Abstract
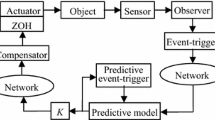
This paper addresses the issues of time delay and deception attacks in networked control systems. An event-based secure networked predictive control system (ESNPCS) architecture is proposed. The ESNPCS integrates a secure transmission protocol and an event-based networked predictive control. The secure transmission protocol guarantees the integrity, confidentiality and authenticity of transmitted data in networked control systems. The networked predictive control compensates time delay based on the control signal prediction sequence derived from the previous states, control inputs and outputs. The event-based control method alleviates the adverse influence of network congestion through the event trigger conditions. A theoretical result using the Lyapunov theory is obtained for the stability of the ESNPCS. Practical experiments are implemented to demonstrate the effectiveness of the proposed ESNPCS.
Similar content being viewed by others
References
Z.-Y. Wang and G.-P. Liu, “Performance improvement of NCSS under complex network via concurrent paths,” Journal of Systems Science and Complexity, vol. 32, no. 2, pp. 453–478, April 2019.
D.-R. Ding, Q.-L. Han, and Z.-D. Wang, “A survey on model-based distributed control and filtering for industrial cyber-physical systems,” IEEE Transactions on Industrial Informatics, vol. 15, no. 5, pp. 2483–2499, May 2019.
J. I. Leon, S. Kouro, and L. G. Franquelo, “The essential role and the continuous evolution of modulation techniques for voltage-source inverters in the past, present, and future power electronics,” IEEE Transactions on Industrial Electronics, vol. 63, no. 5, pp. 2688–2701, May 2016.
Y.-B. Zhao, J. Kim, X.-M. Sun, and G.-P. Liu, “On the delay effects of different channels in Internet-based networked control systems,” International Journal of Systems Science, vol. 44, no. 11, pp. 2119–2129, November 2013.
C. Peng and Q.-L. Han, “Delay-range-dependent robust stabilization for uncertain T-S fuzzy control systems with interval time-varying delays,” Information Sciences, vol. 181, no. 19, pp. 4287–4299, October 2011.
G.-P. Liu, J. Sun, and Y.-B. Zhao, “Design, analysis and real-time implementation of networked predictive control systems,” Acta Automatica Sinica, vol. 39, no. 11, pp. 1769–1777, November 2013.
G.-P. Liu, Y.-Q. Xia, J. Chen, D. Rees, and W.-S. Hu, “Networked predictive control of systems with random network delays in both forward and feedback channels,” IEEE Industrial Electronics Magazine, vol. 54, no. 3, pp. 1282–1297, July 2007.
T.-Y. Zhang and G.-P. Liu, “Predictive tracking control of network-based agents with communication delays,” IEEE/CAA Journal of Automatica Sinica, vol. 5, no. 6, pp. 1150–1156, November 2018.
G.-P. Liu, “Design and analysis of networked non-linear predictive control systems,” IET Control Theory & Applications, vol. 9, no. 11, pp. 1740–1745, July 2015.
J. Wang and B.-C. Ding, “Two-step output feedback predictive control for hammerstein systems with networked-induced time delays,” International Journal of Systems Science, vol. 49, no. 13, pp. 2753–2762, August 2018.
M. Li and Y. Chen, “Robust time-varying h∞ control for networked control system with uncertainties and external disturbance” International Journal of Control, Automation, and Systems, vol. 16, no. 5, pp. 2125–2135, October 2018.
X.-M. Sun, K.-Z. Liu, C. Wen, and W. Wang, “Predictive control of nonlinear continuous networked control systems with large time-varying transmission delays and transmission protocols,” Automatica, vol. 64, pp. 76–85, February 2016.
H.-C. Yi, C.-J. An, and J.-Y. Choi, “Compensation of time-varying delay in networked control system over WI-FI network,” International Journal of Computers Communications and Control, vol. 12, no. 3, pp. 415–428, June 2017.
A. Kuzu, S. Bogosyan, and M. Gokasan, “Predictive input delay compensation with grey predictor for networked control system,” International Journal of Computers Communications & Control, vol. 11, no. 1, pp. 67–76, February 2016.
Z.-H. Pang, G.-P. Liu, D.-H. Zhou, and D.-H. Sun, “Design and performance analysis of networked predictive control systems based on input-output difference equation model,” International Journal of Control, Automation, and Systems, vol. 15, no. 1, pp. 416–426, February 2017.
