzo B, Fang Y. DPavatar: a real-time location protection framework for incumbent users in cognitive radio networks. IEEE Trans Mob Comput. 2019;19(3):552–65.
Dong X, Gong Y, Ma J, Guo Y. Protecting operation-time privacy of primary users in downlink cognitive two-tier networks. IEEE Trans Veh Technol. 2018;67(7):6561–72.
Diruai EM, Sobabe GC, Bai X, Guo B. Spectrum sensing based on channel holding time. In 2017 10th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI). 2017:1–5.
Pei Y, Hoang AT, Liang Y-C. Sensing-throughput tradeoff in cognitive radio networks: How frequently should spectrum sensing be carried out? In 18th International Symposium on Personal, Indoor and Mobile Radio Communications. IEEE. 2007:1–5.
Zhang Z, Wen X, Xu H, Yuan L. Sensing nodes selective fusion scheme of spectrum sensing in spectrum-heterogeneous cognitive wireless sensor networks. IEEE Sens J. 2018;18(1):436–45.
Bhattarai S, Vaka PR, Park J. Thwarting location inference attacks in database-driven spectrum sharing. IEEE Trans Cogn Commun Netw. 2018;4(2):314–27.
Georgiadou Y, de By RA, Kounadi O. Location privacy in the wake of the gdpr. ISPRS Int J Geo Inf. 2019;8(3):157.
Commission FC et al. Order on reconsideration and second report and order. 2016;FCC-16-55.
Asoodeh S, Liao J, Calmon FP, Kosut O, Sankar L. Three variants of differential privacy: Lossless conversion and applications. IEEE J Selected Areas Inf Theory, in Print. 2021.
Chen X, Zhang T, Shen S, Zhu T, Xiong P. An optimized differential privacy scheme with reinforcement learning in vanet. Computers & Security. 2021;110:102446.
Mao Y, Chen T, Zhang Y, Wang T, Zhong S. Towards privacy-preserving aggregation for collaborative spectrum sensing. IEEE Trans Inf Forensics Secur. 2017;12(6):1483–93.
Li S, Zhu H, Gao Z, Guan X, Xing K, Shen X. Location privacy preservation in collaborative spectrum sensing. In Proceedings IEEE INFOCOM. 2012:729–737.
Hassan MU, Rehmani MH, Chen J. DEAL: Differentially Private Auction for Blockchain-Based Microgrids Energy Trading. IEEE Trans Serv Comput. 2020;13(2):263–75.
Yin C, Xi J, Sun R, Wang J. Location privacy protection based on differential privacy strategy for big data in industrial internet of things. IEEE Trans Industr Inf. 2018;14(8):3628–36.
Fan L. Practical Image Obfuscation with Provable Privacy. In IEEE International Conference on Multimedia and Expo (ICME). 2019.
Roman N, Corn M, Diaci J. Sharing economy: Implementing decentralized privacy-preserving parking system. In IEEE International Conference on Smart Internet of Things (SmartIoT). 2020:109–116.
Xin C, Song M. Analysis of the on-demand spectrum access architecture for cbrs cognitive radio networks. IEEE Trans Wireless Commun. 2020;19(2):970–8.
Yang Y, Zhang Q, Wang Y, Emoto T, Akutagawa M, Konaka S. Multi-strategy dynamic spectrum access in cognitive radio networks: Modeling, analysis and optimization. China Communications. 2019;16(3):103–21.
Gomez-Cuba F, Asorey-Cacheda R, Gonzalez-Castano FJ, Huang H. Application of cooperative diversity to cognitive radio leasing: Model and analytical characterization of resource gains. IEEE Trans Wireless Commun. 2013;12(1):40–9.
Sajid A, Khalid B, Ali M, Mumtaz S, Masud U, Qamar F. Securing cognitive radio networks using blockchains. Futur Gener Comput Syst. 2020;108:816–26.
Barthe G, Gaboardi M, Grgoire B, Hsu J, Strub P. Proving differential privacy via probabilistic couplings. In 31st Annual ACM/IEEE Symposium on Logic in Computer Science (LICS). 2016:1–10.
