Abstract
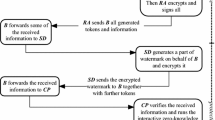
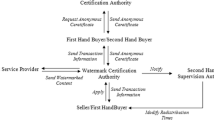
A buyer-seller watermarking protocol is a combination of traditional watermarking and fingerprinting techniques. Recently, Frattolillo proposed such a watermarking protocol suitable for web context. Frattolillo’s scheme has two problems which would make it hard to implement practically. Several possible solutions to the two problems are presented in this paper.
Similar content being viewed by others
References
Qiao L, Nahrstedt K. Watermarking schemes and protocols for protecting rightful ownerships and customer’s rights [J]. Journal of Visual Communication and Image Represent, 1998, 9(3): 194–210.
Memon N, Wong P W. A buyer-seller watermarking protocol [J]. IEEE Transactions on Image Processing, 2001, 10(4): 643–649.
Lei C L, Yu P L, Tsai P L, et al. An efficient and anonymous buyer-seller watermarking protocol [J]. IEEE Transactions on Image Processing, 2004, 13(12): 1618–1626.
Frattolillo F. Watermarking protocol for web context [J]. IEEE Transactions on Information Forensics and Security, 2007, 2(3): 350–363.
Kuribayashi M, Tanaka H. Fingerprinting protocol for images based on additive homomorphic property [J]. IEEE Transactions on Image Processing, 2005, 14(12): 2129–2139.
Rivest R L, Shamir A, Adelman L. A method for obtaining digital signatures and public key cryptosystems [J]. Communication of the ACM, 1978, 21(2): 120–126.
Okamoto T, Uchiyama S. A new public-key cryptosystem as secure as factoring [C]//Eurocrypt’98, LNCS. Berlin: Springer-Verlag, 1998: 308–318.
Paillier P. Public-key cryptosystems based on composite degree residuosity classes [C]//Eurocrypt’99, LNCS. Berlin: Springer-Verlag, 1999: 223–238.
Mao W. Modern cryptography: Theory and practice [M]. London: Prentice Hall PTR, 2003.
Stinson D R. Cryptography: Theory and practice [M]. 2nd ed. Boca Raton: CRC Press, 2002.
Cox I J, Kilian J, Leighton T, et al. Secure spread spectrum watermarking for multimedia [J]. IEEE Transactions on Image Processing, 1997, 6(12): 1673–1687.
Cox I J, Miller M L, Bloom J A. Digital watermarking [M]. San Francisco: Morgan Kaufmann, 2002.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: the National Natural Science Foundation of China (Nos. 60970110, 60972034 and 60773086), the National Basic Research Program (973) of China (No. 2007CB311201) and the Shanghai Leading Academic Discipline Project(No. B412)
Rights and permissions
About this article
Cite this article
Zeng, P., Cao, Zf. & Lin, H. Analysis and enhancement of a watermarking protocol suitable for web context. J. Shanghai Jiaotong Univ. (Sci.) 15, 392–396 (2010). https://doi.org/10.1007/s12204-010-1022-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12204-010-1022-2