H. W. Gomma and A. Allam, “Physical layer privacy scheme for networked control systems,” International Journal of Control, Automation, and Systems, vol. 13, no. 1, pp. 167–174, February 2015.
P. Swaminathan, K. Padmanabhan, S. Ananthi, and R. Pradeep, “The secure field bus (SecFB) protocol — network communication security for secure industrial process control,” Proc. of the 10th Conference IEEE Region, pp. 1–4, 2006.
R. A. Gupta and M. Y. Chow, “Performance assessment and compensation for secure networked control systems,” Proc. of the 34th Conference IEEE Industrial Electronics Society, pp. 2929–2934, 2008.
Q. Zhang, C.-H. Wu, and J. D. Irwin, “A coalition key-evolving signature scheme towards intrusion resilient mobile networks for industrial applications,” Proc. of the 29th Conference of the IEEE Industrial Electronics Society, pp. 1447–1452, 2003.
Y.-F. Xu, R.-G. Song, L. Korba, L.-H. Wang, W.-M. Shen, and S. Lang, “Distributed device networks with security constraints,” IEEE Transactions on Industrial Informatics, vol. 1, no. 4, pp. 217–225, November 2005.
Z.-H. Pang and G.-P. Liu, “Design and implementation of secure networked predictive control systems under deception attacks,” IEEE Transactions on Control Systems Technology, vol. 20, no. 5, pp. 1334–1342, September 2012.
R.-N. Yang, Y.-R. Y, J. Sun, and H. R. Karimi, “Event-based networked predictive control for networked control systems subject to two-channel delays,” Information Sciences, vol. 524, pp. 136–147, July 2020.
X.-X. Yin, D. Yue, S.-L. H, C. Peng, and Y.-S. Xue, “Model-based event-triggered predictive control for networked systems with data dropout,” SIAM Journal on Control and Optimization, vol. 54, no. 2, pp. 567–586, March 2016.
L. Zhao, X. Ma, and J. Wang, “Networked predictive control for linear systems with quantizers by an event-driven strategy,” Journal of the Franklin Institute, vol. 356, no. 6, pp. 3245–3269, February 2019.
F. Mendel, T. Nad, and M. Schläffer, “Finding SHA-2 characteristics: Searching through a minefield of contradictions,” Proc. of the 17th Conference on the Theory and Application of Cryptology and Information Security, vol. 7073, pp. 288–307, December 2011.
P. Mahajan and A. Sachdeva, “A study of encryption algorithms AES, DES and RSA for security,” Global Journal of Computer Science and Technology, vol. 13, no. 15, pp. 14–22, December 2013.
J. Daemen and V. Rijmen, The Design of Rijndael: AES — The Advanced Encryption Standard, Berlin, Heidelberg, 2002.
Funding
This research was supported by the National Natural Science Foundation of China under Grants 61973257 and 61973331, Sichuan Youth Science and Technology Foundation under Grant 2017JQ0022, and the Innovation Fund of Postgraduate, Xihua University under Grant YCJJ2021067.
Author information
Authors and Affiliations
Corresponding author
Additional information
Biao Xiang is currently pursuing a Master’s degree in the School of Electrical Engineering and Electronic Information, Xihua University, China. His research interests include networked control and intelligent control.
Xia Liu received her Ph.D. degree from University of Electronic Science and Technology of China in 2011. In 2009–2010, she was a visiting scholar in the Department of Electrical and Computer Engineering, University of Alberta, Canada. In 2013–2014, she was a visiting scholar in the Department of Mechanical Engineering, the University of Adelaide, Australia. Since 2012, She has been with the School of Electrical Engineering and Electronic Information in Xihua University, China, and now a professor. Her research interests include nonlinear system and control.
Yong Chen received his Ph.D. degree in control theory and control engineering from Chongqing University, Chongqing, China, in 2007. Since 2015, he has been a Professor and a Ph.D. supervisor with the School of Automation Engineering and the Director of the Institute of Electric Vehicle Driving System and Safety Technology, University of Electronic Science and Technology of China, Chengdu, China. He is a member of the Chinese Society for Electrical Engineering. His current research interests broadly include power electronics, motor control, energy control, networked control, and smart grid.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Xiang, B., Liu, X. & Chen, Y. Event-based Networked Predictive Control Systems with Secure Transmission Protocol. Int. J. Control Autom. Syst. 20, 1076–1086 (2022). https://doi.org/10.1007/s12555-021-0265-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12555-021-0265-z