Hassan MU, Rehmani MH, Faheem Y. Performance evaluation of broadcasting strategies in cognitive radio networks. Wireless Netw. 2019;25(3):999–1016.
Saleem Y, Rehmani MH. Primary radio user activity models for cognitive radio networks: A survey. J Netw Comput Appl. 2014;43:1–16.
Bansal T, Li D, Sinha P. Opportunistic channel sharingin cognitive radio networks. IEEE Trans Mob Comput. 2014;13(4):852–65.
Tsiropoulos GI, Dobre OA, Ahmed MH, Baddour KE. Radio resource allocation techniques for efficient spectrum access in cognitive radio networks. IEEE Comm Surveys Tutor. 2016;18(1):824–47.
Hassan MR, Karmakar GC, Kamruzzaman J, Srinivasan B. Exclusive use spectrum access trading models in cognitive radio networks: A survey. IEEE Comm Surveys Tutor. 2017;19(4):2192–231.
Mochaourab R, Holfeld B, Wirth T. Distributed channel assignment in cognitive radio networks: Stable matching and walrasian equilibrium. IEEE Trans Wireless Commun. 2015;14(7):3924–36.
Chen Z, Qiu RC. Q-learning based bidding algorithm for spectrum auction in cognitive radio, in. Proceedings of IEEE Southeastcon. 2011;2011:409–12.
Yi C, Cai J. Ascending-price progressive spectrum auction for cognitive radio networks with power-constrained multiradio secondary users. IEEE Trans Veh Technol. 2018;67(1):781–94.
Wang Z, Li J, Hu J, Ren J, Li Z, Li Y. Towards privacy-preserving incentive for mobile crowdsensing under an untrusted platform. In IEEE INFOCOM 2019 - IEEE Conference on Computer Communications. 2019:2053–2061.
Li T, Jung T, Qiu Z, Li H, Cao L, Wang Y. Scalable privacy-preserving participant selection for mobile crowdsensing systems: Participant grouping and secure group bidding. IEEE Trans Netw Sci Eng. 2020;7(2):855–68.
Ni T, Chen Z, Xu G, Zhang S, Zhong H. Differentially private double auction with reliability-aware in mobile crowd sensing. Ad Hoc Netw. 2021;114:102450.
Grissa M, Yavuz AA, Hamdaoui B. Trustsas: A trustworthy spectrum access system for the 3.5 ghz cbrs band. In IEEE INFOCOM 2019 - IEEE Conference on Computer Communications. 2019:1495–1503.
Wang J, Errapotu SM, Gong Y, Qian L, Jantti R, Pan M, Han Z. Data-driven optimization based primary users operational privacy preservation. IEEE Trans Cogn Comm Netw. 2018;4(2):357–67.
Zhang Y, Lee C, Niyato D, Wang P. Auction approaches for resource allocation in wireless systems: A survey. IEEE Comm Surveys Tutor. 2013;15(3):1020–41.
Kasiri B, Lambadaris I, Yu FR, Tang H. Privacy-preserving distributed cooperative spectrum sensing in multi-channel cognitive radio manets. In IEEE International Conference on Communications (ICC). 2015:7316–7321.
Yan Y, Dong A, Zheng H, Sun Y. Privacy-preserving spectrum allocation in cognitive radio networks based on truthful online double auction mechanism. Procedia Comp Sci. 2020;174:304–8.
Dai Y, Wu J, Du X. Hierarchical and hybrid: Mobility-compatible database-assisted framework for dynamic spectrum access. IEEE Trans Netw Sci Eng. 2020;7(1):216–26.
Kaaniche N, Laurent M, Belguith S. Privacy enhancing technologies for solving the privacy-personalization paradox: Taxonomy and survey. J Netw Comput Appl. 2020:102807
Wu D, Wu X, Gao J, Ji G, Wu T, Zhang X, Dou W. A survey of game theoretical privacy preservation for data sharing and publishing. In International Conference on Security and Privacy in Digital Economy. Springer. 2020:205–216.
Gunukula S, Sherif AB, Pazos-Revilla M, Ausby B, Mahmoud M, Shen XS. Efficient scheme for secure and privacy-preserving electric vehicle dynamic charging system. In IEEE International Conference on Communications (ICC). 2017:1–6.
Tsou Y, Chen H, Chang Y. RoD: evaluating the risk of data disclosure using noise estimation for differential privacy. IEEE Transactions on Big Data. 2019:1–1.
Cao Y, Yoshikawa M, Xiao Y, Xiong L. Errata on quantifying differential privacy in continuous data release under temporal correlations. IEEE Trans Knowl Data Eng. 2019;31(11):2234–2234.
Celebi H, Arslan H. Utilization of location information in cognitive wireless networks. IEEE Wirel Commun. 2007;14(4):6–13.
Prasad NR. Secure cognitive networks, in European Conference on Wireless Technology. IEEE. 2008:107–110.
Wang W, Zhang Q. Privacy-preserving collaborative spectrum sensing with multiple service providers. IEEE Trans Wireless Commun. 2014;14(2):1011–9.
Hu F, Chen B, Wang J, Li M, Li P, Pan M. MastDP: matching based double auction mechanism for spectrum trading with differential privacy. In IEEE Global Communications Conference (GLOBECOM). 2019:1–6.
Yang X, Wang T, Ren X, Yu W. Survey on improving data utility in differentially private sequential data publishing. IEEE Transactions on Big Data. 2017:1–1.
Li K, Luo G, Ye Y, Li W, Ji S, Cai Z. Adversarial privacy preserving graph embedding against inference attack. IEEE Internet Things J, in Print. 2020:1–1.
Liu J, Zhang C, Fang Y. Epic: A differential privacy framework to defend smart homes against internet traffic analysis. IEEE Internet Things J. 2018;5(2):1206–17.
Rassouli B, Rosas FE, Gndz D. Data disclosure under perfect sample privacy. IEEE Trans Inf Forensics Secur. 2020;15:2012–25.
Todo Y, Isobe T, Meier W, Aoki K, Zhang B. Fast correlation attack revisited, in Annual International Cryptology Conference. Springer. 2018:129–159.
Lu N, Shen XS. Scaling laws for throughput capacity and delay in wireless networks a survey. IEEE Comm Surveys Tutor. 2014;16(2):642–57.
Mokhtarzadeh H, Taherpour A, Taherpour A, Gazor S. Throughput maximization in energy limited full-duplex cognitive radio networks. IEEE Trans Commun. 2019;67(8):5287–96.
Alsaba Y, Rahim SKA, Leow CY. Beamforming in wireless energy harvesting communications systems: A survey. IEEE Comm Surveys Tutor. 2018;20(2):1329–60.
Gopikrishnan S, Priakanth P, Srivastava G. Dedc: Sustainable data communication for cognitive radio sensors in the internet of things. Sustain Comput: Infor Syst. 2020:100471.
Karunakaran P, Gerstacker WH. Sensing algorithms and protocol for simultaneous sensing and reception-based cognitive d2d communications in lte-a systems. IEEE Trans Cogn Commun Netw. 2018;4(1):93–107.
Chen Z, Ni T, Zhong H, Zhang S, Cui J. Differentially private double spectrum auction with approximate social welfare maximization. IEEE Trans Inf Forensics Secur. 2019;14(11):2805–18.
Wu C, Wei Z, Wu F, Chen G, Tang S. Designing differentially private spectrum auction mechanisms. Wireless Netw. 2016;22(1):105–17.
Wang J, Zhang X, Zhang Q, Li M, Guo Y, Feng Z, Pan M. Data-driven spectrum trading with secondary users’ differential privacy preservation. IEEE Transactions on Dependable and Secure Computing. 2019.
Clark M, Psounis K. Optimizing primary user privacy in spectrum sharing systems. IEEE/ACM Trans Networking. 2020;28(2):533–46.
Zhou P, Wei W, Bian K, Wu DO, Hu Y, Wang Q. Private and truthful aggregative game for large-scale spectrum sharing. IEEE J Sel Areas Commun. 2017;35(2):463–77.
Jin X, Zhang Y. Privacy-preserving crowdsourced spectrum sensing. IEEE/ACM Trans Networking. 2018;26(3):1236–49.
Dong X, Li G, Zhang T, Lu D, Shen Y, Ma J. An incentive mechanism with bid privacy protection on multi-bid crowdsourced spectrum sensing. World Wide Web. 2020;23(2):1035–55.
Li S, Zhu H, Gao Z, Guan X, Xing K, Shen X. Location privacy preservation in collaborative spectrum sensing. In Proceedings IEEE INFOCOM. 2012:729–737.
Huang Z, Gong Y. Differential location privacy for crowdsourced spectrum sensing. In Conference on Communications and Network Security (CNS). IEEE. 2017:1–9.
Zhou J, Zhang Y, Cao Z, Dong X. PPSAS: lightweight privacy-preserving spectrum aggregation and auction in cognitive radio networks. In 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS). 2019:1127–1137.
Li H, Yang Y, Dou Y, Lu C, Zabransky D, Park JMJ. Comparison of incumbent user privacy preserving technologies in database driven dynamic spectrum access systems. In International Conference on Cognitive Radio Oriented Wireless Networks. Springer. 2018:55–65.
Zhang Z, Zhang H, He S, Cheng P. Bilateral privacy-preserving utility maximization protocol in database-driven cognitive radio networks. IEEE Trans Dependable Secure Comput. 2020;17(2):236–47.
Ahmend R, Chen Y, Hassan B, Du L. CR-IoTNet: Machine learning based joint spectrum sensing and allocation for cognitive radio enabled IoT cellular networks. Ad Hoc Netw. 2021;112:102390.
Ying X, Roy S, Poovendran R. Pricing mechanisms for crowd-sensed spatial-statistics-based radio mapping. IEEE Trans Cogn Comm Netw. 2017;3(2):242–54.
Cheng Q, Nguyen DN, Dutkiewicz E, Mueck M. Preserving honest/dishonest users operational privacy with blind interference calculation in spectrum sharing system. IEEE Trans Mob Comput. 2020;19(12):2874–90.
Khan AA, Rehmani MH, Reisslein M. Cognitive radio for smart grids: Survey of architectures, spectrum sensing mechanisms, and networking protocols. IEEE Comm Surveys Tutor. 2016;18(1):860–98.
Khan AA, Rehmani MH, Reisslein M. Requirements, design challenges, and review of routing and MAC protocols for CR-based smart grid systems. IEEE Commun Mag. 2017 May 12;55(5):206–15. https://doi.org/10.1109/MCOM.2017.1500744.
Hassan MU, Rehmani MH, Kotagiri R, Zhang J, Chen J. Differential privacy for renewable energy resources based smart metering. J Parallel Distributed Comp. 2019;131:69–80.
Sun G, Liu G, Wang Y. SDN architecture for cognitive radio networks. In 2014 1st International Workshop on Cognitive Cellular Systems (CCS). 2014:1–5.
Dacier MC, Knig H, Cwalinski R, Kargl F, Dietrich S. Security challenges and opportunities of software-defined networking. IEEE Security Privacy. 2017;15(2):96–100.
Ahmend MS. Designing of internet of things for real time system. Materials Today: Proceedings. 2021.
Khan AA, Rehmani MH, Rachedi A. When cognitive radio meets the internet of things? in. International Wireless Communications and Mobile Computing Conference (IWCMC). 2016;2016:469–74.
Khan AA, Rehmani MH, Rachedi A. Cognitive-radio-based internet of things: Applications, architectures, spectrum related functionalities, and future research directions. IEEE wirel commun. 2017 Jun 22;24(3):17–25. https://doi.org/10.1109/MWC.2017.1600404.
Somov A, Dupont C, Giaffreda R. Supporting smart-city mobility with cognitive internet of things. In 2013 Future Network & Mobile Summit. IEEE, 2013:1–10.
Du M, Wang K, Chen Y, Wang X, Sun Y. Big data privacy preserving in multi-access edge computing for heterogeneous internet of things. IEEE Commun Mag. 2018;56(8):62–7.
Awin FA, Alginahi YM, Abdel-Raheem E, Tepe K. Technical issues on cognitive radio-based internet of things systems: A survey. IEEE Access. 2019;7:97887–97908.
Bkassiny M, Li Y, Jayaweera SK. A survey on machine-learning techniques in cognitive radios. IEEE Comm Surveys Tutor. 2012;15(3):1136–59.
Ding H, Li X, Ma Y, Fang Y. Energy-efficient channel switching in cognitive radio networks: A reinforcement learning approach. IEEE Trans Veh Technol. 2020;69(10):12359–62.
Sarikhani R, Keynia F. Cooperative spectrum sensing meets machine learning: Deep reinforcement learning approach. IEEE Commun Lett. 2020;24(7):1459–62.
Liu C, Wang J, Liu X, Liang Y-C. Deep cm-cnn for spectrum sensing in cognitive radio. IEEE J Sel Areas Commun. 2019;37(10):2306–21.
Zheng H, Hu H, Han Z. Preserving user privacy for machine learning: local differential privacy or federated machine learning? IEEE Intell Syst. 2020;35(4):5–14.
Du M, Wang K, Xia Z, Zhang Y. Differential privacy preserving of training model in wireless big data with edge computing. IEEE Transactions on Big Data. 2018;6(2):283–95.
Ji Z, Lipton ZC, Elkan C. Differential privacy and machine learning: a survey and review. 2014. arXiv preprint arXiv:1412.7584.
ur Rahman S, Kim G-H, Cho Y-Z, Khan A. Positioning of uavs for throughput maximization in software-defined disaster area uav communication networks. J Commun Netw. 2018;20(5):452–463.
Mei W, Zhang R. UAV-sensing-assisted cellular interference coordination: A cognitive radio approach. IEEE Wireless Communications Letters. 2020;9(6):799–803.
Xu H, Yu W, Griffith D, Golmie N. A survey on industrial internet of things: A cyber-physical systems perspective. IEEE Access. 2018;6:78238–78259.
Onumanyi AJ, Abu-Mahfouz AM, Hancke GP. Towards cognitive radio in low power wide area network for industrial iot applications. In 2019 IEEE 17th International Conference on Industrial Informatics (INDIN). 2019;1:947–950.
Chan WK, Chin JJ, Goh VT. Simple and scalable blockchain with privacy. J Info Sec Appl. 2021;58:102700.
Berdik D, Otoum S, Schmidt N, Porter D, Jararweh Y. A survey on blockchain for information systems management and security. Infor Proc Manag. 2021;58(1):102397.
Rehmani MH. Blockchain Systems and Communication Networks: From Concepts to Implementation, T. T. Engineering, Ed. Springer Nature Switzerland AG. 2021.
Mekrache A, Bradai A, Moulay E, Dawaliby S. Deep reinforcement learning techniques for vehicular networks: recent advances and future trends towards 6g. Veh Commun. 2021:100398.
Daniel A, Paul A, Ahmed A. Queuing model for cognitive radio vehicular network. In IEEE International Conference on Platform Technology and Service. 2015:9–10.
Hossain MA, Noor RM, Yau K-LA, Azzuhri SR, Zaba MR, Ahmedy I. Comprehensive survey of machine learning approaches in cognitive radio-based vehicular ad hoc networks. IEEE Access 2020;8:78054–78108.
Hasegawa M, Hirai H, Nagano K, Harada H, Aihara K. Optimization for centralized and decentralized cognitive radio networks. Proc IEEE. 2014;102(4):574–84.
Qu Y, Pokhrel SR, Garg S, Gao L, Xiang Y. A blockchained federated learning framework for cognitive computing in industry 4.0 networks. IEEE Trans Ind Inf. 2021;17(4):2964–2973.
Rathee G, Ahmad F, Kurugollu F, Azad MA, Iqbal R, Imran M. CRT-BIoV: A cognitive radio technique for blockchain-enabled internet of vehicles. IEEE Trans Intell Transp Syst, in Print. 2020:1–11.
Luong NC, Anh TT, Binh HTT, Niyato D, Kim DI, Liang Y-C. Joint transaction transmission and channel selection in cognitive radio based blockchain networks: A deep reinforcement learning approach. In IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). 2019:8409–8413.
Kotobi K, Bilen SG. Secure blockchains for dynamic spectrum access: A decentralized database in moving cognitive radio networks enhances security and user access. IEEE Veh Technol Mag. 2018;13(1):32–9.
Patnaik M, Prabhu G, Rebeiro C, Matyas V, Veezhinathan K. Probless: A proactive blockchain based spectrum sharing protocol against ssdf attacks in cognitive radio iobt networks. IEEE Netw Lett. 2020;2(2):67–70.
Hassan MU, Rehmani MH, Chen J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Futur Gener Comput Syst. 2019;97:512–29.
Hassan MU, Rehmani MH, Chen J. Differential privacy in blockchain technology: A futuristic approach. J Parallel Distrib Comput. 2020;1(145):50–74.
Akkarajitsakul K, Hossain E, Niyato D, Kim DI. Game theoretic approaches for multiple access in wireless networks: A survey. IEEE Comm Surveys Tutor. 2011;13(3):372–95.
Xu Y, Anpalagan A, Wu Q, Shen L, Gao Z, Wang J. Decision-theoretic distributed channel selection for opportunistic spectrum access: Strategies, challenges and solutions. IEEE Comm Surveys Tutor. 2013;15(4):1689–713.
Roth A. Differential privacy, equilibrium, and efficient allocation of resources. In 2013 51st Annual Allerton Conference on Communication, Control, and Computing (Allerton). 2013:1593–1597.
Liang YC, Zeng Y, Peh EC, Hoang AT. Sensing-throughput tradeoff for cognitive radio networks. IEEE Trans Wireless Commun. 2008;7(4):1326–37.
Hong X, Wang J, Wang C-X, Shi J. Cognitive radio in 5g: a perspective on energy-spectral efficiency trade-off. IEEE Commun Mag. 2014;52(7):46–53.
Zheleva MZ, Chandra R, Chowdhery A, Garnett P, Gupta A, Kapoor A, Valerio M. Enabling a nationwide radio frequency inventory using the spectrum observatory. IEEE Trans Mob Comput. 2018;17(2):362–75.
Nasr M, Shokri R, Houmansadr A. Comprehensive privacy analysis of deep learning: Passive and active white-box inference attacks against centralized and federated learning, in. IEEE Symposium on Security and Privacy (SP). 2019;2019:739–53.
Nghia Le T, Chin W, Chen H. Standardization and security for smart grid communications based on cognitive radio technologies-a comprehensive survey, IEEE Communications Surveys Tutorials. 2017;19(1):423–445.
IEEE. Draft guide for architectural framework and application of federated machine learning, IEEE P3652.1/D6, 2020;1–70.
Pokhrel SR, Singh S. Compound tcp performance for industry 4.0 wifi: A cognitive federated learning approach. IEEE Transactions on Industrial Informatics. 2021;17(3):2143–2151.
Lyu L, Yu J, Nandakumar K, Li Y, Ma X, Jin J, Yu H, Ng KS. Towards fair and privacy-preserving federated deep models. IEEE Trans Parallel Distrib Syst. 2020;31(11):2524–41.
Sattler F, Muller KR, Samek W. Clustered federated learning: Model-agnostic distributed multitask optimization under privacy constraints. IEEE Transactions on Neural Networks and Learning Systems, in Print. 2020:1–13.
Funding
No funding sources are associated with this article.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Ethical Approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Conflict of Interest
The authors declare that they have no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ul Hassan, M., Rehmani, M.H., Rehan, M. et al. Differential Privacy in Cognitive Radio Networks: A Comprehensive Survey. Cogn Comput 14, 475–510 (2022). https://doi.org/10.1007/s12559-021-09969-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12559-021-09969-9